Work From Home (WFH) is not a new concept. Employees across the globe and domains have been taking care of assigned tasks from home in case of any emergency or support. The WFH setups were mostly configured securely by the Information Technology (IT) department of each organization.
With India suddenly going into lockdown from March 2020 due to COVID-19, employees of most of the organizations here had to WFH to ensure work was getting done on time and thereby doing their part in boosting the Indian economy and are still continuing to do so. This WFH force is a huge percentage of the employees in comparison to the numbers before pandemic times. Also, many organizations were not prepared for this sudden and immediate requirement and had to let their employees set up and use their own machines for work, giving adversaries opportunities to gain access to confidential, personal and organizational information.
Adversaries have been observed employing techniques as simple as brute-forcing passwords to finding zero days in day-to-day used applications. In this blog, we will discuss various techniques employed by adversaries to exploit services and applications thereby taking maximum advantage of this current situation.
Remote Access Service
Remote Desktop Protocol (RDP) and Virtual Network Computing (VNC) are two of the most utilized services for remote graphical access globally. With organizations requesting their employees to WFH, most of the employees have been given remote access to their work machines and production servers through some remote access service.
With this sudden rise in the number of employees working remotely from home, network administrators are more focused on providing fast and smooth connectivity with scant regard for security. Only a few organizations are realising the importance of securing remote connections by adding additional layers of security such as multi factor authentication during setting up of the connection itself.
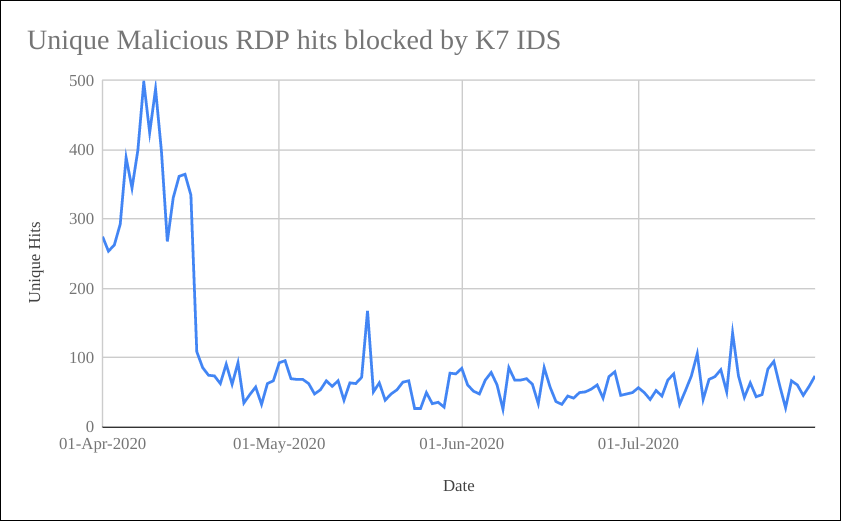
Once everyone started working from home due to the imposed lockdown from late March, we have observed a spike in network packets blocked by K7 Intrusion Detection System (IDS) rules, showing that attackers increased their attempts to abuse RDP using known vulnerabilities and password brute-forcing.
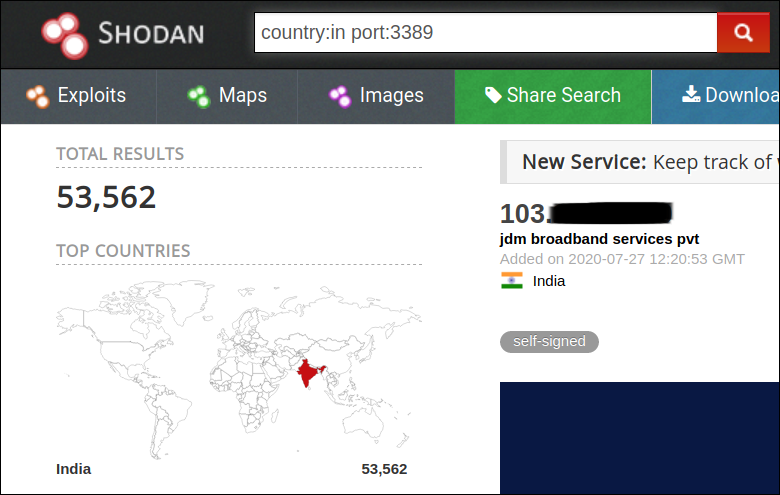
Using Shodan, we observed that a large number of machines were still using default ports for RDP (Port: 3389) and for VNC (Port: 5800), thereby becoming the frontline victims to be exploited easily.
