This is volume I of a three part series based on our (Kaarthik RM and Rajababu A) paper for AVAR 2013, discussing the prevalence of autorun malware in the Asian region, taking it further by analyzing an example of such a malware
To Brief it Out…
The Autorun Worm: an infection that uses an antiquated mechanism to make itself prevalent, especially in the Asian region. Even though the Autorun or Autoplay feature was deprecated by Microsoft quite some time ago, it is still actively exploited in the wild. For instance an autorun worm, widely known as ProsLikeFan, has been spreading like wildfire. Most interestingly, this isn’t your traditional Win32 PE binary, but a highly obfuscated JavaScript. This worm is certainly not the handiwork of a script-kiddy.
Beneath several layers of obfuscation lies a WMI malware which can retrieve users’ system information and post this information to a C&C server, and invites other malware to the host machine at the behest of the remote attacker.
This paper will discuss the reasons why autorun-related malware are very prevalent in the Asian region, the Indian sub-continent in particular. We will also focus on a technical dissection of the afore-mentioned JavaScript malware, cover its lifecycle its geographical prominence and will also include a brief take on its C&C network.
Autorun & Its Prevalence
An autorun worm uses the now deprecated feature: Autoplay, to initiate malicious executables from removable drives. This exploit’s target vector has a wider coverage, owing to the fact that removable drives or pen drives have become the most popular method for quick data transfer by physical media.
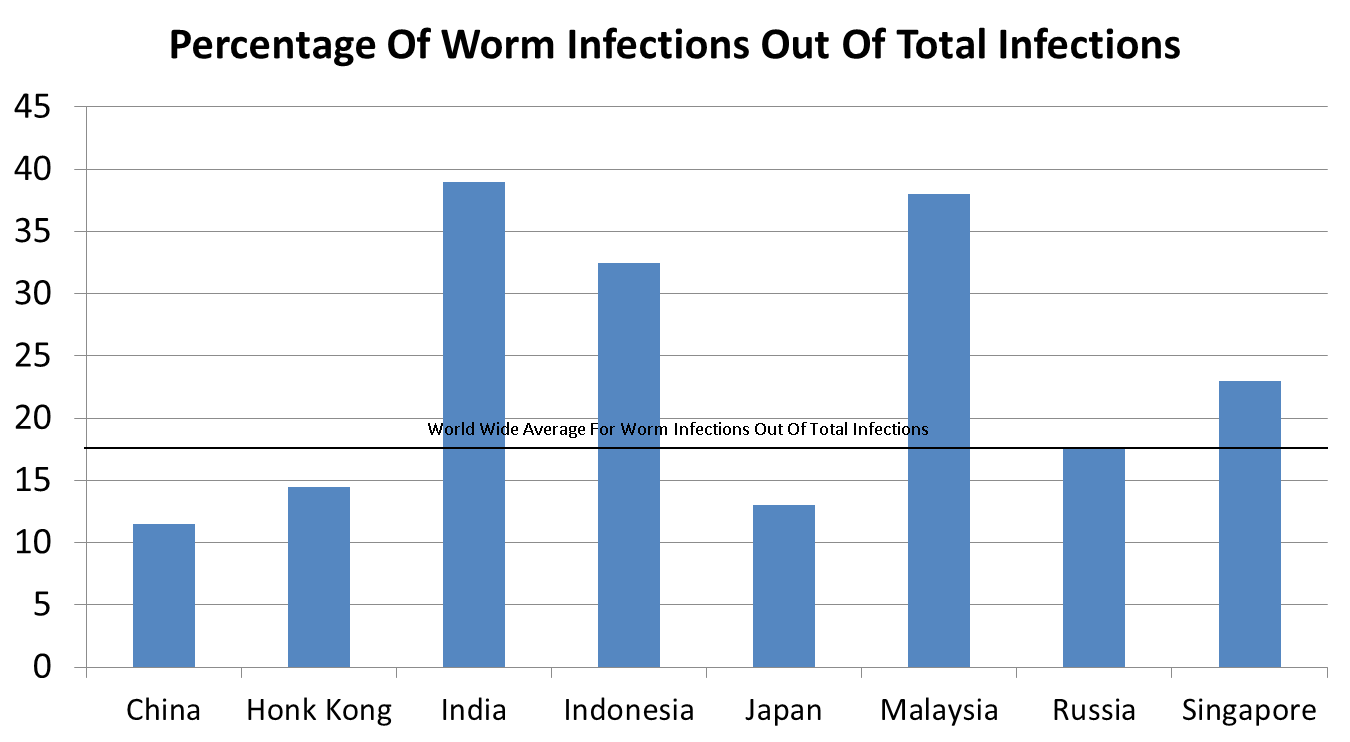
Autorun worms have had higher success ratio in the Asian region. A closer look at the infection ratio of worms in the Asian region would give us a better insight on the above mentioned fact. Figure 1 given below shows worm infections as a percentage of the total infections in the Asian region.
