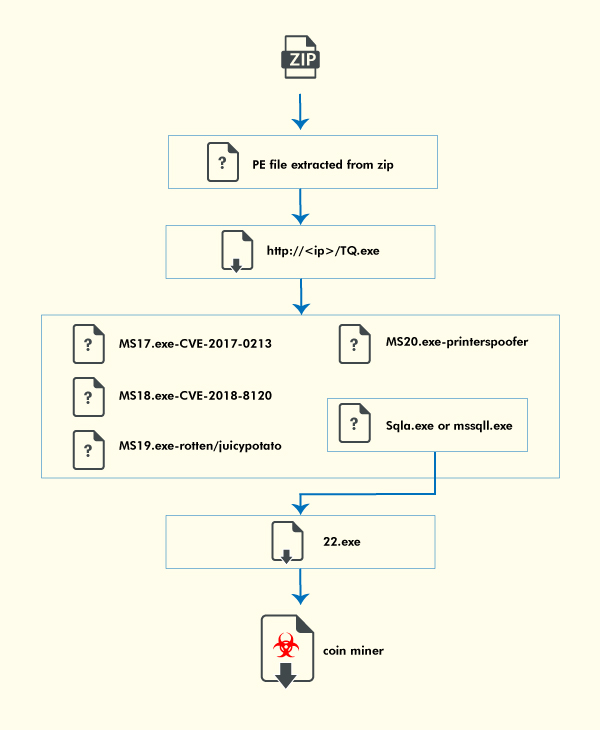
Crypto mining malware trends have been increasing over the years because the actors have always been consistent at including new tricks. Coinminer campaigns have also been seen to rely heavily on SMB vulnerabilities as their Ransomware counterparts for the past few years. This blog, is going to analyse an interesting binary’s kill chain which delivers XMRig coinminer and uses privilege elevation exploits like CVE-2018-8120, CVE-2017-0213 along with tools like Print spoofer, juicy/rotten potato, once it enters the system. A similar case was reported by Tencent in 2019, however, this year they have additionally included tools for privilege elevation, in addition to the exploits they have been using earlier. We also believe that the threat actor has Chinese links and is strongly related to the group which has been using the Gh0st variant malware. The overall infection flow is depicted in Figure 1 which we will be seeing in detail in the blog.
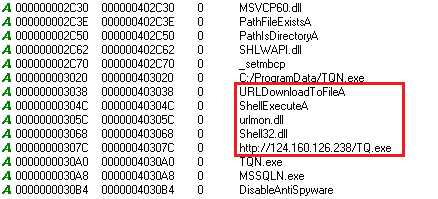
We started our analysis when we encountered a zip file submitted to VT which when extracted had a 20KB PE downloader file which was neither encrypted nor obfuscated. This file downloads a PE file named TQ.exe from an IP as shown in Figure 2.
TQ.exe
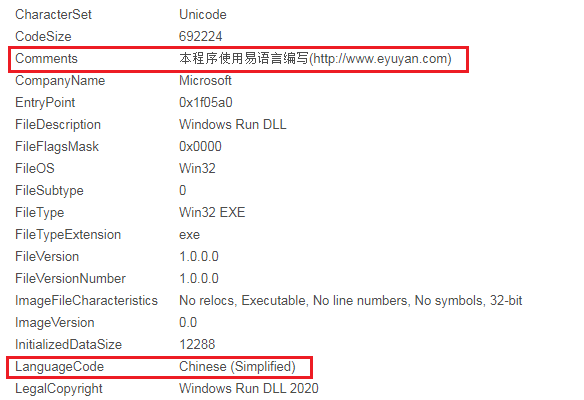
Figure 3 shows the Exiftool metadata of the file which clearly shows that the language is Chinese and also reveals that they are using products from eyuyan.com which enables them to program in their native language.
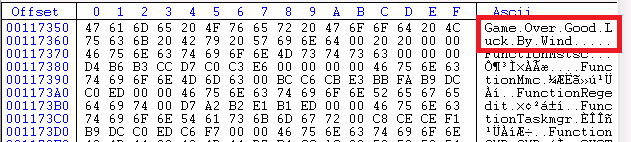
This file is compressed using the standard UPX packer which we unpacked and then searched for strings to see if we could find any interesting phrase. Later, we found an infamous string “Game Over Good Luck By Wind” as shown in Figure 4 which is attributed to Gh0st variant of malware used by Chinese APT groups like IronTiger APT and ZombieBoy campaign.
