This is the second part of a six-part blog based on the paper submitted by my colleague Gregory and myself on Advanced Persistent Threats (APT), for AVAR 2014.
Continuing from the first part of our paper…
Initial Compromise
Armed with information obtained from the previous stage, the perpetrators may adopt several techniques to sneak into the organization. Traditional attacks involve actively targeting vulnerable applications and exploiting Internet facing resources like webservers, SQL servers, FTP servers, etc. As log analysis and security around these external resources have caught on, the attackers have had to evolve their tactics in order to be successful.
Infiltration Methodology
The attackers now target the most vulnerable element of any organization – the human. Social engineering tactics are used to entice an individual or a group of users into running code, which will allow the attackers to introduce their malware into the organization’s network. The most commonly used attack techniques are:
- Spear Phishing
- Watering Hole
Spear Phishing
Spear phishing involves the attacker compromising a machine by sending a well-crafted email to a targeted user and convincing him/her to:
- Open an embedded link that points to a website loaded with zero-day exploits, or
- Open a malicious attachment (EXE, PDF, DOCX etc.)
both of which exploit the rendering application to drop or download, and execute a payload with backdoor capabilities
Watering Hole
Watering hole attack involves the attacker placing exploits, possibly zero-day in nature, on a trusted website which is frequented by the users of the organization. When a targeted user visits the site, the exploit code is automatically invoked and the malware installed on his/her machine.
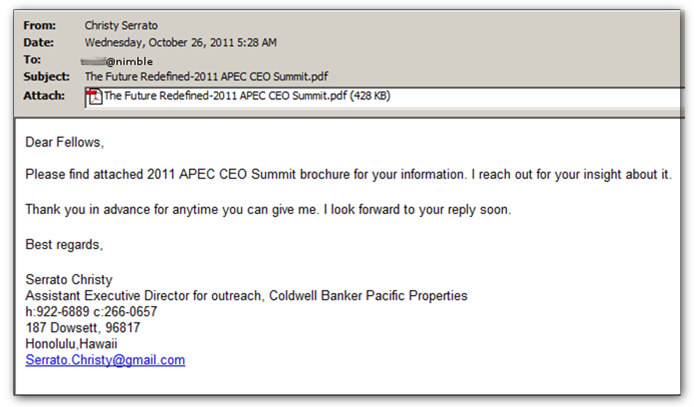
Case Study
The U.S. Veterans of Foreign Wars’ website was recently compromised to serve a zero-day exploit (CVE-2014-0322). A similar watering hole attack exploiting zero-day vulnerabilities has occurred in the past targeting a specific group of people by compromising the website of the Council for Foreign Relations.
Fig.2 shows publicly available website access logs of users along with their non-routable IP addresses. This information can be used to evaluate the browsing habits of individuals in the company and eventually to execute a watering hole attack.
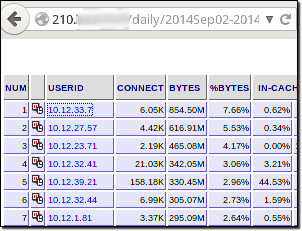
Fig.2: Publicly available map of internal IP addresses and their website logs
Security Bypassing
Email attachments, file downloads, HTTP requests, etc. originating from users undergo rigorous checks at various layers that include:
- Network/Gateway layer scanners
- Email/File/URL scanners
- Sandboxed file analysis
- Endpoint/Desktop layer scanner
- Anti-Virus/HIPS/firewall
- Application security features
- Operating system security features
Once the human element falls prey to social engineering, and is coaxed into downloading a file/email or visiting an exploit site, the attackers are faced with challenge of defeating a series of network and end point security solutions before conquering the victim’s machine. Listed below are some of the tactics used by the perpetrators to bypass these layers of security.
Attachment Archive File Format Abuse
Discrepancies in the way in which a security product handles a compressed file versus that of an un-archiving application has led to abuse of the popular ZIP file format. Un-archiving apps identify ZIP file types by scanning the last 64KB of the file for a special magic marker. Security scanners on the other hand, with a need for speed, identify the file type by inspecting only the first few bytes from the beginning of the file.
