This is the final instalment of a 3-part series representing my paper for AVAR 2011, investigating malware which have emanated from Asia, charting the likely reasons for these, and attempting to predict future trends.
Continuing from the second instalment on last week’s blog…
In the Name of Mammon
The volume of malware samples up to 2006 and the 20 years prior to that could not have totalled more than a quarter of a million. Post 2006, however, the number of malware samples discovered year-on-year has multiplied manifold, with the current number of daily samples being in the order of tens of thousands. An estimate of the gross volume of malware samples since 2007 stands at well over 52.6 million.
The modern threat landscape is heavily dominated by malware written for financial gain, and since 2007 much of this malware is believed to originate in China and Russia (and the erstwhile republics of the Soviet Union), with those in South Korea and Brazil being smaller but significant players. It must be borne in mind that tracing malware back to its true origins is a difficult exercise since it is extremely straightforward for malware to pretend to come from another country, whether based on malware hosting URL or locales within the binary samples, etc. However, a crude analysis of recent malware samples suggests that 20% come from China, 10% come from Russia, 3% may be attributed to Brazil, and 2% are Korean. These numbers are almost certainly gross underestimates. Suffice to state that the perception that the bulk of malware, much of it with a financial motive, comes from a handful of countries is a reasonable one. However, one ought to go further in an attempt to understand the potential reasons for this geographical bias in malware origin. Let us first digress briefly to explore the nature of some of the modern threats that have emanated from Asia.
Lineage of Modern Asian Malware
The spate of Autorun worms has already been described earlier. Many of these Autorun worm families did not have an obvious link to financial gain. The motive was to morph soon enough.
 During the mid-to-late 2000s Asian malware was dominated by families of High Level Language Prepender file infectors and password stealers (PWS/PSW Trojans) which are believed to originate primarily in China. These PWS Trojans targeted online games such as Lineage and World of Warcraft, supposedly popular amongst Chinese gamers. Stolen game passwords and artefacts appear to have been sufficiently in demand to warrant a black market involving the exchange of hard currency.
During the mid-to-late 2000s Asian malware was dominated by families of High Level Language Prepender file infectors and password stealers (PWS/PSW Trojans) which are believed to originate primarily in China. These PWS Trojans targeted online games such as Lineage and World of Warcraft, supposedly popular amongst Chinese gamers. Stolen game passwords and artefacts appear to have been sufficiently in demand to warrant a black market involving the exchange of hard currency.
In more recent years the Asian malware focus has expanded to encompass mundane Distributed Denial of Service and other hacker tools, Browser Helper Objects and browser hijackers, botnets with remote Command & Control, and rootkits. Interestingly, the increase in mobile threats, e.g. for the Android platform, is believed to be fuelled by authors in Russia and China.
Dave the Malware Author
 Despite the Terminator series and other sci-fi films from Hollywood, code which control machines, whether it is good or nasty, is well and truly written by humans rather than automatons or some abstract force of evil. This fact raises interesting and important questions about malware authorship and the reasons for it. There is general agreement and plenty of statistics about the volume and sources of burgeoning malware, but perhaps an insufficiently clear understanding of and explanation for the phenomenon. Of course much of the malware is written for monetary gain, however, why then are the contributions to the threat landscape so heavily influenced by geography?
Despite the Terminator series and other sci-fi films from Hollywood, code which control machines, whether it is good or nasty, is well and truly written by humans rather than automatons or some abstract force of evil. This fact raises interesting and important questions about malware authorship and the reasons for it. There is general agreement and plenty of statistics about the volume and sources of burgeoning malware, but perhaps an insufficiently clear understanding of and explanation for the phenomenon. Of course much of the malware is written for monetary gain, however, why then are the contributions to the threat landscape so heavily influenced by geography?