This file has many PE files embedded within it to take care of specific tasks like run entry creation, task scheduling (persistence), AV checking and the like. One file among the embedded binaries was different as can be seen from the MZ header of the file shown in Figure 5.
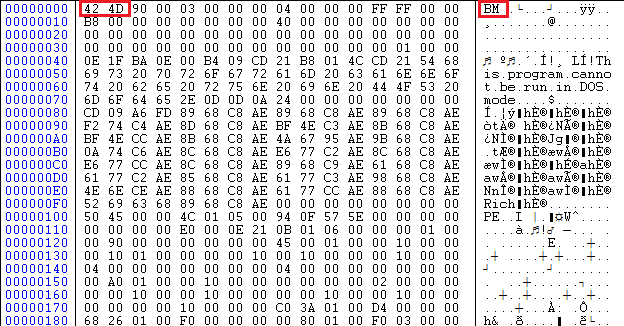
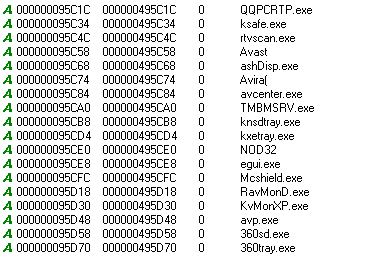
This embedded PE binary gets dropped on to the system as %WINDIR%\mpmgsvc.dll. This binary is also not protected by any crypter or obfuscator and hence looking at the strings would reveal interesting information. It has a list of AV names as shown in Figure 6 which it will look for by enumerating the running processes using CreateToolhelp32Snapshot, Process32First and Process32Next APIs.
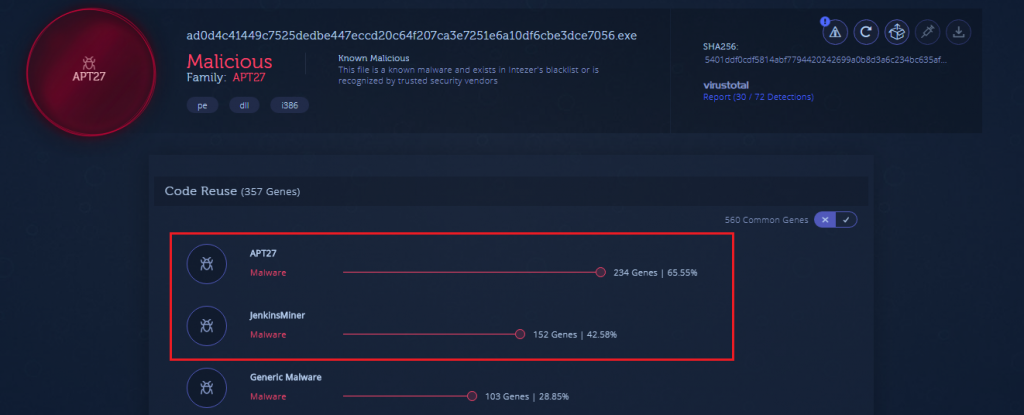
Further, on checking the malware hash in Intezer, to see if we can find any specific malware gene for attribution, as expected we did get a 65% match to APT27 (Chinese actor) and 40% match to JenkinsMiner as depicted in Figure 7.
Now, after looking at the embedded file found inside TQ.exe, let’s focus on the binaries dropped by TQ.exe which are named MS17.exe, MS18.exe, MS19.exe, MS20.exe and mssqll.exe/Sqla.exe. Here, 4 files except mssqll.exe/Sqla.exe are used for elevating the privilege once the binary reaches the system.
