Threat actors focus on gaining remote access and control of victims’ devices. For this they either use fake apps or masquerade as legitimate apps. This blog is about the Rusty Droid RAT, which masquerades Chrome browser for Android. The sample under consideration is taken from this tweet. It has the capabilities of tracking financial activities, which includes sending and reading SMS messages and spam messages, and intercepting emails from Gmail accounts. Additionally, it can initiate calls to premium-rate numbers, resulting in financial losses.
In this blog, we will be analyzing “com.catajuhufepusuwo.xenonome” which masquerades as “Chrome” as shown in Fig.1.
Technical Analysis
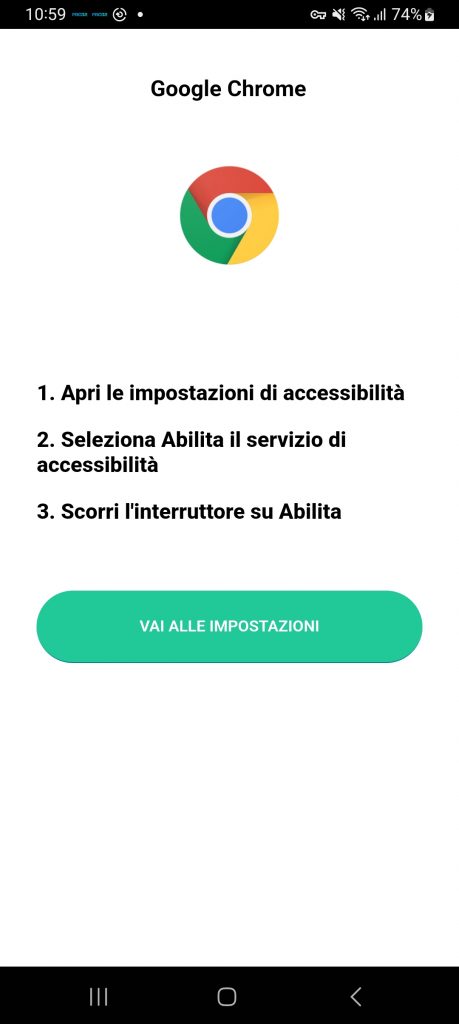
Once Rusty Droid is installed on the device, it keeps on bringing up the Accessibility Service setting option on the device, as shown in Fig.2, until the user allows this app to have the Accessibility Service enabled which hides the App’s icon from the application drawer.

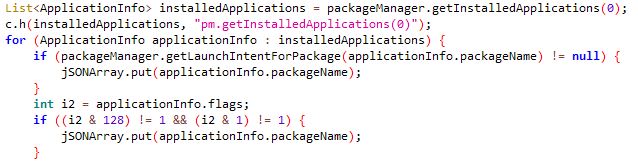
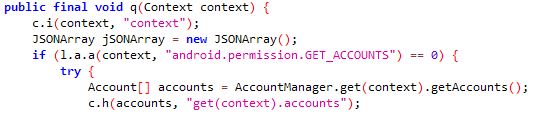
Rusty Droid initially gathers the following data from the victim’s device: contact list, Get accounts, installed app list, device info before establishing communication to C2 as shown in Fig.3, Fig.4, Fig.5.
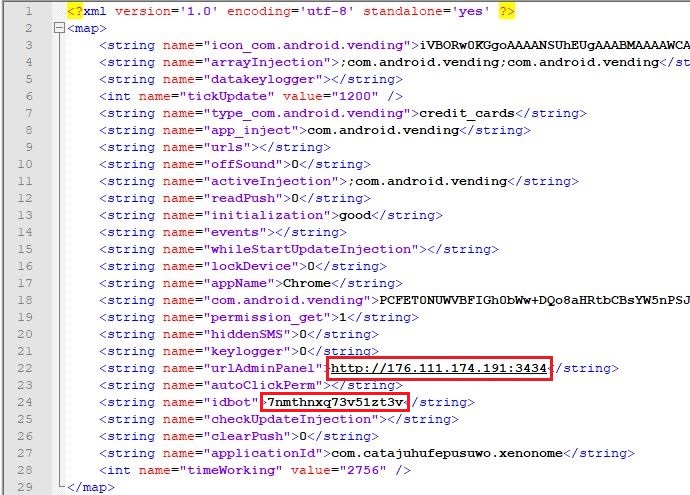
Once the accessibility permissions are granted, this malicious APK decrypts the malicious payload file called LqL.json from the App’s asset folder as shown in Fig.6, to an executable DEX format and loads the decrypted file. Also, the malicious APK drops settings.xml file which contains the malicious C2 server IP address and bot id as shown in Fig.7.