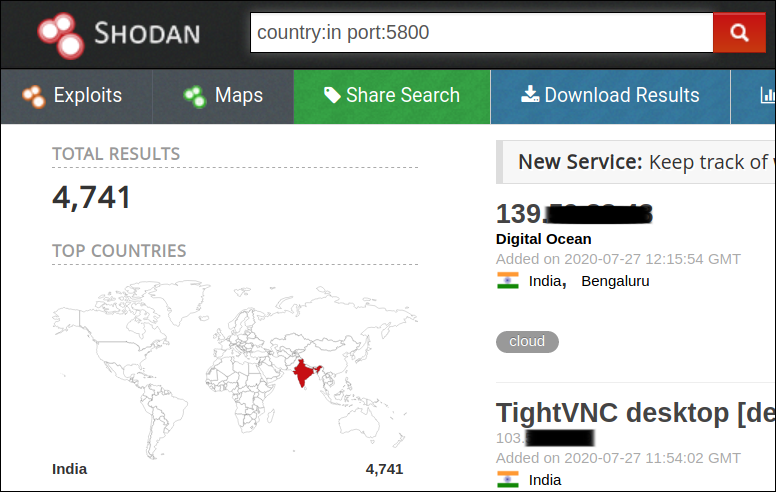
Out of these ~58000 machines, there’s a good number of machines with weak or no security mechanism implemented.
Organizations have been reportedly incurring huge financial and data losses due to data leakage or ransomware attacks. Forensic analysis of these attacks has shown insecure RDP configuration as an entry point for the attackers into the victim’s network. So it is crucial to add multiple layers of security for RDP connections or any other remote access services.
A major weakness that has been observed in many of the attacks is the service misconfiguration that occurs as a result of setting passwords that can be easily brute-forced while trying to secure remote access services.
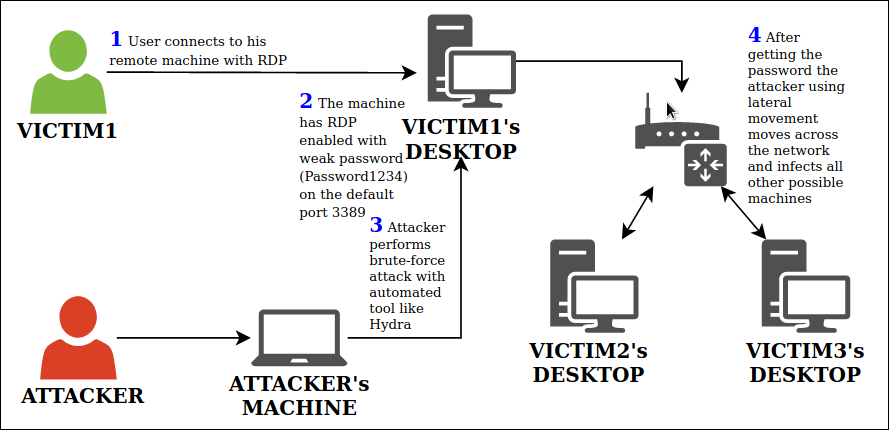
Figure 4 depicts a basic kill chain that we have observed during multiple attacks, on enterprise networks, exploiting RDP. The point of entry to the network is usually the system using the default RDP port (3398) and weak credentials (e.g.: Password1234), thereby exposing the RDP service to the Internet. The attacker can use a brute-force attack with automated tools like Hydra to easily find the password and break into the system.
Once the attacker gets into a system in the network, they move across the network through lateral movement and infecting other systems becomes much easier. Adversaries are all the more benefited if there are shared drives in the network with complete read/write access so that they can do extensive damage.
TrickBot, a popular malware which first emerged in 2016 as a Banking Trojan, has been constantly evolving. Since emerging in 2016, it has extended its functionalities to include credentials stealing, delivering other malware such as Emotet and much more.
A new variant of Trickbot has been identified which includes a new module called rdpScanDLL. This module is built for brute-forcing RDP accounts.
The kill chain for this malware is similar to Figure 4. The malware has a predefined set of IP addresses which are being targeted instead of “spray-and-pray” technique.
