Recently, we came across a detection in our telemetry report named “PM KISAN YOJNA”, masquerading as the official government application that has gained our attention. This latest Android malware is a dropper that delivers a stealer to collect sensitive user information.
Let’s move to the technical part…
To evade security measures, some samples were deliberately malformed, and the malware uses a multi-stage dropper technique. The malware author intentionally crafted these dropper payloads to bypass static analysis, APK analysis tools such as Apktool and Jadx were unable to decompile them, complicating the analysis.
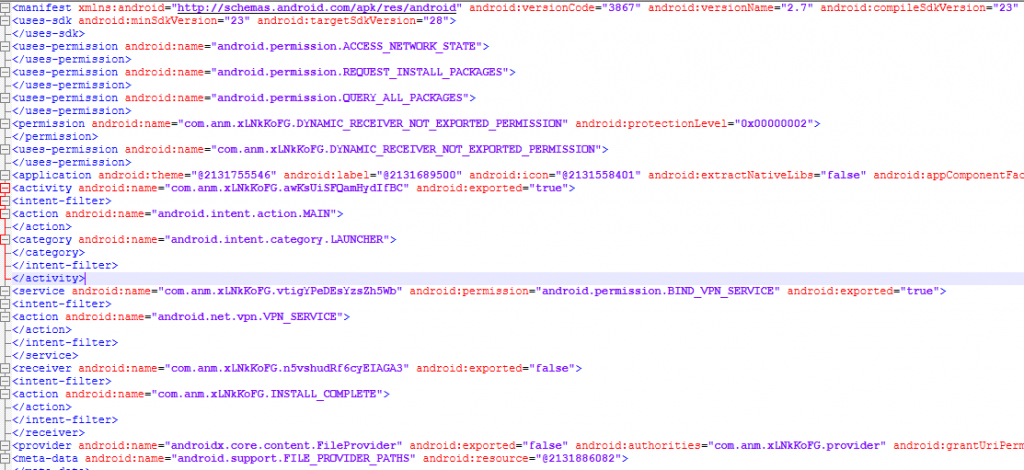
Here, I have used a tool apkinspector to decode AndroidManifest.xml from an APK, shown in Fig.1. It requests permissions such as QUERY_ALL_PACKAGES and REQUEST_INSTALL_PACKAGES to gain access to install apps without user knowledge.
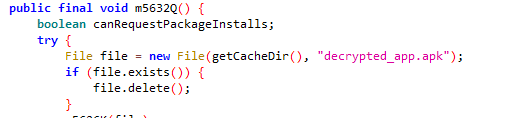
Static analysis reveals that the sample analysed installs another APK “decrypted_app.apk” with package name com.service.shop as shown in Fig.2.
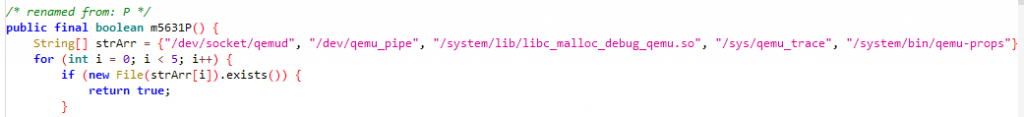
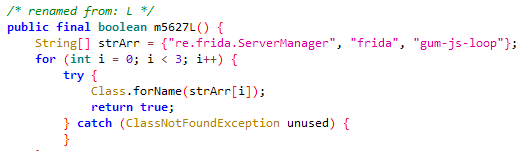
Also, the app incorporates emulator check, Frida check and root check to avoid being analysed in controlled environments as shown in Fig.3,Fig.4 and Fig.5.