Figure 1: Worm Infection Rate
The world over average for worm infections is 17.5% as shown in the above graph. This is with respect to data from Microsoft’s Security Intelligence Report 1. It is evident from the graph above that in India almost 40% of the infections seem to be worm related.
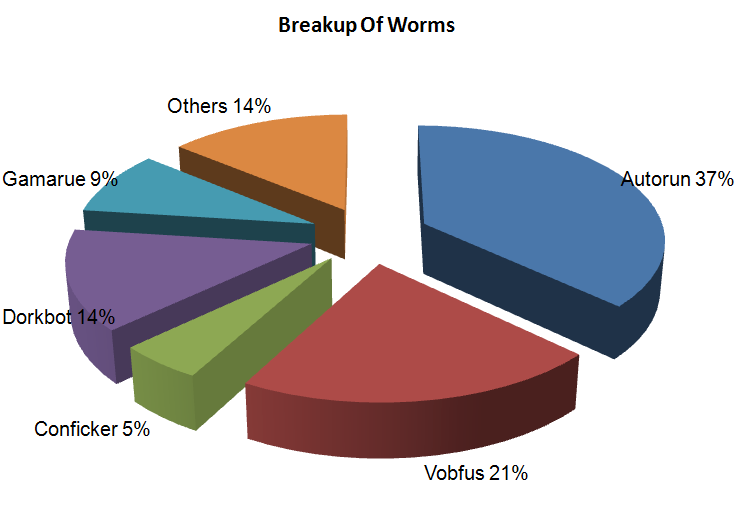
Figure 1.1 displayed below provides the breakup of the Worm related malware.
Figure 1.1: Breakup of Worms Based on K7 Threat Control Lab’s internal Telemetry
From the chart above, it is clear that autorun malware dominates the infection ratio of the worm category. One must consider that families like Vobfus, Gamarue etc. also employ the autorun technique to improve their infection vector. Though most of the above mentioned worm families are all Win32PE types, it is interesting to note that there is an increase in the Non-PE category of worms. For instance ProsLikeFan, as it is commonly known, is a JavaScript malware that is on the rise.
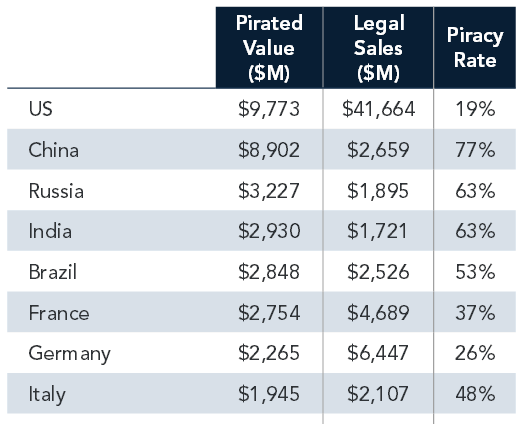
Figure 1.2: Software Piracy Rates According to BSA Global 2
The reason autorun malware thrives in India (according to Figure 1.2) is due to the fact that software piracy is still at large, this rules out timely security updates. Also a very small percentage of the computer users in India are broadband internet users, this again widens the target. It is evident that only a very small percentage of computer users would have the update from Microsoft that deprecated the autorun mechanism for removable drives.
1. http://www.microsoft.com/security/sir/threat/default.aspx#asia
2. http://globalstudy.bsa.org/2011
Images courtesy of host.nacdnet.org and openclipart.org
Kaarthik RM & Raja Babu A
K7TCL
If you wish to subscribe to our blog, please add the URL provided below to your blog reader:
https://labs.k7computing.com/feed/