| File name | Usage |
| MS20.exe | Print spoofer |
| MS19.exe | juicy/rotten potato |
| MS18.exe | CVE-2018-8120 |
| MS17.exe | CVE-2017-0213 |
MS17.exe: Elevation of Privilege Vulnerability
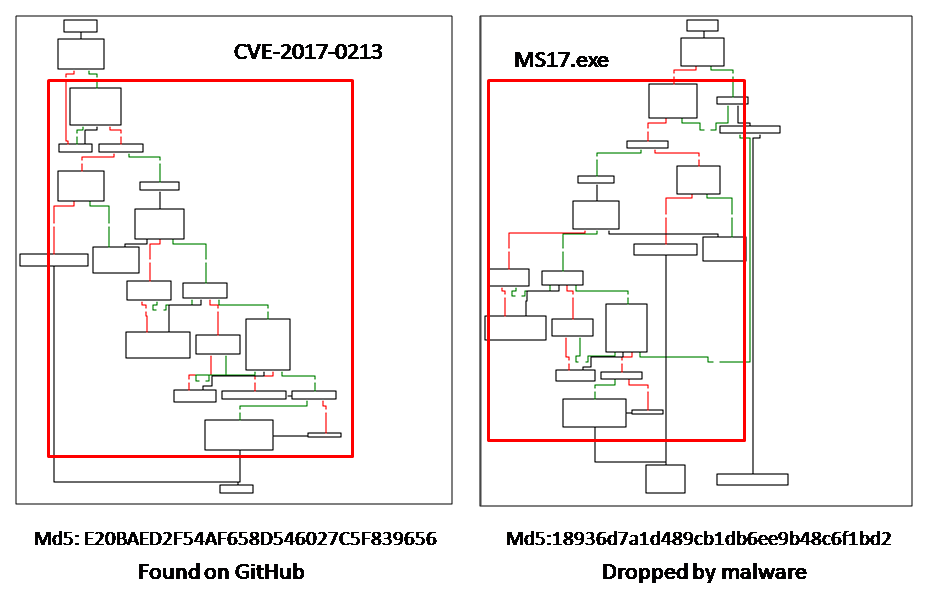
MS17.exe is actually a module for elevating the privilege by exploiting CVE-2017-0213. The exploit code is available for download on GitHub and exploit.db. We downloaded the source code from GitHub and compiled it and compared it with MS17.exe as shown in Figure 8. They were similar in both the function flow and code usage.
MS18.exe: Elevation of Privilege Vulnerability
MS18.exe is actually a module for elevating the privilege by exploiting CVE-2018-8120. The source code for this exploit is also available for download from forums like GitHub and exploit.db. Figure 9 shows the comparison of one of the functions named GetCpuNumber() found in the source code available from GitHub and the MS18.exe and Figure 10 shows the function flow between the 2 files.
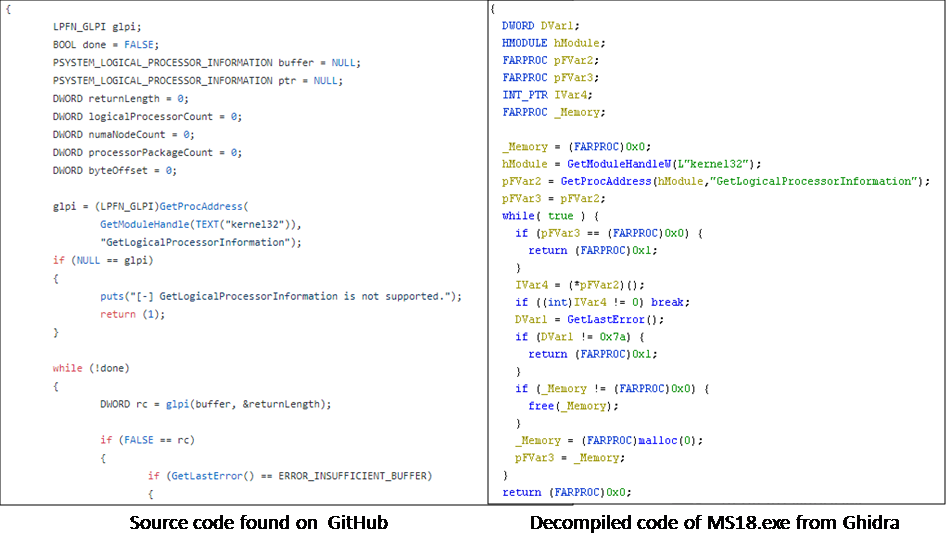
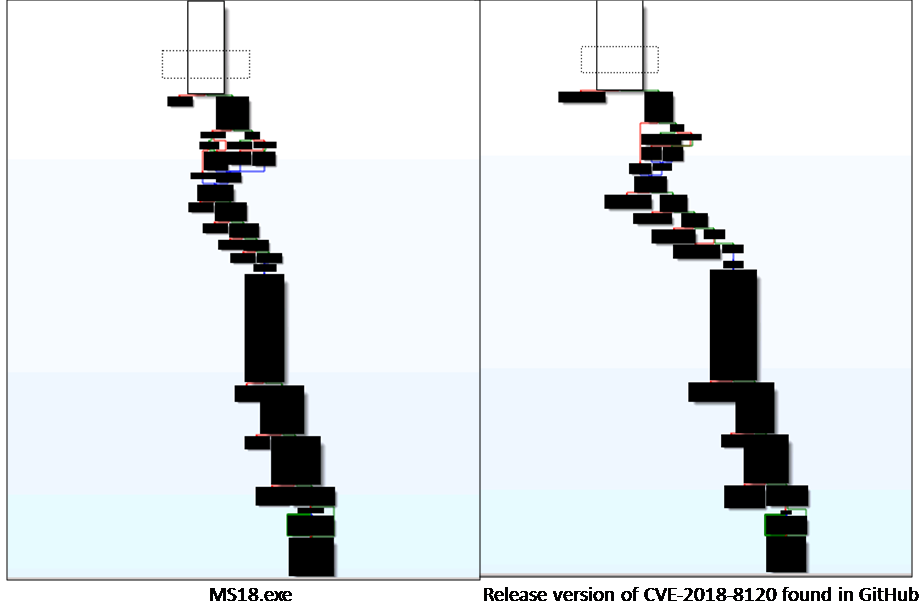
The systems most likely to be impacted are
- Win7 x32
- Win7 x64
- Win2008 x32
- Win2008 R2 x32
- Win2008 R2 Datacenter x64
- Win2008 Enterprise x64
MS19.exe: Privilege Escalation Tool
