It is the era of Ransomware and Halloween is just around the corner. We have witnessed yet another ransomware outbreak for the calendar year, lashing eastern European countries and Russia.
This ransomware dubbed “BadRabbit” hit systems in Ukraine, Russia, Bulgaria, Turkey, Germany and even Japan and South Korea, as per news agency reports. Russia and Ukraine have been the worst hit countries, with Kiev Metro and the Odessa airport in the Ukraine being early casualties. An official statement to this effect was released by CERT Ukraine.
It appears the initial outbreak for this ransomware was via drive-by downloads from hacked news agency sites in Russia. The dropper ransomware was served up as an “update for Flash Player installer”, duly named install_flash_player.exe (FBBDC39AF1139AEBBA4DA004475E8839). Ah, social engineering does still work a treat, doesn’t it?
The infected sites contained a script which resolved to the following URL:
h**p://1dnscontrol[.]com/flash_install
The domain 1dnscontrol[.]com was been taken down pretty quickly.
BadRabbit, similar to WannaCry and NotPetya, in the sense that it is multi-component, using several complimentary executable files to infect the user machine. There are even code (none of them employ any form of code obfuscation) and filename similarities between these families. In BadRabbit and NotPetya the main infection modules are actually DLL files but have a ‘.dat’ extension.
The main dropper masquerading as a Flash Player installer must be run with admin privileges since its components are to be written to the C:\Windows directory as follows:
- c:\windows\infpub.dat -> Main encryption and infection module : DLL (2FE32D2A6BFC72D215496B055E5A53AD)
- c:\windows\cscc.dat -> Driver file from diskcryptor.net : SYS (B4E6D97DAFD9224ED9A547D52C26CE02)
- c:\windows\dispci.exe -> Part of the disk encryption module and responsible for the MBR infection : EXE (B14D8FAF7F0CBCFAD051CEFE5F39645F)
- c:\Readme.txt -> Text file with information about the encrypted files and how to get them back
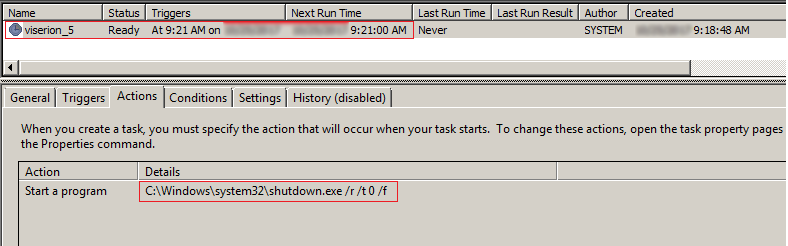
Scheduled tasks are created to initiate other modules of the infection and to reboot the system. Unusually, the system reboots twice during the entire infection cycle.
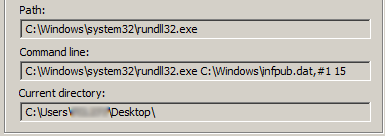
Once the main dropper is executed it drops a DLL file which is the file encryption module. It gets initiated using rundll32.exe as shown below:
The argument passed to the infpub.dat denotes that the first export function is referenced by ordinal number followed by the number 15, which is the time until reboot.
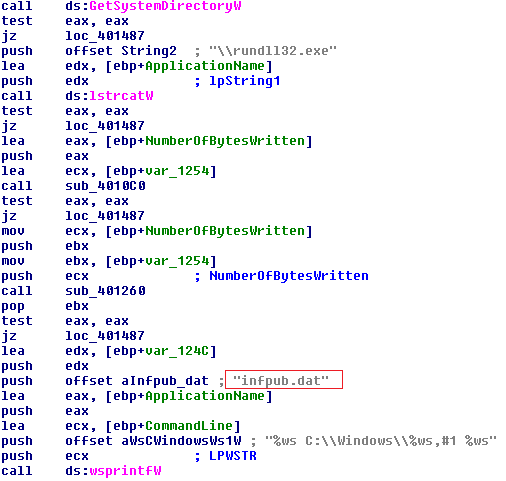
As shown in the code snippet below, the main dropper creates infpub.dat in the Windows directory and then calls CreateProcessW to invoke it. Once the DLL is initiated the process of encryption begins.
