One of the items on a malware authors checklist while distributing malicious code is to make sure that their malware remains undetected, for as long as possible. Scanning their creation using a multiple Anti-Virus scanning system is one among the many techniques in their arsenal which ensures just that.
Although time consuming and resource intensive, the malware author installs various Anti-Virus software and keeps them updated. The malicious files are scanned on this system before they are distributed to the victim.
For malware authors/script kiddies who can’t afford to build such a system, there are underground sites which mimic genuine online file/URL scanning services. A significant difference being, these underground sites in exchange for money, promise not to distribute the scanned files to the Anti-Virus vendors. Given below are screen shots of two such sites:
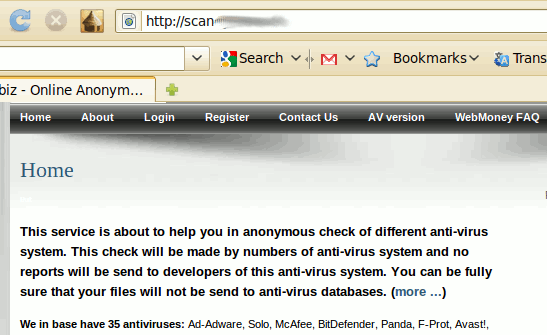
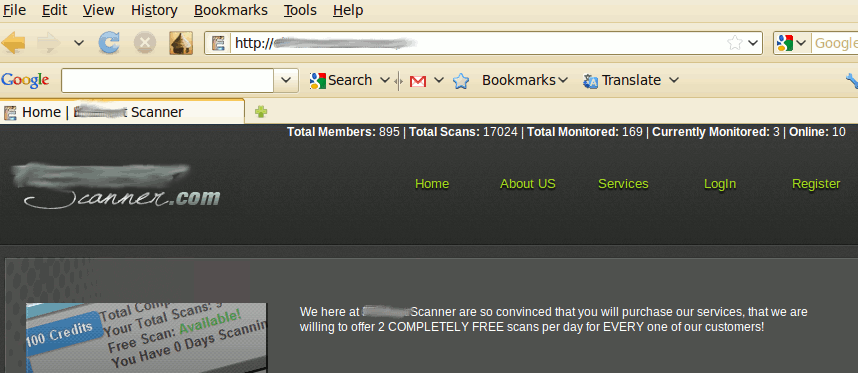
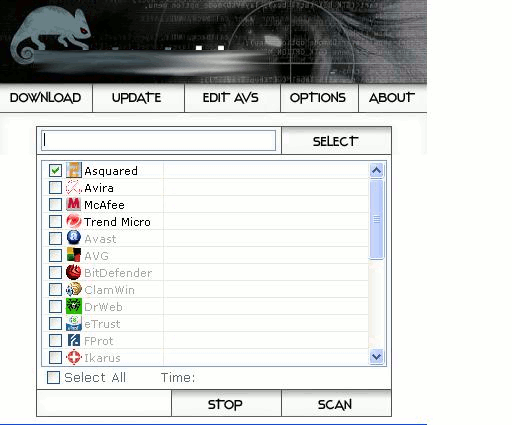
Then there are tools which incorporate multiple scanners & are distributed for free. Given below is a screen shot of one such tool:
If their malicious code is detected by the Anti-Virus vendors during the initial stage of the attack, the malware authors are quick to change their binary.
While traditional checksum based detections alone might be ineffective against such files, a combination of several detection methods, which include a behaviour based approach will prove far more effective.
R.V Shyam Charan
K7 TCL
If you wish to subscribe to our blog, please add the URL provided below to your blog reader:
https://labs.k7computing.com/feed/