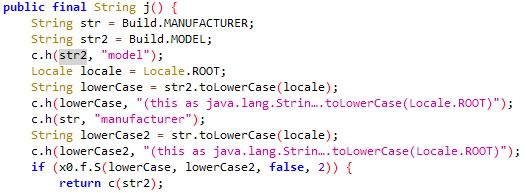
Abusing the Android Accessibility Service, this Trojan acts as a keylogger to steal all the victim’s information on the device; capturing passwords, login credentials, credit card details, and personal messages. This data is then forwarded to cybercriminals, who can exploit it for financial gain or other malicious purposes, leaving victims vulnerable to identity theft and fraud.
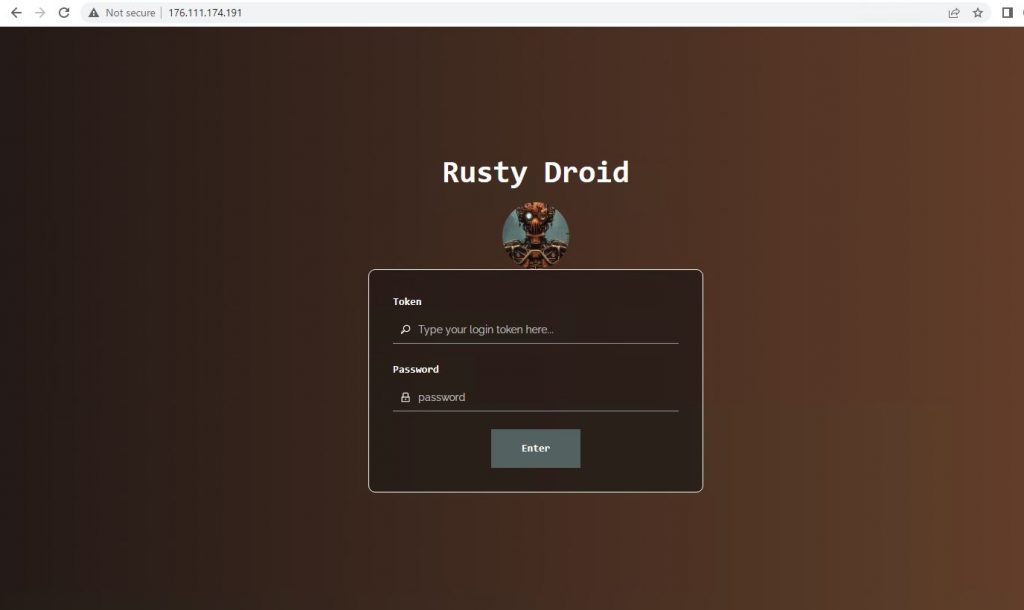
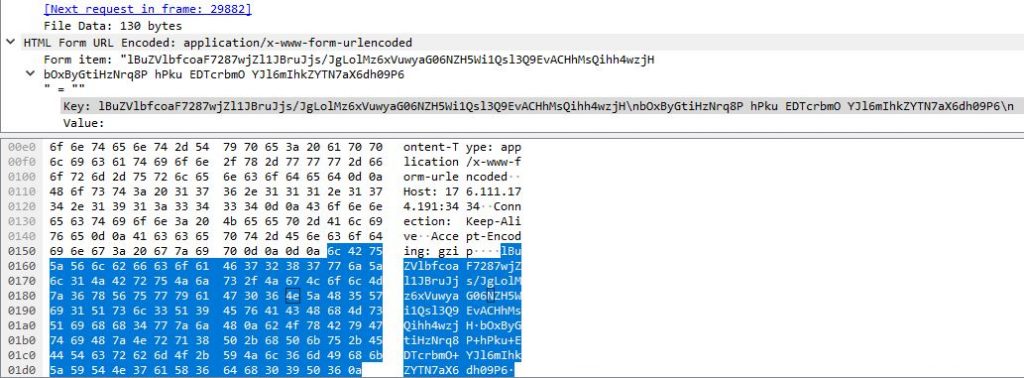
Once the malicious payload is loaded, it contacts the malicious C2 server “176.111.174[.]191” shown in Fig.8
The malware connects to the C2 server and receives encrypted data from the server as shown in Fig.9. The encrypted data is decrypted to receive the list of targeted applications as shown in Fig.10.
