The ongoing Coronavirus outbreak (COVID-19), classified as a pandemic, started in Wuhan, Hubei, China towards the end of 2019 and has since then, spread to many countries. Every government is taking precautionary measures against the spread of this new strain, and have also issued several advisory notices and continues to do so on a regular basis to protect their people.
There are different ways in which this virus is transmitted to humans and to protect themselves people are desperate to read any article issued about Coronavirus protection and prevention without realizing that this could be a threat in its own way; as hackers have started exploiting this scare that is going around and have started sending out malware in seemingly benign looking emails.
We have compiled a list of few benign looking emails that spread dangerous malware in the victim’s system or an enterprise. Critical and confidential information could be leaked because of these, if they are targeting government and military organizations, which could then prove to be a threat to the country. These malware could also steal sensitive information, drop other malware, etc.
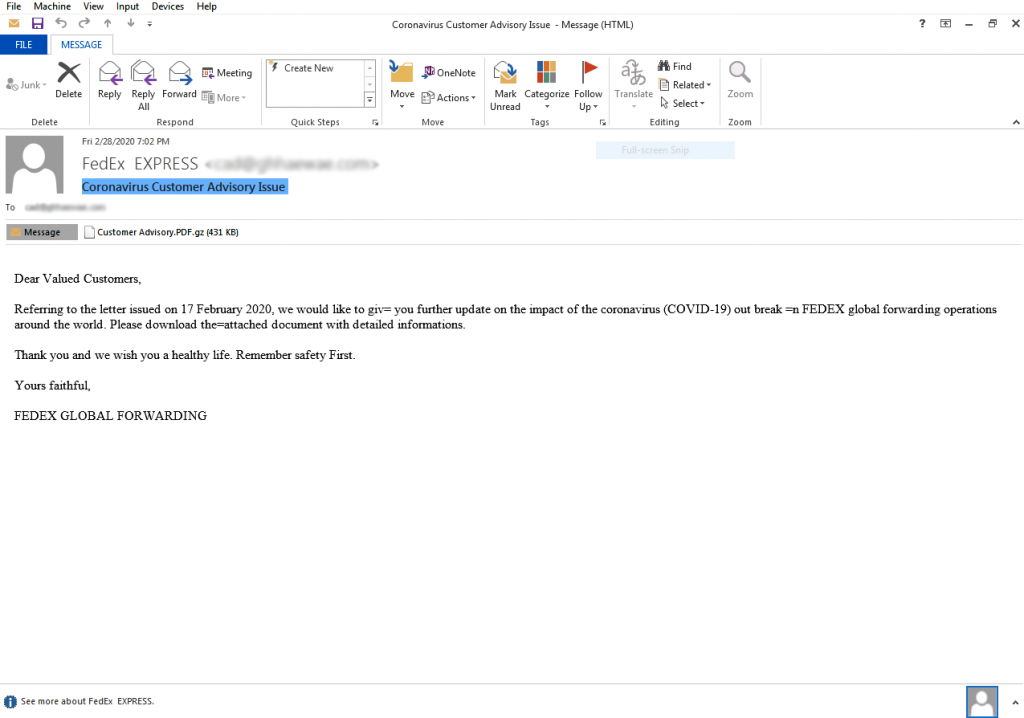
Figure 1, shows a benign looking email sent from FedEx Express, a cargo online based in the United States, issuing an advisory notice to its customers. This attachment contains a malicious compressed zip file having a PDF document in it. This drops the Lokibot malware which is capable of collecting user credentials from browser and email clients.