infpub.dat is in charge of the following:
- User file encryption
- Adding scheduled tasks to reboot the machine and initiate the next module
- Looking for infection targets on the local network
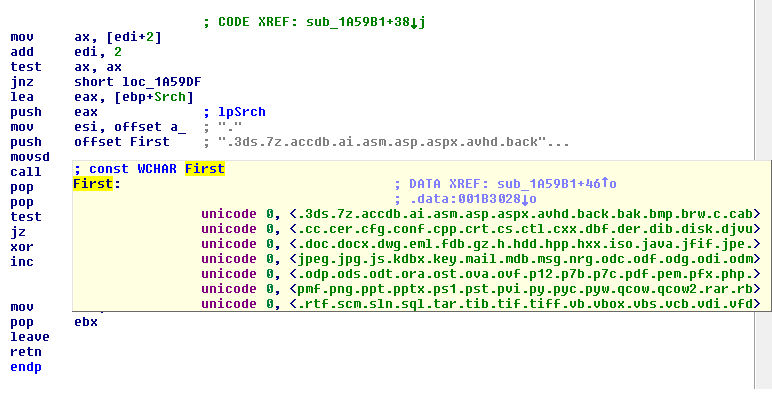
For encryption the ransomware looks for specific extensions:
3ds 7z accdb ai asm asp aspx avhd back bak bmp brw c cab cc cer cfg conf cpp crt cs ctl cxx dbf der dib disk djvu doc docx dwg eml fdb gz h hdd hpp hxx iso java jfif jpe jpeg jpg js kdbx key mail mdb msg nrg odc odf odg odi odm odp ods odt ora ost ova ovf p12 p7b p7c pdf pem pfx php pmf png ppt pptx ps1 pst pvi py pyc pyw qcow qcow2 rar rb rtf scm sln sql tar tib tif tiff vb vbox vbs vcb vdi vfd vhd vhdx vmc vmdk vmsd vmtm vmx vsdx vsv work xls xlsx xml xvd zip
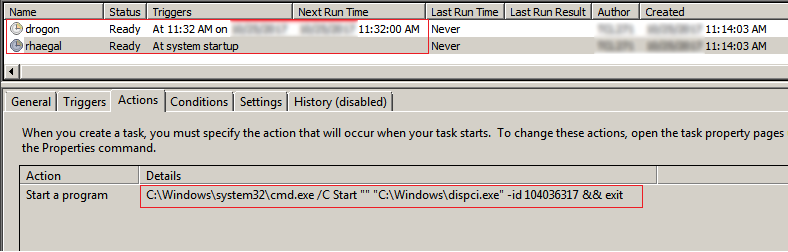
One of the scheduled tasks is to reboot the computer at an elapsed time (NB: this can vary depending on the number and size of files that are to be encrypted) mentioned by the main module. The other is to initiate the diskcrypter executable named as dispci.exe:
There are several references to the “Game of Thrones” TV series, e.g. the scheduled tasks are called “drogon”, “Rhaegal” and “viserion”, and the diskcryptor exe is called “GrayWorm” in the version strings in the resources.
The ransom note is dropped in c:\Readme.txt informing the user of the infection and how the files cannot be retrieved without the ransomware author’s help.
