Recently, we received a report from a user that tiktok.apk was falsely detected as a Trojan. Yes, you read it right; tiktok.apk, one of the Android applications that was banned by the Government of India citing users’ data security violation.
This caught our attention and we decided to investigate further. We tried to find how the users installed an app banned in the country and also how, many such users have reported the same application as a false detection; perhaps the same hash.
Looking at our telemetry reports, we saw that this application, “tiktok.apk” was possibly shared via WhatsApp. The application’s download path was “/storage/emulated/0/WhatsApp/Media/WhatsApp Documents” – the default storage location for WhatsApp downloads. In spite of the app being banned by the Government of India (GoI), the users’ of the app are still persisting interest in TikTok thereby pledging their data privacy
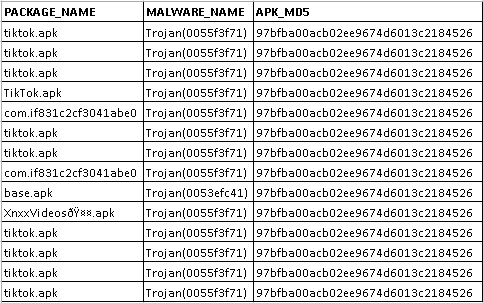
Interestingly, the same reported hash “97bfba00acb02ee9674d6013c2184526” has been shared via WhatsApp, with different names such as “XnxxVideos<xxx>.apk” as shown in Figure 1 and seen in the same storage path of WhatsApp applications.
This could be the next wave of Android Ad Clicker variants that are spread via WhatsApp in the name of tiktok.apk, XnxxVideos<xxx>.apk as we know at the moment of writing this blog.
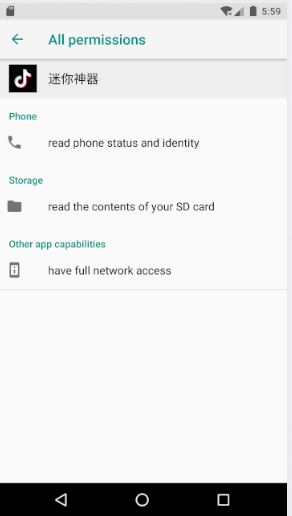
Analysing the sample, after installation, it presents itself with TikTok icon but with a Chinese name
“迷你神器” as shown in Figure 2.

Launching the app attempts to jump scare the user with a ghost image and music. However, users do not see any feature related to the TikTok application. So what does this app do? And why is it being distributed?
This application does not ask for many permissions apart from “SYSTEM_ALERT_WINDOW” and “READ_EXTERNAL_STORAGE” as shown in Figure 3.
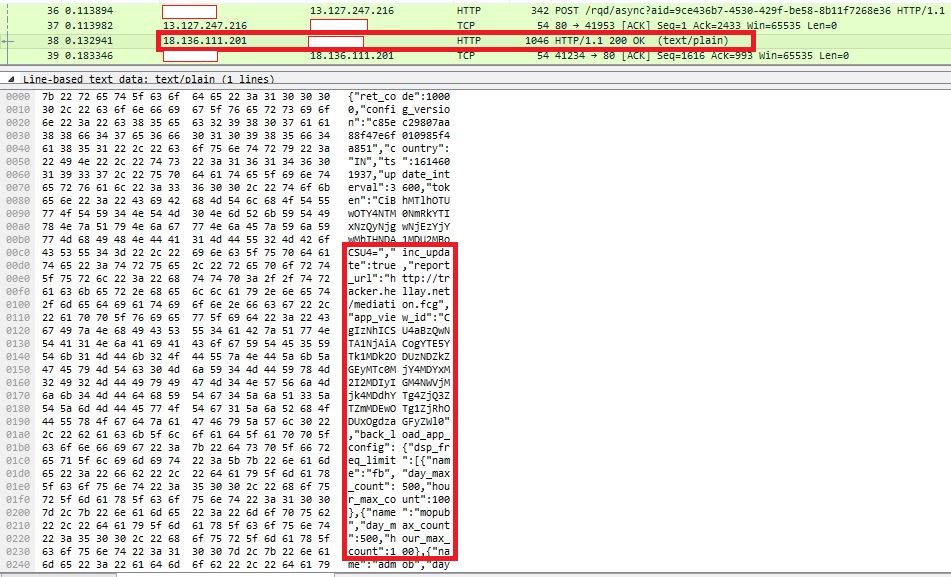
Further analysis of the sample revealed that this app’s main focus is on app monetization. Network traffic from one of the connected ip addresses “18.136.111.201” which hosts app.rqmob.com confirms that AdMob and MoPub, app monetization tools, are featured in this app as shown in Figure 4.