SSH
After remote desktop services, the most utilized remote access service during the lockdown is SSH, used mainly to administer Linux based servers.
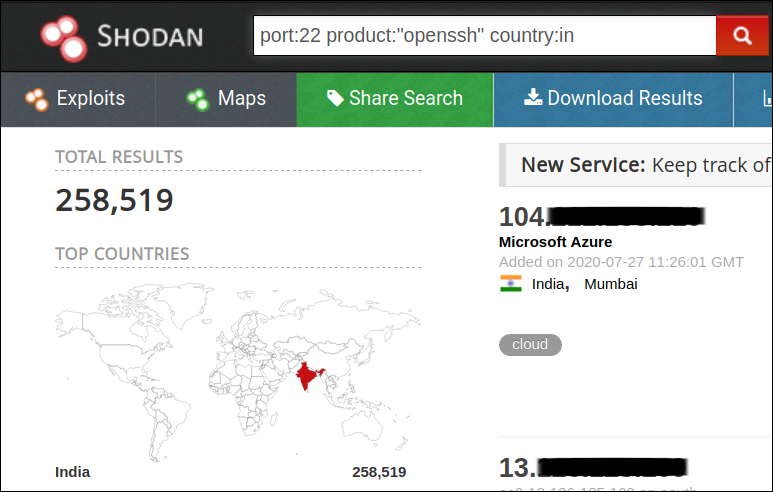
Among different SSH suites, Openssh and Dropbear are the popular ones that are being used. From Shodan, we were able to identify more than 18 million machines running both these services and around 1/3rd of these machines were running vulnerable versions of these suites. India has around 275000 machines exposing SSH ports to the Internet.
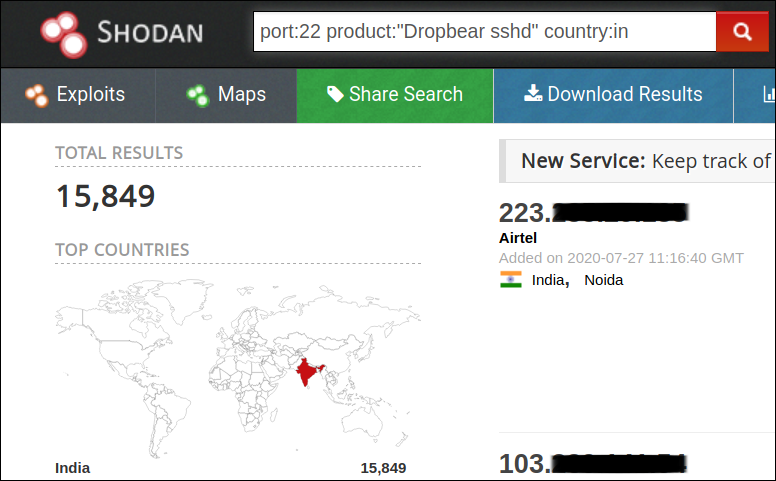
Apart from the service vulnerabilities, there are possibilities to misconfigure SSH allowing adversaries to easily exploit either by simple brute-forcing or through leaked credentials. This can only be prevented by appropriate SSH configuration and implementing multi-level security.
In May 2020, multiple supercomputers across Europe like the UK’s National Supercomputing Service ARCHER were targeted by crypto-mining attacks which were done with the help of leaked credentials. After the attack, the ARCHER system was brought down and the security team implemented 2FA.
In the same month, a new variant of Kaiji malware which is said to be the work of Chinese developers targeted IoT devices through SSH brute-force for passwords and launched DDoS attacks.
Figure 7 depicts a basic kill chain that we have observed during multiple attacks exploiting SSH. When systems running SSH on default port (22) are identified on the Internet, the attacker can run a brute-force attack to identify the password and compromise the system (Figure 7 – 2b). Due to weak credentials such as Password@123, it becomes easier for the attacker to break into the system and continue with lateral movement in the network.
