This is the first part of a three-part blog based on my paper for AVAR 2012 that discusses the security challenges involved in adopting two relatively new technologies, namely, Internet Protocol Version 6 and Internationalized Domain Names.
The Internet landscape is about to witness profound changes with the mass adoption of Internet Protocol Version 6 (IPv6) and Internationalised Domain Names (IDNs) in the near future. While these developments have the potential to be immensely beneficial, they also present certain challenges to the security industry which need to be addressed. These changes not only increase the attack surface for malware authors and spammers, but also render traditional methods of URL and spam blocking obsolete.
The exhaustion of the 32 bit IPv4 addresses assigned by the Internet Assigned Numbers Authority (IANA) has led to the roll-out of its 128 bit successor, IPv6. This provides a significant increase in the address pool available to assign unique IP addresses, not only to computers, but also to other Internet-connected devices. Spammers and malware authors would now have a larger address space to infect and cycle through, vitiating existing methods of detecting spam/malware URLs.
The Internet Corporation for Assigned Names and Numbers (ICANN) has expanded domain names to include non-ASCII based IDNs in a user’s native language script. While these transitions have the potential to localise the global Internet, they also provide cyber criminals (spammers/phishers/malware distributors) enhanced opportunities for exploitation, especially via social engineering.

These cyber criminals will now have the ability to redirect a user to a URL with a character set unfamiliar to him/her. Given the exponential increase in the number of URLs shared among users in our socially inter-networked world, validation of these URLs by the user prima facie now becomes much more complicated, leading to a higher compromise success rate for cyber criminals.
This paper describes the imminent major changes to the Internet networking infrastructure. It attempts to explore the security challenges involved in these milestone developments and presents potential solutions to address them.
The IPv4 Clock is Ticking
The expansion of the Internet from an esoteric academic project to a publicly accessible resource, coupled with the surge of Internet enabled devices over the last decade have contributed to the shrinking pool of available IPv4 addresses.
Fig.1 depicts the number of expected Internet enabled devices and Internet users by 2016, and how they measure up with the number of IPv4 addresses available.
Fig.1: Number of connected devices & Internet users by 2016 [1]
Conservation efforts like Network Address Translation (NAT), Classless Inter Domain Routing (CIDR), reclaiming unused addresses etc., only prolonged what was unavoidable – the depletion, and eventual exhaustion, of IPv4 addresses.
Given that ICANN, which is responsible for distributing IP addresses, gave away the last block of IPv4 addresses to the five Regional Internet Registries (RIR) in early 2011 [2], the need for change is rather pressing.
IPv6 to the Rescue
This IPv4 address crunch has been anticipated for many years, and the Internet Engineering Task Force (IETF) has been working on refining IPv6, the successor to IPv4, since the early 1990s [3]. This version of the Internet Protocol can support up to 300 undecillion addresses compared to the relatively miniscule 4 billion, a number smaller than the current world population, offered by its predecessor. Apart from this massive increase in the address space, the IETF also embedded other features to IPv6 such as support for IPSec, auto-configuration of devices, etc. [4]
These benefits, along with the availability of IPv6 from ISPs, increased end-user device support & IPv6 content, will ensure the adoption of IPv6 in the years to come, eventually making it the dominant Internet Protocol.
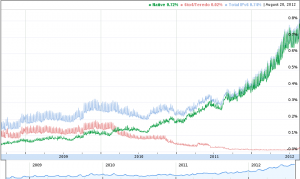
Fig.2 shows that, as expected, the percentage of users accessing Google over a native IPv6 connection has seen a steep rise over recent times.
Fig.2: Percentage of IPv6 users accessing Google [5]
What’s in a Domain Name
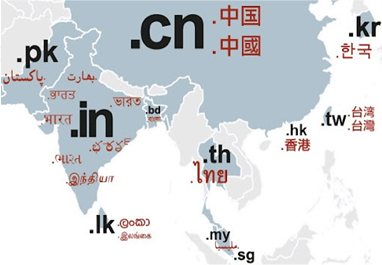
The demand for Internationalised Domain Names (IDNs) has always existed in view of the fact that 60% of the countries around the world have an official language other than English [6]. ICANN, which has domain names within its remit, has recently started allowing IDNs to satisfy this unmet demand.
The introduction of IDNs allows non-ASCII character sets like Arabic, Cyrillic, Tamil, Hindi, Chinese, etc, to be included in a domain name, potentially paving the way for a truly globalised Internet.
These IDNs are converted into ASCII using Puny Code, an encoding syntax invisible to the user, which allows for standard domain name resolutions.
Fig.3 shows a domain name in English, its nonexistent IDN equivalent in the Tamil script, and the Puny Code representation of the IDN which is used for a domain name resolution.
Fig3: Domain Name, IDN, Puny Code representation
The current demand for IDNs, combined with registrars throwing them away at a price cheaper than the regular domains, could see a surge in the number of non-English sites registering domain names in their local language.
Click here to read the second part of this blog.
References:
[1] http://www.google.com/intl/en/ipv6/images/graph.png
[2] http://en.wikipedia.org/wiki/IPv6#Exhaustion_of_IPv4_addresses
[3] http://en.wikipedia.org/wiki/IPv6#Working-group_proposal
[4] Information on http://en.wikipedia.org/wiki/IPv6
[5] http://www.google.com/intl/en/ipv6/statistics.html
[6] http://en.wikipedia.org/wiki/List_of_countries_where_English_is_an_official_language
Images courtesy of icann.org & worldipv6launch.org
Lokesh Kumar
Manager, K7 Threat Control Lab
If you wish to subscribe to our blog, please add the URL provided below to your blog reader:
https://labs.k7computing.com/feed/