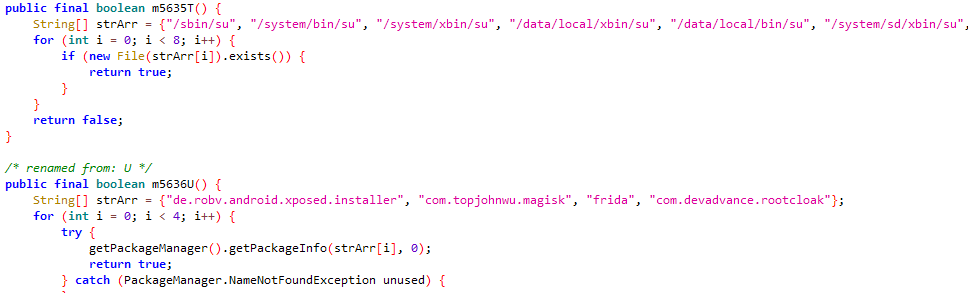
Malware Analysis
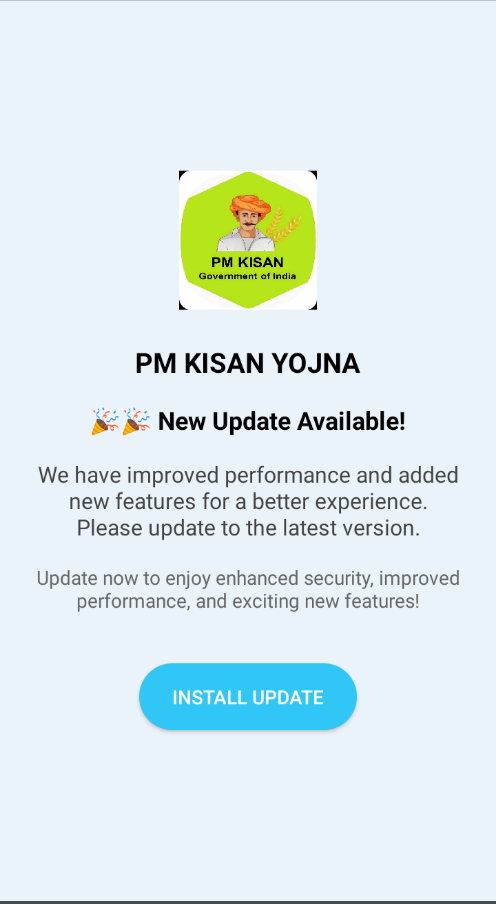
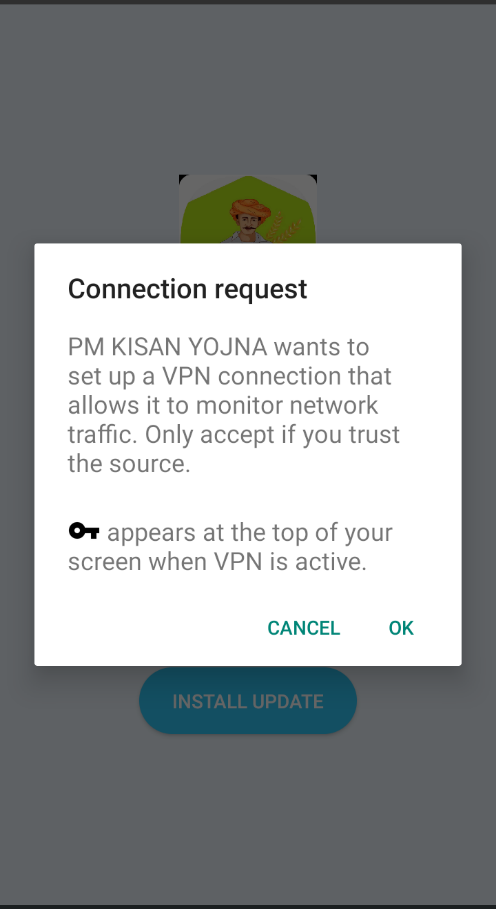
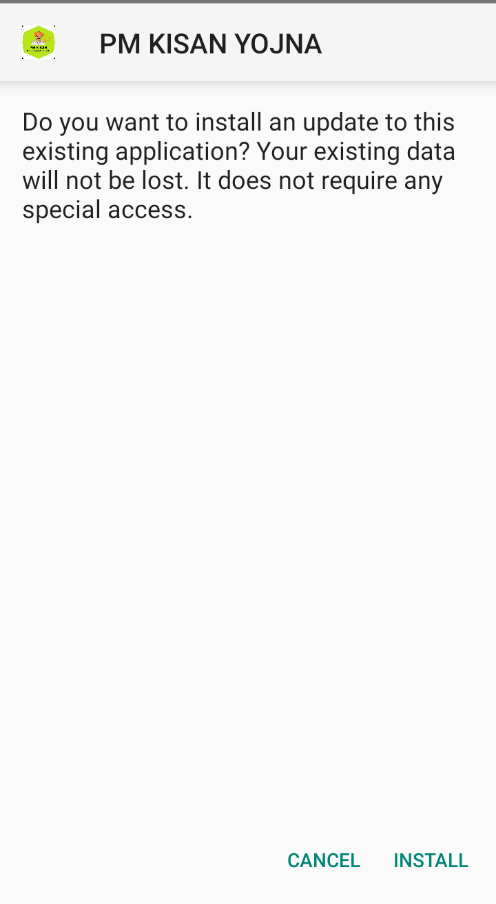
Once installed, the app immediately prompts the user to install an update for the app. Upon clicking “INSTALL UPDATE” the app requests permission to set up a VPN connection, stating “PM KISAN YOJNA” wants to set