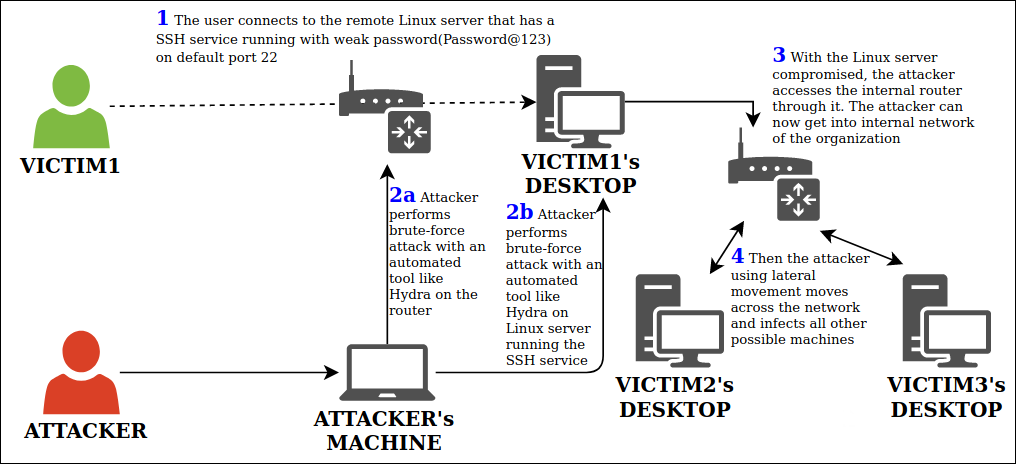
Here, the router has been exposed to the internet directly, making it easy for attackers to enter the network. And if the router has been configured with default credentials, it makes it all the more easier for the attacker to run a dictionary attack to gain access to the corporate network (Figure 7 – 2a) and also easily identify all the systems that are connected to this router.
Routers
There’s no doubt that routers are a gateway to the Internet, and are also the most ignored when it comes to security especially in a non-enterprise environment. With the increase in the number of remote workers, the importance of securing routers also has increased exponentially.
The vulnerabilities that are being exploited in routers are increasing day by day and most of these are usually for simple issues like improper configuration. Adversaries exploit service misconfiguration to take control of the device and gain access to the network.
For this discussion, let’s turn our attention towards the two most deployed routers – D-Link and Netgear.
D-Link
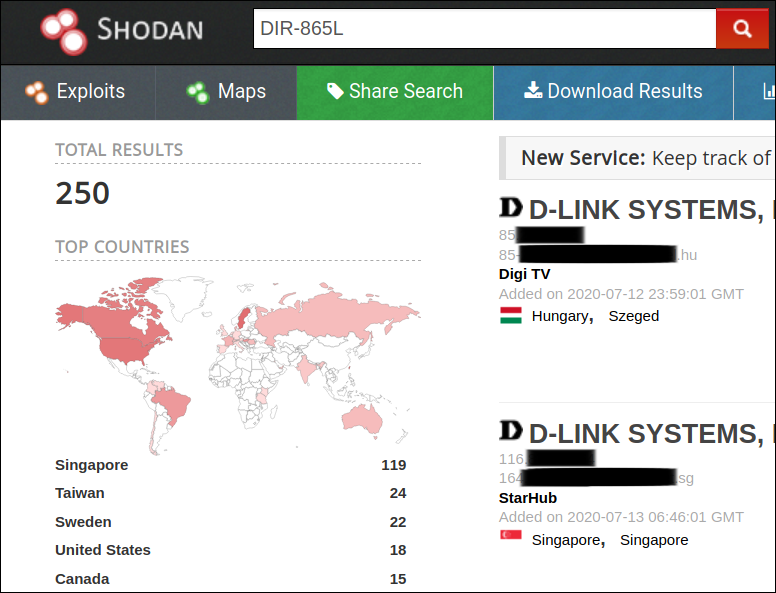
In June 2020, six critical vulnerabilities had been identified in DIR-865L Wireless Router. This router was introduced during 2013 and D-Link had officially mentioned that these devices have reached End-of-Service (EOS) during Feb 2016. However, even after that they released a patch to address multiple security bugs during 2018.
Using Shodan, we found that, even after End-of-Service (EOS) and multiple vulnerabilities being discovered, around 250 DIR-865L routers are still connected to the Internet as shown in Figure 8.
Netgear
Another popular router is Netgear. It is one of the most used routers.