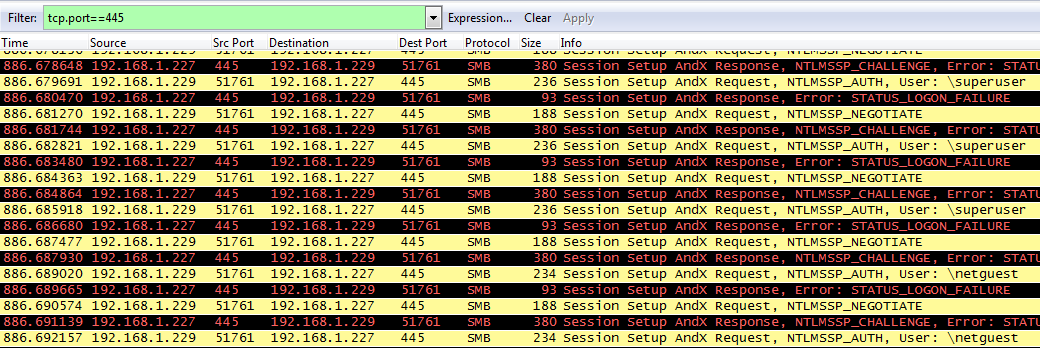
Once the encryption is done. The ransomware goes on to scan the LAN for possible infection targets. This is done by sending out requests to look for SMB shares. It uses the Mimikatz tool to scan for any traces of user credentials in memory. The ransomware then uses a list of hardcoded usernames and passwords to bruteforce into any available machine on the LAN.
This list is made up of weak and frequently-used passwords. For better insight on choosing strong passwords one can refer to one of our earlier blog posts.
Shown above is a network capture of the attempted spread to SMB shares. Once the ransomware has bruteforced into any network machine it tries to place the DLL component infpub.dat on those systems and initiates that ransomware module using Service Control Manager.
Once this is done the system gets rebooted and the diskcryptor module dispci.exe takes over. The other file dropped, cscc.dat, is actually a driver that can perform disk encryption. Note, however, that it is a legitimate file. At this point in time another schedule task gets added which is also for a reboot.
The time for triggering this task is updated several times before the scheduled task is finally executed.
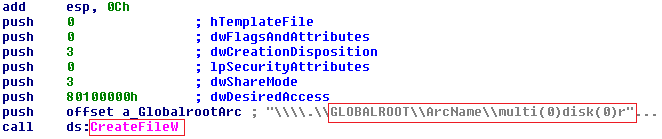
Before going for the reboot the ransomware performs one final task which is to overwrite the MBR of the system. It uses CreateFileW on GLOBALROOT\ArcName\multi(0)disk(0)rdisk(0)partition(1) to get a handle to the MBR.
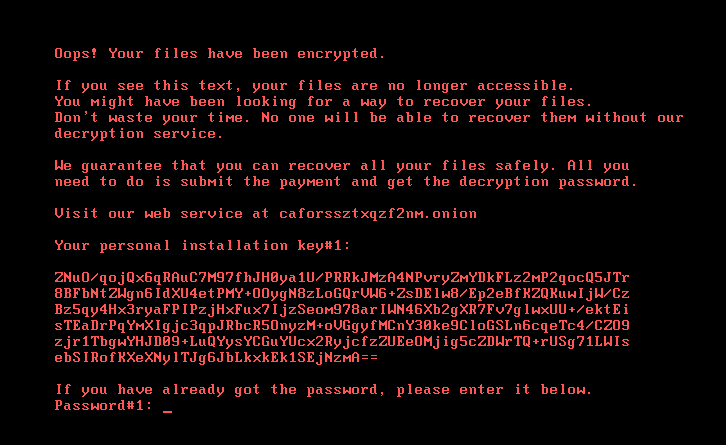
Once this is done the system reboots and displays the following message informing the user that they have wasted a lot of time trying to decrypt the files by other means.
