Go code related malwares are getting pretty common day by day because of multiple reasons like easy to code, a single codebase which can be used to generate samples for multiple OSes, difficult to reverse engineer, etc. We came across a campaign recently where attackers used Go based clip bankers to steal crypto on the go using a Telegram bot . We saw multiple variants of similar kinds of clip bankers where code has been modified frequently with the base functionality remaining the same. We are going to talk about such clip bankers in this blog in detail.
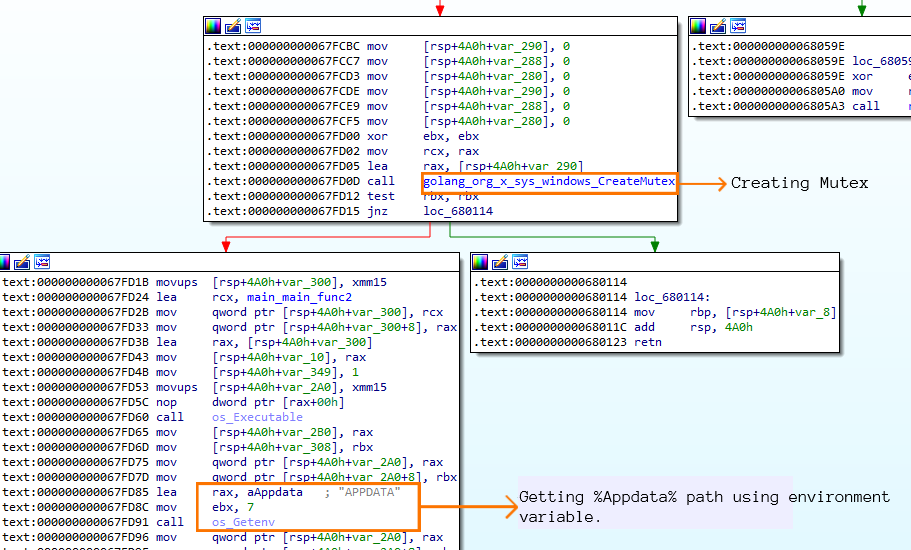
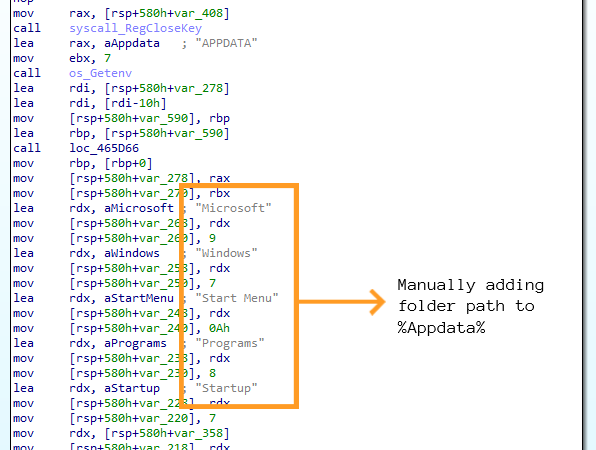
Let’s analyse the samples now. The malware first creates a mutex to avoid running the sample again in the same machine and then gets the path of the APPDATA folder on the machine to create a directory inside the Roaming folder so as to copy the malware there with random name and hidden file attributes. Some samples copy malware directly inside the startup folder.
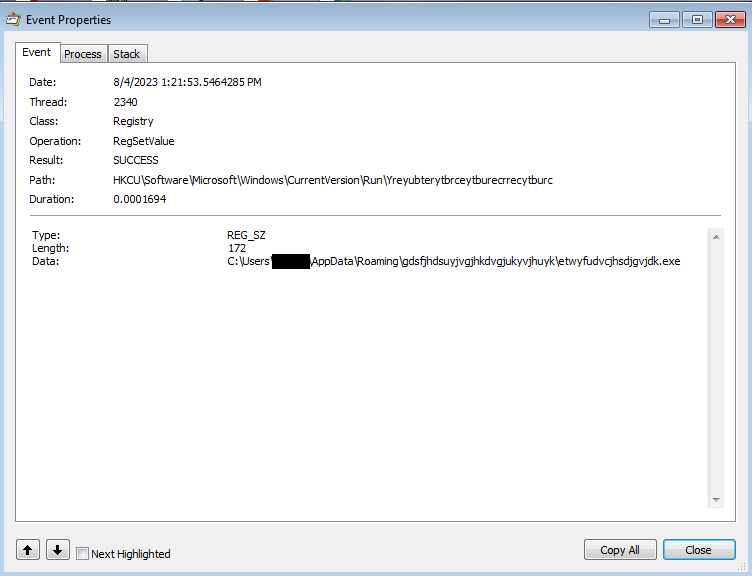
After copying malware, a CurrentVersion\Run registry is created to run the sample automatically on startup.
