The world is moving from human reality to artificial reality aka advanced artificial intelligence (AI). In January 2025, Deepseek, an advanced artificial intelligence developed by a Chinese startup based in Hangzhou released its first chatbot application based on Deepseek-R1 model for iOS and Android platforms. This blog is about how threat actors create deceptive websites that mimic Deepseek AI to mislead users into downloading their malicious app.
We at K7 Labs recently came across a twitter post about Deepseek Android Malware as shown in Figure 1.
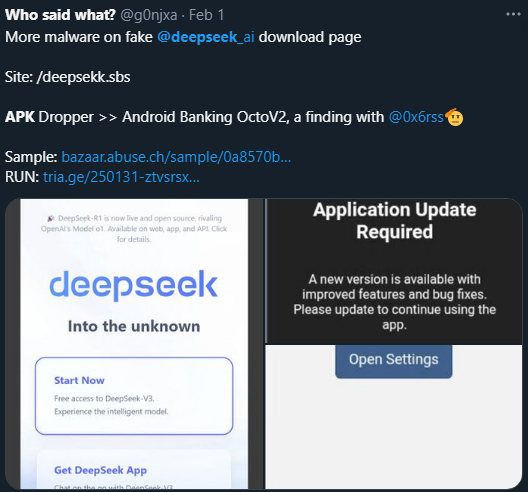
This malware is propagated via the malicious phishing link hxxps://deepsekk[.]sbs as shown in Figure 2.

Once the user clicks on the message, it downloads a malicious DeepSeek.apk (Hash: e1ff086b629ce744a7c8dbe6f3db0f68) from hxxps://deepsekk[.]sbs/DeepSeek.apk website and saves the file to device “Sdcard/Downloads” folder as shown in Figure 3.
Once the user falls prey to this Trojan and installs the malicious “DeepSeek.apk”, the app uses the genuine DeepSeek icon in the device app drawer as shown in Figure 4.

Once the user launches the malicious Deepseek app, an update screen appears. When the user clicks “Update”, they are prompted to enable the “Allow from this source” option and install an additional app, as shown in Figure 5.
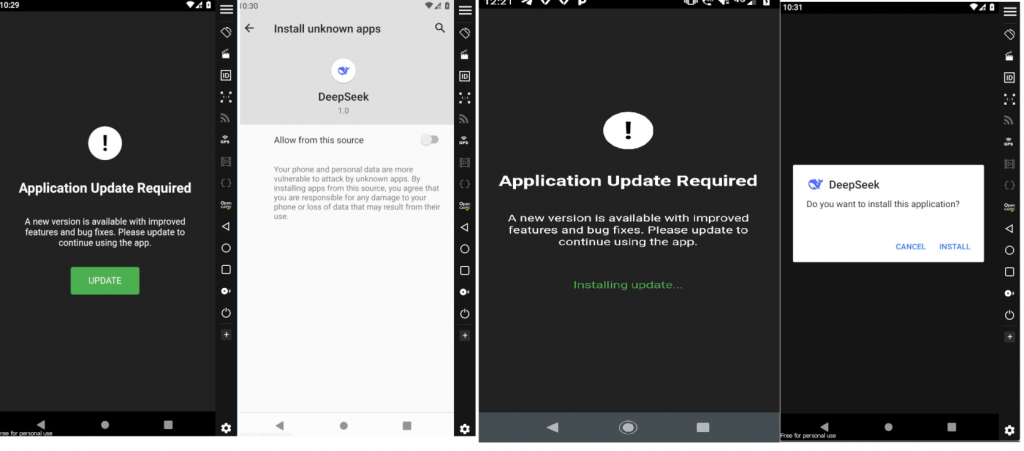
After completing this process, an additional Deepseek app icon appears in the device’s app drawer, as shown in Figure 6 . Based on the figure, we concluded that two instances of the Deepseek malware are installed on the device, each with a different package name.

To verify this, the Logcat logs show the installation process of two APKs, as seen in the below Figure 7.
