On 29th June 2020, Government of India banned Android apps of Chinese origin from being used in the country citing safety and privacy issues. This list included TikTok, a video-sharing social networking application installed over millions of devices in India.
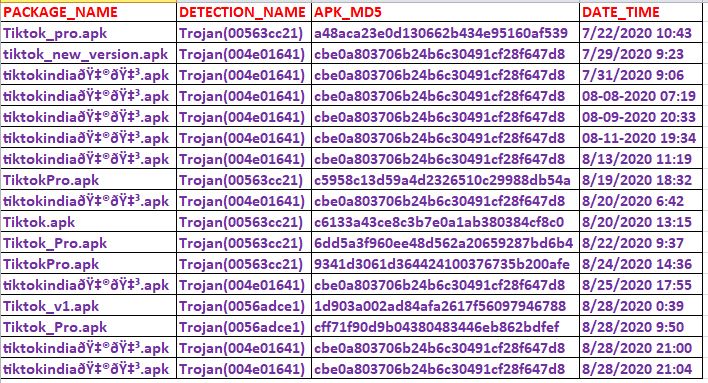
The cybercriminals are now taking advantage of users’ attraction and interest towards TikTok to deliver malware, yet another incident to add. Our researchers saw an increased number of detection reports in the name of the banned TikTok app since the end of July 2020, on sifting through our Telemetry data as shown in Figure 1. This ad scammer threat targets Jio users.
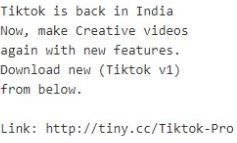
The fake TikTok app has the code within itself to spread via smishing messages as shown in Figure 2.
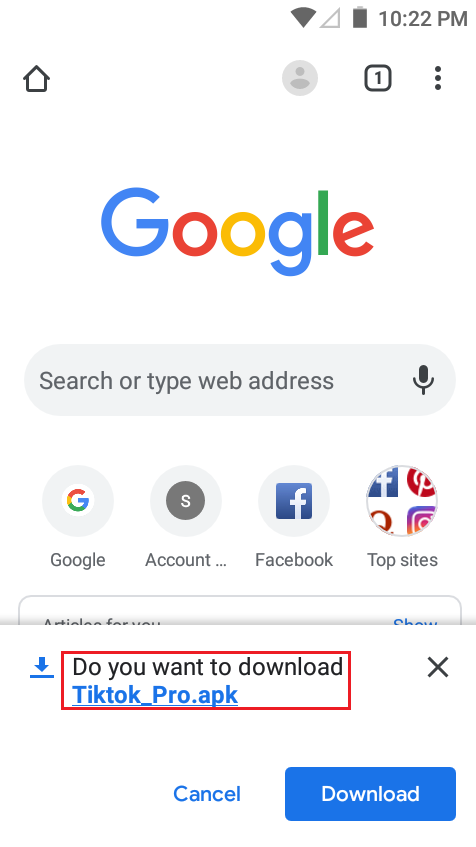
When the user clicks on the link in the SMS, the fake TikTok APK is downloaded to the user’s device as shown in Figure 3.
At the time of writing this blog, these apps were observed to do nothing more than displaying advertisements to the users. Once installed, the fake Tiktok_Pro app displays a message to the user and asks the victim to enter username and password as shown in Figure 4. A point to note is that there is no validation done for the same and any username and password can be entered by the user, an effort just to trick the victim to trust the app. Probability is that a user might tend to enter his/her already registered TikTok (original) credentials instead of fake credentials as soon as they see TikTok.