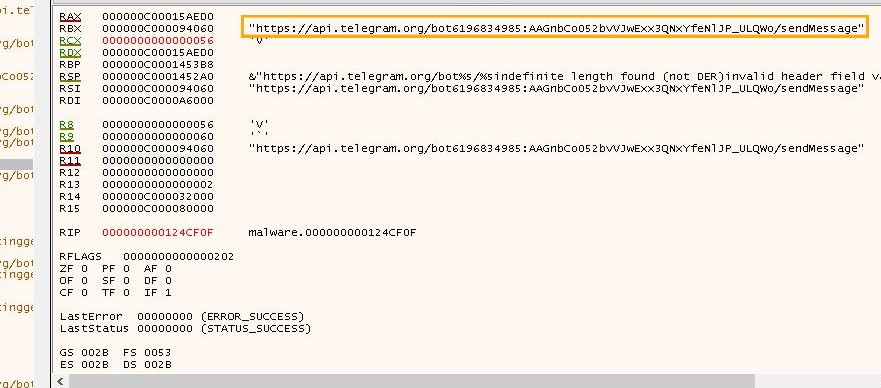
After executing from the new location, the malware continues execution if and only if it establishes connection to the Telegram bot with the token in the API for authentication.
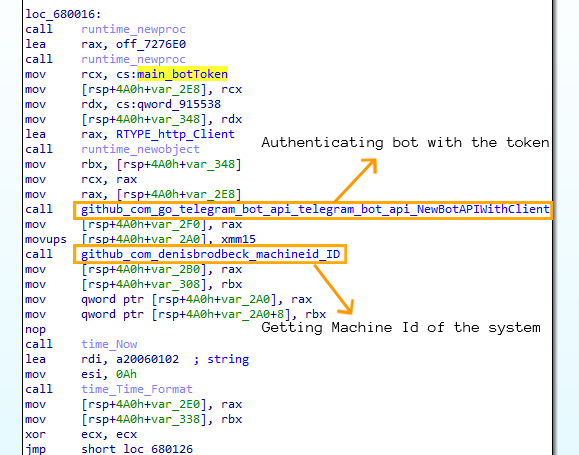
After getting response code 200 from the bot, the malware first gets the unique Machine ID of the system using registry key SOFTWARE\Microsoft\Cryptography to uniquely identify the victim and then reads all the clipboard content of the victim. This is implemented using a Go based open source module from github.
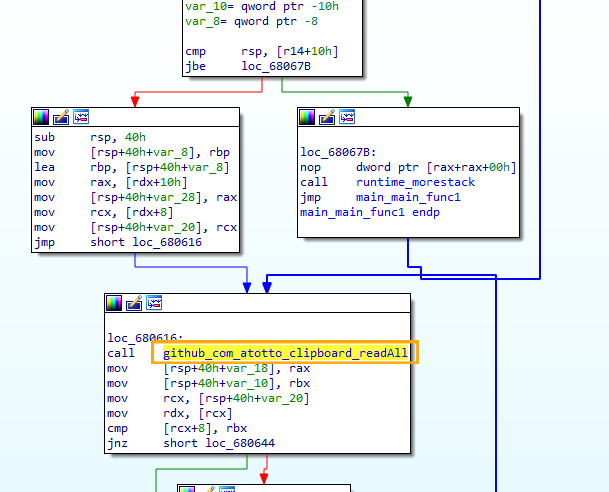
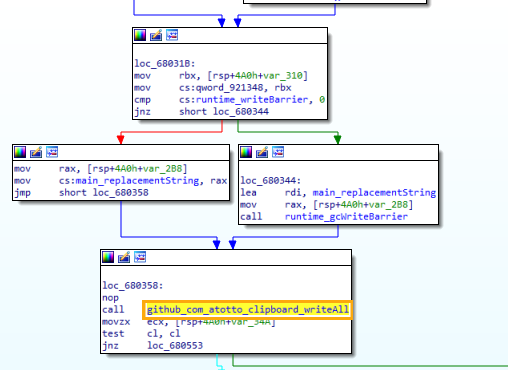
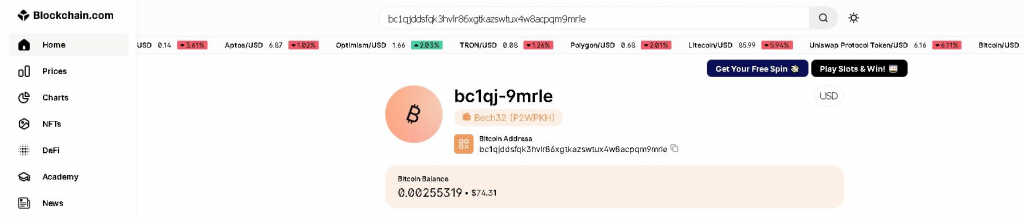
After reading all the content from clipboard, the malware parses through the content and tries to figure out if the content has crypto wallet addresses by using regular expressions so that it can replace the address with the attackers’ crypto wallet address. Only the crypto wallet address is changed with all the other content remaining the same and this modified content is again written to the victims’ clipboard.