Dotcom Boom

Since 2007 the number of internet users in China and Russia has more than doubled to over 420 million (>31% of the population) and 59 million (>42% of the population) users respectively. This dramatic increase in a short timeframe implies a massive investment in internet infrastructure, both network connectivity and PC hardware, and a phenomenal increase in computer literacy.
Of course, these infrastructure improvements provide the means and viability for malware production since it is now increasingly possible to create and distribute malware globally, and reap the profits. Importantly, the increasing number of internet users also provides a growing local “market” for malware, i.e. there are now many more potential victims to exploit.
Internet penetration is increasing in other parts of Asia such as India and the “Tiger Cub” nations of Indonesia, Malaysia, Philippines and Thailand. It remains to be seen if the increase in the number of internet users in these countries leads to a concomitant rise in the number of malware emanating from them.

Legal Aid
Writing and distributing malware, essentially a form of common thievery in the modern day and potentially very damaging, is or ought to be against the law. Therefore there are likely to be legal aspects, with local flavours, to the geographical trend in malware.
The cyber crime laws in the so-called “malware hubs” are considered relatively lax or poorly enforced, due to various technical and administrative reasons . The process of strengthening cyber crime laws is certainly progressing, albeit at a viscous pace according to some. It is indeed surprising that even Japan, with its government departments dedicated to monitoring and fighting cyber crime [e.g. Office of IT Security Policy, Ministry of Economy, Trade and Industry], has supposedly only just recently made malware writing illegal.
It is possible that many of the victims of modern malware have been in countries other than the alleged malware hubs. This leads to issues of international jurisdiction. Local law enforcement agencies in victim countries would struggle to prosecute overseas perpetrators, and the law enforcement agencies in possible malware hub countries may not have sufficient incentive to investigate cyber crime and prosecute offenders when the victims are outside their remit.
 Reports on the arrests of cyber criminals in China and elsewhere in Asia have made the press and blogs. There have also been coordinated international law enforcement efforts to arrest and prosecute cyber criminals which have shown positive, albeit probably ephemeral, results . No doubt, there are still too many loopholes for malware writers to function with impunity, and a course correction, replete with international treaties, is warranted.
Reports on the arrests of cyber criminals in China and elsewhere in Asia have made the press and blogs. There have also been coordinated international law enforcement efforts to arrest and prosecute cyber criminals which have shown positive, albeit probably ephemeral, results . No doubt, there are still too many loopholes for malware writers to function with impunity, and a course correction, replete with international treaties, is warranted.
SOD’s Law?
Iniquitous growth, inadequate job and education opportunities and denial of basic human freedoms are leading to growing radicalization of the youth, intolerance and extremism.
We have no choice but to meet these challenges head-on.
– Shree Manmohan Singh, Honourable Prime Minister of India, in his address to the UN General Assembly, 24th September 2011
Human greed has no nationality. However, the sheer scale of the migration towards following a dubious path in the malware hubs suggests possible institutional concerns. Inadequate overall legislation notwithstanding, one would assume there are other core reasons to forsake Confucian values. These core reasons constitute a “Seeds of Discontent” hypothesis.
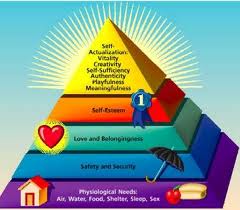 Money, the universal means of exchange in economics, forms the rationale for malware creation and distribution, and, perforce, economics deals with the fundamentals of social welfare. Deficiencies in social welfare sow the seeds of discontent, sometimes tending to result in undesirable activities, including malware authorship, as there is a scramble to satisfy Maslow’s hierarchy of needs when resources are scarce. If indeed the core issues derive from economic indicators, then we ought to spend some time investigating them in laymen’s terms.
Money, the universal means of exchange in economics, forms the rationale for malware creation and distribution, and, perforce, economics deals with the fundamentals of social welfare. Deficiencies in social welfare sow the seeds of discontent, sometimes tending to result in undesirable activities, including malware authorship, as there is a scramble to satisfy Maslow’s hierarchy of needs when resources are scarce. If indeed the core issues derive from economic indicators, then we ought to spend some time investigating them in laymen’s terms.
