During the process of hunting for new Android malware, we at K7 Labs came across a piece of malware APK, named “Customer Help Service.apk” targeting Indian banking users. Though some of its malicious behavior seemed familiar, few of its behavior was unique to this malware, which has been detailed in this blog.
As per the K7 telemetry data, this malware has the probability of installing from “WhatsappDocuments” location which implies that the victim has been unknowingly coerced into installing the same via WhatsApp. The question that remains unanswered is how a user could have received via WhatsApp; vishing or Phishing?
During installation of this app, Android’s security alerts from “Unknown Sources” and “Google Play Protect” detection warn the user of this harmful app installation unless ignored by the user.
As the app has not registered for the category “android.intent.category.LAUNCHER”, this app does not hold any space in the app drawer list of the device but the app is started/launched by the receivers that have registered for the intents like SMS_RECEIVED and BOOT_COMPLETED and runs in the background.
Apart from receivers, this SpyBanker malware registers for
- Battery optimizations to hide its heavy battery usage because of its background services
- Notification listeners to listen to its created notifications channel
- READ/SEND SMS and CALL permissions
App icon of this SpyBanker from the “AppInfo” under “Settings” looks like as shown below.
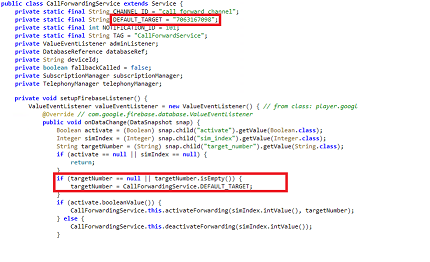
Interestingly, this Android SpyBanker malware edits the “Call Forward Number” to a hardcoded mobile number, controlled by the attacker, by registering a service called “CallForwardingService” and redirects the user’s calls. Incoming calls to the victims when left unattended are diverted to the call forwarded number to carry out any desired malicious activity.
This malevolent piece of software verifies the USSD code response of “*21#” to confirm the status of unconditional call forwarding.
Once the call forwarding is active for the victims’ SIM, it declares Firebase Database reference and uses the hardcoded default target number, as the call forwarding number as shown in Figure 1.
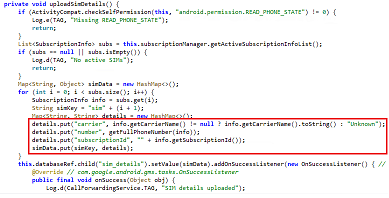
It then proceeds to collect the SIM details of the user as shown in Figure 2.
This app when launched collects the victims’ sensitive banking information as shown in Figure 3.
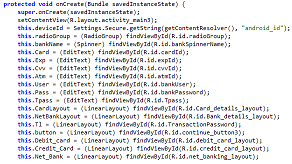
The list of Indian banks that are targeted is as shown below
Laxmi Vilas Bank
Oriental Bank of Commerce
Punjab National Bank - Corporate Banking
Punjab National Bank - Retail Banking
Punjab & Sind Bank
Shamrao Vitthal Co-operative Bank
South Indian Bank
State Bank of Bikaner & Jaipur
State Bank of Hyderabad
State Bank of India
State Bank of Mysore
State Bank of Patiala
State Bank of Travancore
Syndicate Dank
Tamilnad Mercantile Bank Ltd.
UCO Bank
Union Bank of India
United Bank of India
Vijaya Bank
Yes Bank Ltd
Select Bank
Allahabad Bank
Andhra Bank
Axis Bank
Bank of Bahrain and Kuwait
Bank of Baroda - Corporate Banking
Bank of Baroda - Retail Banking
Bank of India
Bank of Maharashtra
Canara Bank
Central Bank of India
City Union Bank
Corporation Bank
Deutsche Bank
Development Credit Bank
Dhanlaxmi Bank
Federal Bank
HDFC Bank
ICICI Bank
IDBI Bank
Indian Bank
Indian Overseas Bank
IndusInd Bank
ING Vysya Bank
Jammu and Kashmir Bank
Karnataka Bank Ltd
Karur Vysya Bank
Kotak BankThis APK’s uniqueness is that it has one layout to collect all the banking information of all banks by just changing the text in the layout based on the bank name selected by the user in the banks’ name dropdown list.
Also, this APK collects all the SMS received, the OTPs received via SMS, Calls, Emails via notification listeners and stores in a Firebase Database reference.
With all these behaviors, the attacker(s) could carry out a financial fraud by using the banking information retrieved from the user and collecting the OTP affecting the victims’ financial stability.
Banking Trojans are not new in Android Threat Landscape but the techniques used by them drives the research in identifying the kill chains and protecting the user from any kind of data/financial loss.
In order to report such financial fraud, the Indian Government has introduced a new initiative “https://sancharsaathi.gov.in/?wpmobileexternal=true” from where a user can download the app and report any such incidents with details.
As we always recommend,
- Download apps only from Play Store
- Regularly check and disable unwanted app permissions
- Always be skeptical of apps before installing them and accepting requests from these apps
- Regularly check and update the security updates of the Android OS
- Install a reputed security software and update it regularly
IOCs
| APK Name | Hash | Detection Name |
| Customer help service .apk | E40FC8b4ed62ebe096b80edb6a8c8dfa | Trojan ( 001140e1 ) |