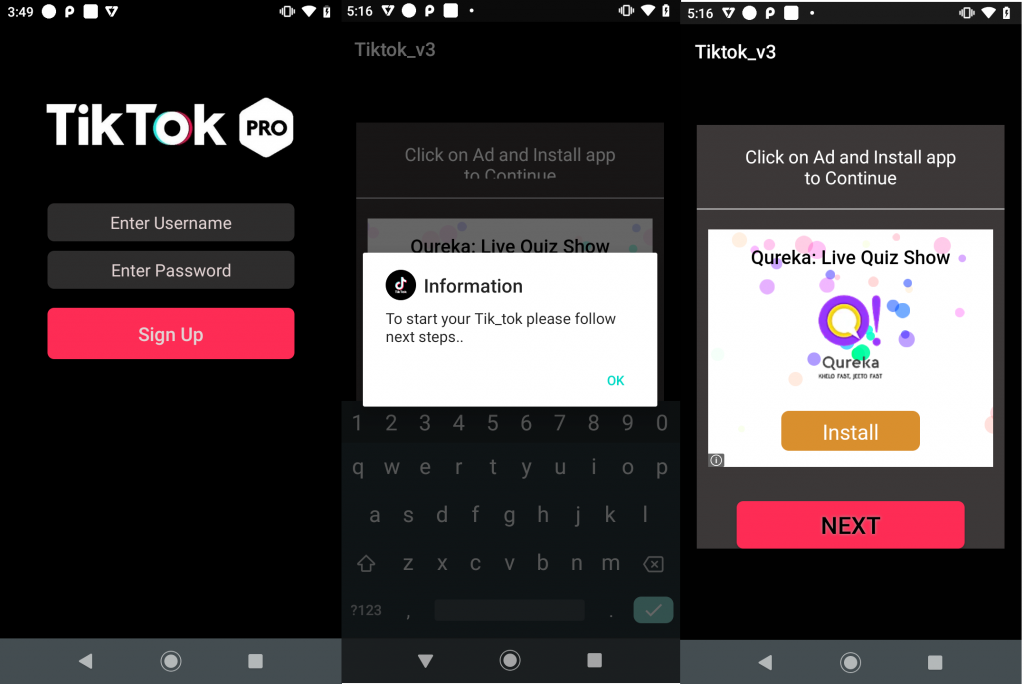
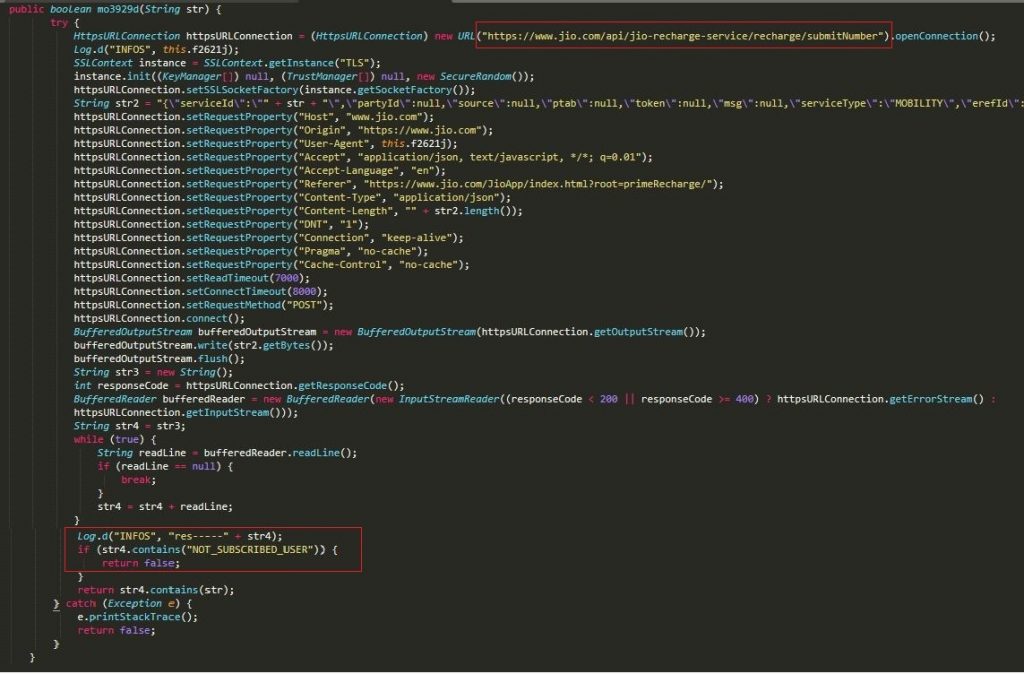
Figure 5 shows requests sent to Jio’s official recharge APIs to verify if that is a Jio subscriber and to check the validity of the victim’s Jio phone number(s), This clearly shows that this malware has targeted only the Jio users.