From the pcap it is seen that this fake app posts the user’s data like device model, geo-location for the malware author to identify the device. Response from the host appclick.rqmob.com contains the ad data to be displayed in the compromised device as shown in Figure 5.
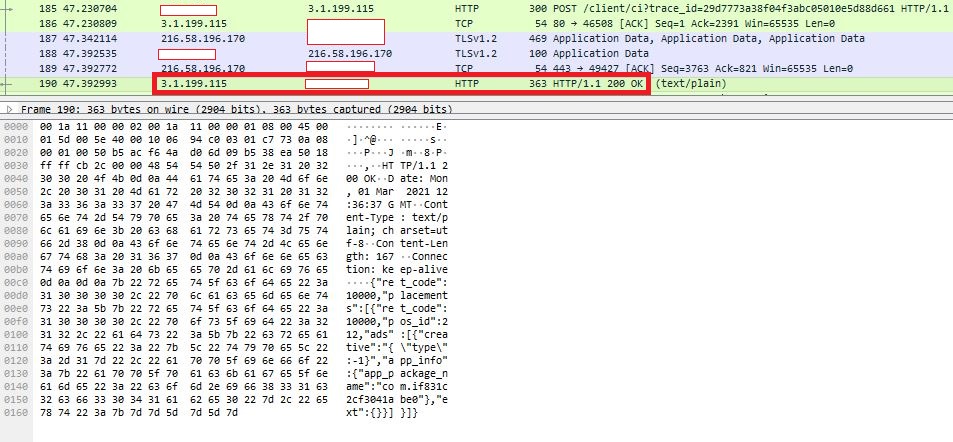
These network responses show that the malware author displays ads via the host applick.rqmob.com. Custom view of the corresponding ad is created and ad clicking is executed. The warning of clicking is silenced by using ”@SuppressLint(“ClickableViewAccessibility”).
Ad clicking on these ads happens silently based on gestures performed by the user like touchmonitor, pressmenu, focuschange, onscrollstatechanged, onnothingselected, onpageselected etc., and by using performClick() function as shown in Figure 6.
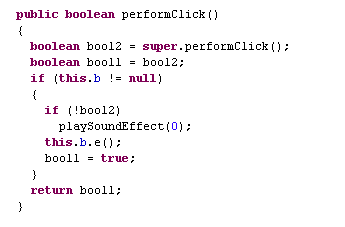
“super.performClick()” calls the super implementation which generates an accessibility event and calls the onClickListener() of the view, if any, defined already. Also in case of any click failure, this app plays the aforementioned music. At this point in time, this app does not seem to do any more suspicious activities but the users must be aware that they should not prefer any other third party sources for app downloads and installations at the cost of their data privacy and security.
Data privacy is taken seriously by the higher authorities, even then the responsibility lies with the users in securing their data. Users must be aware why data privacy is important and act accordingly. Malware authors will try and trick an average user into spreading their malware by exploiting the users’ interest in social media. It is the users who have to be wary of such malevolent activities in the wild and safeguard themselves from such attacks. Users are recommended to install a reputed security software like K7 Mobile Security (Android and iOS) to protect their data and privacy.
Indicators Of Compromise (IOC)
File Name: tiktok.apk
MD5 : 97BFBA00ACB02EE9674D6013C2184526
K7 Detection Name: Trojan (0055f3f71)









