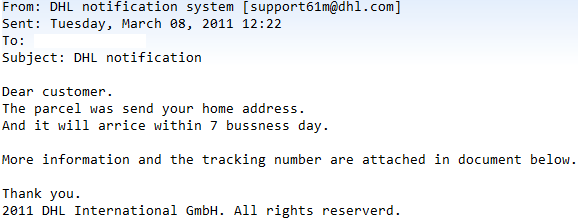
Bredolab is a family of Russian botnets which are frequently spammed out purporting to be from reputed organisations such as DHL or UPS. The messages have ZIP archive attachments containing the malicious bot executable. This particular spam campaign has been alive for the best part of the last couple of years with little change, which implies that it is still efficacious. Why “fix something that ain’t broke”?
Yesterday, however, as blogged by my colleague in the Anti-Virus community, the campaign unexpectedly changed insofar as several grammatical and spelling mistakes made their way into the standard fake message “from DHL”:
It is true that on several occasions in the past cybercriminals have been found wanting where communication in English is concerned. However, the latest message with all the errors breaks with the trend seen over the past couple of years. Previous versions of the social engineered message body were largely error free, at least ostensibly, and therefore rather convincing … well, probably only to the uninitiated. In fact the executable file within the ZIP archive in the current campaign even has an Adobe PDF icon.
Given the discrepancy between the old and the new versions of this campaign, one wonders whether there has been a change of helmsman coordinating these attacks who attaches less importance to quality control. On the other hand it is possible that the spelling mistakes have been deliberately introduced to evade targeted spam rules based on standard text patterns. After all the only reason that the bot executable is sent within a ZIP attachment is to circumvent heuristic rules at the gateway which may quarantine emails containing raw executables.
In any case it is important to stay informed about this particular campaign to reduce instances of PEBCAK (Problem Exists Between Chair And Keyboard), and to ensure that your Anti-Virus software is kept up-to-date. K7 products detect the latest bredolab executable as Trojan (0021b05e1).
Samir Mody
Senior Manager, K7TCL