Post WannaCry the world witnessed yet another brutal ransomware-style attack last week by Petya. Yet not a single user of a K7 Security Product reported any issue to K7 Technical Support, although Petya is known to have hit several Indian computers.
We at K7TCL constantly monitor for any new instances of malware, especially destructive ones like Petya. K7 Security Products protect their users by detecting Petya component files from the ransomware’s release time till date, as
- Trojan (0001140e1)
- Trojan (00510cfe1)
Unlike WannaCry, in addition to encrypting user’s data files, Petya ransomware may also modify the Master Boot Record (MBR) of the user’s machine as well, complicating the scenario still further.
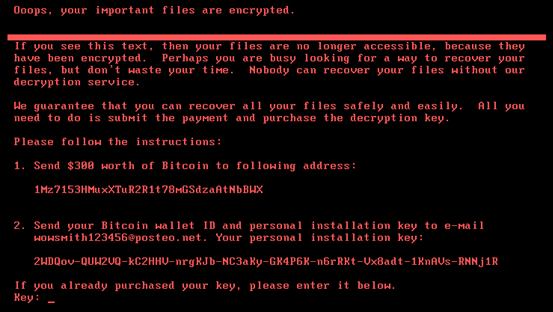
The image shown above is the screen displayed on an infected computer demanding a ransom of “$300 worth of bitcoin”. However there is reason to believe that the real objective of this variant of Petya was not to make money but just to destroy data in an irreversible way.
Anyway the “ransom screen” appears after a sequence of malicious activities are performed. Let us take a quick look at the technical details of Petya and how it infects a user’s machine.
Petya ransomware comes in as a DLL file (Dynamic Link Library) and is executed as follows:
Rundll32.exe “<path to Petya.dll>” #1
Note: Petya.dll is the pseudo name of the sample executed.
Petya has several spreading techniques. One of these employs the same method as that used by WannaCry ransomware to enter a victim’s machine by exploiting a critical SMB RCE vulnerability, i.e. using EternalBlue to exploit vulnerabilities covered in the MS17-010 update. Petya is also capable of worm-like activity to spread across the systems in a network, remotely executed using PsExec.
As this malware is executed, it first checks if the following privileges are available
- SeShutdownPrivilege – Required to shut down a local system
- SeDebugPrivilege – Required to debug and adjust the memory of a process owned by another account
- SeTcbPrivilege – This privilege identifies its holder as part of the trusted computer base. Some trusted protected subsystems are granted this privilege
Once the Petya DLL confirms that the required privileges are available, it enumerates all the running process in the system to verify if any of the following Anti-Virus programs are installed in that system by using its own XOR encryption routine to determine a hash value.
| Hash Value | Process Name | AV Product |
| 0x2E214B44 | avp.exe | Kaspersky |
| 0x6403527E | ccSvcHst.exe | Symantec |
| 0x651B3005 | NS.exe | Norton |
The results of both privileges checks and Anti-Virus process check are stored as bit-masked global variables that affect the flow in which this Petya malware executes on a system.
Assuming that the required checks are satisfied to run, this malware copies the entire file into virtual memory using “VirtualAlloc” and “MemCpy” APIs, so that it can delete the main file using the “DeleteFileA” API, and then jump to a new entry point in the newly created virtual space.
Then by using “LoadLibraryA” and “GetProcAddress” it dynamically rebuilds the import table of the file in virtual space. It also checks for the presence of “perfc.dat” in the Windows folder, and if found exits execution completely.
Otherwise it infects the MBR by opening a handle to logical volume \.\C:, retrieving the drive geometry and overwrites sectors at 0x200 from the start. In the same way, it also retrieves the geometry of \.\PhysicalDrive0 and overwrites sectors on that drive with malicious code.
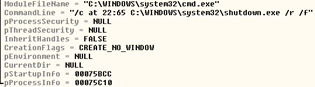
After infecting the MBR this malware creates a scheduled task to perform a system restart after 15 minutes.
This time is utilized by malware to drop and execute a file from its resource section into the Temp folder which acts as an infostealer, and also tries to spread itself by creating threads which attempt to enumerate all subnets of the local network, then trying to connect to each IP to test its SMB ports.
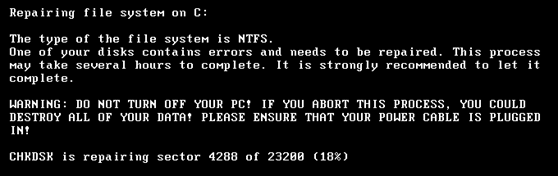
As the restart task triggers, it displays a fake Chkdsk.exe repair screen as it tries to encrypt the hard drive as shown below
Once the encryption is done, as the final step it shows a ransom note demanding $300 as shown earlier.
Apart from the continuous protection from K7 Security products against malware, we recommend users to regularly and urgently deploy security updates for the operating system as soon as available.
Shiv Chand
Senior Threat Researcher, K7TCL