up a VPN connection likely to take control of network traffic on the device for data exfiltration/malicious purpose as shown in Fig.6 and Fig.7.
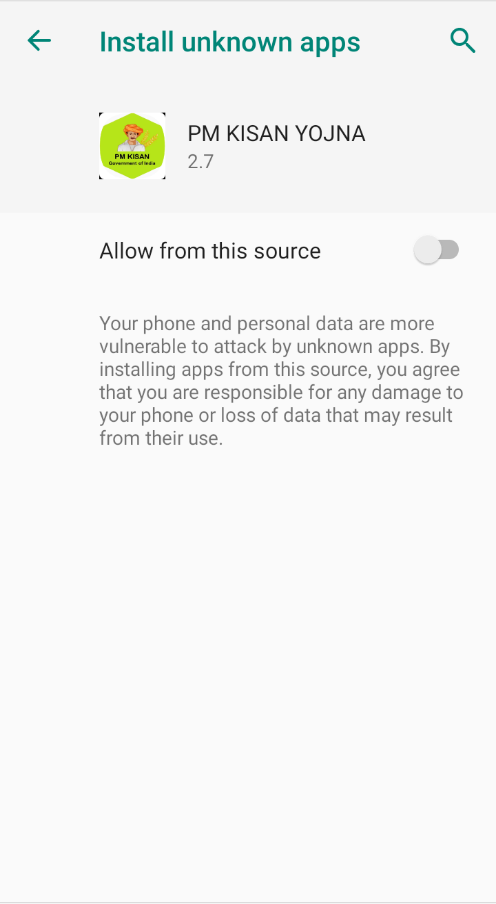
Upon affirming the VPN connection request, the app then prompts for permission to install apps from unknown sources. Once this access is granted, the app initiates an installation as shown in Fig.8 and Fig.9.