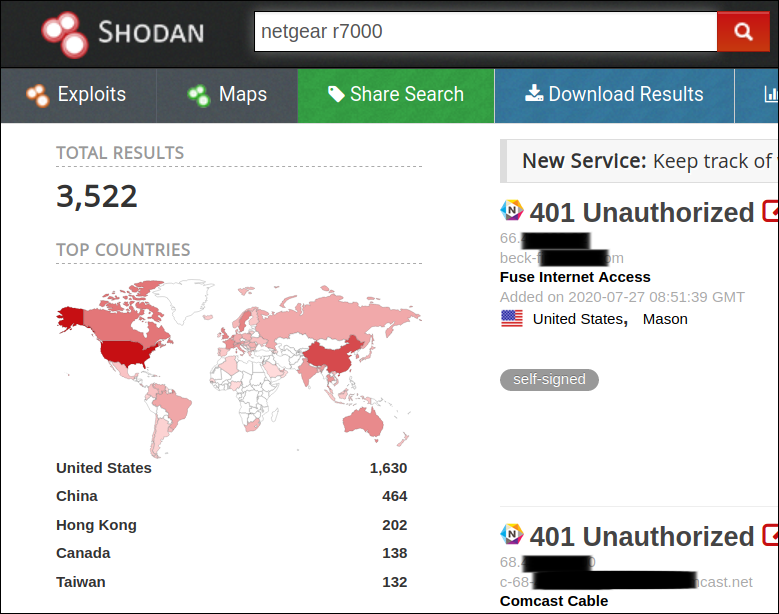
Upto 79 router models in Netgear were identified to be vulnerable to a critical vulnerability that has been identified in the httpd services within each router’s firmware.
With Shodan, we were able to identify that around 40000 of these routers were connected to the Internet directly. Making them all prime targets to be exploited. Out of the 79 routers models R7000 and R8000 were the most used models.
Everybody would be aware of Mirai, a malware that turns Internet connected devices into a network of bots that performs malicious activities. A new Mirai variant has been identified that has exploits for 9 new vulnerabilities focusing on routers and other IoT devices.
Out of the 9 new vulnerabilities, 2 belonged to Comtrend and Netlink routers which were identified to be vulnerable to remote code execution in 2020.
Teleconferencing and Team Collaboration
One other important issue every organization had to address was team collaborations during the lockdown. Applications such as Zoom, Microsoft Teams, Google Meet are few of the most popular ones that were able to solve this problem. But these new applications gave rise to a new set of attack vectors that many organizations had ignored and not considered to be critical. This caused a sudden surge in such applications being exploited. Here are few of the popular vulnerabilities:
Zoom
The most popular teleconferencing application made headlines when Apple removed it from all Mac and iPhone devices due to vulnerabilities. Critical vulnerabilities in Zoom are not new but the sudden increase in its usage has given rise to much more issues and with Zoom claiming it has upto 300 million users it becomes a very serious issue that needs to be addressed.
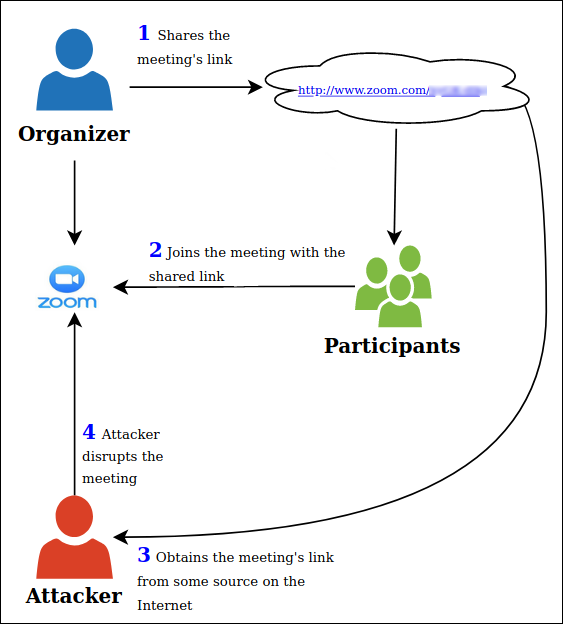
Zoom bombing is a type of cyber attack where an uninvited person enters into the zoom meeting or a chat room causing havoc throughout the world. It can lead to intrusion of privacy, loss of confidential information and much more. In Zoom meeting links, by default the password for the meeting gets added to the link as a parameter ‘pwd’ as shown in Figure 10 and screen sharing is also enabled by default. This makes zoom bombing a pretty simple one. All the attacker has to do is get hold of a link to the meeting and join in to cause disruption.

Any user who has the link can join the meeting without any password and share his screen in the meeting. This kill chain is depicted in Figure 11.