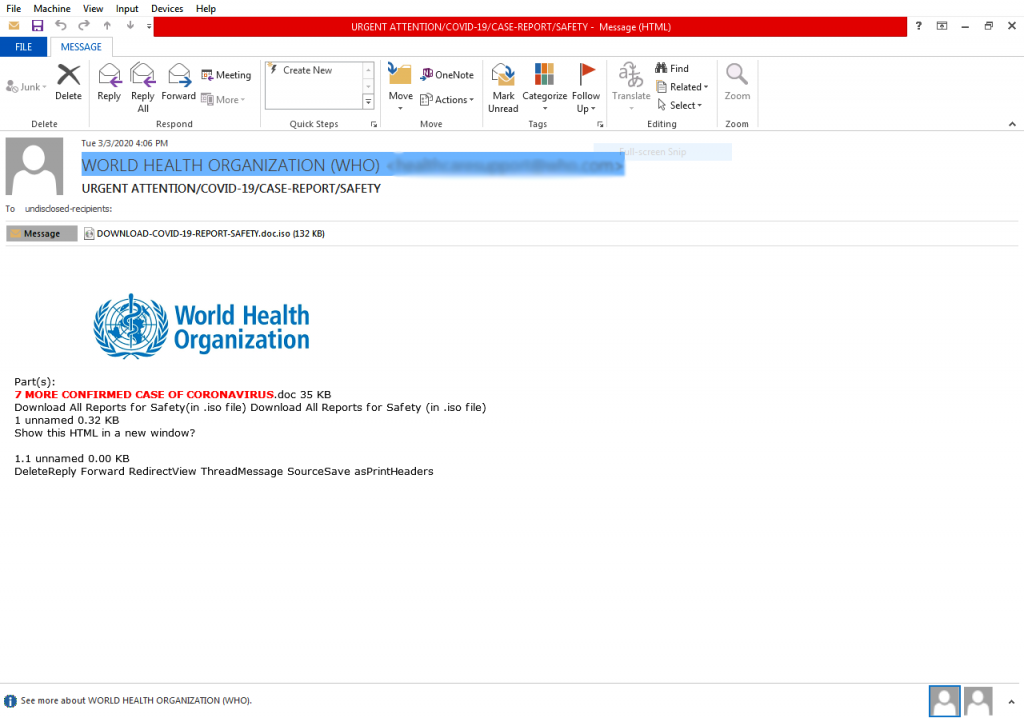
Figure 2, is another email which also drops Lokibot malware. The email is supposedly from the World Health Organization (WHO), having an attachment in “.iso” format, containing a “.doc” file. An iso reader is required to run the malware. Lokibot being an info stealer steals FTP credentials and passwords stored in browsers.
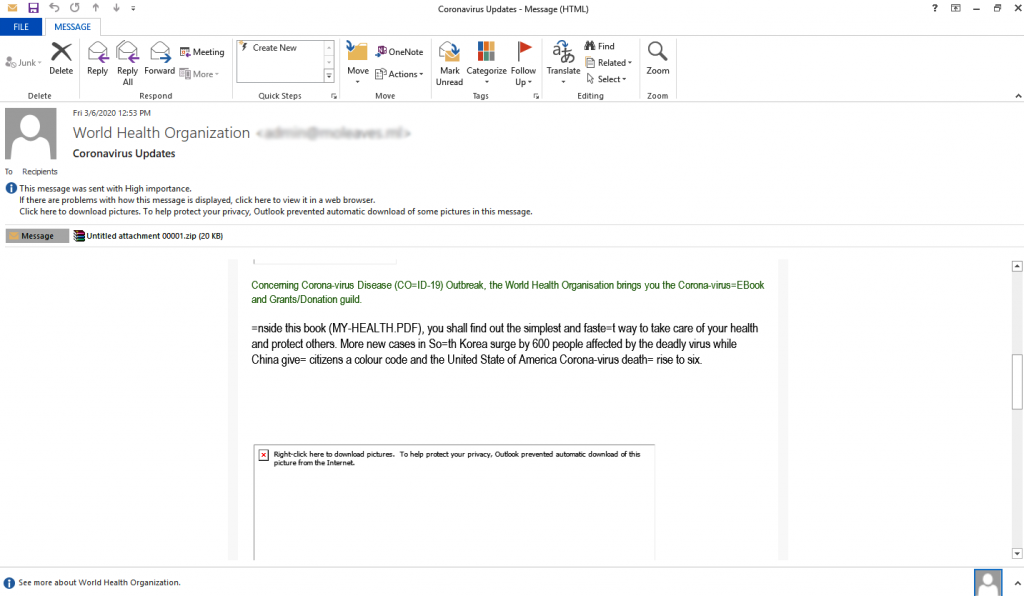
Figure 3, is again an email from the World Health Organization (WHO), having an unnamed zip file as the attachment with a PDF file in it, with the subject “Coronavirus Updates”. However, it is actually a malicious exe file. The malware is the Formbook malware which is a spyware. It injects itself in to various browsers like Firefox, IE, etc. and monitors clipboard, captures screenshots, etc.
