This is the second instalment of a 3-part series representing my paper for AVAR 2011, investigating malware which have emanated from Asia, charting the likely reasons for these, and attempting to predict future trends.
Continuing from the first instalment on last week’s blog…

The Art of Cyber War
Nation-specific Attacks
Stuxnet, a worm with a particularly venomous, damaging payload, was almost certainly targeting the Iranian nuclear establishment. Given the means and the end, if one were to consider the motive, one would have no alternative but to attribute the creation of Stuxnet to powerful nations inimical to Iran’s nuclear programme, a couple of which are in West Asia.
The use of malware as an instrument of state policy may have already been in effect for a couple decades[Rainer Fahs, keynote address, EICAR2011]. In modern times nation-to-nation attacks, alleged or otherwise, have been given considerable publicity with much finger wagging and pointing. Many of these instances of cyber warfare appear to originate in Asia, which is hardly surprising given the frosty relationships that exist between several neighbourhood countries in Asia, e.g. North Korea-South Korea, India-Pakistan, etc. Indeed, avoiding the mention of China’s alleged contribution to cyber warfare would be like ignoring the elephant in the room, and the apparent involvement of Israeli personnel most certainly deserves an explicit mention.
There have been several documented cases of nation-specific cyber attacks, some of which are potentially ongoing. These cases may be summarised as follows:
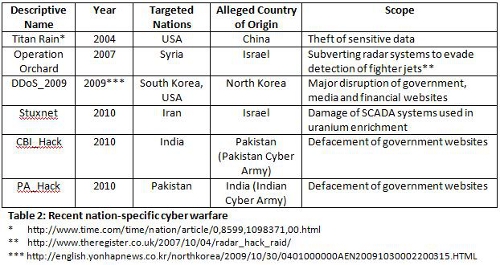
The strategic advantage offered to powerful and resourceful nations via targeted cyber attacking is highly significant. As described in Table 2, the scope of these attacks could be anything from the stealing of state secrets to the targeted damage of both government hardware and software. Critical modern infrastructure is controlled by computer systems which presents an irresistible target for cyber attacks.
The stakes and incentives involved in cyber warfare are high, and cyber attacks are unlikely to diminish in the years to come. On the contrary, cyber warfare is likely to increase manifold with an eastward shift in the balance of power in the global hegemony suggesting an increasing involvement of Asian states.
There can be little doubt that the military and intelligence establishments of various nations have wings dedicated to cyber warfare. Sun Tzu would have been proud. Given the enormous resources involved and the high-profile, targeted nature of cyber attacks, it is difficult to predict the security responses of commercial Anti-Virus companies and the general public at large. It is likely that standard civilian bodies would be largely bystanders in these events. Indeed, for every attack that is reported and documented in the public domain, there may well be several others which are kept very firmly under wraps.
However, perhaps there are some mitigating circumstances:
- As a diplomatic preventative measure, it is possible that there could be an international convention, perhaps UN-brokered, on cyber warfare. The US government has already been contemplating diplomatic talks with certain countries. The main issue herein could well be the difficulty in proving state versus non-state actors, a challenge even in conventional warfare where proxy militant groups have been used with impunity to perpetrate attacks across international boundaries.
- Standard technical measures to secure systems, including instituting prescribed system configurations and policies, may be sufficient to prevent “80 percent of commonly known cyber attacks”.
Notwithstanding, it will be interesting to track how events transpire in the future. The average citizen of the world may well have to wait for the future offerings from Hollywood or Bollywood, with their vivid imaginations, to gauge the extent of the issues dealt with by sedentary agents code named ‘0000 0000 0111’, ‘JS0N B0URN3’, etc.
Corporate Insecurities
The attacks on large, well-known corporate entities over the recent past have been much publicised. The alleged origin of some of these high-profile, ongoing, attacks lie in Asia. It is worth summarising some of these attacks, described as “Advanced Persistent Threats”, as follows:
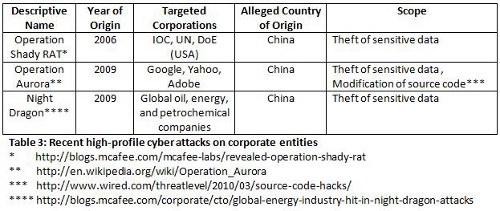
The origin of some of the attacks mentioned in Table 3 is up for heated debate as the parties concerned accuse each other of skulduggery and conspiratorial activity. In many cases, hard evidence pointing the finger at a specific culprit is rather difficult to gather which provides a level of immunity from risk for the perpetrators.
Targeted attacks on large corporate entities could, no doubt, yield valuable information which can eventually be used for significant financial gain, whether through a transfer of intellectual property, sabotage of competitor infrastructure, or a straightforward theft of classified financial data. The perceived or real benefits from such attacks for the perpetrators provide a clear incentive to invest resources.
Under these circumstances of high reward versus relatively low risk, and given the recent record of security breaches, the trend of targeted cyber attacks against corporations looks set to continue, and probably at an increasing rate.
Malware in Societal Conflicts


Terrorism may be defined as the systematic use of coercive tactics to instil fear in a targeted group as a means to the end of a perceived political gain.
Conflicts between different groups, whether within the bounds of the same sovereign territory or across international frontiers, have existed since the dawn of mankind. Some of the high-profile modern day conflicts involve actors, “state” or “non-state”, based in Asia who resort to forms of terrorism, whose definition and application to any given scenario is highly subjective, in an attempt to seek political mileage or redress against perceived grievances.
Given the advance of technology and the ubiquity of computer systems, many in critical infrastructure, acts of terror have included or are likely to include, at an increasing rate, attacks via binary media, i.e. code, software, etc. These attacks may be described as “Cyber Terrorism”.
Groups involved in international terrorist activities, many based in Pakistan and Afghanistan, include individuals familiar with modern computer systems and communication channels. Groups such as “al-Qaeda” allegedly have a dedicated R&D wing with ‘digital specialists’ successfully exploiting smartphone platforms for the theft of sensitive data. Given the impact it would likely have in spreading anxiety, there is a possibility, nay probability, that attempts will be made to cause the targeted destruction of systems in the future, via the mass deployment of malware, in addition to data theft.
Sometimes civilian bodies have been targeted by groups which are unlikely to be described as “militant”. Rather, it is possible that the civilian bodies themselves may conform to the definition of “militant”, yet another subjective and emotive term. For example, there have been numerous, but intermittent, malware attacks on pro-Tibet groups in recent years, the ones in 2008 just before the Beijing Olympics being widely reported by the media and in various IT security blogs. Many of these attacks involve the use of documents such as PPT and PDF containing crafted exploit code (some attacks have involved browser exploits), mailed to known individuals or posted to various fora. Attacks such as these have been alleged to originate in China , but some or all of them could have involved a social engineering angle, financially motivated, to exploit the media attention attributed to societal conflicts in areas such as Palestine or Tibet . Once again, it is difficult to garner specific evidence to arraign any one party. It remains to be seen how malware might be used in the future against such groups as the number of documented incidents appears to be waning.
The security industry has played, and will continue to play, a role in mitigating and remediating many of these attacks since the victims tend to be ordinary civilians, even if specifically targeted on occasion, and visibility of such attacks is relatively high.
Images courtesy of:
cyberlawsinindia.blogspot.com
mumbai.olx.in
www.warchat.org
Samir Mody
Senior Manager, K7TCL
If you wish to subscribe to our blog, please add the URL provided below to your blog reader:
https://labs.k7computing.com/feed/