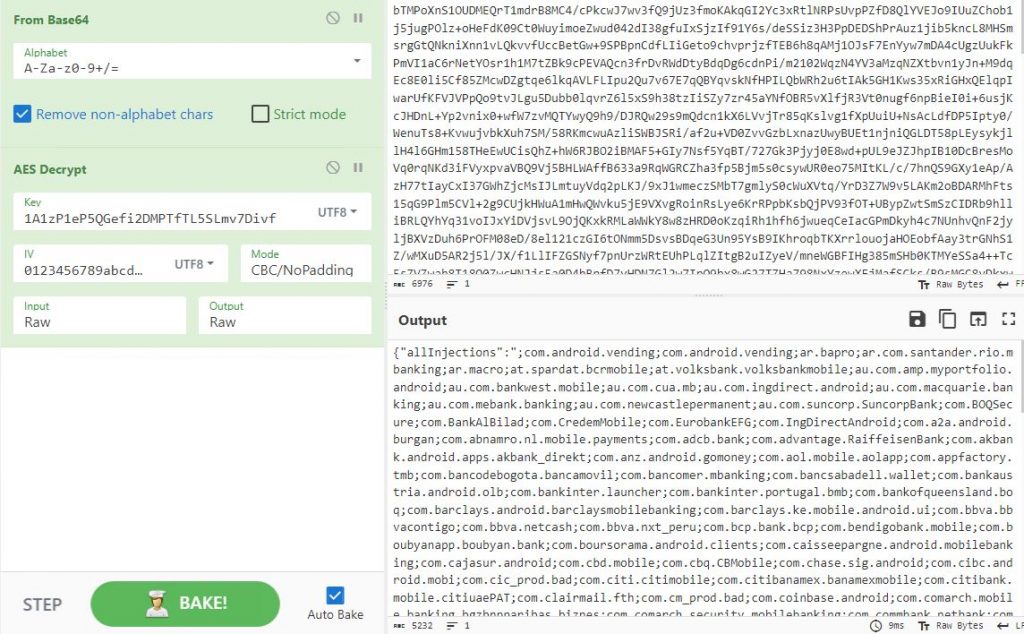
Whenever the user tries to interact with the targeted application on the device, the malware captures the keystroke to acquire the login credentials of the targeted app. It has the capacity to steal seed phrases for cryptocurrency wallets, potentially leading to the theft of valuable digital assets
Remote Access Trojans are a popular mobile threat and they are becoming more and more sophisticated in nature. Users are advised to use a reputable security product like K7 Mobile Security and also regularly update and scan your devices with it to stay safe from such threats. Also keep your devices updated and patched against the latest security vulnerabilities.