An attacker abuses this disparity by creating a malicious ZIP file and manipulating its headers by adding junk data at the beginning of the ZIP file. This specially crafted file deceives security scanners into thinking that it is of an unknown type and escapes detection, but un-archiving applications are able to successfully extract the malicious code at the end point.
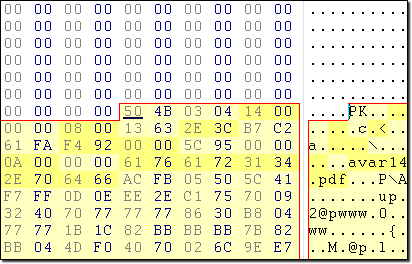
Fig.3 shows a Proof-of-Concept [2] archive file that is capable of evading security scanners
Fig.3: Crafted ZIP file with NULL data prefixed.
Gateway Sandboxing Bypass
Suspicious files that match certain criteria are typically executed within a sandboxed environment for a short period of time. Depending on their behavior, the files are either blocked from the user or released to him/her.
Attackers can craft malicious files which detect such controlled settings by looking for specific registry keys, in-memory code changes, mouse pointer movement, etc.
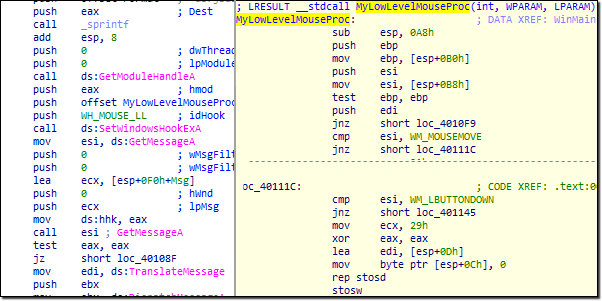
For example if the malicious file identifies that it is being executed in a sandboxed environment, it stays idle without performing any activity thereby bypassing this check. The Up-Clicker Trojan [3] attempts to evade sandbox analysis by staying idle and waiting for a mouse click before activating itself.
Fig.4: Code showing Up-Clicker Trojan set to activate on mouse click
Browser Multi-Purpose Internet Mail Extensions (MIME) Sniffing
This attack exploits differences in the way in which security scanners and web browsers identify the content returned by an HTTP server.
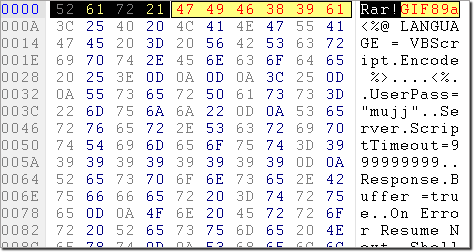
Security scanners parse the magic headers available at the beginning of a file returned by the web server, to identify the file type. This means that a specially crafted malicious HTML file containing the magic marker commonly found in a GIF image will be identified by the scanner as an image file, exempted from scanning and let through into the network.
Web browsers on the other hand, depend on the MIME type in the HTTP response header returned by the web server to identify the file type. When this information is absent as is the case of a response from an attacker controlled web server, the web browser resorts to content sniffing to determine the MIME type. So, the same malicious HTML containing the GIF magic marker will now be identified as HTML content by the user’s browser and rendered accurately to execute the exploit code.
Fig.5: Malicious script containing bogus RAR and GIF magic markers.
Click here to read the third part of this blog
References:
[2] http://www.reversinglabs.com/news/vulnerability/reversinglabs-vulnerability-advisories.html
[3] http://www.infosecurity-magazine.com/news/trojan-upclicker-ties-malware-to-the-mouse
Lokesh Kumar
K7 Threat Control Lab
If you wish to subscribe to our blog, please add the URL provided below to your blog reader:
https://labs.k7computing.com/feed/