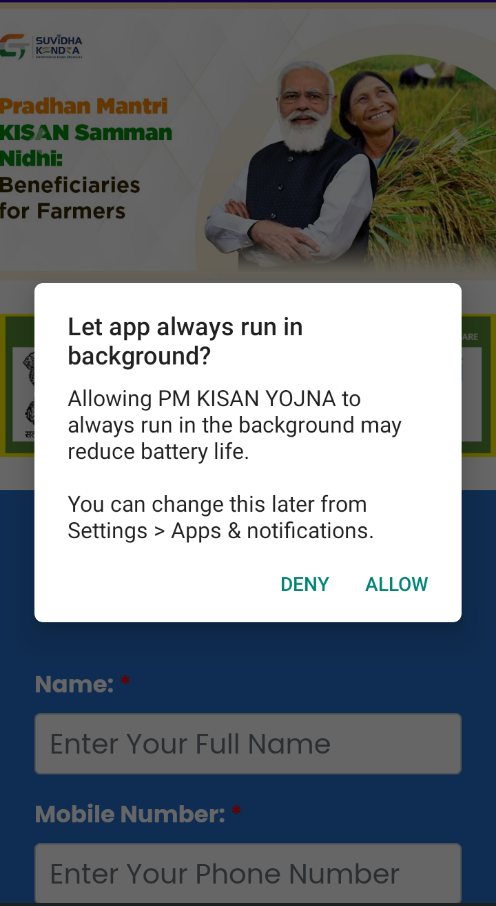
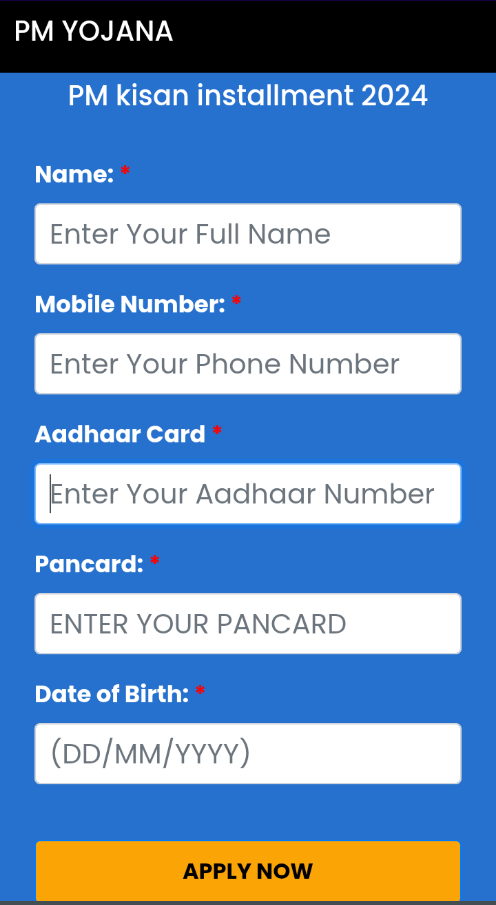
Once the update is installed, the app opens a fake “PM-Kisan Samman Nidhi” page. Here, it collects personal information like Name, Mobile Number, Aadhaar Card, PAN Card, and Date of Birth, and requests permission to run in the background as shown in Fig.10, Fig.11 and Fig.12.

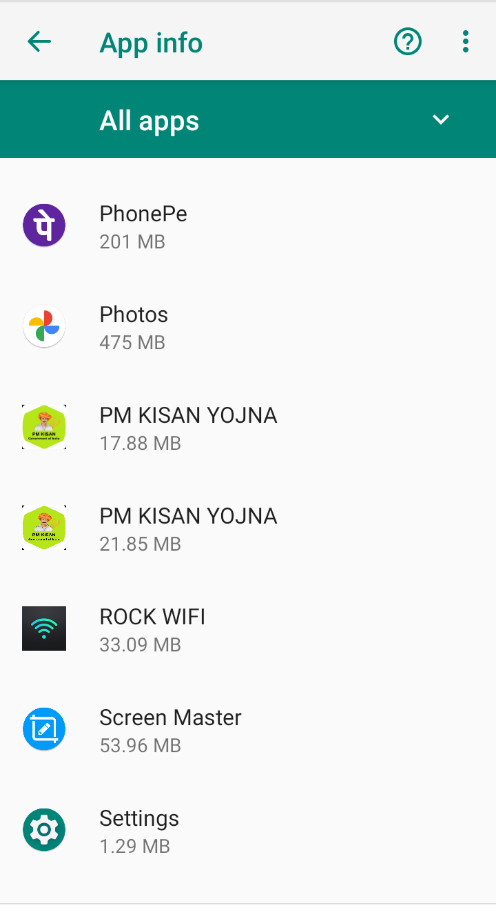
The app claiming to be an “update” isn’t an update for an existing app; it’s a separate application installed with the same name as an existing app in a stealthy way. Once installed, the app hides its icon from the App Drawer. Checking Settings > Apps will reveal that two applications having the same name are now present on the device as shown in Fig.13.