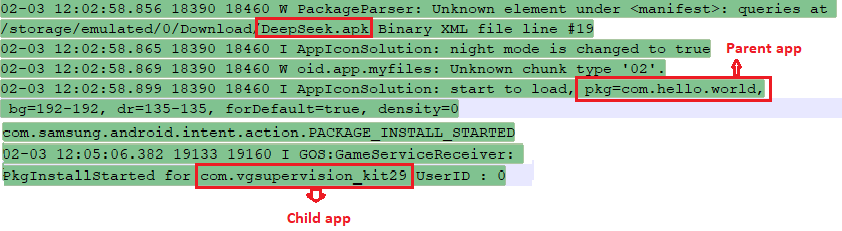
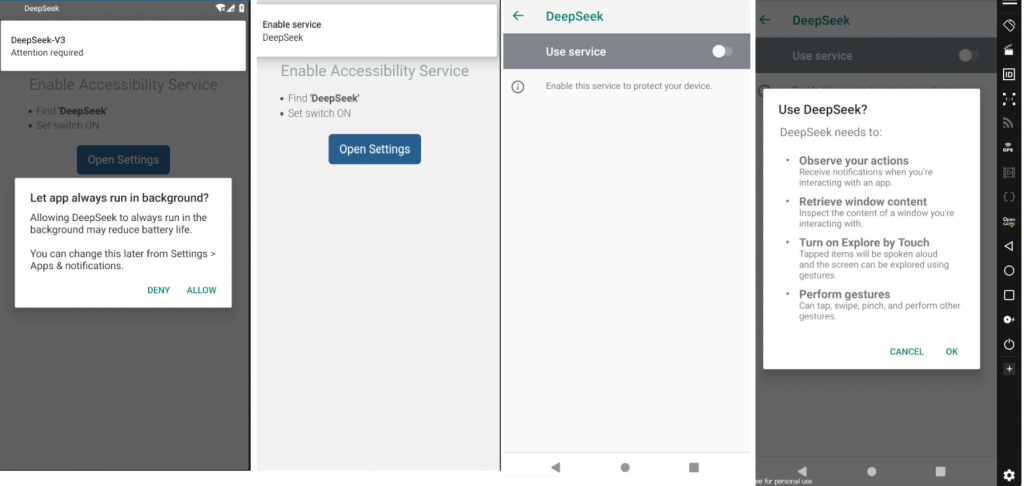
From here on, we will refer to the package “com.hello.world” as the parent app and “com.vgsupervision_kit29” as the child app. Once the child app “com.vgsupervision_kit29” is installed on the device, it frequently brings up the Accessibility Service setting option on the device, as shown in Figure 8 , until the user eventually allows this app to have the Accessibility Service enabled.
Technical Analysis
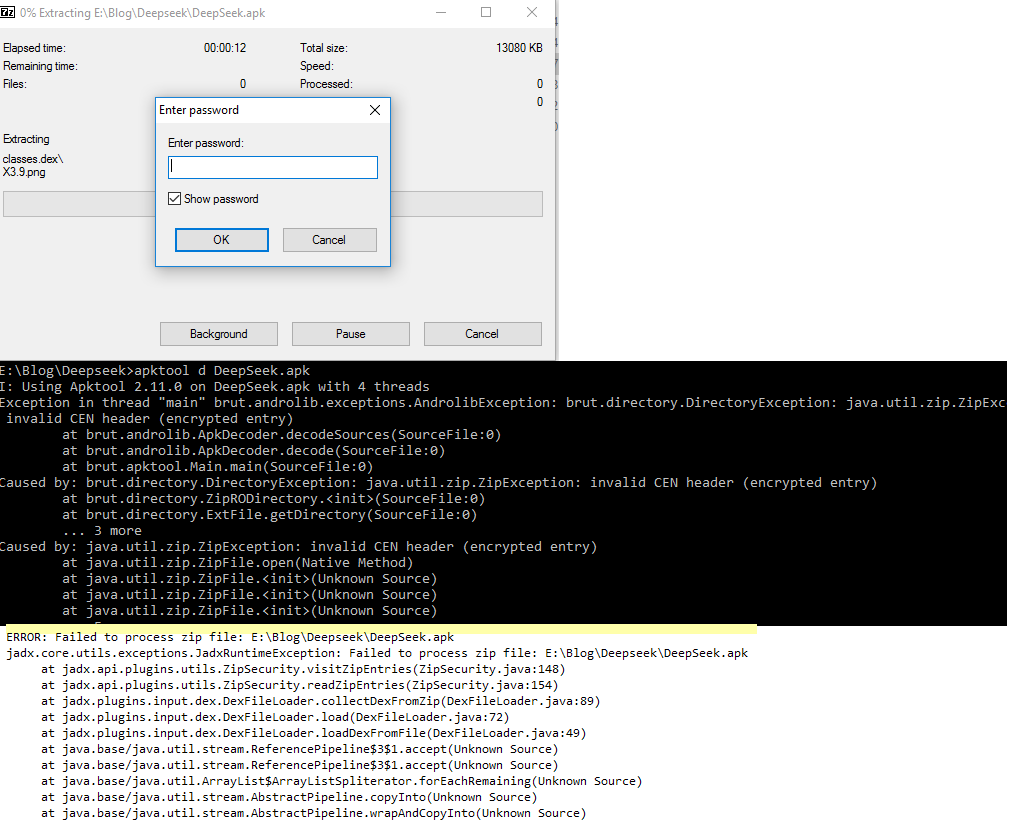
To proceed with our analysis, we attempted to extract the parent apk “deepseek.apk” using 7-Zip, but it prompted us for a password although we were able to successfully install and execute the app on the device. This