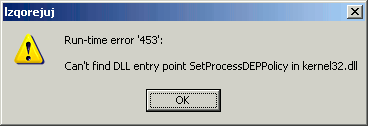
Here at K7TCL, we noticed a spike in the number of samples arriving with the file name “porno-rolik[2 digit number].avi.exe”. Closer inspection of the files revealed that it was yet another variant of a Ransomware. On execution, this ransomware displays a fake error message like the one shown below:
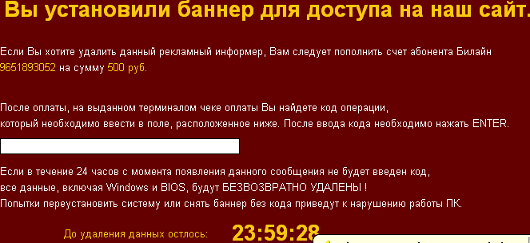
The ransomware then reboots the computer and a sexually explicit image is displayed to the user demanding him/her to dial a premium rate number and enter a code which would then unlock the machine. This particular ransomware even goes to the extent of displaying a countdown message and threatening to delete the files on the computer if the unlock code is not provided within a period of 24 hours.
Given below is a list of the URLs which were found distributing this ransomware last week:
- http://pornovirtualxxx.ru/[Blocked]porno-rolik[Blocked].avi.exe
- http://veryhotxxxporno.ru/[Blocked]porno-rolik[Blocked].avi.exe
- http://bestvideopornoxxx.ru/[Blocked]porno-rolik[Blocked].avi.exe
- http://lolkorussiangirlsporno.ru/[Blocked]porno-rolik[Blocked].avi.exe
- http://megabytespornovideo.ru/[Blocked]porno-rolik[Blocked].avi.exe
- http://pornovirtualxxx.ru/[Blocked]porno-rolik[Blocked].avi.exe
- http://smotripornomnogoxxx.ru/[Blocked]porno-rolik[Blocked].avi.exe
Our blog readers might recall an earlier blog post where we had discussed about how malware authors have gotten better at manipulating peoples behaviour to execute their code & this ransomware campaign is another example of such a scenario. Looking at the file name, the URLs which distribute them and the error message that is displayed on the malware execution suggests that this ransomware arrives as a part of a fake codec scam, possibly when a user attempts to download a video promising to deliver explicit content.
Our usual sentiments about keeping one’s security solution up-to-date & avoiding downloads from unknown sites apply.
Lokesh Kumar
K7TCL