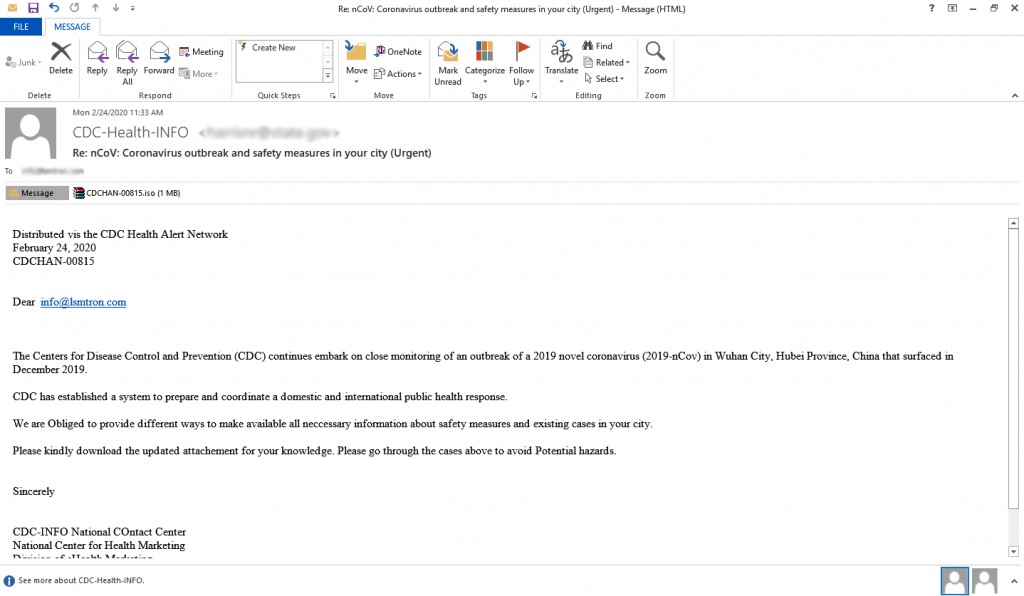
Figure 4, is a spam mail from Centers for Disease Control and Prevention (CDC) in the United States. The subject line increases the urgency of the email, which is a signal to remain cautious. The attachment contains the infamous Remcos RAT and comes attached in “.iso” format. This Trojan sends system info to the C&C and based on the commands received from it can act as a downloader, a keylogger, get the status of a running process, upload files to a desired location, query the network, etc.