The user is forced to retrieve their files only by paying the ransom within the timeframe given by the ransomware author. However, we at K7 Threat Control Lab urge users to refrain from paying the ransom for several reasons, including:
- Payment of the ransom increases the profitability of ransomware, thus fueling further attacks
- There is no guarantee that paying the ransom would result in getting your files back
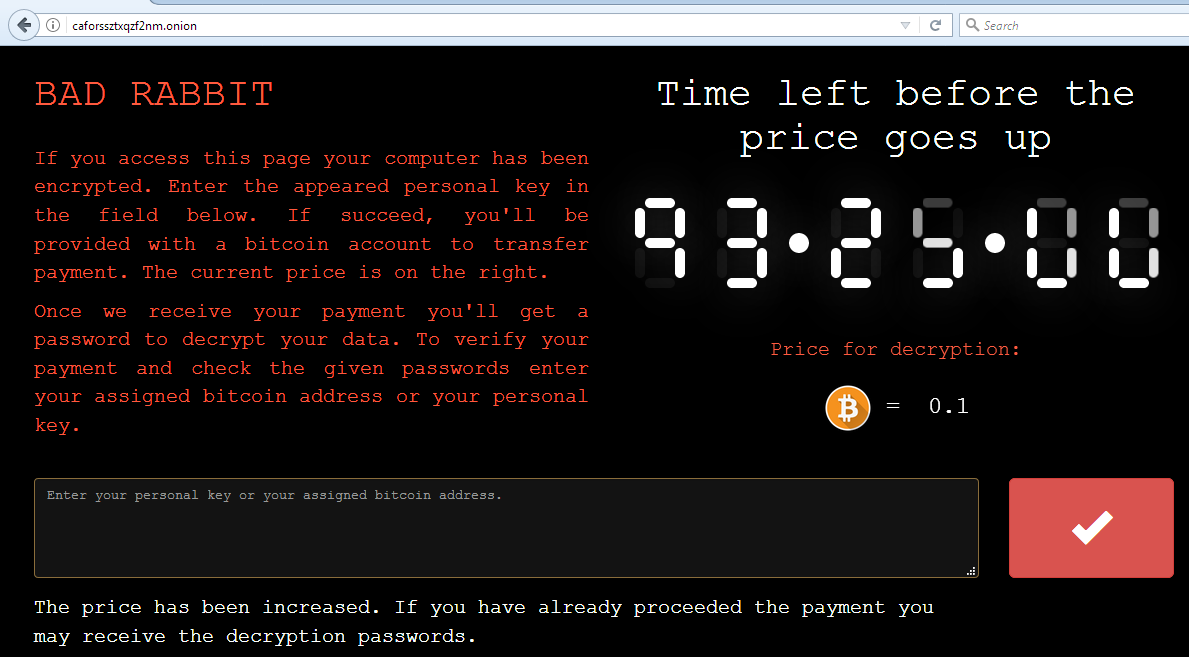
Shown below is the onion site that displays the custom message for each user depending on their personal installation key#1. The ransom starts with 0.05 bitcoins and keeps increasing with time.
The various malicious components of the ransomware are detected by K7 as follows:
install_flash_player.exe - Trojan ( 0051a3031 ) dispci.exe - Trojan ( 0051a3031 ) infpub.dat - Trojan ( 0051a2c11 ) 16605a4a29a101208457c47ebfde788487be788d – mimikatz 32-bit module - Riskware ( 0051a31b1 ) 413eba3973a15c1a6429d9f170f3e8287f98c21c - mimikatz 64-bit module - Trojan ( 0051a5241 )
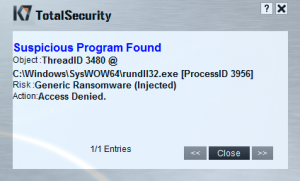
Apart from this the ransomware’s attempt to encrypt files is completely blocked by K7’s Ransomware Protection feature:
Kaarthik RM, Senior Threat Researcher, K7TCL Lokesh J, Threat Researcher, K7TCL Gladis Brinda R, Threat Researcher, K7TCL Rajesh Kumar R, Threat Researcher, K7TCL Mary Muthu Fransisca, Threat Researcher, K7TCL