Unlike the other 2 files which we saw earlier, this is not an exploit code. It is a tool used for privilege escalation named Juicy Potato which according to the author is the sugared version of Rotten Potato. This tool leverages the privilege escalation chain based on BITS service and when you have SeImpersonate or SeAssignPrimaryToken privileges. The list of possible systems whose CLSID tested are as follows.
- Windows 7 Enterprise
- Windows 8.1 Enterprise
- Windows 10 Enterprise
- Windows 10 Professional
- Windows Server 2008 R2 Enterprise
- Windows Server 2012 Datacenter
- Windows Server 2016 Standard
MS20.exe: Privilege Escalation Tool
This is another privilege escalation tool called Print Spoofer which was introduced around May 2020. This tool also exploits the impersonation privilege on Windows systems but is supposed to be more effective than Juicy/Rotten potato since its Print Spoofer was tried and tested on Windows 10 and Server 2016/2019 before release. It is more successful with systems where the users have SeAssignPrimaryToken privilege or SeImpersonate privilege which allows you to run code or create a new process. It can also impersonate a user with named pipes and token. Figure 11 depicts the code comparison of a function CheckAndEnablePrivilege() between the source code found on GitHub and the MS20.exe.
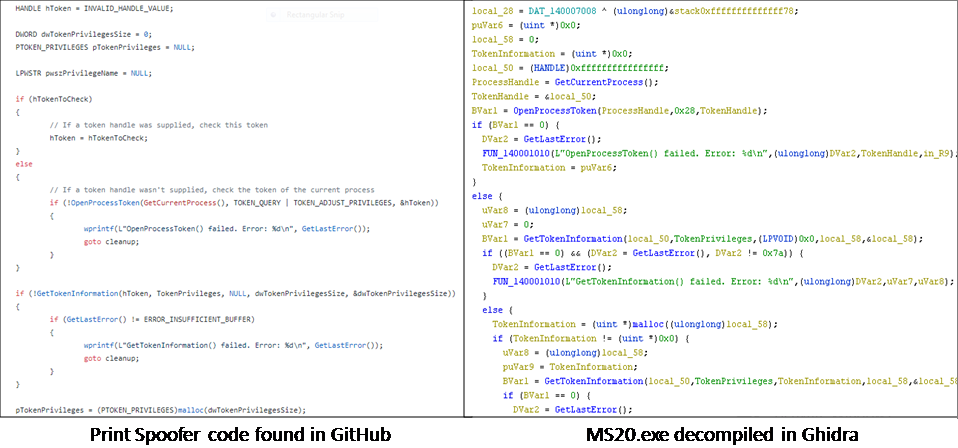
Sqla.exe/mssqll.exe
This is the 5th file dropped by TQ.exe. Primarily all that this file does is to download another PE file as depicted in Figure 12 where the URL pattern is hxxps[:]//<IP>/11.exe or hxxps[:]//<IP>/22.exe.
