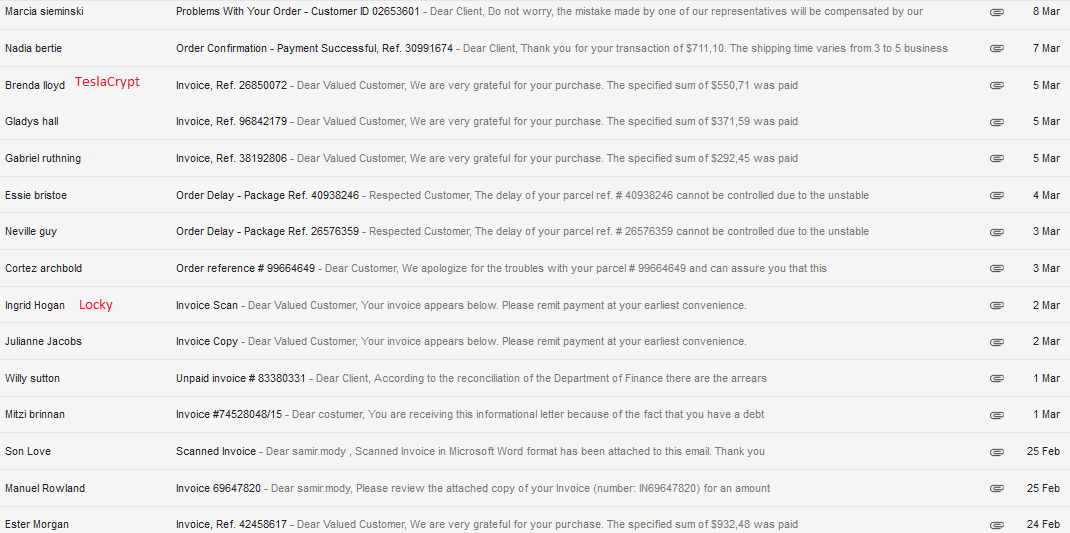
Beware of two aggressive ransomware spam campaigns which have been active for the past few weeks.
The above screenshot of my own spam folder exemplifies the typical theme used by the new ransomware kid on the block, “Locky”, and the latest version of an established ransomware called “TeslaCrypt“.
Although both ransomware spam runs pretend to be an “Invoice”, the next stage of the infection vector for Locky and TeslaCrypt differ significantly from each other. Locky spam mails contain an attachment such as ‘scan_<number>.doc’, whereas the current TeslaCrypt spam contains a ZIP archive wrapping a JavaScript file, e.g. ‘invoice_<random alphanumeric>.js’.
The Locky DOC file contains a password-protected macro VBA script. Please note, since macros can contain malicious code they are disabled by default in Microsoft Word, and should remain so. The objective of the Locky macro script as well as the TeslaCrypt JavaScript is to download and execute the respective ransomware payload EXE.
Typical malicious spam campaigns deliver the payload directly in a ZIP attachment containing an EXE. However such attachments are easier to block at the email gateway level since they are considered “high risk”. It is more difficult to block non-EXE files at the gateway as a matter of policy, hence the Locky and TeslaCrypt attachments are more likely to get past gateway filters onto the local computer. Thereafter, given their script context rendered by standard interpreting applications, the download and execution of the ransomware payload is less likely to be blocked by behavioural protection mechanisms such as HIPS and the firewall.
K7 has robust protection at multiple levels against both ransomware campaigns, however, as always, prevention is much better than cure. In the case of spam, it is best to completely avoid emails from unknown sources, especially those which expect one to open an attachment or click on a link.
Samir Mody
Senior Manager, K7TCL
If you wish to subscribe to our blog, please add the URL provided below to your blog reader: https://labs.k7computing.com/feed