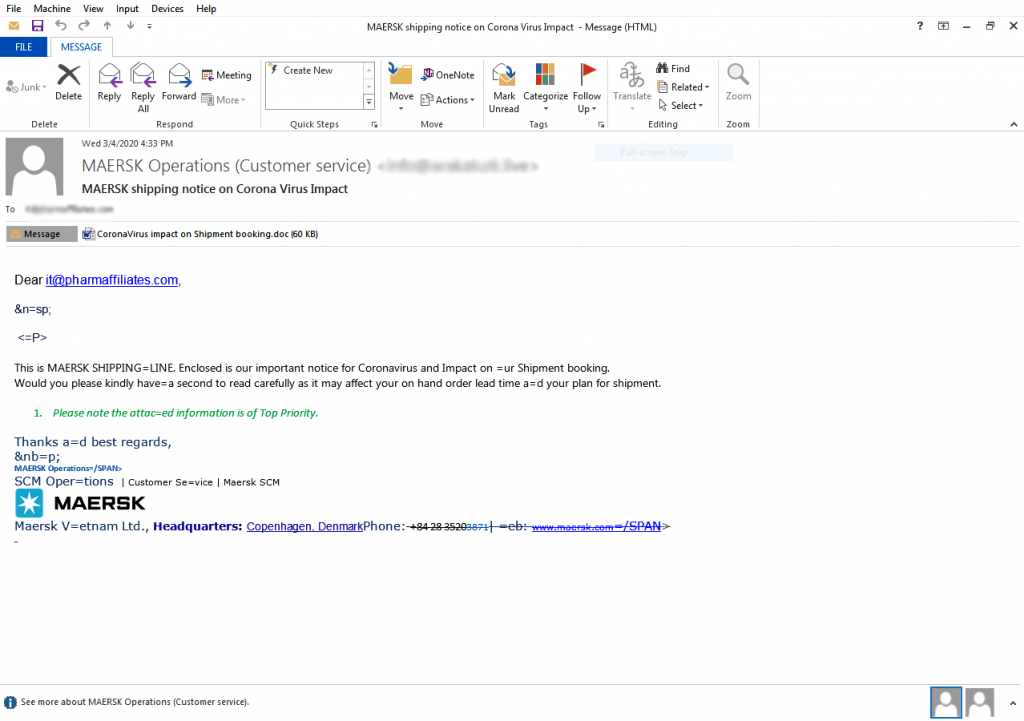
Figure 5, is a spam email from Maersk, the largest container ship and supply vessel operator, sent to their clients. The email comes with an attached file “CoronaVirus Impact on Shipment booking.doc”. This is actually a macro malware. It drops Emotet, a banking Trojan on the victim’s system. It steals banking credentials, drops other malware such as Trickbot banking Trojan, Ryuk ransomware based on commands from its C&C, etc.
There have also been targeted attacks by a few infamous APT groups who also use emails to target their victims. Here, we would be looking into how the APT36 group aka Transparent Tribe is using this time to infect and scare the hell out of everybody.
A detailed blog regarding the nuances about this has been written by one of our researchers, just that this time around the message in the initial vector is different, which is now related to the Coronavirus scare as shown in Figure 6. The payload dropped was still Crimson RAT, a Remote Access Trojan which provides an adversary unauthorized access to a victim’s device over a network.
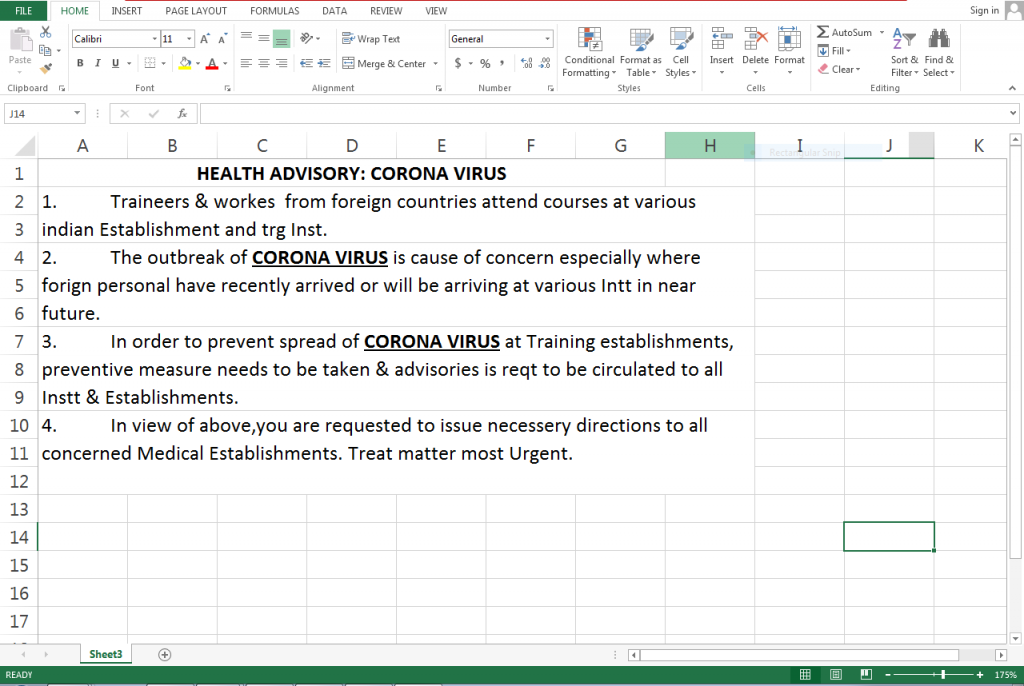
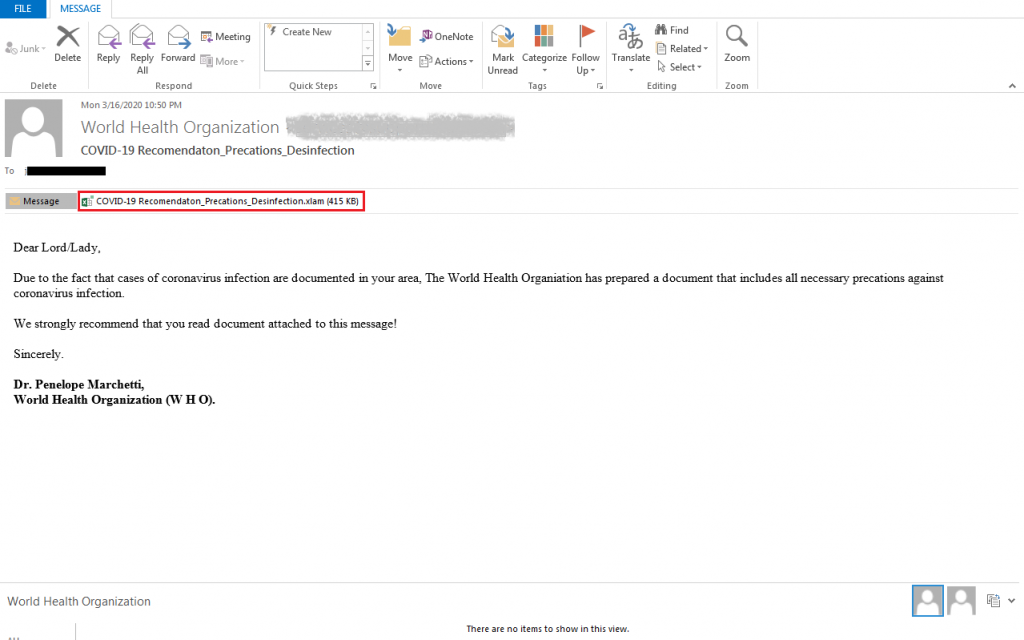
Another targeted attack is shown in Figure 7. It is a spam email apparently sent from the World Health Organization (WHO), having the subject “COVID-19 Recomendation_Precations_Desinfection” with an attached excel document. We believe that this is used by the Gorgon APT group to spread malware.
We at K7 have detection for all of the above mentioned cases.
Few precautionary measures that can be taken to protect oneself from such scams:
- Do not open emails from unknown sources
- Check the senders’ and receivers’ email id to confirm if it is from the said originator
- Check for unwanted characters in the email content
- Do not get carried away by hackers who increase the priority of the emails with URGENT/ATTENTION/TOP PRIORITY etc., in the subject/body and highlighting content in the body of the email
- Check for the sender’s name in the email signature
- Check for hyperlinked text and see if it is a legitimate one by only hovering around the link
- Check for sentence phrasing and grammatical mistakes
- Check if the attachments are properly named
- Check for the images, if any, in the email are properly attached
- Check for the credibility of the undersigned
- Do not enable macros by default
- Ensure the OS and all applications are updated and patched for the latest vulnerabilities
- Keep your security product updated and use a reputable AV product like K7 Total Security