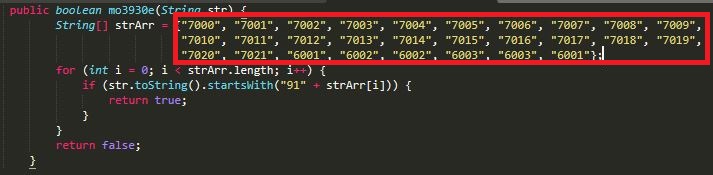
As explained in one of our earlier blog, this fake app further spreads by collecting the contact information from the victim’s device and forwarding a text message to all of the Jio numbers in the victim’s contact list as shown in Figure 6.
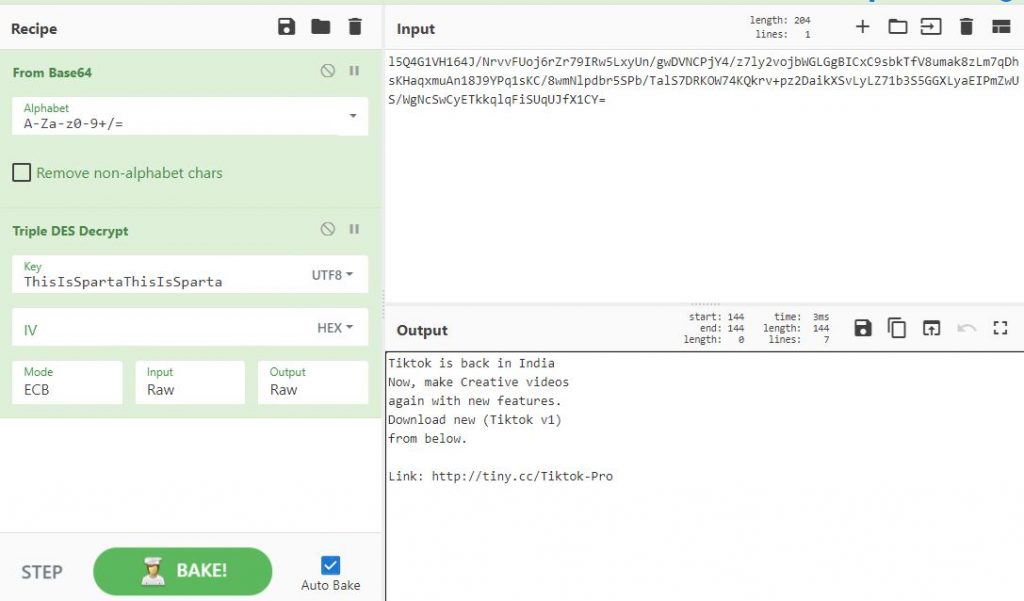
Smishing message that is sent to the victim’s contact list is carried with the code as a TripleDES encrypted string as shown in Figure 7.
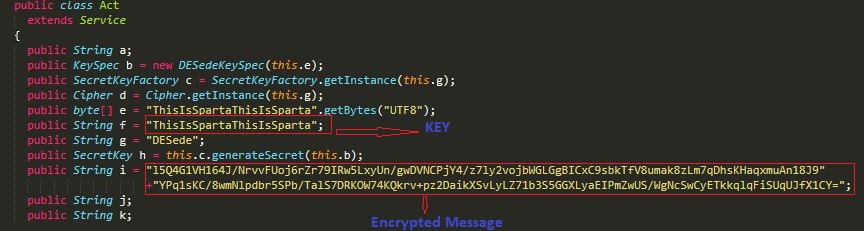
The message gets decrypted as shown in Figure 8 before it reaches the victim (Jio user).
As mentioned earlier, these fake apps are just ad scammers, as of now, that force the user to click on the ad thereby generating revenue for the threat actors. K7 Mobile Security users have protection against these kinds of mobile threats. Android users are requested to install the latest version of K7 Mobile Security and keep it updated to protect themselves from the latest threats. Also, we recommend Android users to avoid believing in and installing applications from third party links.
Indicators of Compromise (IoCs)
| Package name | Hash | Detection Name |
| Tiktok-Pro.apk | cff71f90d9b04380483446eb862bdfef | Trojan ( 0056adce1 ) |
| Tiktok-Pro.apk | a48aebeb2259e4f3d71205176b889dfe | Trojan ( 00563cc21 ) |
| Tiktok-Pro.apk | af9d792c605f3e9a062629b9cf983109 | Trojan ( 00563cc21 ) |
| Tiktok-pro.apk | edb563fdcab0ab0580fdeefad6fff9ad | Trojan ( 00563cc21 ) |