is unusual and we have been observing a rapid increase in the number of such password-protected malicious APK files in our zoo collection. Furthermore, reversing tools like APKTool and Jadx failed to parse these APK files, as shown in Figure 9.
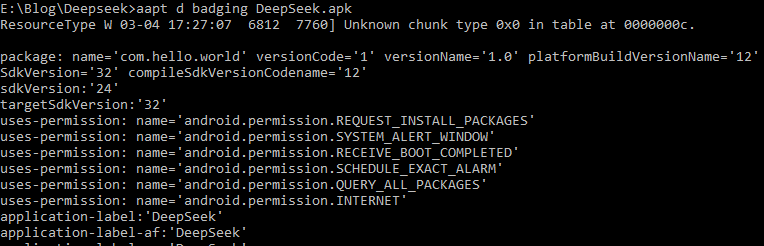
However, we noticed that the app under consideration was successfully parsed by the Android SDK tool aapt as shown in Figure 10.
Since the reversing tools failed to parse the APK, we extracted the files created by the app from the emulator after installation.
Code Analysis after child app installation
Locating the .cat file from parent app’s assets folder
Once the user launches the malicious parent app “com.hello.world”, it scans the app’s assets directory to find a file with the “.cat” extension as shown in Figure 11.
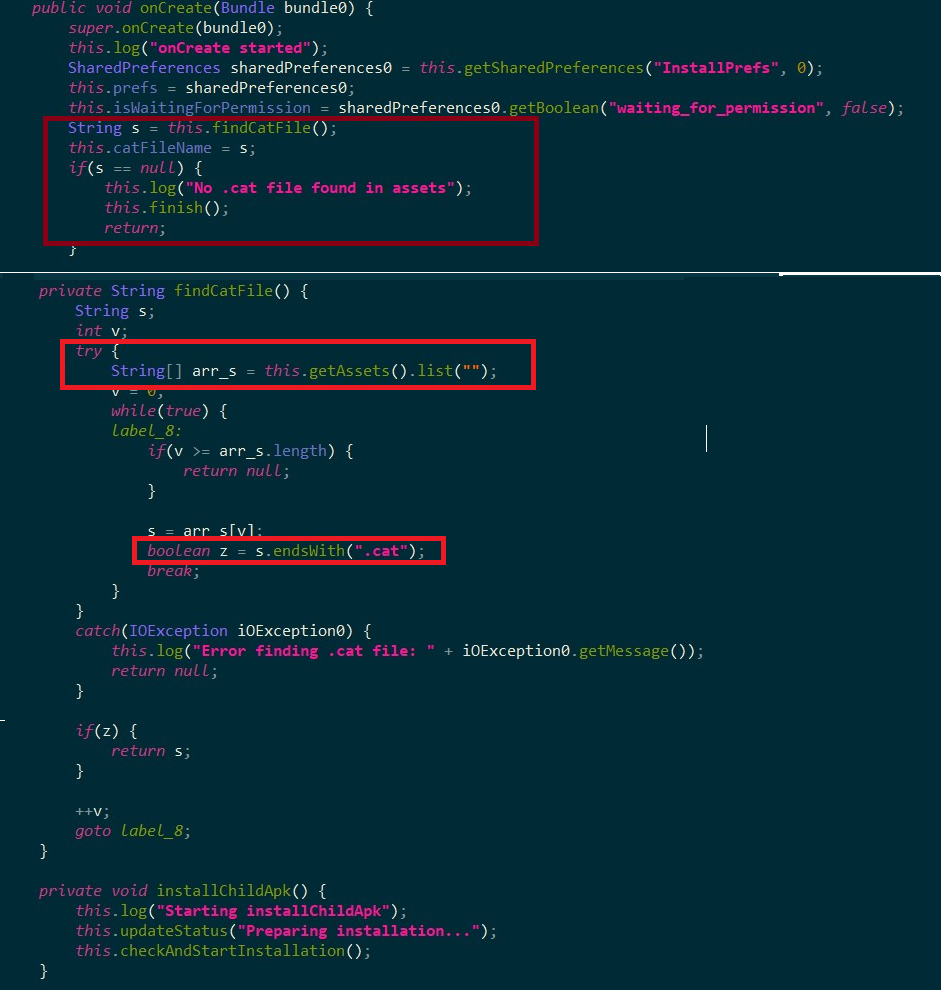
Figure 12 shows the .cat file present in the parent apps assets folder.
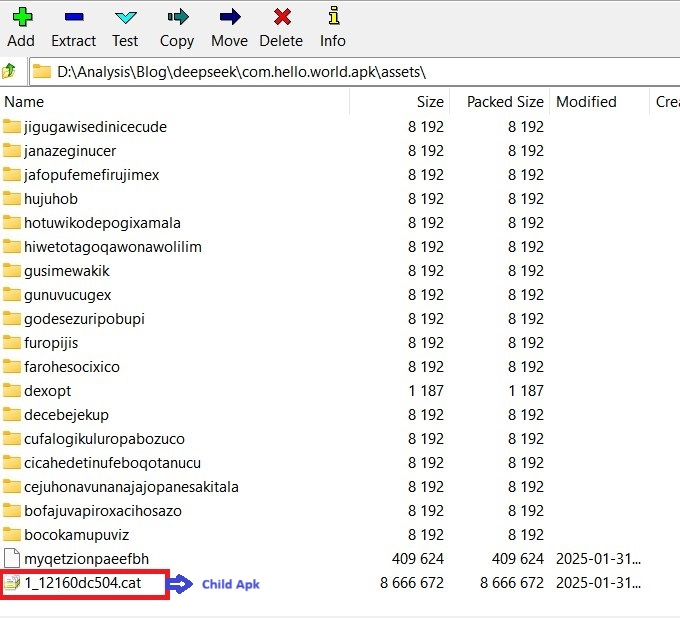
Extracting, Verifying and Installing the .cat file
The parent app opens “.cat” file from apps assets folder and copies the file into “data/data/com.hello.world/cache/Verify.apk” folder, which then uses the android method “PackageManager.getPackageArchiveInfo()” to check if it’s a valid APK. After the app verification, it starts installing the app on the device as a child package with the name as “com. vgsupervision_kit29” as shown in Figure 13. A point to note was that the installed child package was also password protected.