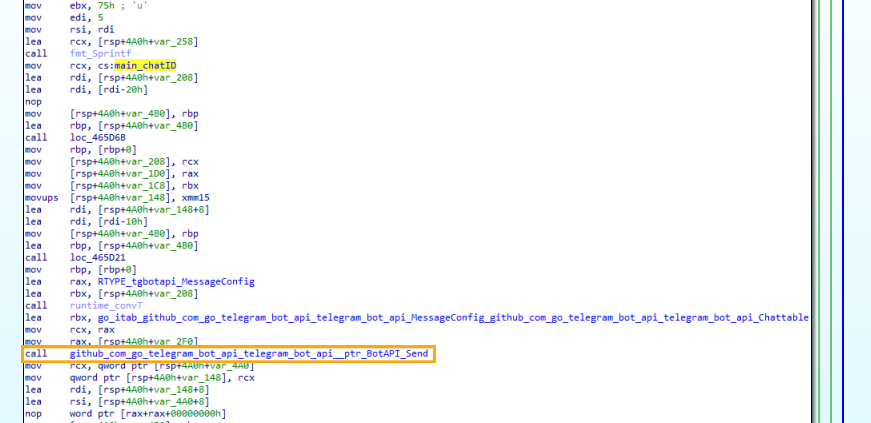
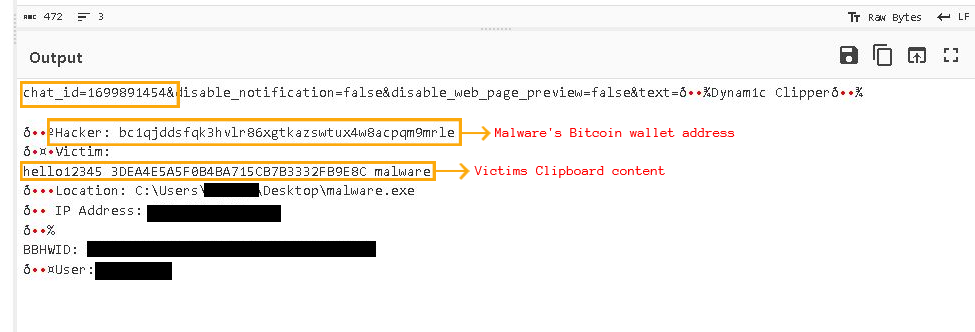
Then the malware sends victims information to the attacker to keep track of the victims using Telegram bot and the malware forms a message which consists of IP Address,location of malware, MachineId,victim’s clipboard content ,Username, etc.
As we can see, creating malware has become so easy because of easy availability of ready to use code. Protecting yourself by investing in a reputable security product such as K7 Antivirus is therefore necessary in today’s world. We at K7 Labs provide detection for clip bankers like these and all the latest threats. Users are advised to use a reliable security product such as “K7 Total Security” and keep it up-to-date to safeguard their devices.
IOCs
| Hash | Detection Name |
| 7819e8b66bbd678d9898a39630c5cb94e1d63b3ffe46b7cf0e9d4477e7ebc9a8 | Trojan ( 005a7a4e1 ) |
| cf58ff751bc10914fca398a2f609114dd24005ac2307435de084488bed63a0a1 | Trojan ( 005a7a4e1 ) |
| 88fb5c53b84be0f6920e6cb02572d32fe23312e32d2a003a3a0c30f6583e4525 | Trojan ( 005a7a4e1 ) |
Telegram bots
https://api[.]telegram.org/bot6196834985:AAGnbCo052bvVJwExx3QNxYfeNlJP_ULQWo/getMe https://api[.]telegram.org/bot6178300689:AAE_Khw1mc6SGGUGoqaAkA7LhctwrtjGxXo/getMe https://api[.]telegram.org/bot6240158659:AAHW9JcpmR7UEn0cDKvOUiiAVaj-hdcWzgU/getMe
Bitcoin Wallet Addresses
Bc1q8jgyp7qs6j9lstr7em94q4l8rvl7szjnzhtywq
Bc1qjddsfqk3hvlr86xgtkazswtux4w8acpqm9mrle
qphmukvwzu4s07ku34zhpz646lgt6ayulug2vn24q4