The dropped apk employs the same bypass technique to evade static analysis. Launching the dropped apk reveals the app functionalities, which include requesting sensitive permissions such as VIEW_SMS, and SEND_SMS as shown in Fig.14.
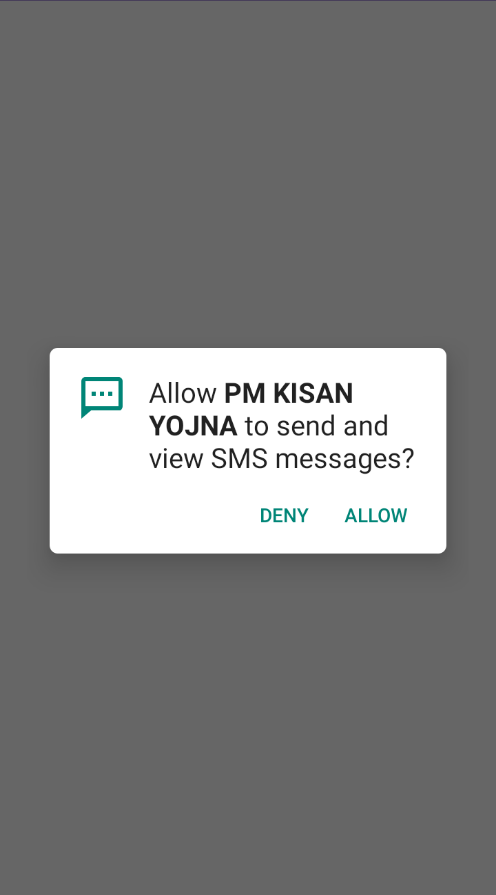
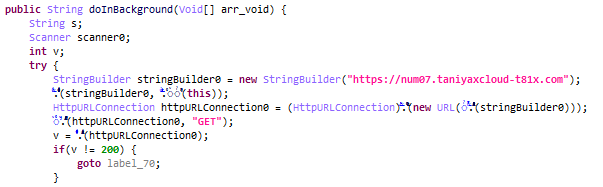
The app then establishes a connection without the user’s knowledge, accesses SMS messages, and then transmits them to the C2 server as shown in Fig.15. However, during this analysis, the C2 server was down.
This “PM KISAN YOJNA” malware deceptively installs, mimics official apps, and steals personal information and SMS. The new variant of the fake “PM KISAN YOJNA” malware which is named “Salvador” is also rising, this highlights that attackers are consistently refining their methods to appear legitimate, evade detection, and maximize data theft.
Never install apps from any third party sources apart from the official Play Store. Also keep your devices updated and patched against the latest security vulnerabilities.
Users are advised to use a reputable security product like “K7 Mobile Security” and also regularly update and scan your devices with it to stay safe from such threats. Stay vigilant to protect yourself from these evolving cybercriminal tactics.
IOCs
Dropper: a6e03e3fbe4eefffea8167c711f516ac
Payload: 39ecbe64e324d7ed9001a001a1a02edd
| Package Name | APK Hash | Detection Name |
| com.anm.xLNkKoFG | a6e03e3fbe4eefffea8167c711f516ac | Spyware ( 005c6e841 ) |
| com.YMQ.jUe3SzqW | 1a1492b7137187f889dbc3c62991fbb4 | Spyware ( 005c6e841 ) |
| com.reg.wIDTSOQC | c454724659b3a7e20943259b34f4cf6c | Spyware ( 005c6e841 ) |
| com.aeJ.aKAC3He4 | c15169f82b6faa4ab4d1153bd1f29d79 | Spyware ( 005c6e841 ) |
| com.irh.OUEzehFT | 4d88539abed469b952734a0ec82528fa | Spyware ( 005c6e841 ) |
| com.esd.ZpQiEIcr | 6ac966298d7411c891521c9ba2f4efaa | Spyware ( 005c6e841 ) |
| com.anm.xLNkKoFG | a6e03e3fbe4eefffea8167c711f516ac | Spyware ( 005c6e841 ) |
| com.grf.mSYuTgIj | 6cbdc73258944c70426a6472a22b02eb | Spyware ( 005c6e841 ) |