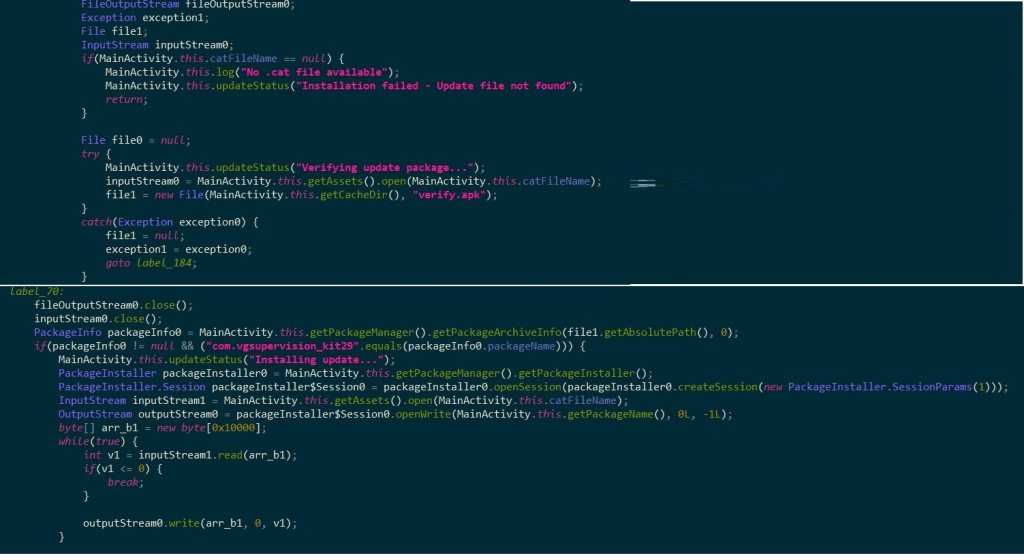
C2 Communication
After the malicious client application “com.vgsupervision_kit29” is successfully installed on the device, it utilizes a Domain Generation Algorithm (DGA), which is usually employed to dynamically generate domain names for Command & Control (C2) communication so as to evade domain blacklisting as shown in Figure 14.
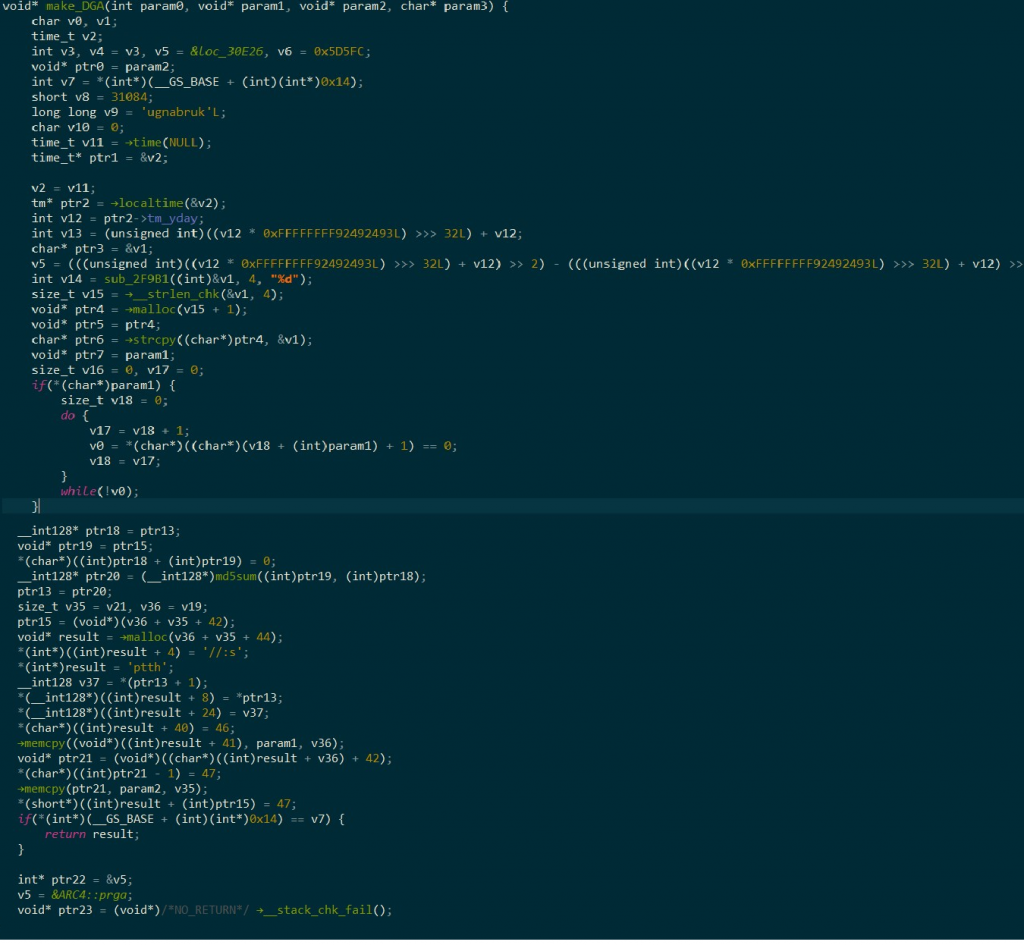
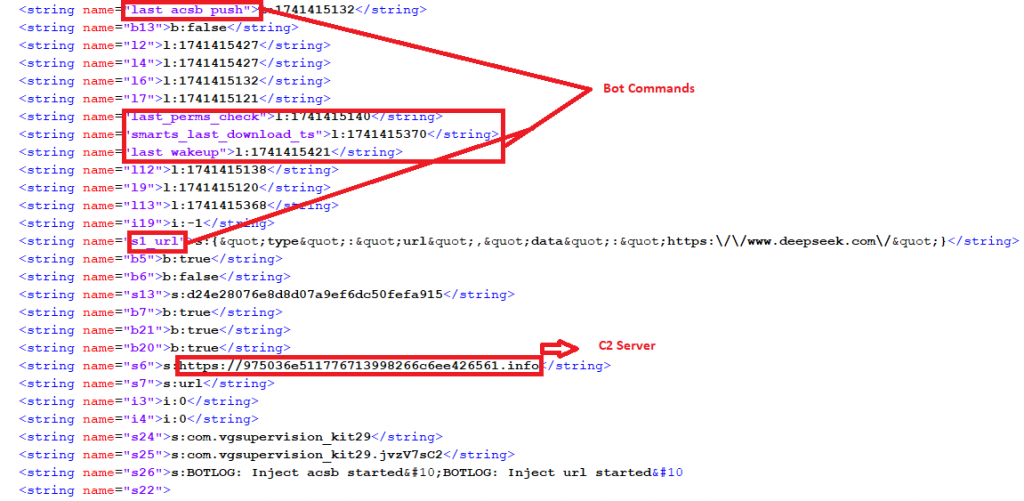
It then scans and retrieves a list of all installed applications on the victim’s device. This list is then transmitted to the C2 server. Additionally, the bot commands and C2 details are stored in the “/data/data/com.vgsupervision_kit29/shared_prefs/main.xml” file, as shown in Figure 15.
At K7, we protect all our customers from such threats. Do ensure that you protect your mobile devices by scanning them with a reputable security product like K7 Mobile Security and keeping the product active and updated. Also patch your devices for all the known vulnerabilities. Users are also warned to exercise caution and use only reputed platforms like Google Play and App Store for downloading software.
Indicators of Compromise (IoCs)
| Package Name | Hash | Detection Name |
| com.vgsupervision_kit29 | 99fe380d9ef96ddc4f71560eb8888c00 | Trojan ( 0056e5201 ) |
| com.hello.world | E1FF086B629CE744A7C8DBE6F3DB0F68 | Trojan ( 005bc2f21 ) |
URL
hxxps://deepsekk[.]sbs/DeepSeek[.apk
MITRE ATT&CK
| Tactics | Techniques |
| Defense Evasion | Hide ArtifactsDownload New Code at RuntimeUser EvasionInput Injection |
| Privilege Escalation | Device Administrator PermissionsAbuse Elevation Control Mechanism |
| Discovery | Security Software DiscoverySystem Information Discovery |
| Collection | Input CaptureKeylogging |
| Impact | Account Access RemovalData Encrypted for Impact |