CVE-2020-11470 is a vulnerability in Zoom Client for Meetings version 4.6.8 and earlier on macOS which allows local processes to obtain unprompted microphone and camera access. In layman terms, any local process can get the microphone and camera access without the user being notified.

MS Teams
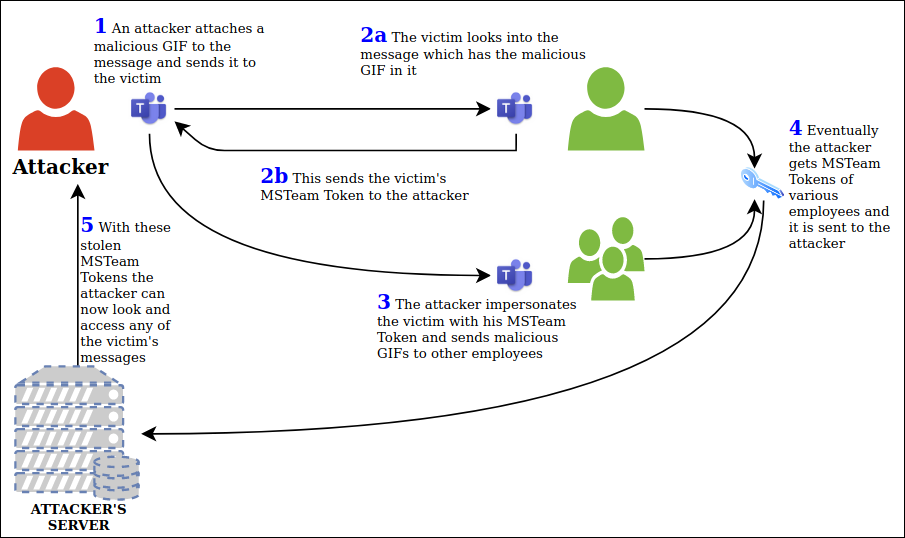
Account Takeover Vulnerability is a simple bug that allows any malicious user to send a specially crafted GIF message to a victim and then getting control of his account by getting the victim’s Team’s token, by which he can impersonate the victim and repeat the process. This can result in the entire organisation’s employees’ accounts getting compromised.
Figure 13 shows the kill chain for MS Teams account takeover vulnerability.
It was reported that the sites aadsync-test.teams[.]microsoft[.]com and data-dev[.]teams[.]microsoft[.]com were vulnerable to account takeover vulnerability. Using the above sites, the attacker only has to send a malicious GIF image to the victim. With the src=”” attribute the attacker can embed malicious links. Being an image, when the victim opens the message, the GIF is loaded automatically which will result in the victim’s authtoken cookies being sent to the subdomain (which the attacker is holding) enabling the attacker to steal these cookies. As a result of a successful attack, the attacker can get hold of the victim’s tokens and victim’s data. The attacker can now impersonate the victim and send the crafted GIF to other employees resulting in multiple employees losing their authtoken cookies to the attacker and their data getting stolen by the attacker.
Conclusion
We discussed services and applications that enable a smooth WFH during this critical time. These services, although productive, if insecure may result in loss of Confidentiality, Integrity and Availability (CIA) of organization’s and personal data. Adversaries are continuously working to identify weaknesses in an organization’s network and in such times, it becomes even more crucial to ensure security of the network. Therefore, we suggest to follow a few recommendations given here to ensure systems and data are secured against these adversaries.
Recommendations
- Keep updating the operating systems and installed applications and services to the latest version as and when new updates are available
- Update default service port and assign random port
- Setup firewall and configure it to allow custom port
- Use Virtual Private Network (VPN) or Multi Factor Authentication (MFA) for remote access
- Follow strict password policy and account lockout policy
- Disable administrator or root access for remote login
- Enable Network Level Authentication (NLA) for RDP
- For SSH access
- Disable empty password by setting ‘PermitEmptyPasswords’ to ‘no’ in the config file
- Instead of just password, use Private/Public keys for authentication and add passphrase to give additional layers of security
- Mitigate brute-force attacks by setting MaxAuthTries to a small number in the config file
- For routers
- Ensure default passwords are not used
- Disable unnecessary services
- Disable admin console access to external network
- Patch the device regularly
- Update the router models to the latest and avoid service expired models
- Use a reputed security product such as K7 Total Security to stay safe from cyber threats