The newly downloaded file is responsible for downloading the actual coinminer and executing it in the infected system. The coinminer is XMRig 5.0.1 version which is available in both 32 bit and 64 bit versions. The 64 bit version is downloaded from www[.362com.com/64.exe and 32 bit version is downloaded from www[.362com.com/32.exe. Apart from the miner file, it is also responsible for downloading a text file as depicted in Figure 13 which acts as an update configuration file for the miner and also maintains a list of processes and service names to kill in order to free the system resources from any previously running miners.
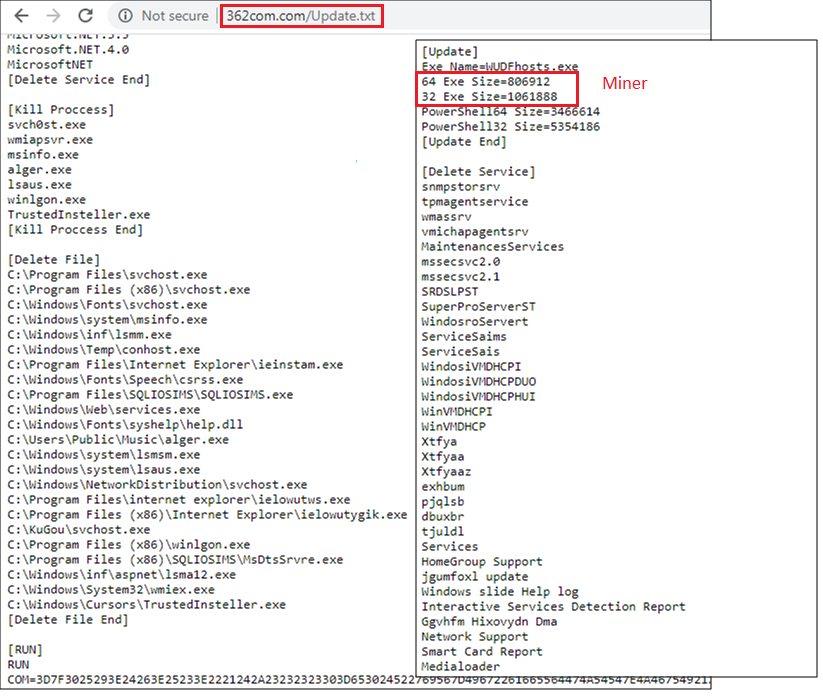
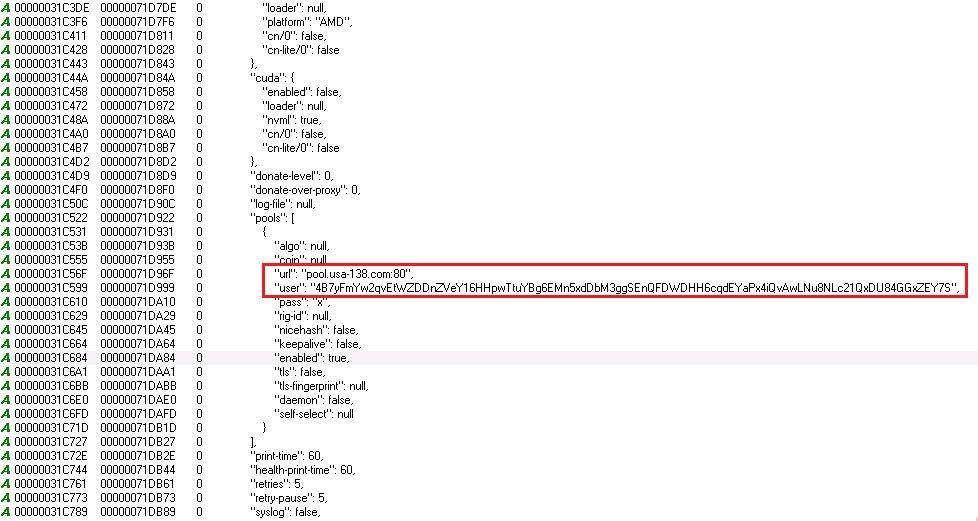
Figure 14 depicts the configuration file of the miner which has the user’s wallet info and mining pool url. The miner will be saved in any one of the names mentioned viz. TrustedInsteller.exe, WUDFhosts.exe, and WmiApSvr.exe.