A few of the global malware hubs went through periods of extreme economic restructuring based on Freidmanesque rather than Keynesian principles throughout the 1990s [Naomi Klein, “The Shock Doctrine”]. The extent of the economic volte-face in a couple of cases was from chalk to cheese, or vice-versa depending on one’s perspective. It is alleged that one of the eventual key consequences of these economic restructuring programmes was the loss of jobs and livelihoods for large swathes of people.
 Since the 1990s several instances of downturns in the globalised economy, including the “credit crunch” which began in 2008, could have piqued the general sense of consternation and despair. A marked increase in criminal activity, including the establishment of mafia gangs, may well have been a reaction to these unfortunate scenarios. High-tech criminal activity, in the form of cyber crime, comes to the fore when the perpetrators happen to be adept university graduates who are unable to find suitable employment in the legitimate IT sector.
Since the 1990s several instances of downturns in the globalised economy, including the “credit crunch” which began in 2008, could have piqued the general sense of consternation and despair. A marked increase in criminal activity, including the establishment of mafia gangs, may well have been a reaction to these unfortunate scenarios. High-tech criminal activity, in the form of cyber crime, comes to the fore when the perpetrators happen to be adept university graduates who are unable to find suitable employment in the legitimate IT sector.
Let us consider Russia, a Eurasian country, as a simple case study since candid information is freely available. Russia’s unemployment rate has averaged around 8.4% with a high of 14.6% in February, 1999. Unemployment, and possibly other social welfare, benefits are reportedly far better on paper than they are in reality, and Russia’s inflation rate, double-digit on average over recent years, can be considered high. Mr. Putin, Russia’s former president and a firm candidate to return to the Kremlin, envisages an increase of average wages and salaries by 50% to US $1,000 by 2014. An ambitious $1,000 in 3 years time fades, nay wilts, in comparison to a guaranteed monthly salary of $5,000 currently offered to write custom packers to wrap malware. Therefore the incentive for many young Russian graduates, especially those with an IT background, to contribute to the “malware industry” appears particularly strong.
 It is a reasonable assumption that most people who are able to comfortably satisfy Maslow’s pyramid through legitimate means are unlikely to be tempted by malware writing, given the moral and legal implications. The corollary of this, however, would be that once a person has been “turned”, he/she might have crossed “the point of no return”, i.e. succumbed to the malaise. Nevertheless the emphasis ought to be on dissuading the next generations of youth from partaking in the malware industry. This will be no easy task given the economic policy changes that might be required under difficult globalised economic conditions.
It is a reasonable assumption that most people who are able to comfortably satisfy Maslow’s pyramid through legitimate means are unlikely to be tempted by malware writing, given the moral and legal implications. The corollary of this, however, would be that once a person has been “turned”, he/she might have crossed “the point of no return”, i.e. succumbed to the malaise. Nevertheless the emphasis ought to be on dissuading the next generations of youth from partaking in the malware industry. This will be no easy task given the economic policy changes that might be required under difficult globalised economic conditions.
One would wager an educated guess, indeed a lot more, that the current trend of financially motivated malware, in increasing numbers, out of Asia and elsewhere will continue unabated. The role of the IT security industry is to continue to protect customers against malware attacks, and the law enforcement agencies are expected to prosecute the perpetrators. However, for the longer term, it could be the global policy-makers who hold the key to attempt to resolve the underlying issues to stem the gushing flow of malware.
The End
Images courtesy of:
dave-broos.blogspot.com
squidoo.com
medicmagic.net
gyanvihar.org
webend.in
tattoodonkey.com
blog.envole.net
microreviews.org
nwgasbdc.blogspot.com
Samir Mody
Senior Manager, K7TCL
If you wish to subscribe to our blog, please add the URL provided below to your blog reader:
https://labs.k7computing.com/feed/