Targeted Applications
| com.android.vending | com.caisseepargne.android.mobilebanking |
| ar.bapro | com.cajasur.android |
| ar.com.santander.rio.mbanking | com.cbd.mobile |
| ar.macro | com.cbq.CBMobile |
| at.spardat.bcrmobile | com.chase.sig.android |
| at.volksbank.volksbankmobile | com.cibc.android.mobi |
| au.com.amp.myportfolio.android | com.cic_prod.bad |
| au.com.bankwest.mobile | com.citi.citimobile |
| au.com.cua.mb | com.citibanamex.banamexmobile |
| au.com.ingdirect.android | com.citibank.mobile.citiuaePAT |
| au.com.macquarie.banking | com.clairmail.fth |
| au.com.mebank.banking | com.cm_prod.bad |
| au.com.newcastlepermanent | com.coinbase.android |
| au.com.suncorp.SuncorpBank | com.comarch.mobile.banking.bgzbnpparibas.biznes |
| com.BOQSecure | com.comarch.security.mobilebanking |
| com.BankAlBilad | com.commbank.netbank |
| com.CredemMobile | com.csam.icici.bank.imobile |
| com.EurobankEFG | com.db.mm.norisbank |
| com.IngDirectAndroid | com.db.mobilebanking |
| com.a2a.android.burgan | com.db.pbc.miabanca |
| com.abnamro.nl.mobile.payments | com.db.pbc.mibanco |
| com.adcb.bank | com.dib.app |
| com.advantage.RaiffeisenBank | com.discoverfinancial.mobile |
| com.akbank.android.apps.akbank_direkt | com.finansbank.mobile.cepsube |
| com.anz.android.gomoney | com.finanteq.finance.ca |
| com.aol.mobile.aolapp | com.fullsix.android.labanquepostale.accountaccess |
| com.appfactory.tmb | com.fusion.banking |
| com.bancodebogota.bancamovil | com.fusion.beyondbank |
| com.bancomer.mbanking | com.garanti.cepsubesi |
| com.bancsabadell.wallet | com.getingroup.mobilebanking |
| com.bankaustria.android.olb | com.greater.Greater |
| com.bankinter.launcher | com.grppl.android.shell.BOS |
| com.bankinter.portugal.bmb | com.grppl.android.shell.CMBlloydsTSB73 |
| com.bankofqueensland.boq | com.grppl.android.shell.halifax |
| com.barclays.android.barclaysmobilebanking | com.htsu.hsbcpersonalbanking |
| com.barclays.ke.mobile.android.ui | com.imaginbank.app |
| com.bbva.bbvacontigo | com.infonow.bofa |
| com.bbva.netcash | com.ingbanktr.ingmobil |
| com.bbva.nxt_peru | com.isis_papyrus.raiffeisen_pay_eyewdg |
| com.bcp.bank.bcp | com.itau.empresas |
| com.bendigobank.mobile | com.kasikorn.retail.mbanking.wap |
| com.boubyanapp.boubyan.bank | com.konylabs.capitalone |
| com.boursorama.android.clients | com.konylabs.cbplpat |
| com.kutxabank.android | Com.magiclick.odeabank |
| com.kuveytturk.mobil | com.moneybookers.skrillpayments |
| com.latuabancaperandroid | com.mobileloft.alpha.droid |
IOCs
| Package Name | Hash | Detection Name |
| com.catajuhufepusuwo.xenonome | 3bc49abd12c9f0bc3d4f141e2f2376f3 | Trojan ( 0058fc031 ) |
| com.urgerdaao.dwwvbcows | fd9bc14fdfc21de632d363a80b4a69b3 | Trojan ( 0053b5f91 ) |
| com.znhbvvokm.iyjrxjabx | 2691b6a84986eb619d45af50016a17b7 | Trojan ( 0053b5f91 ) |
| com.doporuyobore.yikago | 789f57d8233b4a1b0a7a0ad8f7352ef8 | Trojan ( 0058ed4d1 ) |
| com.qjkcaktam.wyfyzisfa | 6b2a2579bdaac9ee796d274bd4ad530f | Trojan ( 0053b5f91 ) |
| com.doporuyobore.yikago | 629f602e284543cc3f355c6c98128574 | Trojan ( 005572801 ) |
| com.iijyzgtwg.oikklnflw | b58a906419cbe4f7d02a44467d2069f8 | Trojan ( 0053b5f91 ) |
| com.catajuhufepusuwo.xenonome | fc876e95f893bf66a5c22f20eceb62ce | Trojan ( 0058fc031 ) |
| com.jfufkgjcu.kntchyhax | 196e0290f33455c95a2ee0064ce4d8d8 | Trojan ( 0053b5f91 ) |
C2 mentioned in settings.xml
hxxp://176.111.174[.]191:3434