Attribution
All the facts we have seen above strongly suggest that the threat actor is Chinese. So obviously it must be any one among the Chinese APT groups. Already, Figure 7 suggests that one of the embedded files is attributed to APT 27, so we tried to collect other info to see if it matches the attribution.
1. IP used here
| 118.45.42.72 | AS 4766 ( Korea Telecom ) |
| 124.160.126.237 | AS 4837 ( CHINA UNICOM China169 Backbone ) |
| 124.160.126.238 | AS 4837 ( CHINA UNICOM China169 Backbone ) |
| 222.99.11.146 | AS 4766 ( Korea Telecom ) |
All the URL and IP used here resolve to Korea and China which is similar to the Operation PZCHAO (espionage infrastructure related to APT27) discovered by Bitdefender in 2017.
2. If we also take a closer look at the attack chain mentioned in Operation PZCHAO and the attack chain in our blog (Figure 1), both are similar to some extent.
3. The use of Gh0st variant binaries in the attack chain to download further files is also related to APT27.
So we can conclude that this campaign is strongly connected to the APT27 group and that this campaign has been active since 2017 and they have been frequently updating the tools that they use for privilege escalation as and when new tools are introduced year by year.
We at K7 computing have detection for all such malware and tools. As we always recommend, use a reputed security product such as K7 Total Security to stay safe from any cyber threats.
Indicators of Compromise (IoCs)
| Hash | File Info | K7 Detection Name |
| 5D2E9716BE941D7C77C05947390DE736 | 22.exe/11.exe | Trojan ( 00521b151 ) |
| 4A72E30C0A582B082030ADFD8345014F | 64 bit Miner | Adware ( 0054d80b1 ) |
| 70E694D073C0440D9DA37849B1A06321 | 32 bit Miner | Trojan ( 0051918e1 ) |
| 0D31F807FAA5170942BB2F4095EE3F6B | PE file extracted from zip | Trojan-Downloader ( 005107621 ) |
| 18936D7A1D489CB1DB6EE9B48C6F1BD2 | MS17.exe | Trojan-Downloader ( 0052d1511 ) |
| DEF4FFF6491283E71E8F9462ABC968FA | MS18.exe | Trojan ( 0053c9721 ) |
| F4F11DC6AA75D0F314EB698067882DD5 | MS19.exe | Trojan ( 0055d1e31 ) |
| 0F30CB0826032787EC221BDB9D952D0E | MS20.exe | Trojan ( 005681051 ) |
| FEF89B11C40BA67C88E0B02FCB495C63 | mssqll.exe | Trojan ( 004fe3c61 ) |
| DC60A503FB8B36AB4C65CDFA5BD665A1 | sqla.exe | Trojan ( 004fe3c61 ) |
| 9450249AE964853A51D6B55CD55C373E | TQ.exe | Trojan ( 005376ae1 ) |
| 99CF2CC6C859B104E35220785716AD8E | TQ.exe | Trojan ( 005376ae1 ) |
| 188C75635D9FDCB3F0030D12446BCBAF | Zip | Trojan-Downloader ( 005107621 ) |
Domains
hxxp://22ssh[.com
hxxp:// ssh.22ssh[.com
hxxp:// www.362com[.com
hxxp:// www.361com[.com
hxxp:// down.362com[.com
hxxp:// ssh.362com[.comhxxp:// pool.usa-138[.com
IPs
118[.45.42.72
124[.160.126.237
124[.160.126.238
222[.99.11.146









